Cataloguing Strategic Innovations and Publications
Designing and Implementing an Enterprise Network for Security, Efficiency, and Resilience

The success of any enterprise depends on the efficiency and security of its network. A well-designed and implemented enterprise network provides the backbone for all the organization's operations, ensuring the seamless flow of data, communication, and collaboration. However, designing and implementing an enterprise network can be a daunting task, with several factors to consider, including security, efficiency, and resilience. In this blog, we will explore the major players in this space and discuss whether to use a single vendor or hybrid network approach.
Major Players in the Enterprise Network Space:
There are several major players in the enterprise network space, including Cisco, Juniper Networks, Hewlett Packard Enterprise, Aruba Networks, and Extreme Networks. These companies provide a range of networking solutions, from switches, routers, firewalls, and wireless access points to network management software.
Single Vendor vs. Hybrid Network Approach:
When designing and implementing an enterprise network, you can either use a single vendor or a hybrid network approach. A single-vendor approach involves using network solutions from one vendor, while a hybrid network approach combines solutions from multiple vendors.
A single-vendor approach can be beneficial in terms of ease of management, as all the solutions come from one vendor, ensuring compatibility and integration. It can also simplify support and maintenance, as you only need to deal with one vendor for all your network needs.
However, a single-vendor approach can also be limiting, as you are limited to the solutions provided by that vendor. You may also be locked into that vendor's pricing and upgrade cycles, limiting your flexibility.
On the other hand, a hybrid network approach provides more flexibility and choice, allowing you to choose the best solutions from multiple vendors to meet your specific needs. It can also be more cost-effective, as you can choose the most cost-effective solution for each aspect of your network.
However, a hybrid network approach can also be more complex, as you need to ensure compatibility and integration between solutions from different vendors. It can also require more support and maintenance, as you may need to deal with multiple vendors for different aspects of your network.
Designing and Implementing an Enterprise Network:
When designing and implementing an enterprise network, you need to consider several factors, including:
- Security: Ensure that your network is secure, with firewalls, intrusion detection and prevention systems, and other security measures in place.
- Efficiency: Design your network for maximum efficiency, with optimized routing, load balancing, and Quality of Service (QoS) features.
- Resilience: Ensure that your network is resilient, with redundant links and backup systems in place to minimize downtime.
- Scalability: Design your network to scale as your organization grows, with the ability to add new devices and services as needed.
Designing and implementing an enterprise network can be a complex and challenging task, but with the right planning and approach, you can ensure maximum security, efficiency, and resilience. Whether you choose a single vendor or hybrid network approach, it's important to consider the major players in this space and select the solutions that best meet your organization's specific needs.
Additionally, it's essential to have a clear understanding of your organization's requirements, such as the number of users, types of devices, and the applications that will be running on the network. This will help you select the appropriate network solutions that can handle your organization's needs.
Furthermore, as the threat landscape continues to evolve, it's important to stay up-to-date with the latest security technologies and best practices. You should regularly assess your network's security posture, perform vulnerability scans and penetration tests, and apply the latest security patches and updates to ensure that your network is protected against the latest threats.
Moreover, it's critical to have a comprehensive disaster recovery plan in place in case of unexpected events such as natural disasters, cyberattacks, or system failures. A disaster recovery plan should include backup systems and data, as well as procedures for restoring critical systems and services.
In conclusion, designing and implementing an enterprise network is a crucial aspect of any organization's success. By ensuring maximum security, efficiency, and resilience, you can provide a solid foundation for all your operations. Whether you choose a single vendor or hybrid network approach, it's essential to carefully consider the major players in this space and select the appropriate solutions that meet your specific needs. Additionally, regularly assessing your network's security posture and having a comprehensive disaster recovery plan in place will help you mitigate risks and ensure business continuity in the face of unexpected events.
Finally, it's important to keep up with industry trends and advancements in network technology. For example, software-defined networking (SDN) and network function virtualization (NFV) are emerging technologies that can bring significant benefits to enterprise networks. SDN enables network administrators to centrally manage and automate network configuration, while NFV allows network services such as firewalls and load balancers to be virtualized and run on commodity hardware, reducing costs and increasing flexibility.
Overall, designing and implementing an enterprise network requires careful planning, consideration of multiple factors, and a continuous focus on improving security, efficiency, and resilience. By staying up-to-date with the latest technologies and best practices, you can ensure that your network remains a strong foundation for your organization's success.
Here are some of the leading companies in the IT Networking and network space, along with a brief list of their key products:
- Cisco Systems - Cisco is one of the world's largest networking companies, providing a range of hardware and software products for network infrastructure, security, collaboration, and cloud computing. Key products include:
- Catalyst switches
- Nexus switches
- ASR routers
- ISR routers
- Meraki wireless access points
- Umbrella cloud security platform
- Juniper Networks - Juniper is a leading provider of network hardware and software solutions, with a focus on high-performance routing, switching, and security. Key products include:
- MX Series routers
- QFX Series switches
- EX Series switches
- SRX Series firewalls
- Contrail SD-WAN
- Huawei - Huawei is a major player in the global networking market, offering a broad portfolio of products for enterprise and carrier customers. Key products include:
- CloudEngine switches
- NetEngine routers
- AirEngine Wi-Fi access points
- HiSecEngine security solutions
- FusionInsight big data platform
- HPE Aruba - HPE Aruba specializes in wireless networking solutions, with a strong focus on mobility and IoT. Key products include:
- ArubaOS switches
- ClearPass network access control
- AirWave network management
- Instant On wireless access points
- Central cloud management platform
- Extreme Networks - Extreme Networks provides a range of network solutions for enterprise and service provider customers, with an emphasis on simplicity and automation. Key products include:
- ExtremeSwitching switches
- ExtremeRouting routers
- ExtremeWireless Wi-Fi access points
- ExtremeControl network access control
- ExtremeCloud cloud management platform
- Fortinet - Fortinet is a leading provider of cybersecurity solutions, including network security, endpoint security, and cloud security. Key products include:
- FortiGate firewalls
- FortiAnalyzer analytics platform
- FortiClient endpoint protection
- FortiWeb web application firewall
- FortiSIEM security information and event management
These are just a few examples of the many companies and products in the IT networking and network space.
Here are some leading companies in the IT networking and network space that offer proxy solutions, along with a brief list of their key products:
- F5 Networks - F5 Networks offers a range of networking and security solutions, including application delivery controllers (ADCs) and web application firewalls (WAFs) that can act as proxies. Key products include:
- BIG-IP ADCs
- Advanced WAF
- SSL Orchestrator
- DNS services
- Silverline cloud-based WAF and DDoS protection
- Symantec (now Norton LifeLock) - Symantec provides a range of security solutions, including web security and cloud access security brokers (CASBs) that can function as proxies. Key products include:
- Web Security Service
- CloudSOC CASB
- ProxySG secure web gateway
- Advanced Secure Gateway
- SSL Visibility Appliance
- Blue Coat (now part of Symantec) - Blue Coat offers a range of proxy solutions for web security and application performance. Key products include:
- ProxySG secure web gateway
- Advanced Secure Gateway
- SSL Visibility Appliance
- WebFilter URL filtering
- MACH5 WAN optimization
- Zscaler - Zscaler provides cloud-based security and networking solutions, including web proxies and secure web gateways. Key products include:
- Zscaler Internet Access (ZIA)
- Zscaler Private Access (ZPA)
- Zscaler Cloud Firewall
- Zscaler Cloud Sandbox
- Zscaler B2B
- Palo Alto Networks - Palo Alto Networks offers a range of security and networking solutions, including a next-generation firewall (NGFW) that can act as a proxy. Key products include:
- Panorama network security management
- NGFWs (PA Series)
- Prisma Access secure access service edge (SASE)
- GlobalProtect remote access VPN
- Cortex XDR extended detection and response
Many companies offer proxy solutions in IT networking. Here are a few of them and a brief overview of their products:
1. Cisco: Cisco offers a range of proxy solutions, including Cisco Web Security, Cisco Cloud Web Security, and Cisco Email Security. These solutions provide advanced threat protection, URL filtering, and data loss prevention features.
2. F5 Networks: F5 Networks offers a range of proxy solutions, including F5 BIG-IP Local Traffic Manager and F5 Advanced Web Application Firewall. These solutions provide load balancing, SSL offloading, and application security features.
3. Blue Coat: Blue Coat offers a range of proxy solutions, including Blue Coat ProxySG and Blue Coat Web Security Service. These solutions provide web filtering, malware protection, and data loss prevention features.
4. Fortinet: Fortinet offers a range of proxy solutions, including FortiGate and FortiWeb. These solutions provide web filtering, SSL inspection, and application security features.
5. Palo Alto Networks: Palo Alto Networks offers a range of proxy solutions, including Palo Alto Networks Next-Generation Firewall and Palo Alto Networks Threat Prevention. These solutions provide advanced threat protection, URL filtering, and data loss prevention features.
When comparing these products, it's important to consider factors such as their feature set, ease of use, scalability, and cost. Some products may be better suited for small businesses, while others may be better suited for large enterprises. Additionally, some products may offer more advanced features than others, such as the ability to inspect encrypted traffic. It's also important to consider the level of support offered by each vendor, as well as their track record in terms of security and reliability. Ultimately, the best proxy solution will depend on the specific needs of the organization and the budget available.
It's difficult to provide a comprehensive comparison of all the products from the different companies mentioned, as each solution has its strengths and weaknesses depending on specific use cases and requirements. However, here are some general pros and cons of the products mentioned:
- Cisco Systems
- Pros: Cisco is a market leader in the networking space, with a broad range of hardware and software solutions to meet various needs. Their products are known for their reliability, scalability, and interoperability. Cisco is also investing in emerging technologies such as software-defined networking (SDN) and the Internet of Things (IoT).
- Cons: Cisco's products can be expensive, and their licensing models can be complex. Customers may require specialized expertise to configure and maintain Cisco solutions, which can add to the overall cost.
- Juniper Networks
- Pros: Juniper is a leading provider of high-performance networking solutions, with a strong focus on security. Their products are known for their reliability and scalability, and Juniper has a reputation for innovation in areas such as software-defined networking (SDN) and automation. Juniper's solutions are also designed to integrate well with other vendors' products.
- Cons: Juniper's product portfolio may be more limited compared to competitors such as Cisco. Some customers may also find Juniper's CLI (command-line interface) less intuitive compared to other vendors' GUI (graphical user interface).
- Huawei
- Pros: Huawei offers a comprehensive portfolio of networking products, including hardware, software, and services. They are known for their competitive pricing and innovation, particularly in emerging markets. Huawei's solutions are designed to be easy to use and manage, with a focus on user experience.
- Cons: Huawei has faced scrutiny from some governments over security concerns, which may be a factor in some customers' purchasing decisions. In addition, some customers may have concerns about the quality and reliability of Huawei's products, particularly in comparison to established market leaders.
- HPE Aruba
- Pros: HPE Aruba is a leading provider of wireless networking solutions, with a strong focus on mobility and IoT. Their products are designed to be easy to use and manage, with a focus on user experience. HPE Aruba also offers a range of cloud-based solutions for centralized management and analytics.
- Cons: HPE Aruba's product portfolio may be more limited compared to competitors such as Cisco. Some customers may also find their pricing less competitive compared to other vendors.
- Extreme Networks
- Pros: Extreme Networks offers a range of networking solutions for enterprise and service provider customers, with an emphasis on simplicity and automation. Their products are designed to be easy to use and manage, with a focus on user experience. Extreme Networks also offers cloud-based solutions for centralized management and analytics.
- Cons: Extreme Networks' product portfolio may be more limited compared to competitors such as Cisco. Some customers may also find their pricing less competitive compared to other vendors.
- Fortinet
- Pros: Fortinet is a leading provider of cybersecurity solutions, with a range of products for network security, endpoint security, and cloud security. Their products are designed to be easy to use and manage, with a focus on integration and automation. Fortinet is also investing in emerging technologies such as artificial intelligence (AI) and machine learning (ML).
- Cons: Some customers may find Fortinet's solutions less scalable compared to other vendors. In addition, Fortinet's licensing models can be complex, which may add to the overall cost.
- F5 Networks
- Pros: F5 Networks is a leading provider of application delivery and security solutions, including web application firewalls (WAFs) and proxies. Their products are known for their performance, scalability, and security. F5 Networks is also investing in emerging technologies such as cloud-native
Here is a comparison of some popular proxy products in the market:
- Squid Proxy
- Pros: Squid is a free and open-source proxy server that is widely used for caching web content and improving network performance. It is highly configurable and supports a range of protocols, including HTTP, HTTPS, FTP, and more. Squid is also compatible with many operating systems and can be used in various deployment scenarios.
- Cons: Squid may require more technical expertise to set up and configure compared to commercial solutions. It also may not have as many advanced features as some commercial products.
- Nginx
- Pros: Nginx is a high-performance web server and reverse proxy that is widely used in production environments. It is known for its scalability, reliability, and speed. Nginx can be used as a standalone proxy or in conjunction with other web servers such as Apache. It also supports a wide range of protocols and can be used for load balancing and content caching.
- Cons: Nginx may require more technical expertise to set up and configure compared to other commercial products. Some users may also find the documentation to be less comprehensive compared to other solutions.
- HAProxy
- Pros: HAProxy is a popular open-source load balancer and reverse proxy server that is known for its high performance and reliability. It supports a range of protocols, including TCP, HTTP, and HTTPS, and can be used for load balancing, content caching, and more. HAProxy also has an active user community and a comprehensive documentation repository.
- Cons: HAProxy may require more technical expertise to set up and configure compared to some commercial products. It may also not have as many advanced features as some other solutions.
- F5 BIG-IP
- Pros: F5 BIG-IP is a commercial proxy server that is widely used in enterprise environments. It is known for its advanced features such as traffic management, application security, and content caching. F5 BIG-IP can be used to optimize network traffic, improve application performance, and provide high availability for applications.
- Cons: F5 BIG-IP may be more expensive compared to other solutions, and may require specialized expertise to configure and maintain. Some users may also find the licensing model to be complex.
- Blue Coat ProxySG
- Pros: Blue Coat ProxySG is a commercial proxy server that is widely used in enterprise environments. It is known for its advanced features such as web filtering, application visibility and control, and threat protection. Blue Coat ProxySG can be used to secure and optimize network traffic, improve application performance, and provide advanced security features such as malware protection and DLP.
- Cons: Blue Coat ProxySG may be more expensive compared to other solutions, and may require specialized expertise to configure and maintain. Some users may also find the licensing model to be complex.
It's difficult to determine which company is the safest to partner with for networking and proxy needs, as each company has its strengths and weaknesses.
That being said, when selecting a company to partner with, it's important to consider factors such as the company's reputation, track record, and level of customer support. It's also important to consider the specific needs of your organization and whether the company's products and services align with those needs.
Some well-known companies in the networking and proxy space with strong reputations and a history of providing reliable and secure products and services include Cisco, Juniper Networks, Palo Alto Networks, and Fortinet. However, it's important to conduct thorough research and evaluation before deciding to ensure that the chosen partner meets your specific needs and security requirements.
When it comes to product stability and reliability for networking and proxy needs, several companies have a strong reputation for providing high-quality products and services. Here are a few examples:
- Cisco: Cisco is one of the most well-known companies in the networking space, and is known for its high-quality routers, switches, firewalls, and other networking equipment. Cisco's products are known for their reliability, performance, and security, and the company has a strong reputation for providing excellent customer support.
- Juniper Networks: Juniper Networks is another well-known company in the networking space, and is known for its high-performance routers, switches, and security products. Juniper's products are known for their stability and reliability, and the company has a strong focus on security, making it a good choice for organizations that prioritize security.
- Palo Alto Networks: Palo Alto Networks is a company that specializes in network security and is known for its firewalls, security appliances, and other security products. Palo Alto's products are known for their reliability and performance, and the company has a strong focus on threat prevention and detection, making it a good choice for organizations that need strong security protections.
- Fortinet: Fortinet is another company that specializes in network security, and is known for its firewalls, security appliances, and other security products. Fortinet's products are known for their reliability and performance, and the company has a strong focus on threat prevention and detection, making it a good choice for organizations that prioritize security.
All of these companies have a strong reputation for providing stable and reliable products and services for networking and proxy needs. The best company to partner with will depend on the specific needs and priorities of your organization, so it's important to evaluate each company carefully and choose the one that is the best fit for your needs.
It is possible to pick products from different companies to establish a network. Many organizations choose to do this to build a network that best fits their specific needs and requirements.
When selecting products from different companies, it's important to ensure that they are compatible with each other and will work together seamlessly. This may require additional configuration and integration work to ensure that the various products can communicate and share information effectively.
It's also important to ensure that the products selected from each company meet the security and performance requirements of the organization. This may involve researching each product and evaluating its capabilities, features, and security protocols.
In summary, it is possible to mix and match products from different companies to establish a network, but it's important to ensure that the products selected are compatible with each other and meet the needs and requirements of the organization.
A Comprehensive Guide to Cisco Network Protocols: From Basics to Advanced
Sanjay K Mohindroo
In today's technologically advanced world, networking plays a vital role in the success of any business or organization. Cisco, as one of the world's leading networking technology providers, offers a wide range of network protocols that are essential for managing and maintaining a network. This guide will provide an in-depth understanding of Cisco network protocols for IT leaders and networking professionals who want to gain a comprehensive knowledge of Cisco networking. In this article, we will list and explain the various Cisco network protocols that IT networking folks and IT leadership need to be aware of.
- Routing Protocols: Routing protocols are used to enable routers to communicate with each other and determine the best path for data transmission. Cisco offers three primary routing protocols:
- Routing Information Protocol (RIP): a distance-vector protocol that sends the entire routing table to its neighbors every 30 seconds.
- Open Shortest Path First (OSPF): a link-state protocol that exchanges link-state advertisements to construct a topology map of the network.
- Enhanced Interior Gateway Routing Protocol (EIGRP): a hybrid protocol that uses both distance-vector and link-state algorithms to determine the best path.
- Switching Protocols: Switching protocols are used to forward data packets between different network segments. Cisco offers two primary switching protocols:
- Spanning Tree Protocol (STP): a protocol that prevents network loops by shutting down redundant links.
- VLAN Trunking Protocol (VTP): a protocol that synchronizes VLAN configuration information between switches.
- Wide Area Network (WAN) Protocols: WAN protocols are used to connect remote networks over a wide geographic area. Cisco offers two primary WAN protocols:
- Point-to-Point Protocol (PPP): a protocol used to establish a direct connection between two devices over a serial link.
- High-Level Data Link Control (HDLC): a protocol used to encapsulate data over serial links.
- Security Protocols: Security protocols are used to secure the network and prevent unauthorized access. Cisco offers two primary security protocols:
- Internet Protocol Security (IPSec): a protocol used to secure IP packets by encrypting them.
- Secure Sockets Layer (SSL): a protocol used to establish a secure connection between a client and a server.
- Multi-Protocol Label Switching (MPLS): MPLS is a protocol used to optimize the speed and efficiency of data transmission. It uses labels to forward packets instead of IP addresses, which allows for faster routing and less congestion on the network.
- Border Gateway Protocol (BGP): BGP is a protocol used to route data between different autonomous systems (AS). It is commonly used by internet service providers to exchange routing information.
- Hot Standby Router Protocol (HSRP): HSRP is a protocol used to provide redundancy for IP networks. It allows for two or more routers to share a virtual IP address, so if one router fails, the other can take over seamlessly.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. It is commonly used in voice and video applications to prevent latency and ensure high-quality transmission.
In conclusion, Cisco network protocols are essential for maintaining and managing a network. Understanding these protocols is crucial for IT networking folks and IT leadership. By implementing Cisco network protocols, organizations can ensure that their network is secure, efficient, and reliable. Relevant examples and case studies can provide a better understanding of how these protocols work in real-life scenarios.
Examples of some of the Cisco network protocols mentioned in the article.
- Routing Protocols: Let's take a look at OSPF, which is a link-state protocol that exchanges link-state advertisements to construct a topology map of the network. This protocol is commonly used in enterprise networks to provide faster convergence and better scalability. For example, if there is a link failure in the network, OSPF routers can quickly recalculate the best path and update the routing table, ensuring that data is still transmitted efficiently.
- Switching Protocols: The Spanning Tree Protocol (STP) is a protocol that prevents network loops by shutting down redundant links. It works by selecting a single active path and blocking all other redundant paths, ensuring that there is no possibility of a loop forming. For example, if there are two switches connected via multiple links, STP will identify the shortest path and block the other links to prevent broadcast storms or other network issues.
- Wide Area Network (WAN) Protocols: The Point-to-Point Protocol (PPP) is a protocol used to establish a direct connection between two devices over a serial link. PPP provides authentication, compression, and error detection features, making it an ideal protocol for connecting remote sites. For example, if a company has a branch office in a remote location, it can use PPP to connect the remote site to the main office via a leased line.
- Security Protocols: Internet Protocol Security (IPSec) is a protocol used to secure IP packets by encrypting them. This protocol provides confidentiality, integrity, and authentication features, making it an ideal choice for securing data transmissions over the Internet. For example, if an organization needs to send sensitive data over the internet, it can use IPSec to encrypt the data, ensuring that it cannot be intercepted or modified by unauthorized parties.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. For example, if an organization is running voice and video applications on their network, they can use QoS to prioritize that traffic over other less critical traffic, ensuring that no latency or jitter could impact the quality of the transmission.
These are just a few examples of how Cisco network protocols work in real-life scenarios. By understanding how these protocols work and implementing them correctly, organizations can ensure that their network is secure, efficient, and reliable.
Here are some examples of how organizations can implement Cisco network protocols in their network infrastructure:
- Routing Protocols: An organization can implement the OSPF protocol by configuring OSPF on their routers and setting up areas to control network traffic. They can also use OSPF to optimize the path selection between routers by configuring the cost of the links based on bandwidth and delay.
- Switching Protocols: To implement the Spanning Tree Protocol (STP), an organization can configure STP on their switches to prevent network loops. They can also use Rapid Spanning Tree Protocol (RSTP) or Multiple Spanning Tree Protocol (MSTP) to reduce the convergence time and improve network performance.
- Wide Area Network (WAN) Protocols: An organization can implement the Point-to-Point Protocol (PPP) by configuring PPP on their routers to establish a direct connection between two devices over a serial link. They can also use PPP with authentication, compression, and error detection features to improve the security and efficiency of their network.
- Security Protocols: To implement the Internet Protocol Security (IPSec) protocol, an organization can configure IPSec on their routers and firewalls to encrypt data transmissions and provide secure communication over the Internet. They can also use IPSec with digital certificates to authenticate users and devices.
- Quality of Service (QoS): An organization can implement Quality of Service (QoS) by configuring QoS on their switches and routers to prioritize network traffic. They can also use QoS with Differentiated Services Code Point (DSCP) to classify and prioritize traffic based on its type and importance.
These are just a few examples of how organizations can implement Cisco network protocols in their network infrastructure. By implementing these protocols correctly, organizations can ensure that their network is secure, efficient, and reliable, providing the necessary tools to support business-critical applications and services.
Here's a tutorial on how to configure some of the Cisco network protocols on routers and switches.
- Routing Protocols:
Step 1: Enable the routing protocol on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the router ID and set up the interfaces by using the "router ospf" command.
Step 3: Set up the areas to control network traffic by using the "area" command.
Step 4: Configure the cost of the links based on bandwidth and delay by using the "ip ospf cost" command.
Step 5: Verify the OSPF configuration by using the "show ip ospf" command.
- Switching Protocols:
Step 1: Enable the Spanning Tree Protocol (STP) on the switch by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the bridge priority by using the "spanning-tree vlan [vlan-id] root" command.
Step 3: Set up the port priority and cost by using the "spanning-tree vlan [vlan-id] [port-id] priority [priority]" and "spanning-tree vlan [vlan-id] [port-id] cost [cost]" commands.
Step 4: Verify the STP configuration by using the "show spanning tree" command.
- Wide Area Network (WAN) Protocols:
Step 1: Enable the Point-to-Point Protocol (PPP) on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the PPP authentication by using the "ppp authentication [chap/pap]" command.
Step 3: Set up the PPP options by using the "ppp multilink" and "ppp multilink fragment delay [delay]" commands.
Step 4: Verify the PPP configuration by using the "show ppp multilink" command.
- Security Protocols:
Step 1: Enable the Internet Protocol Security (IPSec) protocol on the router or firewall by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the crypto map and set up the IP address and the pre-shared key by using the "crypto map [map-name] [seq-num] ipsec-isakmp" and "set peer [peer-address] key [pre-shared-key]" commands.
Step 3: Configure the access list to specify the traffic to be encrypted by using the "access-list [acl-number] permit [source-address] [destination-address]" command.
Step 4: Verify the IPSec configuration by using the "show crypto map" command.
- Quality of Service (QoS):
Step 1: Enable the Quality of Service (QoS) on the switch or router by entering the configuration mode using the "configure terminal" command.
Step 2: Set up the class map and the match criteria by using the "class-map [class-name]" and "match [criteria]" commands.
Step 3: Configure the policy map and the traffic shaping by using the "policy-map [policy-name]" and "shape average [bandwidth]" commands.
Step 4: Apply the QoS policy to the interface by using the "service-policy output [policy-name]" command.
Step 5: Verify the QoS configuration by using the "show policy-map interface [interface-name]" command.
These are just some basic steps for configuring some of the Cisco network protocols on routers and switches. Depending on your specific network requirements, you may need to configure additional settings or features. Always make sure to test and verify your configuration to ensure that it is working as expected.
Cisco's networking devices, such as routers and switches, run on an operating system (OS) called Cisco IOS (Internetwork Operating System). IOS is a proprietary OS that is specifically designed to run on Cisco's networking hardware.
IOS provides the networking infrastructure with a wide range of features, including routing, switching, and security protocols. It also includes a command-line interface (CLI) that allows administrators to configure and manage the device's settings.
One of the key advantages of IOS is its modular design, which allows administrators to customize the OS by adding or removing specific features as needed. This modularity provides flexibility in managing the network devices and helps to keep the OS streamlined and efficient.
In addition to the traditional IOS, Cisco also offers a range of specialized operating systems for specific devices or environments, such as IOS XR for service provider networks or IOS XE for enterprise networks.
Overall, IOS is a reliable and flexible operating system that has been proven to be effective in managing and securing Cisco's networking devices. Its CLI is widely used by network administrators around the world, making it a valuable tool for managing networks of all sizes and complexities.
I can provide an extensive list of all the commands used in Cisco IOS, but it would not be feasible to explain every command in detail as it would require a significant amount of time and space. Instead, I can provide an overview of some of the essential commands used in Cisco IOS and their functions:
- enable: This command enables privileged mode, which provides access to configuration commands and advanced system settings.
- show: This command displays information about the system configuration, interface status, and device performance.
- configure terminal: This command enters global configuration mode, which allows users to configure the device settings and protocols.
- interface: This command configures individual interfaces on the device, such as Ethernet or serial ports.
- ip address: This command assigns IP addresses to network interfaces.
- hostname: This command sets the device hostname, which is used for identification purposes.
- ping: This command sends ICMP packets to test network connectivity.
- traceroute: This command traces the path that packets take from the source to the destination.
- Access list: This command configures access control lists to control traffic flow and filter packets.
- shutdown: This command disables an interface or a protocol.
- reload: This command reloads the device, which is useful for resetting configurations or troubleshooting issues.
These commands are just a few examples of the many commands available in Cisco IOS. Each command has specific syntax and options, and it's essential to use them correctly to avoid configuration errors and network issues. Cisco provides extensive documentation and training resources for users to learn about the commands and their functions. Network administrators must understand the basics of IOS commands to effectively manage and maintain their networks.
The Evolution and Future of Networking: Connecting the World

Networking has revolutionized the way we connect. From the telegraph to 5G, we explore its history, present, and future.
In today's digital age, networking has become an integral part of our daily lives. From social media platforms to online banking, we rely on networks to connect us to people and information from around the world. In this blog, we will discuss the history, evolution, present stage, and future of networking, and how it has impacted individuals, businesses, and governments.
The evolution of networking has been one of the most transformative technological advancements in modern history. Today, networking plays an integral role in the way we communicate, conduct business, and connect. In this blog, we will explore the history, evolution, present stage, and future of networking, and highlight how networks are part of our daily lives.
History and Evolution
Networking has come a long way since the early days of communication. In the late 1800s, telegraph systems were used to transmit messages across long distances. This was followed by the telephone, which revolutionized communication by allowing people to talk to each other in real time, regardless of their location. In the mid-20th century, computer networks were developed, allowing computers to communicate with each other over long distances.
The advent of the internet in the 1990s brought about a new era of networking. The internet allowed people to connect on a global scale, and the development of the World Wide Web made it easy to access information and services from anywhere in the world. The growth of social media platforms, mobile devices, and cloud computing has further accelerated the evolution of networking.
Present Stage
Today, networking is an essential part of our daily lives. We use networks to communicate with friends and family, access information and entertainment, conduct business, and even control our homes. Social media platforms like Facebook, Twitter, and Instagram allow us to connect with people around the world and share our experiences. Mobile devices like smartphones and tablets have made it easy to stay connected on the go, while cloud computing has made it possible to access data and services from anywhere in the world.
Businesses and governments also rely heavily on networking to operate efficiently. Networks allow businesses to connect with customers, partners, and suppliers around the world, and to collaborate on projects in real time. Governments use networks to communicate with citizens, manage infrastructure, and provide essential services like healthcare and education.
Future
The future of networking is bright, with new technologies promising to bring about even more transformative changes. One of the most exciting developments is the emergence of 5G networks, which will offer faster speeds, lower latency, and greater reliability than current networks. This will enable new applications like autonomous vehicles, virtual and augmented reality, and smart cities.
Other emerging technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain are also poised to revolutionize networking. IoT devices will enable the creation of smart homes, smart cities, and even smart factories, while AI will help us better manage and analyze the vast amounts of data generated by these devices. Blockchain technology, on the other hand, will enable secure and transparent transactions between parties, without the need for intermediaries.
Conclusion
In conclusion, networking has come a long way since its early days, and it has become an essential part of our daily lives. Networks have helped individuals connect, businesses operate efficiently, and governments provide essential services. As we look to the future, new technologies promise to bring about even more transformative changes, and it is an exciting time to be part of the networking industry.
The advancements in networking technology have made our lives simpler and more effective. They have enabled us to access information, communicate with each other, and carry out transactions from anywhere in the world. Networking technology has also facilitated the growth of e-commerce, allowing businesses to sell products and services online and reach customers across the globe.
In addition, networking technology has made it easier to work remotely and collaborate with colleagues in different locations. This has become particularly important in the wake of the COVID-19 pandemic, which has forced many businesses and individuals to work from home.
The benefits of networking technology are not limited to individuals and businesses. Governments have also been able to leverage networking technology to provide essential services to citizens. For example, telemedicine has made it possible for people to receive medical care remotely, while e-learning platforms have made education more accessible to people around the world.
There are many different types of networks, but some of the most common ones include:
- Local Area Network (LAN): A LAN is a network that connects devices in a small geographical area, such as a home, office, or school. It typically uses Ethernet cables or Wi-Fi to connect devices and is often used for file sharing and printing.
- Wide Area Network (WAN): A WAN is a network that connects devices across a larger geographical area, such as multiple cities or even countries. It uses a combination of technologies such as routers, switches, and leased lines to connect devices and is often used for communication between different branches of a company.
- Metropolitan Area Network (MAN): A MAN is a network that covers a larger area than a LAN but is smaller than a WAN, such as a city or a campus. It may use technologies such as fiber optic cables or microwave links to connect devices.
- Personal Area Network (PAN): A PAN is a network that connects devices within a personal space, such as a smartphone or tablet to a wearable device like a smartwatch or fitness tracker.
- Wireless Local Area Network (WLAN): A WLAN is a LAN that uses wireless technology such as Wi-Fi to connect devices.
- Storage Area Network (SAN): A SAN is a specialized network that provides access to storage devices such as disk arrays and tape libraries.
- Virtual Private Network (VPN): A VPN is a secure network that uses encryption and authentication technologies to allow remote users to access a private network over the internet.
- Cloud Network: A cloud network is a network of servers and storage devices hosted by a cloud service provider, which allows users to access data and applications over the internet from anywhere.
These are just a few examples of the many types of networks that exist. The type of network that is appropriate for a particular application will depend on factors such as the size and location of the network, the type of devices being connected, and the level of security required.
Several different types of network architectures can be used to design and implement networks. Some of the most common types include:
- Client-Server Architecture: In a client-server architecture, one or more central servers provide services to multiple client devices. The clients access these services over the network, and the servers manage the resources and data.
- Peer-to-Peer Architecture: In a peer-to-peer architecture, devices on the network can act as both clients and servers, with no central server or authority. This allows devices to share resources and communicate with each other without relying on a single server.
- Cloud Computing Architecture: In a cloud computing architecture, services and applications are hosted on servers located in data centers operated by cloud service providers. Users access these services over the internet, and the cloud provider manages the infrastructure and resources.
- Distributed Architecture: In a distributed architecture, multiple servers are used to provide services to clients, with each server handling a specific function. This provides redundancy and fault tolerance, as well as better scalability.
- Hierarchical Architecture: In a hierarchical architecture, devices are organized into a tree-like structure, with a central node or root at the top, followed by intermediary nodes, and finally end devices at the bottom. This allows for efficient communication and management of devices in larger networks.
- Mesh Architecture: In a mesh architecture, devices are connected in a non-hierarchical, mesh-like topology, with multiple paths for communication between devices. This provides high fault tolerance and resilience, as well as better scalability.
- Virtual Private Network (VPN) Architecture: In a VPN architecture, devices in a network are connected over an encrypted tunnel, allowing users to access a private network over the internet securely.
Each type of network architecture has its advantages and disadvantages, and the appropriate architecture will depend on the specific needs and requirements of the network.
There are many different network protocols used for communication between devices in a network. Some of the most common types of network protocols include:
- Transmission Control Protocol (TCP): A protocol that provides reliable and ordered delivery of data over a network, ensuring that data is delivered without errors or loss.
- User Datagram Protocol (UDP): A protocol that provides a connectionless service for transmitting data over a network, without the reliability guarantees of TCP.
- Internet Protocol (IP): A protocol that provides the addressing and routing functions necessary for transmitting data over the internet.
- Hypertext Transfer Protocol (HTTP): A protocol used for transmitting web pages and other data over the internet.
- File Transfer Protocol (FTP): A protocol used for transferring files between computers over a network.
- Simple Mail Transfer Protocol (SMTP): A protocol used for transmitting email messages over a network.
- Domain Name System (DNS): A protocol used for translating domain names into IP addresses, allowing devices to locate each other on the internet.
- Dynamic Host Configuration Protocol (DHCP): A protocol used for dynamically assigning IP addresses to devices on a network.
- Secure Shell (SSH): A protocol used for secure remote access to a network device.
- Simple Network Management Protocol (SNMP): A protocol used for monitoring and managing network devices.
These are just a few examples of the many types of network protocols that exist. Different protocols are used for different purposes, and the appropriate protocol will depend on the specific needs of the network and the devices being used.
Each network protocol serves a specific purpose in facilitating communication between devices in a network. Here are some of the most common uses of the network protocols:
- Transmission Control Protocol (TCP): TCP is used for reliable and ordered delivery of data over a network, making it ideal for applications that require high levels of accuracy and completeness, such as file transfers or email.
- User Datagram Protocol (UDP): UDP is used when speed is more important than reliability, such as for video streaming, real-time gaming, and other applications that require fast response times.
- Internet Protocol (IP): IP is used for addressing and routing packets of data across the internet, enabling devices to find and communicate with each other.
- Hypertext Transfer Protocol (HTTP): HTTP is used for transmitting web pages and other data over the internet, making it the protocol of choice for browsing the World Wide Web.
- File Transfer Protocol (FTP): FTP is used for transferring files between computers over a network, making it a common protocol for sharing files between users or transferring files to a web server.
- Simple Mail Transfer Protocol (SMTP): SMTP is used for transmitting email messages over a network, enabling users to send and receive emails from different devices and email clients.
- Domain Name System (DNS): DNS is used for translating domain names into IP addresses, allowing devices to locate each other on the internet.
- Dynamic Host Configuration Protocol (DHCP): DHCP is used for dynamically assigning IP addresses to devices on a network, enabling devices to connect to a network and communicate with other devices.
- Secure Shell (SSH): SSH is used for secure remote access to a network device, enabling users to log in to a device from a remote location and perform administrative tasks.
- Simple Network Management Protocol (SNMP): SNMP is used for monitoring and managing network devices, enabling administrators to monitor device performance, configure devices, and troubleshoot issues.
In summary, network protocols play a critical role in enabling communication and data transfer between devices in a network. Each protocol has its specific purpose, and the appropriate protocol will depend on the specific needs of the network and the devices being used.
The protocols used in different network architectures can vary depending on the specific implementation and requirements of the network. Here are some examples of protocols commonly used in different network architectures:
- Client-Server Architecture: Protocols such as TCP, UDP, HTTP, SMTP, and FTP are commonly used in client-server architecture to enable communication between clients and servers.
- Peer-to-Peer Architecture: Peer-to-peer networks often use protocols such as BitTorrent, Direct Connect (DC), and Gnutella to facilitate file sharing and communication between devices.
- Cloud Computing Architecture: Cloud computing often relies on protocols such as HTTP, HTTPS, and REST (Representational State Transfer) to enable communication between clients and cloud services.
- Distributed Architecture: Distributed systems often use protocols such as Remote Procedure Call (RPC), Distributed Component Object Model (DCOM), and Message Passing Interface (MPI) to enable communication between different servers in the network.
- Hierarchical Architecture: Hierarchical networks often use protocols such as Simple Network Management Protocol (SNMP) to enable the management and monitoring of devices in the network.
- Mesh Architecture: Mesh networks often use protocols such as Ad-hoc On-demand Distance Vector (AODV), Dynamic Source Routing (DSR), and Optimized Link State Routing (OLSR) to enable communication between devices in the network.
- Virtual Private Network (VPN) Architecture: VPNs often use protocols such as Internet Protocol Security (IPsec), Secure Socket Layer (SSL), and Transport Layer Security (TLS) to provide secure and encrypted communication between devices.
These are just a few examples of the many protocols used in different network architectures. The appropriate protocol will depend on the specific needs and requirements of the network, as well as the devices and applications being used.
Here are some common networking technologies and a brief explanation of each:
- Ethernet: As explained earlier, Ethernet is a wired networking technology commonly used in local area networks (LANs) to transmit data packets between computers and other network devices over a physical network cable.
- Wi-Fi: Wi-Fi is a wireless networking technology that uses radio waves to connect devices to the internet or a local network without the need for physical cables. Wi-Fi networks are commonly used in homes, offices, public spaces, and other locations.
- Bluetooth: Bluetooth is a wireless networking technology used for short-range communication between devices, typically within a range of 10 meters. Bluetooth is commonly used for connecting wireless headphones, speakers, keyboards, and other devices to smartphones, tablets, and computers.
- NFC (Near Field Communication): NFC is a short-range wireless communication technology that allows two devices to exchange data when they are close to each other. NFC is commonly used for contactless payments, ticketing, and other applications.
- Cellular Networks: Cellular networks are wireless networking technologies used to connect mobile devices such as smartphones and tablets to the internet or a cellular network provider. These networks use radio waves to communicate between mobile devices and cellular network towers.
- VPN (Virtual Private Network): VPN is a technology that allows users to securely connect to a private network over the internet. VPNs use encryption and other security measures to protect data transmitted over the network, making them useful for remote workers, travelers, and others who need to access private networks from outside the organization.
- DNS (Domain Name System): DNS is a technology used to translate human-readable domain names (such as google.com) into IP addresses used by computers and other devices to connect to websites and services over the internet.
These are just a few examples of the many networking technologies available today. The appropriate technology will depend on the specific needs and requirements of the network and the devices being used.
Here are some common wired networking technologies and a brief explanation of each:
- Ethernet: Ethernet is a wired networking technology commonly used in local area networks (LANs) to transmit data packets between computers and other network devices over a physical network cable. Ethernet supports various speeds ranging from 10 Mbps to 100 Gbps or more.
- Fiber Optics: Fiber optics is a wired networking technology that uses glass or plastic fibers to transmit data over long distances at high speeds. Fiber optic cables are capable of transmitting data at speeds of up to 100 Gbps or more and are commonly used in internet backbone networks, data centers, and other high-speed networking applications.
- Coaxial Cable: Coaxial cable is a wired networking technology that uses a copper core surrounded by a shield to transmit data between devices. Coaxial cables are commonly used in cable television (CATV) networks and some older LANs.
- Powerline Networking: Powerline networking is a wired networking technology that uses existing electrical wiring to transmit data between devices. Powerline adapters plug into electrical outlets and use the wiring in the walls to transmit data at speeds of up to 2 Gbps.
- Ethernet over HDMI (EOH): EOH is a wired networking technology that uses HDMI cables to transmit Ethernet data between devices. EOH is commonly used in home theater systems and other applications that require high-speed data transfer over short distances.
- USB Networking: USB networking is a wired networking technology that uses USB cables to connect devices and transfer data between them. USB networking is commonly used to connect peripherals such as printers and external hard drives to computers.
These are just a few examples of the many wired networking technologies available today. The appropriate technology will depend on the specific needs and requirements of the network and the devices being used.
Ethernet is a family of wired networking technologies commonly used in local area networks (LANs). It is a standard for transmitting data packets between computers and other network devices over a physical network cable.
Ethernet was originally developed by Xerox Corporation in the 1970s, and it has since become a widely used technology in networking. Ethernet uses a protocol called the Ethernet protocol to transmit data packets over the network.
Ethernet networks typically use twisted pairs or fiber optic cables to transmit data between devices. These cables connect to a network switch or hub, which manages the traffic between devices.
Ethernet networks can support various speeds, ranging from 10 Mbps (megabits per second) to 100 Gbps (gigabits per second) or more. The most common Ethernet speeds used today are 10/100/1000 Mbps, also known as Gigabit Ethernet.
Ethernet is used in many different types of networks, including home and office networks, data centers, and internet service provider (ISP) networks. It is a reliable and widely adopted technology that has enabled the growth and development of modern computer networks.
Here are some fiber networking technologies with explanations:
- Fiber to the Home (FTTH): FTTH is a type of fiber networking technology that delivers high-speed internet, TV, and phone services directly to homes and businesses. FTTH uses optical fiber cables to transmit data at extremely high speeds, enabling users to enjoy reliable and fast connectivity.
- Fiber to the Building (FTTB): FTTB is similar to FTTH, but instead of connecting individual homes, it connects multiple units or businesses within a building to a fiber network. This technology is commonly used in multi-tenant buildings, such as apartments or offices.
- Fiber to the Curb (FTTC): FTTC uses fiber-optic cables to connect to a neighborhood's central distribution point or cabinet, and then uses copper wires to connect to individual homes or businesses. This technology is used to provide high-speed internet services to suburban areas.
- Passive Optical Network (PON): PON is a fiber networking technology that uses a single optical fiber cable to provide high-speed internet, TV, and phone services to multiple users. PON is a cost-effective solution for delivering high-speed connectivity to a large number of users in a single network.
- Dense Wavelength Division Multiplexing (DWDM): DWDM is a fiber networking technology that allows multiple wavelengths of light to be transmitted over a single optical fiber cable. This technology enables high-capacity transmission of data over long distances, making it ideal for applications such as telecommunications, data centers, and long-distance networking.
- Gigabit Passive Optical Network (GPON): GPON is a type of PON that uses a single optical fiber cable to provide high-speed internet, TV, and phone services to multiple users. GPON is capable of delivering data rates of up to 2.5 Gbps, making it an attractive solution for high-bandwidth applications.
These are just a few examples of fiber networking technologies, each with its strengths and weaknesses. The appropriate technology will depend on the specific application, location, and budget.
Here are some types of fiber networking with explanations:
- Single-mode fiber (SMF): Single-mode fiber is an optical fiber designed to carry a single ray of light, or mode, over long distances. It has a small core diameter, typically 8-10 microns, and is capable of transmitting data at extremely high speeds over long distances with minimal signal loss. SMF is commonly used in long-distance telecommunications and data center applications.
- Multimode fiber (MMF): Multimode fiber is an optical fiber designed to carry multiple modes of light simultaneously. It has a larger core diameter, typically 50 or 62.5 microns, and is capable of transmitting data over shorter distances than single-mode fiber. MMF is commonly used in local area networks (LANs) and other short-distance applications.
- Plastic optical fiber (POF): Plastic optical fiber is made of polymer materials rather than glass. POF has a larger core diameter than glass fiber, typically 1mm, and is capable of transmitting data at lower speeds over shorter distances. POF is commonly used in automotive and home networking applications.
- Active Optical Cable (AOC): Active Optical Cable is a type of fiber optic cable that integrates optical and electrical components to provide high-speed data transfer over longer distances than copper cables. AOC typically uses multimode fiber and is commonly used in data centers and high-performance computing applications.
- Fiber Distributed Data Interface (FDDI): FDDI is a high-speed networking technology that uses a ring topology to transmit data over optical fiber cables. FDDI is capable of transmitting data at speeds of up to 100 Mbps and is commonly used in mission-critical applications, such as banking and government networks.
These are just a few examples of fiber networking types, each with its advantages and disadvantages. The appropriate type will depend on the specific application, location, and budget.
Here are some common uses of different types of fiber networking:
- Single-mode fiber: Single-mode fiber is commonly used in long-distance telecommunications applications, such as transmitting data between cities or countries. It is also used in data centers for high-speed interconnects and storage area networks.
- Multimode fiber: Multimode fiber is commonly used in local area networks (LANs) and other short-distance applications. It is also used in data centers for high-speed interconnects and fiber channel storage area networks.
- Plastic optical fiber: Plastic optical fiber is commonly used in automotive and home networking applications, such as transmitting audio and video signals between devices.
- Active Optical Cable: Active Optical Cable is commonly used in data centers for high-speed interconnects and storage area networks. It is also used in high-performance computing applications, such as supercomputing and machine learning.
- Fiber Distributed Data Interface: FDDI is commonly used in mission-critical applications, such as banking and government networks, as well as in high-speed data center interconnects.
Overall, fiber networking is used in a wide range of applications where high-speed, reliable, and secure data transmission is required. Whether it's transmitting data across continents, connecting devices in a home network, or powering a supercomputer, fiber networking plays a critical role in modern communication and computing systems.
Here are some common wireless networking technologies and a brief explanation of each:
- Wi-Fi: Wi-Fi is a wireless networking technology that uses radio waves to connect devices to the internet or a local network without the need for physical cables. Wi-Fi networks are commonly used in homes, offices, public spaces, and other locations. Wi-Fi operates in frequency bands ranging from 2.4 GHz to 5 GHz, with different Wi-Fi standards supporting different speeds and features.
- Bluetooth: Bluetooth is a wireless networking technology used for short-range communication between devices, typically within a range of 10 meters. Bluetooth is commonly used for connecting wireless headphones, speakers, keyboards, and other devices to smartphones, tablets, and computers. Bluetooth uses the 2.4 GHz frequency band.
- NFC (Near Field Communication): NFC is a short-range wireless communication technology that allows two devices to exchange data when they are close to each other. NFC is commonly used for contactless payments, ticketing, and other applications. NFC operates at 13.56 MHz.
- Cellular Networks: Cellular networks are wireless networking technologies used to connect mobile devices such as smartphones and tablets to the internet or a cellular network provider. These networks use radio waves to communicate between mobile devices and cellular network towers. Cellular networks operate in various frequency bands depending on the network provider.
- Zigbee: Zigbee is a wireless networking technology commonly used in home automation and Internet of Things (IoT) devices. Zigbee operates in the 2.4 GHz and 900 MHz frequency bands and is designed for low-power and low-data-rate applications.
- Z-Wave: Z-Wave is a wireless networking technology similar to Zigbee, used in home automation and IoT devices. Z-Wave operates in the 900 MHz frequency band and is designed for low-power and low-data-rate applications.
These are just a few examples of the many wireless networking technologies available today. The appropriate technology will depend on the specific needs and requirements of the network and the devices being used.
Here are some networking technologies used for communication in space exploration:
- Deep Space Network (DSN): The Deep Space Network is a network of radio antennas located in three different locations on Earth (California, Spain, and Australia) and is operated by NASA's Jet Propulsion Laboratory (JPL). DSN is used to communicate with and receive data from spacecraft exploring our solar system and beyond.
- Laser Communication Relay Demonstration (LCRD): LCRD is a NASA project that aims to test the use of laser communication technology for communication between spacecraft in deep space. Laser communication has the potential to transmit data at much higher speeds than radio communication.
- Tracking and Data Relay Satellite (TDRS): TDRS is a network of communication satellites operated by NASA that provides continuous communication coverage to spacecraft in low-Earth orbit. TDRS satellites are used to relay data between the spacecraft and ground stations on Earth.
- Interplanetary Internet: The Interplanetary Internet is a communication system being developed by NASA that will enable communication between spacecraft and rovers exploring other planets and moons in our solar system. This system is designed to be resilient to the high latency and intermittent connectivity of deep-space communication.
These are just a few examples of the many networking technologies used for communication in space exploration. The appropriate technology will depend on the specific mission requirements and the distance and location of the spacecraft or rovers.
Here is a comparison of the space communication technologies mentioned earlier:
- Deep Space Network (DSN): Pros:
- Established and reliable technology
- Can communicate with multiple spacecraft simultaneously
- Supports a wide range of frequencies for communication
Cons:
- Limited bandwidth and data rates compared to newer technologies
- Long latency due to the distance between Earth and deep space spacecraft
- Limited coverage area and sensitivity to atmospheric conditions
- Laser Communication Relay Demonstration (LCRD): Pros:
- High data rates and bandwidth compared to radio communication
- More resilient to interference and jamming
- Can potentially reduce the size and weight of communication equipment on spacecraft
Cons:
- Requires line-of-sight communication and precise pointing of the laser beam
- Sensitive to atmospheric conditions and space debris
- Technology is still in development and not yet widely adopted
- Tracking and Data Relay Satellite (TDRS): Pros:
- Continuous communication coverage for low-Earth orbit spacecraft
- Supports high data rates and bandwidth
- Established and reliable technology
Cons:
- Limited coverage area outside of the low-Earth orbit
- It is costly to maintain and replace satellites
- Sensitive to atmospheric conditions and space debris
- Interplanetary Internet: Pros:
- Designed to be resilient to high latency and intermittent connectivity
- Supports a wide range of data rates and bandwidth
- Can potentially improve communication efficiency and reliability
Cons:
- Technology is still in development and not yet widely adopted
- Requires significant investment and infrastructure
- Limited coverage area and sensitivity to atmospheric conditions
In terms of the best approach for space communication, depends on the specific mission requirements and constraints. Each technology has its strengths and weaknesses, and the appropriate technology will depend on distance, location, data rates, bandwidth, and reliability requirements. For example, the Deep Space Network may be more appropriate for long-range communication with multiple spacecraft, while laser communication may be more suitable for high-bandwidth communication over shorter distances. Ultimately, a combination of these technologies may be used to provide a comprehensive communication network for space exploration.
In conclusion, networking technology has come a long way since its early days, and it has had a profound impact on our daily lives. As we look to the future, new technologies will continue to emerge, offering even greater benefits and transforming the way we live, work, and communicate with each other.
The Evolution of Programming Languages: Past, Present, and Future

Programming has come a long way since its inception in the 19th century, with new technologies and innovations driving its evolution. In this blog, we explore the history of programming, the types of programming languages, the future of programming, the role of AI in programming, and the role of popular IDEs in modern programming.
Programming is important because it enables us to create software, websites, mobile apps, games, and many other digital products that we use in our daily lives. It allows us to automate tasks, solve complex problems, and create innovative solutions that improve our lives and businesses. In today's digital age, programming skills are in high demand and are essential for success in many industries, from tech to finance to healthcare. By learning to code, we can open up a world of opportunities and take advantage of the many benefits that technology has to offer.
Initially, programming was done using punch cards and it was a tedious and time-consuming task. But with the invention of computers, programming became more accessible and efficient. In this blog, we will take a closer look at the evolution of programming languages, the history of programming, types of programming languages, the future of programming, the role of AI in programming, and the role of IDEs popular for programming.
History of Programming
The history of programming dates back to the early 19th century when mathematician Ada Lovelace created an algorithm for Charles Babbage's Analytical Engine, which is considered the first computer. However, the first actual programming language was developed in the 1950s, called FORTRAN (Formula Translation). This language was used for scientific and engineering calculations.
In the 1960s, programming languages such as COBOL (Common Business-Oriented Language), BASIC (Beginners All-Purpose Symbolic Instruction Code), and ALGOL (Algorithmic Language) were developed. These languages were used to write applications for business and research.
The 1970s saw the development of languages such as C and Pascal, which were used to write operating systems and applications. In the 1980s, the first object-oriented language, Smalltalk, was created. This language allowed developers to create reusable code and was used for graphical user interfaces.
The 1990s saw the development of scripting languages such as Perl and Python, which were used for web development. In the early 2000s, languages such as Ruby and PHP became popular for web development. Today, programming languages such as Java, C++, Python, and JavaScript are widely used for various applications.
Logic plays a fundamental role in programming. Programming is essentially the process of writing instructions for a computer to follow, and these instructions must be logical and well-organized for the computer to execute them correctly.
Programming requires logical thinking and the ability to break down complex problems into smaller, more manageable parts. Programmers use logic to develop algorithms, which are step-by-step procedures for solving problems. These algorithms must be logical and accurate, with each step leading logically to the next.
In programming, logical operators and conditional statements are used to control the flow of a program. Logical operators such as AND, OR, and NOT are used to evaluate logical expressions and make decisions based on the results. Conditional statements such as IF, ELSE, and SWITCH are used to execute different parts of a program based on specific conditions.
Thus, logic is a critical component of programming. Without it, programs would not work correctly or produce the desired results. By developing strong logical thinking skills, programmers can write efficient and effective code that solves complex problems and meets the needs of users.
Types of Programming Languages
Programming languages can be broadly classified into three categories:
- Low-Level Languages: These languages are closer to the machine language and are used to write operating systems, device drivers, and firmware. Examples include Assembly Language, C, and C++.
- High-Level Languages: These languages are easier to learn and use than low-level languages. They are used to write applications, games, and websites. Examples include Java, Python, and Ruby.
- Scripting Languages: These languages are used to automate repetitive tasks, such as web development and system administration. Examples include Perl, Python, and Ruby.
Here is a list of programming languages and a brief explanation of each:
- Java: Java is a high-level, object-oriented programming language developed by Sun Microsystems (now owned by Oracle Corporation). Java is designed to be platform-independent, meaning that Java code can run on any computer with a Java Virtual Machine (JVM) installed. Java is widely used for developing web applications, mobile apps, and enterprise software.
- Python: Python is a high-level, interpreted programming language that emphasizes code readability and simplicity. Python is widely used for scientific computing, data analysis, web development, and artificial intelligence.
- C: C is a low-level, compiled programming language that is widely used for systems programming and embedded systems development. C is known for its efficiency and control over hardware, making it an ideal choice for developing operating systems, device drivers, and firmware.
- C++: C++ is an extension of the C programming language that adds support for object-oriented programming. C++ is widely used for developing high-performance software, including operating systems, games, and scientific simulations.
- JavaScript: JavaScript is a high-level, interpreted programming language that is widely used for developing web applications. JavaScript runs in web browsers and provides interactivity and dynamic behavior to web pages.
- Ruby: Ruby is a high-level, interpreted programming language that emphasizes simplicity and productivity. Ruby is widely used for web development, automation, and scripting.
- Swift: Swift is a high-level, compiled programming language developed by Apple Inc. Swift is designed for developing applications for iOS, macOS, and watchOS. Swift is known for its safety, speed, and expressiveness.
- PHP: PHP is a server-side, interpreted programming language that is widely used for developing web applications. PHP is known for its simplicity and ease of use, making it a popular choice for web developers.
- SQL: SQL (Structured Query Language) is a domain-specific language used for managing relational databases. SQL is used to create, modify, and query databases, and is widely used in business and data analysis.
- Assembly language: Assembly language is a low-level programming language that is used to write instructions for a computer's CPU. Assembly language is difficult to read and write, but provides direct access to hardware and can be used to write highly optimized code.
There are many other programming languages in use today, each with its strengths and weaknesses. Choosing the right programming language for a particular task depends on a variety of factors, including the requirements of the project, the developer's experience and expertise, and the availability of tools and libraries.
Here are some examples of low-level programming languages and a brief explanation of each:
- Machine Language: Machine language is the lowest-level programming language that a computer can understand. It is a binary code consisting of 0's and 1's that correspond to machine instructions. Each computer architecture has its specific machine language, which is difficult to read and write.
- Assembly Language: Assembly language is a low-level programming language that is easier to read and write than machine language. Assembly language uses mnemonics to represent machine instructions, making it more human-readable. Assembly language programs are translated into machine language by an assembler.
- C: C is a high-level programming language that can also be considered a low-level language due to its low-level memory access and pointer manipulation capabilities. C provides direct access to hardware, making it an ideal choice for systems programming and embedded systems development.
- Ada: Ada is a high-level programming language designed for safety-critical systems, such as aerospace and defense applications. Ada provides low-level access to hardware and memory management, making it suitable for systems programming.
- FORTRAN: FORTRAN (FORmula TRANslation) is a high-level programming language that was designed for scientific and engineering applications. FORTRAN provides low-level control over hardware, allowing for efficient computation and numerical analysis.
Low-level programming languages provide direct access to hardware and memory, allowing for precise control over system resources. However, they can be difficult to read and write and require a deep understanding of computer architecture. Low-level programming languages are often used for systems programming, device drivers, and embedded systems development, where performance and control are critical.
To become a good programmer, there are several key skills that you should develop:
- Logical thinking: Programming requires logical thinking, the ability to break down complex problems into smaller, manageable parts, and to develop algorithms to solve them.
- Attention to detail: Good programmers pay attention to detail, writing clean, efficient, and error-free code.
- Persistence: Programming can be challenging, and it often requires persistence and patience to debug and solve problems.
- Adaptability: Programming languages and technologies are constantly evolving, so good programmers must be adaptable and willing to learn new skills and techniques.
- Collaboration: Programming often involves working in teams, so good programmers must be able to collaborate effectively with others, share their ideas, and give and receive constructive feedback.
- Creativity: Programming can also be a creative process, requiring programmers to come up with innovative solutions to problems and to think outside the box.
By developing these skills and continuously learning and improving your programming abilities, you can become a successful and highly skilled programmer.
Future of Programming
The future of programming is bright, with new technologies such as artificial intelligence, machine learning, and the Internet of Things (IoT) driving innovation. With the increasing demand for intelligent applications and systems, programming languages such as Python and R, which are used for machine learning, are gaining popularity.
With the rise of low-code and no-code platforms, programming is becoming more accessible to non-programmers, enabling them to build simple applications without needing to write code. As technology advances, programming will likely become more intuitive and user-friendly, enabling anyone to create complex applications with ease.
Role of AI in Programming
Artificial intelligence is playing an increasingly important role in programming. AI is being used to automate various aspects of programming, such as code generation, testing, and debugging. With the help of machine learning algorithms, AI can learn from past code to predict and suggest solutions to programming problems.
AI is also being used to improve software development workflows, making it easier for developers to collaborate and manage code. For example, GitHub, a popular platform for hosting and sharing code, uses AI to provide code suggestions and automate workflows.
Role of IDEs Popular for Programming
Integrated Development Environments (IDEs) are software applications that provide developers with tools for writing, testing, and debugging code. IDEs are designed to streamline the development process, making it easier for developers to write code and manage their projects. Some of the most popular IDEs for programming include:
- Visual Studio Code: This IDE is a lightweight and powerful tool that supports many programming languages, including JavaScript, Python, and C++. It has built-in debugging, Git integration, and extensions that can enhance its functionality.
- IntelliJ IDEA: This IDE is designed for Java developers and provides advanced features such as code refactoring, code analysis, and debugging. It also supports other programming languages such as Python, Kotlin, and Scala.
- Eclipse: This IDE is an open-source platform that supports many programming languages, including Java, C++, and Python. It has a modular architecture, making it easy to customize and extend its functionality.
- Xcode: This IDE is designed for macOS and iOS development and supports languages such as Swift and Objective-C. It has a graphical user interface that allows developers to create interfaces and design layouts.
IDEs have become an essential tool for modern programming, allowing developers to write and manage code more efficiently. With the rise of AI and machine learning, IDEs are likely to become even more intelligent, providing developers with better code suggestions and automated workflows.
Here are some popular Integrated Development Environments (IDEs) and a brief explanation of each:
1. Eclipse: Eclipse is a popular open-source IDE for Java development, but it also supports many other programming languages, such as C++, Python, and PHP. Eclipse offers a wide range of plugins and extensions, making it highly customizable and extensible.
2. Visual Studio: Visual Studio is a popular IDE for Windows development, offering support for multiple programming languages, including C#, Visual Basic, and Python. Visual Studio offers many features, such as code editing, debugging, and profiling tools.
3. IntelliJ IDEA: IntelliJ IDEA is an IDE designed for Java development, offering features such as intelligent code completion, refactoring tools, and debugging capabilities. IntelliJ IDEA is known for its speed and productivity.
4. Xcode: Xcode is an IDE for macOS and iOS development, offering features such as a visual editor, debugging tools, and testing frameworks. Xcode also includes a wide range of templates and tools for developing Apple applications.
5. PyCharm: PyCharm is an IDE for Python development, offering features such as code completion, debugging, and testing tools. PyCharm also includes support for scientific computing and data analysis libraries.
Using an IDE effectively involves using its features and tools to streamline the development process and improve productivity. Here are some tips for using an IDE effectively:
1. Customize your environment: Take advantage of the customization options available in your IDE, such as keyboard shortcuts, color schemes, and code templates. This can help you work more efficiently and reduce distractions.
2. Use code completion: Most IDEs offer code completion features, which can save you time and reduce errors by suggesting code as you type.
3. Debug effectively: Use the debugging tools in your IDE to identify and fix errors in your code. Learn how to set breakpoints, step through code, and inspect variables to find the root cause of problems.
4. Use version control: IDEs often offer integration with version control systems such as Git. Learning how to use version control effectively can help you collaborate with other developers, manage changes to your codebase, and roll back changes if necessary.
5. Learn keyboard shortcuts: Learning keyboard shortcuts for common tasks can save you time and improve your productivity. Take the time to learn the most important shortcuts for your IDE and incorporate them into your workflow.
In conclusion, programming has evolved significantly over the years, from punch cards to modern programming languages and IDEs. As technology continues to advance, the future of programming looks bright, with AI and machine learning driving innovation and making programming more accessible and intuitive. The role of IDEs will also continue to grow, providing developers with better tools and workflows to create amazing applications and systems.
Exploring the Evolution and Diversity of Unix, BSD, and Linux Operating Systems: Origins, Similarities, Differences, Uses, and Variants
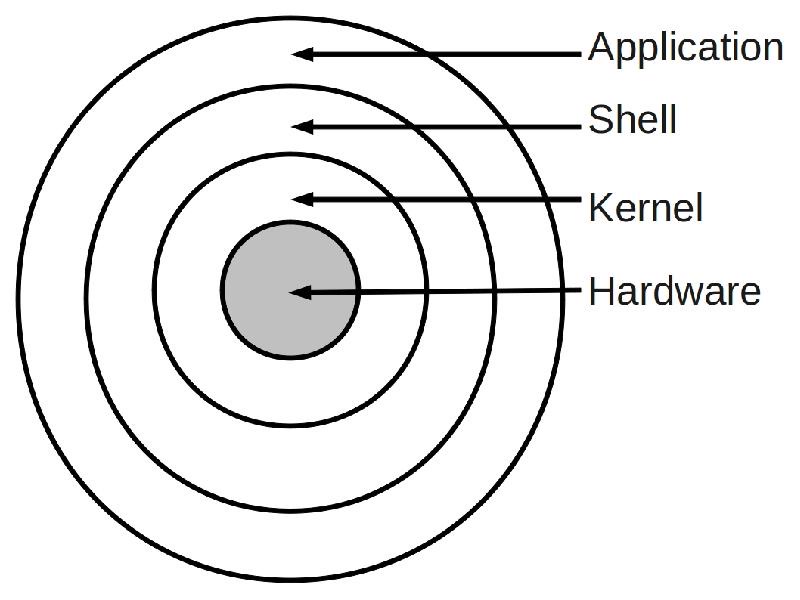
Operating systems are a crucial component of modern computer systems, providing a layer of software that manages the hardware and allows other software applications to run. Unix, BSD, and Linux are three of the most popular operating systems in use today, each with its own unique history, features, and user community.
Operating systems (OS) are an essential part of modern computing. They serve as the interface between the user and the hardware, enabling the user to perform tasks and manage resources. Among the many operating systems in existence, Unix, BSD, and Linux are some of the most popular and widely used. In this blog, we will discuss these operating systems, their origins, similarities, differences, uses, and variants.
Origin
Unix is a family of multitasking, multiuser computer operating systems originally developed in the 1960s by AT&T Bell Labs. It was designed to be portable, meaning it could be used on different types of hardware. Unix quickly gained popularity in the academic and research communities due to its flexibility and power.
UNIX is a widely-used operating system that was first developed in the late 1960s by a team of researchers at Bell Labs, including Ken Thompson and Dennis Ritchie. The system was designed to be a simple and flexible platform for running software and managing resources on mainframe computers, and it quickly gained popularity within the academic and research communities.
Over the years, UNIX has undergone several major revisions and spawned several related operating systems, including Linux and macOS. The development of UNIX was closely tied to the emergence of the Internet and the growth of computer networking, which made it an essential tool for system administrators and software developers around the world.
One of the key features of UNIX is its modular architecture, which allows users to combine and customize software tools and applications to suit their needs. This has made it a popular platform for a wide range of applications, from web servers and databases to scientific computing and artificial intelligence.
Despite its popularity, UNIX has faced several challenges and setbacks over the years, including legal battles over intellectual property rights and competition from newer, more user-friendly operating systems. However, it continues to be widely used in many industries and remains a vital part of the computing landscape.
BSD, or Berkeley Software Distribution, is a version of Unix that was developed at the University of California, Berkeley. It was initially released in the 1970s and was known for its networking capabilities and performance optimizations.
BSD (Berkeley Software Distribution) is a Unix-like operating system that originated at the University of California, Berkeley in the 1970s. It is a descendant of the original Unix operating system developed at Bell Labs.
The origins of BSD can be traced back to the mid-1970s, when researchers at UC Berkeley began developing a set of modifications to the Unix operating system developed at Bell Labs. These modifications, known as the Berkeley Software Distribution, added features like the vi editor, the C shell, and the TCP/IP networking stack.
Over the years, the BSD codebase was continuously developed and improved, leading to the creation of several distinct BSD variants, including NetBSD, FreeBSD, OpenBSD, and DragonFly BSD.
In the 1990s, a legal dispute between AT&T (the owners of Unix) and UC Berkeley over ownership of the Unix source code led to a split in the BSD community. As a result of this dispute, the BSD codebase was stripped of all AT&T-owned code, leading to the creation of a new open-source operating system known as FreeBSD.
Despite the legal challenges, BSD continued to evolve and gain popularity in the 2000s and 2010s. Today, BSD-based operating systems are widely used in a variety of contexts, including servers, routers, and embedded systems.
The fate of BSD has been mixed. While it has never achieved the same level of mainstream success as some other operating systems like Linux, it has remained an important and influential force in the world of open-source software. Today, BSD-based operating systems continue to be developed and used by a dedicated community of developers and users.
Linux is a Unix-like operating system that was developed in the early 1990s by Linus Torvalds, a computer science student at the University of Helsinki in Finland. Linux was created as a free and open-source alternative to Unix.
Linux is a free and open-source operating system that was created by Linus Torvalds in 1991. Torvalds, a Finnish computer science student, created the operating system as a hobby project, inspired by the Unix operating system, which was popular in academic and research settings.
The name "Linux" comes from a combination of Linus's first name and the word "Unix." Linux was originally distributed under the GNU General Public License, which means that anyone can use, modify, and distribute the operating system as long as they adhere to the terms of the license.
Over time, Linux has evolved from a small hobby project to a major player in the operating system market. Today, Linux is used in a wide range of applications, from web servers and supercomputers to smartphones and home automation systems.
One of the key factors in Linux's success is its open-source nature. Because the source code for Linux is freely available, anyone can modify it to suit their needs. This has led to the creation of many different "flavors" of Linux, each tailored to a specific use case or user group.
Another factor in Linux's success is its reputation for stability and security. Because Linux is open-source, bugs and vulnerabilities can be quickly identified and fixed by the community, reducing the risk of security breaches and other issues.
As for Linux's fate, it seems likely that the operating system will continue to play an important role in the tech industry for the foreseeable future. As more and more applications move to the cloud and as the Internet of Things (IoT) becomes more prevalent, the need for reliable and secure operating systems like Linux will only increase.
Similarities
Unix, BSD, and Linux all share many similarities. They are all Unix-like operating systems, meaning they are based on the same fundamental principles and architecture as Unix. They are all designed to be multitasking, multiuser systems, and they all use a command-line interface (CLI) as their primary means of interaction.
Additionally, they are all highly customizable and can be tailored to meet specific needs. They also have robust networking capabilities and are widely used in server environments.
Differences
Despite their similarities, Unix, BSD, and Linux have several key differences. One of the most significant differences is their origins. Unix and BSD were both developed by academic institutions, while Linux was created by an individual developer.
Another difference is their licensing. Unix is a proprietary operating system, meaning it is not freely available to the public. BSD, on the other hand, is open-source, meaning the source code is freely available for anyone to use and modify. Linux is also open-source and is released under the GNU General Public License (GPL).
In terms of their design, Unix and BSD are generally considered to be more stable and secure than Linux. This is because they have been around for much longer and have had more time to mature and develop robust security features.
Uses
Unix, BSD, and Linux are all used in a variety of applications, from desktop computing to large-scale server environments. Unix is commonly used in academic and research settings, while BSD is often used in networking and embedded systems.
Linux, meanwhile, is used in a wide range of applications, from personal desktop computing to mobile devices and servers. It is particularly popular in server environments due to its scalability and flexibility.
Variants
There are many different variants of Unix, BSD, and Linux, each with its unique features and capabilities. Some popular variants of Unix include Solaris, AIX, and HP-UX. Popular variants of BSD include FreeBSD, NetBSD, and OpenBSD. Popular variants of Linux include Ubuntu, Debian, and Fedora.
Unix, BSD, and Linux are all powerful and flexible operating systems that are widely used in a variety of applications. While they share many similarities, they also have key differences in their origins, licensing, and design.
In conclusion, operating systems are an essential component of modern computer systems, providing a crucial layer of software that manages the hardware and allows other software applications to run. Unix, BSD, and Linux are three of the most popular operating systems in use today, each with its own unique history, features, and user community.
Unix is the oldest of the three, developed in the 1960s and widely used in academic and research environments. BSD, based on the Unix source code, was developed in the 1970s and is known for its stability and security. Linux, developed in the 1990s, is an open-source operating system that has gained popularity for its flexibility, scalability, and widespread adoption in server environments.
While Unix and BSD are primarily used in academic and research environments, Linux has become the dominant operating system in the server and embedded systems markets. There are numerous variants of each of these operating systems, with different distributions catering to different use cases and user preferences. For example, Ubuntu and Fedora are popular Linux distributions for desktop users, while CentOS and Debian are commonly used for server deployments.
In summary, Unix, BSD, and Linux are three of the most widely used and influential operating systems in the world today. While they share many similarities, they also have distinct features, user communities, and use cases. Understanding the differences between these operating systems can help users choose the best one for their needs and contribute to the ongoing evolution of these important technologies.
Operating Systems: Understanding their Uses and How to Choose the Right One

An operating system (OS) is software that manages computer hardware and software resources and provides common services for computer programs. The operating system is the most important type of system software in a computer system. It is responsible for the management and coordination of activities and sharing of resources of the computer system. In this blog, we will discuss what operating systems are, their uses, and the criteria to select an operating system.
Types of Operating Systems:
There are four main types of operating systems:
1. Single-User, Single-Tasking OS: This type of operating system is designed to support only one user at a time and can only run one program at a time.
2. Single-User, Multi-Tasking OS: This type of operating system is designed to support one user at a time but can run multiple programs at the same time.
3. Multi-User, Multi-Tasking OS: This type of operating system is designed to support multiple users simultaneously and can run multiple programs at the same time.
4. Real-Time OS: This type of operating system is designed to run real-time applications, such as embedded systems, where the system must respond to events within a specific time frame.
Uses of Operating Systems:
1. Resource Management: The operating system manages the computer's resources, including the CPU, memory, and storage.
2. User Interface: The operating system provides a user interface that allows users to interact with the computer.
3. File Management: The operating system manages files and directories on the computer.
4. Security: The operating system provides security features to protect the computer from viruses and malware.
5. Networking: The operating system allows the computer to connect to a network and share resources with other computers.
Criteria to Select an Operating System:
1. Hardware Requirements: The operating system must be compatible with the computer's hardware. Check the system requirements of the operating system before installing it.
2. User Interface: The operating system's user interface should be user-friendly and easy to navigate.
3. Software Compatibility: The operating system should be compatible with the software you plan to use.
4. Security: The operating system should have built-in security features to protect the computer from viruses and malware.
5. Cost: The cost of the operating system should be considered before selecting one.
6. Support: The operating system should be backed by a company that offers support in case of any issues.
An operating system is a crucial component of a computer system. It manages computer resources and provides services to computer programs. When selecting an operating system, it is important to consider factors such as hardware requirements, user interface, software compatibility, security, cost, and support. By considering these factors, you can select an operating system that meets your needs and allows you to get the most out of your computer system.
The main functions of an operating system are:
- Memory Management: The operating system manages the memory of the computer, allocating it to different programs and processes as needed, and ensuring that programs do not interfere with each other's memory space.
- Processor Management: The operating system manages the processor or CPU, allocating it to different programs and processes as needed, and ensuring that each program gets a fair share of the processor's resources.
- Input/Output Management: The operating system manages the input/output devices, such as the keyboard, mouse, and printer, allowing programs to interact with them and ensuring that data is transmitted correctly.
- File Management: The operating system manages the file system, allowing programs to create, read, write, and delete files, and ensuring that data is stored correctly.
- Security Management: The operating system manages the security of the system, controlling access to resources and protecting the system from unauthorized access or malicious software.
There are several types of operating systems, including:
- Batch Operating System: A batch operating system processes a batch of jobs, without any user interaction. This type of system is used in environments where large numbers of similar jobs need to be processed, such as payroll or billing systems.
- Time-Sharing Operating System: A time-sharing operating system allows multiple users to share the resources of a computer, by dividing the processor time into small time slices and allowing each user to run their programs in turn.
- Real-Time Operating System: A real-time operating system is designed to respond quickly to events, such as sensor data or control signals, with a guaranteed response time.
- Distributed Operating System: A distributed operating system manages a network of computers, allowing them to share resources and work together as if they were a single system.
Operating systems are essential to the functioning of modern computer systems, as they provide a common platform for software developers and users to interact with the computer hardware. Without an operating system, each program would have to manage its memory, processor, input/output, and file system, making it much more difficult and time-consuming to develop and use computer software.
Here are some examples of the types of operating systems:
- Windows: Windows is a widely used operating system developed by Microsoft Corporation. It is a proprietary operating system, meaning that its source code is not publicly available. Windows is used on desktops, laptops, and servers, and it has a graphical user interface (GUI) that allows users to interact with the system using windows, icons, menus, and pointing devices.
- macOS: macOS is the operating system developed by Apple Inc. for their Macintosh computers. Like Windows, it is a proprietary operating system with a GUI. It is known for its user-friendly interface, high security, and seamless integration with Apple's other products, such as iPhones and iPads.
- Linux: Linux is an open-source operating system that is freely available for anyone to use and modify. It is widely used on servers, supercomputers, and embedded systems, and it has a reputation for being stable, secure, and flexible. Linux comes in many different distributions, such as Ubuntu, Fedora, and Debian, each with its own set of features and applications.
- Unix: Unix is a family of operating systems that share a common heritage and design philosophy. It was originally developed in the 1970s by AT&T Bell Labs, and it has since been widely used in academic, scientific, and business environments. Unix is known for its scalability, reliability, and efficiency, and it has been a major influence on the development of other operating systems, such as Linux and macOS.
- Android: Android is a popular operating system developed by Google Inc. for mobile devices such as smartphones and tablets. It is based on the Linux kernel and is open-source, allowing manufacturers and developers to modify it to suit their needs. Android is known for its large app ecosystem and customization options.
The interface between hardware and operating system (OS) is a critical component of a computer system. The hardware components of a computer include the physical components such as the processor, memory, storage devices, input/output (I/O) devices such as the keyboard, mouse, display screen, and other peripheral devices. The operating system is the software that manages the hardware and provides an interface for the user to interact with the computer system.
The interface between the hardware and the operating system is typically achieved through device drivers, which are software components that provide a bridge between the hardware and the operating system. Device drivers are typically included with the operating system or installed separately when new hardware is added to the system.
The device driver communicates with the hardware by sending commands and receiving status information. The operating system communicates with the device driver by sending requests for information or commands to the hardware. For example, if a user types on the keyboard, the hardware generates a signal that is transmitted to the device driver, which translates the signal into a character that the operating system can recognize and process.
The operating system also manages the allocation of resources such as memory and CPU time to different processes running on the computer system. This involves keeping track of which processes are running, which ones are waiting for resources, and which ones have been completed. The operating system also provides a set of system calls, which are programming interfaces that allow applications to access the services provided by the operating system.
In summary, the interface between hardware and operating systems is crucial for the proper functioning of a computer system. The device drivers and system calls provide a bridge between the physical components of the computer and the software that manages them, allowing the operating system to manage the allocation of resources and provide a user-friendly interface for interacting with the computer system.
Here are some examples of batch operating systems:
- IBM OS/360: IBM OS/360 was a batch-processing operating system developed by IBM in the 1960s. It was designed to run on the System/360 mainframe computer and was widely used by businesses and government agencies for data processing applications.
- Burroughs MCP: The MCP (Master Control Program) operating system was developed by Burroughs Corporation in the 1960s and 1970s. It was used on their mainframe computers and was designed to support batch processing, time-sharing, and real-time applications.
- UNIVAC EXEC 8: The UNIVAC EXEC 8 operating system was developed by Sperry Rand Corporation in the 1960s. It was designed to run on their UNIVAC 1108 mainframe computer and supported batch processing and time-sharing applications.
- ICL VME: VME (Virtual Machine Environment) was an operating system developed by International Computers Limited (ICL) in the 1970s. It was used on their mainframe computers and supported batch processing, time-sharing, and real-time applications.
- DEC VMS: VMS (Virtual Memory System) was an operating system developed by Digital Equipment Corporation (DEC) in the 1970s. It was used on their VAX mainframe computers and supported batch processing, time-sharing, and real-time applications.
Here are some examples of time-sharing operating systems:
- UNIX: UNIX is an operating system developed in the 1970s by Bell Labs. It is a multi-user, time-sharing system that has been widely used in academic, scientific, and business environments. It provides a command-line interface and supports multiple user accounts and concurrent processes.
- IBM TSO: TSO (Time Sharing Option) is an operating system developed by IBM in the 1970s. It was designed to run on their mainframe computers and provided a command-line interface and support for multiple users and concurrent processes.
- MULTICS: MULTICS (Multiplexed Information and Computing Service) was an operating system developed in the 1960s by a consortium of companies, including Bell Labs, MIT, and GE. It was designed to support time-sharing, multi-user, and distributed computing applications and was an early precursor to modern operating systems like UNIX.
- Windows Terminal Services: Windows Terminal Services is a component of Microsoft Windows that allows multiple users to connect to a single computer and run programs simultaneously. It provides a remote desktop interface and supports concurrent sessions.
- Linux Containers: Linux Containers are a lightweight virtualization technology that allows multiple users to share a single Linux system while maintaining isolation between their processes. They are often used for cloud computing and web hosting applications.
Here are some examples of real-time operating systems:
- VxWorks: VxWorks is a real-time operating system developed by Wind River Systems. It is used in a wide range of embedded systems and devices, including aerospace and defense systems, automotive systems, medical devices, and industrial automation.
- QNX: QNX is a real-time operating system developed by BlackBerry Limited. It is used in a variety of applications, including automotive systems, medical devices, and industrial control systems.
- FreeRTOS: FreeRTOS is a real-time operating system designed for small embedded systems. It is open-source and has a small footprint, making it ideal for resource-constrained devices.
- Windows CE: Windows CE (Compact Edition) is a real-time operating system developed by Microsoft. It is used in a variety of embedded devices, including handheld computers, medical devices, and automotive systems.
- RTLinux: RTLinux is a real-time operating system that combines the Linux kernel with real-time extensions. It provides a standard Linux programming environment while also supporting real-time applications. It is used in a variety of embedded systems and industrial control applications.
Here are some examples of distributed operating systems:
- Google File System (GFS): GFS is a distributed file system developed by Google. It is used to store and manage large amounts of data across multiple servers and data centers. GFS is designed to provide high reliability and availability, even in the face of server failures.
- Apache Hadoop: Hadoop is a distributed computing platform that includes a distributed file system (HDFS) and a MapReduce programming model. It is widely used for big data processing and analysis.
- Windows Distributed File System (DFS): DFS is a distributed file system developed by Microsoft. It allows users to access files stored on multiple servers as if they were stored on a single system. DFS provides fault tolerance, load balancing, and scalability.
- Amoeba: Amoeba is a distributed operating system developed by Vrije Universiteit in Amsterdam. It is designed to support the development of distributed applications and provides a transparent distributed file system, process migration, and remote procedure calls.
- Plan 9 from Bell Labs: Plan 9 is a distributed operating system developed by Bell Labs. It is designed to support network computing and provides a distributed file system, remote procedure calls, and a network-transparent graphical user interface.
Explaining the internals of Windows, Linux, and Unix operating systems in detail would require a vast amount of technical information, so a brief overview of each is provided.
1. Windows: Windows is a proprietary operating system developed by Microsoft. Its kernel is known as the Windows NT kernel, which provides the core functionality of the system. The Windows NT kernel supports preemptive multitasking, virtual memory, and symmetric multiprocessing. Windows also includes several system services, such as the Windows File Manager, which provides access to the file system, and the Windows Registry, which stores configuration settings. Windows uses a graphical user interface and supports a wide range of hardware and software applications.
2. Linux: Linux is an open-source operating system based on the Unix operating system. The Linux kernel provides the core functionality of the system, including support for multitasking, virtual memory, and symmetric multiprocessing. Linux is known for its flexibility and modularity, with many components of the system available as interchangeable modules. Linux also includes a variety of tools and utilities for system administration and software development. Linux can be run on a wide range of hardware platforms, from desktop computers to embedded systems.
3. Unix: Unix is a family of operating systems developed in the 1960s and 1970s. The Unix kernel provides the core functionality of the system, including support for multitasking, virtual memory, and symmetric multiprocessing. Unix is known for its modular design and emphasis on the command-line interface. Unix includes a variety of tools and utilities for system administration and software development, and many of these have become standard components of modern operating systems. Unix has been used in a wide range of applications, from scientific research to business computing.
Overall, each of these operating systems has its unique features and design principles, but they all share a common set of core functionality and system services. Understanding the internals of an operating system is essential for system administrators and software developers who need to optimize performance, troubleshoot problems, and develop new applications.
Several operating systems are based on the Unix operating system, including:
- Linux: Linux is an open-source operating system that is Unix-like. It is based on the Linux kernel, which was developed by Linus Torvalds in 1991, and has since been modified and extended by a large community of developers.
- macOS: macOS is a proprietary operating system developed by Apple Inc. It is based on the Unix-like operating system, Darwin, which in turn is based on the FreeBSD Unix distribution.
- Solaris: Solaris is a proprietary Unix operating system developed by Sun Microsystems (now owned by Oracle Corporation). It is known for its scalability, reliability, and security features, and is used in many mission-critical environments.
- AIX: AIX (Advanced Interactive eXecutive) is a proprietary Unix operating system developed by IBM. It is designed for IBM's Power Systems servers and is known for its reliability and high availability features.
- HP-UX: HP-UX (Hewlett-Packard UniX) is a proprietary Unix operating system developed by Hewlett-Packard (now Hewlett-Packard Enterprise). It is designed for HP's Itanium-based servers and is known for its scalability and reliability features.
Note that while these operating systems are based on Unix, they may have diverged significantly from the original Unix codebase over time, and may have different features, commands, and user interfaces.
In Unix-like operating systems, interrupts are used to manage hardware devices and handle system events. Here are some of the interrupts commonly used in Unix:
- Hardware Interrupts: These interrupts are generated by hardware devices, such as the keyboard, mouse, and network adapter, to signal the CPU that an event has occurred that requires its attention.
- Software Interrupts: These interrupts are generated by software programs to request a specific service from the operating system. For example, when a process wants to read data from a file, it generates a software interrupt to request the operating system to perform the I/O operation.
- Timer Interrupts: These interrupts are generated by a timer device that is used to keep track of time and schedule tasks. The timer interrupt is used to signal to the CPU that the timer has expired and that the operating system needs to perform some task, such as rescheduling processes.
- Exception Interrupts: These interrupts are generated by the CPU when an error or exception occurs, such as a divide-by-zero error or an illegal instruction. The operating system uses these interrupts to handle the error and prevent the system from crashing.
Interrupts are a fundamental part of the Unix operating system, as they enable hardware devices and software programs to communicate with the CPU and ensure that the system runs smoothly. By using interrupts, the operating system can respond quickly to events and manage system resources efficiently.
The Unix operating system can be divided into several key components, which work together to provide a complete system for running applications and managing resources. Here is a brief overview of the anatomy of a typical Unix system:
- Kernel: The kernel is the core component of the operating system, which provides low-level services such as process management, memory management, device drivers, and file systems. It is responsible for managing the system's resources and providing a consistent interface to the applications running on top of it.
- Shell: The shell is the user interface for the operating system, which allows users to interact with the system and run commands. There are several different shells available in Unix, such as the Bourne shell (sh), C shell (csh), and Korn shell (ksh), each with its syntax and features.
- File system: The file system is how Unix organizes and stores files and directories. Unix file systems are hierarchical, with a root directory at the top and subdirectories branching out below it. The file system can be accessed using commands such as ls, cd, and mkdir.
- Utilities: Unix includes a large collection of command-line utilities, such as ls, grep, awk, sed, and many others, which provide powerful tools for manipulating and processing data.
- Libraries: Unix includes a variety of software libraries, which provide pre-written code for common tasks such as networking, graphics, and database access.
- Networking: Unix includes a wide range of networking capabilities, such as TCP/IP, SSH, FTP, and many others, which allow Unix systems to communicate and share resources across local and wide area networks.
- Applications: Unix supports a wide range of applications, from simple command-line tools to complex graphical applications. Many applications are open-source and can be freely downloaded and installed on Unix systems.
Together, these components provide a powerful and flexible environment for running applications and managing resources on Unix systems. The modularity and flexibility of Unix have contributed to its popularity and longevity as an operating system.
In Unix-like operating systems, interrupts are used to manage hardware devices and handle system events. Here are some of the interrupts commonly used in Unix:
- Hardware Interrupts: These interrupts are generated by hardware devices, such as the keyboard, mouse, and network adapter, to signal the CPU that an event has occurred that requires its attention.
- Software Interrupts: These interrupts are generated by software programs to request a specific service from the operating system. For example, when a process wants to read data from a file, it generates a software interrupt to request the operating system to perform the I/O operation.
- Timer Interrupts: These interrupts are generated by a timer device that is used to keep track of time and schedule tasks. The timer interrupt is used to signal to the CPU that the timer has expired and that the operating system needs to perform some task, such as rescheduling processes.
- Exception Interrupts: These interrupts are generated by the CPU when an error or exception occurs, such as a divide-by-zero error or an illegal instruction. The operating system uses these interrupts to handle the error and prevent the system from crashing.
Interrupts are a fundamental part of the Unix operating system, as they enable hardware devices and software programs to communicate with the CPU and ensure that the system runs smoothly. By using interrupts, the operating system can respond quickly to events and manage system resources efficiently.
The Linux operating system has a similar structure to Unix but with some key differences. Here is a brief overview of the anatomy of a typical Linux system:
- Kernel: The Linux kernel is the core component of the operating system, which provides low-level services such as process management, memory management, device drivers, and file systems. It is responsible for managing the system's resources and providing a consistent interface to the applications running on top of it.
- Shell: Linux provides several different shells, such as bash, zsh, and fish, which provide a user interface for running commands and interacting with the system.
- File system: Like Unix, Linux uses a hierarchical file system, with a root directory at the top and subdirectories branching out below it. The file system can be accessed using commands such as ls, cd, and mkdir.
- User-space utilities: Linux includes a large collection of user-space utilities, such as ls, grep, awk, sed, and many others, which provide powerful tools for manipulating and processing data.
- Libraries: Linux includes a variety of software libraries, which provide pre-written code for common tasks such as networking, graphics, and database access.
- Package management: Linux distributions typically include a package management system, such as apt, yum, or pacman, which allows users to easily install, update, and manage software packages.
- Desktop environment: Linux supports a wide range of graphical desktop environments, such as GNOME, KDE, and Xfce, which provide a graphical user interface for running applications and managing files.
- Networking: Linux includes a wide range of networking capabilities, such as TCP/IP, SSH, FTP, and many others, which allow Linux systems to communicate and share resources across local and wide area networks.
- Applications: Linux supports a wide range of applications, from simple command-line tools to complex graphical applications. Many applications are open-source and can be freely downloaded and installed on Linux systems.
Together, these components provide a powerful and flexible environment for running applications and managing resources on Linux systems. The modularity and flexibility of Linux have contributed to its popularity and widespread use in a wide range of environments, from personal computers to servers and embedded devices.
Linux is an open-source operating system based on the Unix operating system. Linux servers are widely used in various industries, including web hosting, cloud computing, and enterprise-level computing. The anatomy of a Linux server can be divided into several components, including:
- Kernel: The Linux kernel is the core component of the operating system, responsible for managing system resources, handling device drivers, and providing a foundation for other system components. The kernel is responsible for managing memory, scheduling processes, and handling I/O requests.
- Shell: The Linux shell is a command-line interface that provides access to the operating system's services and utilities. The shell provides a way for administrators to interact with the system and perform tasks such as managing files, configuring network settings, and installing software.
- Services: Linux servers typically run a variety of services, including web servers, mail servers, file servers, and database servers. These services are often configured using configuration files that define how the service should operate.
- File System: Linux uses a hierarchical file system, where all files and directories are organized under a single root directory. The file system is responsible for managing files and directories, including permissions and ownership.
- Package Management: Linux servers typically use package management systems to install and manage software packages. These package management systems provide a way to download and install software from central repositories, as well as manage dependencies and updates.
- Security: Linux servers are known for their strong security features, including firewalls, access controls, and encryption. Linux servers also support various authentication protocols, such as Kerberos and LDAP, to ensure that only authorized users can access network resources.
- Virtualization: Linux servers support various virtualization technologies, such as KVM, Xen, and Docker. These technologies allow administrators to create and manage virtual machines or containers on a server, which can be useful for consolidating servers, improving resource utilization, and creating test environments.
In summary, the anatomy of a Linux server includes a powerful kernel, a flexible and robust shell, a wide range of services, a hierarchical file system, a package management system, strong security features, and support for virtualization technologies. Together, these components make Linux servers a popular choice for various industries and applications.
In Linux, an interrupt is a signal sent to the operating system to temporarily halt normal processing and handle an event. Linux uses several types of interrupts, including:
- Hardware Interrupts: These interrupts are generated by hardware devices, such as keyboards, mice, network adapters, and storage devices, to notify the operating system that a task has been completed or an error has occurred.
- Software Interrupts: These interrupts are generated by software applications or drivers to request a service from the operating system, such as reading or writing data from a disk, allocating memory, or opening a network connection.
- System Interrupts: These interrupts are generated by the operating system itself to handle events that require immediate attention, such as system errors, hardware failures, or power management events.
- Interrupt Request (IRQ): An IRQ is a hardware signal used to request attention from the CPU. Each hardware device is assigned a unique IRQ, which allows the operating system to determine which device is generating the interrupt and take appropriate action.
- Soft Interrupts: Soft interrupts are a type of software interrupt used by the Linux kernel to handle low-priority tasks that cannot be processed immediately, such as updating system statistics or handling network traffic.
- System Calls: System calls are a type of software interrupt used by applications or processes to request services from the operating system, such as creating a file, reading data from a disk, or allocating memory.
- Tasklets: Tasklets are a type of software interrupt used by the Linux kernel to handle high-priority tasks that need to be executed promptly, such as handling network packets or disk I/O requests.
- Bottom Halves: Bottom halves are a type of software interrupt used by the Linux kernel to handle tasks that cannot be handled by a tasklet or a soft interrupt, such as updating system statistics or handling memory allocation requests.
In summary, interrupts are a fundamental part of the Linux operating system and are used to handle a wide range of events, from hardware errors to software requests. Understanding how interrupts work is essential for system administrators and developers, as it can help diagnose and troubleshoot system issues.
Unix and Linux are two popular operating systems that share many similarities but also have some significant differences. Here are some of the key similarities and differences between Unix and Linux:
Similarities:
- Unix and Linux are both Unix-like operating systems and share many features and commands.
- Both operating systems are designed to be multi-user and multi-tasking.
- They both support a wide range of programming languages and development tools.
- Both have strong security features and can be used in secure environments.
- They both have a command-line interface, although many Linux distributions also offer a graphical user interface (GUI).
Differences:
- Unix is a proprietary operating system that was developed in the 1970s, while Linux is an open-source operating system that was developed in the 1990s.
- Unix is generally considered to be more stable and reliable than Linux, although this can vary depending on the specific distribution and configuration.
- Linux is more customizable and flexible than Unix, as it is open-source and can be modified and extended by developers and users.
- Unix is typically more expensive than Linux, as it requires licensing fees and proprietary hardware.
- Unix is generally more standardized and consistent across different versions and distributions, while Linux can vary more in terms of features and compatibility.
In terms of which operating system is more reliable and secure, it's difficult to make a definitive statement, as this can depend on many factors, such as the specific version and configuration of the operating system, the hardware it is running on, and the environment in which it is being used. In general, both Unix and Linux are known for their strong security features and are used in many secure environments, such as financial institutions, government agencies, and research facilities. However, Unix is generally considered to be more stable and reliable, due to its long history and standardization.
Here is a brief overview of the anatomy of a typical Windows Server operating system:
- Kernel: The Windows Server kernel is the core component of the operating system, which provides low-level services such as process management, memory management, device drivers, and file systems. It is responsible for managing the system's resources and providing a consistent interface to the applications running on top of it.
- Graphical user interface: Windows Server provides a graphical user interface (GUI) that allows users to interact with the system using windows, icons, menus, and dialog boxes. The GUI is built on top of the Windows API and can be customized using themes and other visual elements.
- File system: Windows Server uses the NTFS file system, which provides advanced features such as file permissions, encryption, and compression. Other file systems, such as FAT and exFAT, are also supported.
- Active Directory: Windows Server includes the Active Directory service, which provides centralized management of users, groups, and computers on a network. Active Directory also provides authentication and authorization services for network resources.
- PowerShell: Windows Server includes the PowerShell command-line interface, which provides a powerful tool for automating system administration tasks and managing system resources.
- Networking: Windows Server includes a wide range of networking capabilities, such as TCP/IP, DNS, DHCP, and many others, which allow Windows systems to communicate and share resources across local and wide area networks.
- Remote Desktop Services: Windows Server includes Remote Desktop Services, which allow users to access the server's desktop remotely using the Remote Desktop Protocol (RDP).
- Hyper-V: Windows Server includes the Hyper-V virtualization platform, which allows multiple virtual machines to run on a single physical server. Hyper-V provides advanced features such as live migration and virtual machine replication.
- Applications: Windows Server supports a wide range of applications, from simple command-line tools to complex graphical applications. Many applications are designed specifically for Windows Server, such as Microsoft Exchange Server and Microsoft SQL Server.
Together, these components provide a powerful and flexible environment for running applications and managing resources on Windows Server systems. The modularity and flexibility of Windows Server have contributed to its popularity and widespread use in a wide range of environments, from small businesses to large enterprises.
In Windows, an interrupt is a signal sent to the operating system to stop normal processing and handle an event. Windows uses several types of interrupts, including:
- Hardware Interrupts: These interrupts are generated by hardware devices, such as keyboards, mice, network adapters, and storage devices, to notify the operating system that a task has been completed or an error has occurred.
- Software Interrupts: These interrupts are generated by software applications or drivers to request a service from the operating system, such as reading or writing data from a disk, allocating memory, or opening a network connection.
- System Interrupts: These interrupts are generated by the operating system itself to handle events that require immediate attention, such as system errors, hardware failures, or power management events.
- Interrupt Request (IRQ): An IRQ is a hardware signal used to request attention from the CPU. Each hardware device is assigned a unique IRQ, which allows the operating system to determine which device is generating the interrupt and take appropriate action.
- Deferred Procedure Call (DPC): A DPC is a software interrupt used by Windows to handle low-priority tasks that cannot be processed immediately, such as updating system statistics or handling network traffic.
- System Calls: System calls are a type of software interrupt used by applications or processes to request services from the operating system, such as creating a file, reading data from a disk, or allocating memory.
In summary, interrupts are a fundamental part of the Windows operating system and are used to handle a wide range of events, from hardware errors to software requests. Understanding how interrupts work is essential for system administrators and developers, as it can help diagnose and troubleshoot system issues.
Navigating Uncertainty: Strategies for Sustaining Your Business in Today's World

- Adapting to the New Normal, Weathering the Storm, and Building Resilience for Long-Term Success.
- Sustaining Business in the Current World: Strategies for Adapting, Weathering, and Building Resilience.
- Adapting to the New Normal: Innovative Approaches to Business Sustainability
- Weathering the Storm: Practical Steps for Surviving Economic Uncertainty
- Resilience in the Face of Adversity: Lessons from Successful Business Owners
The world has undergone a significant transformation over the past few years, with the COVID-19 pandemic and ongoing conflicts leading to unprecedented changes in the way we live and work. For businesses, this has meant adapting to new ways of operating, navigating economic uncertainty, and building resilience for long-term success. In this paper, we will explore practical strategies for sustaining your business in the current world, from adapting to the new normal to weathering the storm of economic uncertainty and building resilience for the future.
In this paper, we have provided practical strategies for sustaining your business in today's world. Whether you are a small business owner or a corporate executive, these strategies can help you navigate uncertainty and position your company for success. By adapting to the new normal, weathering the storm of economic uncertainty, and building resilience for long-term success, businesses can not only survive but thrive in today's world.
Adapting to the New Normal The COVID-19 pandemic has brought about a paradigm shift in the way businesses operate. Remote work has become the norm, and many companies have had to pivot their business models to survive. As the pandemic recedes, businesses must continue to adapt to the new normal to remain competitive. This section explores practical strategies for adapting to the post-pandemic world, including:
- Investing in digital transformation: The pandemic has accelerated the shift towards digital technologies. Companies that invest in digital transformation, such as cloud computing and automation, are better positioned to adapt to the new normal and remain competitive.
- Embracing remote work: Remote work has become a permanent feature of the new normal. Companies that embrace remote work and provide their employees with the necessary tools and support will have a competitive advantage in attracting and retaining talent.
- Diversifying supply chains: The pandemic has highlighted the vulnerabilities of global supply chains. Companies that diversify their supply chains and build redundancy into their operations are better equipped to withstand supply chain disruptions.
Adapting to the New Normal The COVID-19 pandemic has brought about many changes in the business world, one of which is the rise of remote work. With many businesses transitioning to remote work, it has become essential for managers to learn how to manage remote teams effectively. One of the primary benefits of remote work is that it can help businesses save costs on office space and reduce employee turnover. However, some challenges come with remote work, such as the lack of face-to-face interaction and potential communication barriers. To manage remote teams effectively, businesses need to ensure that they have the right tools and processes in place, such as video conferencing software and project management tools.
Another significant change brought about by the pandemic is the acceleration of digital transformation. With businesses investing heavily in technology, it has become essential for companies to prioritize digital transformation initiatives to stay competitive. Digital transformation can help businesses streamline operations, improve customer experiences, and reduce costs. However, implementing digital transformation initiatives can be challenging, and businesses need to ensure that they have the right talent and resources in place to execute these initiatives successfully.
The pandemic and ongoing conflicts have also led to disruptions in supply chains across the world, which can impact businesses in various industries. To manage supply chain risks, businesses need to adopt a proactive approach to supply chain management, such as developing contingency plans and diversifying their supplier base.
Weathering the Storm of Economic Uncertainty In this section, we will discuss how businesses can weather the storm of economic uncertainty and protect themselves against financial losses. Topics covered include:
·Cash flow management: Cash flow is crucial for business survival, especially during times of economic uncertainty. We will explore strategies for managing cash flow effectively, including forecasting and cost control. Cash flow management is critical during times of economic uncertainty. Companies that have a clear understanding of their cash flow position and take proactive measures to manage it are better positioned to survive.
·New revenue streams: To survive in today's world, businesses need to be agile and adaptable. We will discuss how businesses can identify and pursue new revenue streams, and provide examples of companies that have successfully pivoted their business models. The pandemic and war have created new opportunities for businesses that can adapt quickly. Companies that can identify and capitalize on new revenue streams, such as new markets or product lines, will be better positioned to thrive.
·Stakeholder relationships: Strong stakeholder relationships are essential for business success, especially during times of economic uncertainty. We will discuss how businesses can build and maintain strong relationships with customers, suppliers, and employees, and the benefits of doing so.
· Controlling costs: Controlling costs are essential during economic downturns. Companies that can identify and reduce non-essential expenses, without compromising their core operations, will be better positioned to weather the storm.
Weathering the Storm of Economic Uncertainty Economic uncertainty is a significant challenge that businesses face, especially in the current world. Cash flow management is essential for business survival, and businesses need to ensure that they have enough liquidity to weather economic downturns. To manage cash flow effectively, businesses need to forecast revenue and expenses accurately, monitor their cash flow regularly, and control costs where possible.
Identifying and pursuing new revenue streams is also essential for business survival. Businesses need to be agile and adaptable, willing to pivot their business models when necessary to stay competitive. For example, many businesses shifted to online sales during the pandemic, which helped them to survive in a challenging economic environment.
Stakeholder relationships are another critical aspect of business success, especially during times of economic uncertainty. Businesses need to build and maintain strong relationships with customers, suppliers, and employees to survive economic downturns. For example, businesses that prioritize employee well-being are more likely to retain top talent and maintain productivity levels during challenging times.
Building Resilience for Long-Term Success In this section, we will discuss how businesses can build resilience for long-term success and position themselves for growth. Topics covered include:
· Future planning: To build resilience, businesses need to plan for the future and anticipate potential challenges. We will discuss the importance of scenario planning, and provide tips for creating a flexible and adaptable business strategy.
· Talent management: Building a strong and resilient workforce is essential for business success. We will explore strategies for attracting, retaining, and developing top talent, and the benefits of doing so.
· Corporate social responsibility: Businesses that prioritize corporate social responsibility are more likely to build trust with stakeholders and achieve long-term success. We will discuss the importance of CSR, and provide examples of companies that have successfully integrated CSR into their business strategies.
· Building a strong team: A strong team is the foundation of a resilient business. Companies that invest in their employees, foster a positive workplace culture, and provide training and development opportunities will be better positioned to weather the storm.
· Maintaining strong relationships with stakeholders: Strong relationships with customers, suppliers, and other stakeholders are critical during times of economic uncertainty. Companies that maintain open lines of communication, demonstrate flexibility and empathy, and deliver on their promises will be better positioned to maintain these relationships.
· Planning for the future: Finally, businesses must plan for the future. Companies that have a clear vision and mission, set realistic goals, and develop actionable plans to achieve them, will be better positioned to navigate uncertainty and sustain their operations over the long term.
Building Resilience for Long-Term Success Building resilience is essential for businesses that want to position themselves for long-term success. Future planning is essential for building resilience, as businesses need to anticipate potential challenges and plan accordingly. Scenario planning can help businesses prepare for a range of scenarios and develop a flexible and adaptable business strategy.
Talent management is another critical aspect of building resilience, as businesses need to attract, retain, and develop top talent to stay competitive. This involves creating a positive and inclusive work culture, investing in employee training and development, and offering competitive compensation packages.
Corporate social responsibility (CSR) is also essential for building resilience and achieving long-term success. Businesses that prioritize CSR are more likely to build trust with stakeholders and differentiate themselves from competitors.
2. Embrace Digital Transformation
In today's digital age, businesses must embrace digital transformation to stay competitive and relevant. Companies that have already invested in digital technology and have an online presence were able to adapt quickly to remote work during the pandemic and continue their operations.
Digital transformation can help businesses in multiple ways, such as:
- Providing an online platform for customers to browse and purchase products and services
- Streamlining operations with automated processes and cloud-based software
- Offering remote work opportunities to employees
- Facilitating communication and collaboration among team members
To sustain a business in the current situation, it's essential to invest in digital transformation. This investment can be in the form of hardware, software, training, and hiring experts who can guide the transformation process.
3. Diversify Your Offerings
In uncertain times, businesses that have diversified their offerings are better equipped to weather the storm. For example, a restaurant that offers online ordering and delivery in addition to dine-in options is more likely to sustain itself during a pandemic-induced lockdown.
Diversifying your offerings can also mean expanding into new markets, creating new products or services, or targeting new customer segments. The key is to identify areas where you can add value and generate revenue while still leveraging your existing strengths.
4. Prioritize Customer Experience
In a world where customers have more choices than ever before, prioritizing customer experience is crucial for businesses to stand out and retain loyal customers. This involves understanding your customers' needs and preferences, delivering personalized experiences, and providing excellent customer service.
During difficult times, customers are looking for businesses that can provide them with solutions and support. By prioritizing customer experience, businesses can build lasting relationships with customers, increase customer loyalty, and drive repeat business.
5. Stay Agile and Flexible
In uncertain times, businesses need to be agile and flexible to adapt to changing circumstances quickly. This means being open to new ideas and approaches, experimenting with new strategies, and pivoting when necessary.
To stay agile and flexible, businesses need to have a culture that encourages innovation and experimentation. This culture can be fostered by hiring diverse talent, creating a safe environment for experimentation, and providing resources and support to test and implement new ideas.
Conclusion
The current situation has presented significant challenges to businesses worldwide. However, by adopting a proactive approach, embracing digital transformation, diversifying offerings, prioritizing customer experience, and staying agile and flexible, businesses can not only survive but thrive in the face of uncertainty. It's important to remember that every challenge presents an opportunity for growth and innovation, and businesses that can adapt to the changing circumstances are the ones that will succeed in the long run.
In conclusion, sustaining your business in today's uncertain world requires a combination of adaptation, resilience, and innovation. By embracing the new normal, weathering the storm of economic uncertainty, and building resilience in your business, you can position your company for success in the years to come. Remember, the key to sustainability is to plan for the future, stay focused on your goals, and remain agile and adaptable in the face of adversity
A Guide to Servers: Their Usage, History, and Evolution

Servers have become an essential part of modern technology. They are used for a wide range of purposes, including data storage, communication, and cloud computing. In this blog, we will explore the history of servers, their evolution, and their importance in the digital age.
History of Servers:
Servers have been around since the early days of computing. In the 1960s, mainframe computers were used as servers to store and process data. These early servers were large and expensive, and only large corporations and government agencies could afford to use them.
As technology evolved, servers became smaller and more affordable. In the 1980s, personal computers became popular, and companies began using them as servers for local networks. In the 1990s, the Internet became widely available, and servers were used to host websites and provide email services.
Evolution of Servers:
As technology continued to evolve, servers became more powerful and versatile. Today, servers are used for a wide range of purposes, including data storage, communication, cloud computing, and virtualization.
Cloud computing has become particularly popular in recent years. With cloud computing, servers are used to store and process data in remote locations, allowing users to access their data from anywhere in the world. This has led to a shift away from traditional on-premises servers to cloud-based servers.
Usage of Servers:
Servers are used for a wide range of purposes, including:
1. Data Storage: Servers are used to store data, including documents, images, and videos. They provide a centralized location for data storage, making it easy for users to access their data from anywhere.
2. Communication: Servers are used to provide email, chat, and other communication services. They allow users to communicate with each other in real-time, no matter where they are located.
3. Cloud Computing: Servers are used to provide cloud computing services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). These services allow users to access computing resources on demand, without having to invest in their hardware.
4. Virtualization: Servers are used to provide virtualization services, allowing multiple virtual machines to run on a single physical server. This can help organizations save money on hardware costs and reduce their environmental footprint.
Servers have come a long way since their early days as mainframe computers. Today, they are an essential part of modern technology, used for a wide range of purposes. With cloud computing and virtualization, servers are more powerful and versatile than ever before. As technology continues to evolve, servers will undoubtedly play an increasingly important role in the digital age.
Servers can be broadly categorized into different types based on their function, hardware specifications, and intended usage. Here are some of the most common types of servers and a brief explanation of each:
1. Web servers: These servers are designed to host websites and web applications. They typically run specialized software like Apache or Nginx that can handle HTTP requests and serve static and dynamic content to web clients.
2. Database servers: These servers are optimized for storing, managing, and retrieving data from databases. They typically run database management systems (DBMS) like MySQL, Oracle, or Microsoft SQL Server.
3. Application servers: These servers provide a runtime environment for running applications. They can run on a variety of platforms and languages like Java, .NET, or Python.
4. Mail servers: These servers are used to handle email traffic, storing and forwarding messages between mail clients and other mail servers. They typically run specialized software like Postfix or Sendmail.
5. File servers: These servers are used to store and manage files and provide access to them over a network. They may use a variety of protocols like SMB, NFS, or FTP to allow clients to access shared files.
6. Print servers: These servers are used to manage printing services on a network. They typically run specialized software that can handle multiple print requests from different clients and manage print queues.
7. DNS servers: These servers are used to resolve domain names into IP addresses. They typically run a DNS server software like BIND or Windows DNS Server.
8. Proxy servers: These servers act as intermediaries between clients and other servers on a network. They can be used for caching content, filtering requests, or enhancing security.
There are many other types of servers as well, but these are some of the most common. Each type of server has its own hardware and software requirements, as well as specific configuration and management considerations.
Servers typically use processors that are designed for high performance and high reliability, as they are expected to handle heavy workloads and operate continuously. Here are some of the most common types of processors used in servers:
- x86 processors: These processors are based on the Intel x86 architecture and are widely used in servers. They are known for their versatility, power efficiency, and high performance.
- ARM processors: These processors are based on the ARM architecture and are increasingly being used in servers, particularly for energy-efficient workloads. They are commonly used in low-power servers, IoT devices, and edge computing applications.
- Power processors: These processors are designed by IBM and are used in IBM Power Systems servers. They are known for their high performance and scalability, as well as their support for virtualization and workload consolidation.
- SPARC processors: These processors are designed by Oracle and are used in Sun SPARC-based servers. They are known for their high reliability, availability, and serviceability, as well as their support for mission-critical applications.
- MIPS processors: These processors are used in a variety of server and networking applications, particularly in embedded systems and routers. They are known for their power efficiency and low cost.
Each type of processor has its advantages and disadvantages, and the choice of a processor depends on the specific requirements of the server workload. Factors like performance, power efficiency, scalability, and compatibility with software applications all need to be considered when selecting a processor for a server.
The processors used in servers can vary depending on the specific model and configuration. However, here is a general overview of the types of processors used by the server manufacturers mentioned earlier:
- Dell Technologies: Dell's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Hewlett-Packard Enterprise (HPE): HPE's servers also use processors from Intel and AMD, including Xeon and EPYC processors.
- Lenovo: Lenovo's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- IBM: IBM's servers use processors from IBM's own POWER family, as well as processors from Intel and AMD.
- Cisco: Cisco's servers use processors from Intel, including Xeon processors.
- Fujitsu: Fujitsu's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Oracle: Oracle's servers use processors from Oracle's own SPARC family, as well as processors from Intel and AMD.
- Supermicro: Supermicro's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Huawei: Huawei's servers use processors from Huawei's own Kunpeng and Ascend families, as well as processors from Intel and AMD.
In terms of operating systems, the servers listed here can typically run a wide range of operating systems. Common operating systems include:
- Windows Server
- Linux (including Red Hat, CentOS, and Ubuntu)
- Unix (including AIX, HP-UX, and Solaris)
- VMware ESXi
- Citrix Hypervisor
- FreeBSD
However, the specific operating systems supported by a server will depend on its hardware and firmware, as well as the drivers and software available for that particular platform.
Here is a list of some proprietary operating systems and the servers that run these operating systems:
- IBM i: IBM i is a proprietary operating system from IBM that runs on IBM Power Systems servers. IBM i is designed for mid-sized and large organizations and provides a high level of reliability, security, and scalability. IBM i includes many built-in applications and services, including a database management system, web server, and application server.
- z/OS: z/OS is a proprietary operating system from IBM that runs on IBM Z Systems mainframe servers. z/OS is designed for large-scale enterprise environments and provides high performance, reliability, and security. z/OS includes many built-in applications and services, including a database management system, web server, and application server.
- Oracle Solaris: Oracle Solaris is a proprietary operating system from Oracle that runs on Oracle servers. Solaris is designed for businesses of all sizes and provides advanced features such as built-in virtualization, advanced file systems, and integrated security. Solaris includes many built-in applications and services, including a database management system, web server, and application server.
- HPE NonStop: HPE NonStop is a proprietary operating system from Hewlett Packard Enterprise that runs on HPE NonStop servers. NonStop is designed for organizations that require high availability, high performance, and high scalability. NonStop includes many built-in applications and services, including a database management system, web server, and application server.
- Unisys OS 2200: Unisys OS 2200 is a proprietary operating system from Unisys that runs on Unisys ClearPath servers. OS 2200 is designed for businesses of all sizes and provides high reliability, security, and scalability. OS 2200 includes many built-in applications and services, including a database management system, web server, and application server.
Here's a list of some popular proprietary operating systems and the servers that run them:
1. Microsoft Windows Server: This operating system is developed by Microsoft and is designed for server use. It is used by many organizations for various purposes, including web servers, database servers, and application servers.
2. IBM AIX: AIX is a proprietary operating system developed by IBM for use on their servers. It is commonly used in enterprise environments and is known for its reliability and scalability.
3. Oracle Solaris: Solaris is a Unix-based proprietary operating system developed by Oracle. It is commonly used for mission-critical applications and database servers.
4. HP-UX: HP-UX is a proprietary Unix-based operating system developed by Hewlett Packard (now HP Enterprise). It is commonly used in enterprise environments and is known for its scalability and reliability.
5. Red Hat Enterprise Linux: Red Hat Enterprise Linux (RHEL) is a proprietary Linux-based operating system developed by Red Hat. It is commonly used for server use and is known for its stability and security.
6. SUSE Linux Enterprise Server: SUSE Linux Enterprise Server (SLES) is a proprietary Linux-based operating system developed by SUSE. It is commonly used for server use and is known for its stability and security.
7. IBM z/OS: This is a proprietary operating system developed by IBM for their mainframe computers.
8. IBM i: This is another proprietary operating system developed by IBM for their midrange computers.
9. VMS: VMS (Virtual Memory System) is a proprietary operating system developed by Digital Equipment Corporation (DEC) for their VAX and Alpha server systems.
10. OpenVMS: OpenVMS is a successor to VMS, also developed by DEC, which was later acquired by HP.
11. OS/400: This is a proprietary operating system developed by IBM for their AS/400 and iSeries computers.
12. Solaris: Solaris is a proprietary operating system developed by Sun Microsystems, which was later acquired by Oracle Corporation. It is used on their SPARC-based servers.
13. AIX: AIX (Advanced Interactive eXecutive) is a proprietary operating system developed by IBM for their Power Systems servers.
14. HP-UX: HP-UX (Hewlett Packard-Unix) is a proprietary operating system developed by Hewlett-Packard (now Hewlett Packard Enterprise) for their HP 9000 and Integrity server systems.
These are just a few examples, and there are many other proprietary operating systems and servers available on the market.
Some examples of servers that run these operating systems are:
- IBM zSeries mainframes for z/OS and iSeries servers for OS/400 and IBM i.
- DEC VAX and Alpha server systems for VMS and OpenVMS.
- SPARC-based servers for Solaris.
- IBM Power Systems servers for AIX.
- HP 9000 and Integrity servers for HP-UX.
Here is a list of servers that run some of the operating systems I mentioned in my previous answer:
- IBM zSeries mainframes: These servers run IBM's proprietary operating systems, including z/OS and IBM i.
- IBM iSeries servers: These servers run IBM's proprietary operating system, OS/400, which has been renamed to IBM i.
- DEC VAX and Alpha server systems: These servers run Digital Equipment Corporation's proprietary operating systems, VMS and OpenVMS.
- Sun SPARC-based servers: These servers run Solaris, a proprietary operating system developed by Sun Microsystems, which was later acquired by Oracle Corporation.
- IBM Power Systems servers: These servers run AIX, a proprietary operating system developed by IBM.
- Hewlett-Packard (now Hewlett Packard Enterprise) servers: These servers run HP-UX, a proprietary operating system developed by Hewlett-Packard for their HP 9000 and Integrity server systems.
Here is a list of some of the top IT server manufacturing companies and a brief overview of their product lines:
- Dell Technologies - Dell Technologies offers a wide range of server solutions including PowerEdge rack servers, modular servers, tower servers, and blade servers.
- Hewlett-Packard Enterprise (HPE) - HPE offers a variety of server solutions including ProLiant rack and tower servers, Apollo high-performance computing servers, and Moonshot microservers.
- Lenovo - Lenovo offers a range of server solutions including ThinkSystem rack servers, tower servers, blade servers, and high-density servers.
- IBM - IBM offers a range of server solutions including Power Systems servers, z Systems mainframes, and LinuxONE servers.
- Cisco - Cisco offers a range of server solutions including UCS C-Series rack servers, UCS B-Series blade servers, and UCS Mini servers.
- Fujitsu - Fujitsu offers a range of server solutions including PRIMERGY rack servers, PRIMEQUEST mission-critical servers, and SPARC servers.
- Oracle - Oracle offers a range of server solutions including SPARC servers, x86 servers, and Engineered Systems.
- Supermicro - Supermicro offers a range of server solutions including SuperServer rack servers, SuperBlade blade servers, and MicroBlade microservers.
- Huawei - Huawei offers a range of server solutions including KunLun high-end servers, FusionServer rack servers, and Atlas AI computing platforms.
This is not an exhaustive list, and many other companies manufacture servers. The products offered by these companies may vary based on the specific needs of the customer.
Here is a brief description of the server products offered by each of the companies mentioned:
- Dell Technologies: Dell's PowerEdge servers are a popular choice for businesses of all sizes. They offer a range of server options including rack servers, modular servers, tower servers, and blade servers. These servers are designed to provide high performance, reliability, and scalability to handle the demands of modern business applications.
- Hewlett-Packard Enterprise (HPE): HPE's ProLiant servers are designed for small and mid-sized businesses, as well as enterprise-level organizations. They offer a range of server options including rack and tower servers, blade servers, and high-performance computing servers. These servers are designed to deliver high performance, scalability, and energy efficiency.
- Lenovo: Lenovo's ThinkSystem servers are designed for data center environments and offer a range of server options including rack servers, tower servers, blade servers, and high-density servers. These servers are designed to provide high performance, scalability, and energy efficiency, while also offering advanced security and management features.
- IBM: IBM's server offerings include Power Systems servers, z Systems mainframes, and LinuxONE servers. Power Systems servers are designed for businesses of all sizes and are ideal for running mission-critical workloads. z Systems mainframes are designed for large-scale enterprise environments and offer unparalleled security and reliability. LinuxONE servers are designed for organizations looking to run Linux-based workloads at scale.
- Cisco: Cisco's UCS servers are designed for data center environments and offer a range of server options including rack servers, blade servers, and mini servers. These servers are designed to deliver high performance, scalability, and efficiency, while also offering advanced networking and management features.
- Fujitsu: Fujitsu's PRIMERGY servers are designed for small and mid-sized businesses, as well as enterprise-level organizations. They offer a range of server options including rack servers, tower servers, and mission-critical servers. These servers are designed to deliver high performance, scalability, and energy efficiency.
- Oracle: Oracle's server offerings include SPARC servers, x86 servers, and Engineered Systems. SPARC servers are designed for running mission-critical applications and offer high performance and reliability. x86 servers are designed for businesses of all sizes and offer a range of performance and scalability options. Engineered Systems are pre-configured hardware and software solutions designed to run specific workloads such as databases or analytics.
- Supermicro: Supermicro's server offerings include SuperServer rack servers, SuperBlade blade servers, and MicroBlade microservers. These servers are designed for a range of use cases including data center environments, cloud computing, and high-performance computing.
- Huawei: Huawei's server offerings include KunLun high-end servers, FusionServer rack servers, and Atlas AI computing platforms. These servers are designed for businesses of all sizes and offer a range of performance and scalability options, as well as advanced features such as AI acceleration and high-density computing.
All of the servers mentioned are still in production today, although some of them may have newer and more advanced models available.
For example, IBM zSeries mainframes have continued to evolve with new models and capabilities, and IBM iSeries servers have been rebranded as IBM Power Systems running IBM i.
DEC VAX and Alpha servers are no longer being produced, but OpenVMS continues to be supported and is used by some organizations for mission-critical applications.
Sun SPARC-based servers are still in production, with Oracle continuing to develop and support Solaris as well as their SPARC hardware platform.
IBM Power Systems servers are also still in production, with newer models available that offer improved performance and capabilities.
Hewlett Packard Enterprise continues to support HP-UX, although they have shifted their focus towards their newer Linux-based operating system, called HPE OpenVMS.
Fujitsu is a Japanese multinational information technology equipment and services company that offers a wide range of server products for various applications. Here are some of the server models offered by Fujitsu, along with the operating systems that are typically run on them:
- PRIMERGY servers: Fujitsu's PRIMERGY servers are designed for small, medium, and large enterprises, and can run a variety of operating systems, including Windows Server, VMware, and Linux (such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server).
- PRIMEQUEST servers: Fujitsu's PRIMEQUEST servers are designed for mission-critical applications and can run Windows Server, VMware, and Linux (such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server), as well as Fujitsu's proprietary operating system, Solaris.
- SPARC M12 servers: Fujitsu's SPARC M12 servers are based on the Oracle SPARC architecture and can run the Oracle Solaris operating system.
- BS2000 servers: Fujitsu's BS2000 servers are designed for mainframe-class applications and can run Fujitsu's proprietary operating system, BS2000/OSD.
- ETERNUS storage systems: Fujitsu's ETERNUS storage systems can support a wide range of operating systems, including Windows, Linux, and Unix.
Note that Fujitsu offers many other server and storage products, and the specific operating system that can run on them may vary depending on the model and configuration.
BS2000/OSD is a proprietary operating system developed by Fujitsu for its mainframe-class BS2000 servers. The acronym "OSD" stands for "Operating System Division" and represents the division within Fujitsu that is responsible for developing and maintaining the operating system.
BS2000/OSD is designed for high reliability, availability, and scalability, and can support large-scale, mission-critical applications. It includes features such as virtualization, workload management, and fault tolerance to ensure that applications can run continuously and reliably even in the face of hardware failures.
The operating system is designed to support multiple programming languages, including COBOL, PL/I, Assembler, and C/C++, as well as various database systems such as Oracle, IBM DB2, and SAP HANA. It also includes built-in security features such as access control, authentication, and encryption to protect sensitive data and ensure compliance with regulatory requirements.
BS2000/OSD can be customized and configured to meet the specific requirements of a given application or workload and can run multiple instances of the operating system on a single physical server. This allows for efficient use of resources and can help to reduce costs and complexity in large-scale computing environments.
Servers typically use processors that are designed for high performance and high reliability, as they are expected to handle heavy workloads and operate continuously. Here are some of the most common types of processors used in servers:
- x86 processors: These processors are based on the Intel x86 architecture and are widely used in servers. They are known for their versatility, power efficiency, and high performance.
- ARM processors: These processors are based on the ARM architecture and are increasingly being used in servers, particularly for energy-efficient workloads. They are commonly used in low-power servers, IoT devices, and edge computing applications.
- Power processors: These processors are designed by IBM and are used in IBM Power Systems servers. They are known for their high performance and scalability, as well as their support for virtualization and workload consolidation.
- SPARC processors: These processors are designed by Oracle and are used in Sun SPARC-based servers. They are known for their high reliability, availability, and serviceability, as well as their support for mission-critical applications.
- MIPS processors: These processors are used in a variety of server and networking applications, particularly in embedded systems and routers. They are known for their power efficiency and low cost.
Each type of processor has its advantages and disadvantages, and the choice of a processor depends on the specific requirements of the server workload. Factors like performance, power efficiency, scalability, and compatibility with software applications all need to be considered when selecting a processor for a server.
SISC (Single Instruction Set Computer) and RISC (Reduced Instruction Set Computer) are two different types of processor architectures.
SISC processors are designed to handle a wide range of instructions and operations, making them more flexible but also more complex. They can execute instructions that perform a variety of tasks, which allows them to run a wide range of software applications. However, the complexity of SISC processors can make them slower and less efficient when executing certain types of instructions, which can limit their performance for specific workloads.
RISC processors, on the other hand, are designed to execute a smaller set of simple and efficient instructions. This allows them to perform specific operations quickly and efficiently, which can make them well-suited for certain types of workloads like database processing, scientific computing, and image processing. RISC processors also tend to have a simpler and more streamlined design, which can make them easier to manufacture and less expensive to produce.
Overall, the choice of processor architecture depends on the specific requirements of the server workload. Workloads that require a wide range of operations may benefit from SISC processors, while workloads that require fast and efficient execution of specific instructions may benefit from RISC processors.
Here is a list of processors in both SISC and RISC categories:
SISC processors:
- Intel x86 processors (e.g., Intel Core i7, Intel Xeon)
- AMD processors (e.g., AMD Ryzen, AMD EPYC)
- IBM System z processors (e.g., z14, z15)
- Fujitsu SPARC64 processors (e.g., SPARC64 IXfx, SPARC64 XIfx)
RISC processors:
- ARM processors (e.g., ARM Cortex-A, ARM Cortex-M)
- IBM POWER processors (e.g., POWER9, POWER10)
- Oracle SPARC processors (e.g., SPARC T8, SPARC M8)
- MIPS processors (e.g., MIPS32, MIPS64)
Note that some processors can fall into both categories, depending on how they are designed and optimized. For example, Intel Xeon processors are primarily SISC processors but have some RISC-like features and optimizations for specific workloads. Similarly, some ARM processors can support a wider range of instructions and may have more SISC-like characteristics, while others are optimized for specific tasks and have more RISC-like features.
A Guide to Servers: Their Usage, History, and Evolution

Servers have become an essential part of modern technology. They are used for a wide range of purposes, including data storage, communication, and cloud computing. In this blog, we will explore the history of servers, their evolution, and their importance in the digital age.
History of Servers:
Servers have been around since the early days of computing. In the 1960s, mainframe computers were used as servers to store and process data. These early servers were large and expensive, and only large corporations and government agencies could afford to use them.
As technology evolved, servers became smaller and more affordable. In the 1980s, personal computers became popular, and companies began using them as servers for local networks. In the 1990s, the Internet became widely available, and servers were used to host websites and provide email services.
Evolution of Servers:
As technology continued to evolve, servers became more powerful and versatile. Today, servers are used for a wide range of purposes, including data storage, communication, cloud computing, and virtualization.
Cloud computing has become particularly popular in recent years. With cloud computing, servers are used to store and process data in remote locations, allowing users to access their data from anywhere in the world. This has led to a shift away from traditional on-premises servers to cloud-based servers.
Usage of Servers:
Servers are used for a wide range of purposes, including:
1. Data Storage: Servers are used to store data, including documents, images, and videos. They provide a centralized location for data storage, making it easy for users to access their data from anywhere.
2. Communication: Servers are used to provide email, chat, and other communication services. They allow users to communicate with each other in real-time, no matter where they are located.
3. Cloud Computing: Servers are used to provide cloud computing services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). These services allow users to access computing resources on demand, without having to invest in their hardware.
4. Virtualization: Servers are used to provide virtualization services, allowing multiple virtual machines to run on a single physical server. This can help organizations save money on hardware costs and reduce their environmental footprint.
Servers have come a long way since their early days as mainframe computers. Today, they are an essential part of modern technology, used for a wide range of purposes. With cloud computing and virtualization, servers are more powerful and versatile than ever before. As technology continues to evolve, servers will undoubtedly play an increasingly important role in the digital age.
Servers can be broadly categorized into different types based on their function, hardware specifications, and intended usage. Here are some of the most common types of servers and a brief explanation of each:
1. Web servers: These servers are designed to host websites and web applications. They typically run specialized software like Apache or Nginx that can handle HTTP requests and serve static and dynamic content to web clients.
2. Database servers: These servers are optimized for storing, managing, and retrieving data from databases. They typically run database management systems (DBMS) like MySQL, Oracle, or Microsoft SQL Server.
3. Application servers: These servers provide a runtime environment for running applications. They can run on a variety of platforms and languages like Java, .NET, or Python.
4. Mail servers: These servers are used to handle email traffic, storing and forwarding messages between mail clients and other mail servers. They typically run specialized software like Postfix or Sendmail.
5. File servers: These servers are used to store and manage files and provide access to them over a network. They may use a variety of protocols like SMB, NFS, or FTP to allow clients to access shared files.
6. Print servers: These servers are used to manage printing services on a network. They typically run specialized software that can handle multiple print requests from different clients and manage print queues.
7. DNS servers: These servers are used to resolve domain names into IP addresses. They typically run a DNS server software like BIND or Windows DNS Server.
8. Proxy servers: These servers act as intermediaries between clients and other servers on a network. They can be used for caching content, filtering requests, or enhancing security.
There are many other types of servers as well, but these are some of the most common. Each type of server has its own hardware and software requirements, as well as specific configuration and management considerations.
Servers typically use processors that are designed for high performance and high reliability, as they are expected to handle heavy workloads and operate continuously. Here are some of the most common types of processors used in servers:
- x86 processors: These processors are based on the Intel x86 architecture and are widely used in servers. They are known for their versatility, power efficiency, and high performance.
- ARM processors: These processors are based on the ARM architecture and are increasingly being used in servers, particularly for energy-efficient workloads. They are commonly used in low-power servers, IoT devices, and edge computing applications.
- Power processors: These processors are designed by IBM and are used in IBM Power Systems servers. They are known for their high performance and scalability, as well as their support for virtualization and workload consolidation.
- SPARC processors: These processors are designed by Oracle and are used in Sun SPARC-based servers. They are known for their high reliability, availability, and serviceability, as well as their support for mission-critical applications.
- MIPS processors: These processors are used in a variety of server and networking applications, particularly in embedded systems and routers. They are known for their power efficiency and low cost.
Each type of processor has its advantages and disadvantages, and the choice of a processor depends on the specific requirements of the server workload. Factors like performance, power efficiency, scalability, and compatibility with software applications all need to be considered when selecting a processor for a server.
The processors used in servers can vary depending on the specific model and configuration. However, here is a general overview of the types of processors used by the server manufacturers mentioned earlier:
- Dell Technologies: Dell's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Hewlett-Packard Enterprise (HPE): HPE's servers also use processors from Intel and AMD, including Xeon and EPYC processors.
- Lenovo: Lenovo's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- IBM: IBM's servers use processors from IBM's own POWER family, as well as processors from Intel and AMD.
- Cisco: Cisco's servers use processors from Intel, including Xeon processors.
- Fujitsu: Fujitsu's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Oracle: Oracle's servers use processors from Oracle's own SPARC family, as well as processors from Intel and AMD.
- Supermicro: Supermicro's servers use processors from Intel and AMD, including Xeon and EPYC processors.
- Huawei: Huawei's servers use processors from Huawei's own Kunpeng and Ascend families, as well as processors from Intel and AMD.
In terms of operating systems, the servers listed here can typically run a wide range of operating systems. Common operating systems include:
- Windows Server
- Linux (including Red Hat, CentOS, and Ubuntu)
- Unix (including AIX, HP-UX, and Solaris)
- VMware ESXi
- Citrix Hypervisor
- FreeBSD
However, the specific operating systems supported by a server will depend on its hardware and firmware, as well as the drivers and software available for that particular platform.
Here is a list of some proprietary operating systems and the servers that run these operating systems:
- IBM i: IBM i is a proprietary operating system from IBM that runs on IBM Power Systems servers. IBM i is designed for mid-sized and large organizations and provides a high level of reliability, security, and scalability. IBM i includes many built-in applications and services, including a database management system, web server, and application server.
- z/OS: z/OS is a proprietary operating system from IBM that runs on IBM Z Systems mainframe servers. z/OS is designed for large-scale enterprise environments and provides high performance, reliability, and security. z/OS includes many built-in applications and services, including a database management system, web server, and application server.
- Oracle Solaris: Oracle Solaris is a proprietary operating system from Oracle that runs on Oracle servers. Solaris is designed for businesses of all sizes and provides advanced features such as built-in virtualization, advanced file systems, and integrated security. Solaris includes many built-in applications and services, including a database management system, web server, and application server.
- HPE NonStop: HPE NonStop is a proprietary operating system from Hewlett Packard Enterprise that runs on HPE NonStop servers. NonStop is designed for organizations that require high availability, high performance, and high scalability. NonStop includes many built-in applications and services, including a database management system, web server, and application server.
- Unisys OS 2200: Unisys OS 2200 is a proprietary operating system from Unisys that runs on Unisys ClearPath servers. OS 2200 is designed for businesses of all sizes and provides high reliability, security, and scalability. OS 2200 includes many built-in applications and services, including a database management system, web server, and application server.
Here's a list of some popular proprietary operating systems and the servers that run them:
1. Microsoft Windows Server: This operating system is developed by Microsoft and is designed for server use. It is used by many organizations for various purposes, including web servers, database servers, and application servers.
2. IBM AIX: AIX is a proprietary operating system developed by IBM for use on their servers. It is commonly used in enterprise environments and is known for its reliability and scalability.
3. Oracle Solaris: Solaris is a Unix-based proprietary operating system developed by Oracle. It is commonly used for mission-critical applications and database servers.
4. HP-UX: HP-UX is a proprietary Unix-based operating system developed by Hewlett Packard (now HP Enterprise). It is commonly used in enterprise environments and is known for its scalability and reliability.
5. Red Hat Enterprise Linux: Red Hat Enterprise Linux (RHEL) is a proprietary Linux-based operating system developed by Red Hat. It is commonly used for server use and is known for its stability and security.
6. SUSE Linux Enterprise Server: SUSE Linux Enterprise Server (SLES) is a proprietary Linux-based operating system developed by SUSE. It is commonly used for server use and is known for its stability and security.
7. IBM z/OS: This is a proprietary operating system developed by IBM for their mainframe computers.
8. IBM i: This is another proprietary operating system developed by IBM for their midrange computers.
9. VMS: VMS (Virtual Memory System) is a proprietary operating system developed by Digital Equipment Corporation (DEC) for their VAX and Alpha server systems.
10. OpenVMS: OpenVMS is a successor to VMS, also developed by DEC, which was later acquired by HP.
11. OS/400: This is a proprietary operating system developed by IBM for their AS/400 and iSeries computers.
12. Solaris: Solaris is a proprietary operating system developed by Sun Microsystems, which was later acquired by Oracle Corporation. It is used on their SPARC-based servers.
13. AIX: AIX (Advanced Interactive eXecutive) is a proprietary operating system developed by IBM for their Power Systems servers.
14. HP-UX: HP-UX (Hewlett Packard-Unix) is a proprietary operating system developed by Hewlett-Packard (now Hewlett Packard Enterprise) for their HP 9000 and Integrity server systems.
These are just a few examples, and there are many other proprietary operating systems and servers available on the market.
Some examples of servers that run these operating systems are:
- IBM zSeries mainframes for z/OS and iSeries servers for OS/400 and IBM i.
- DEC VAX and Alpha server systems for VMS and OpenVMS.
- SPARC-based servers for Solaris.
- IBM Power Systems servers for AIX.
- HP 9000 and Integrity servers for HP-UX.
Here is a list of servers that run some of the operating systems I mentioned in my previous answer:
- IBM zSeries mainframes: These servers run IBM's proprietary operating systems, including z/OS and IBM i.
- IBM iSeries servers: These servers run IBM's proprietary operating system, OS/400, which has been renamed to IBM i.
- DEC VAX and Alpha server systems: These servers run Digital Equipment Corporation's proprietary operating systems, VMS and OpenVMS.
- Sun SPARC-based servers: These servers run Solaris, a proprietary operating system developed by Sun Microsystems, which was later acquired by Oracle Corporation.
- IBM Power Systems servers: These servers run AIX, a proprietary operating system developed by IBM.
- Hewlett-Packard (now Hewlett Packard Enterprise) servers: These servers run HP-UX, a proprietary operating system developed by Hewlett-Packard for their HP 9000 and Integrity server systems.
Here is a list of some of the top IT server manufacturing companies and a brief overview of their product lines:
- Dell Technologies - Dell Technologies offers a wide range of server solutions including PowerEdge rack servers, modular servers, tower servers, and blade servers.
- Hewlett-Packard Enterprise (HPE) - HPE offers a variety of server solutions including ProLiant rack and tower servers, Apollo high-performance computing servers, and Moonshot microservers.
- Lenovo - Lenovo offers a range of server solutions including ThinkSystem rack servers, tower servers, blade servers, and high-density servers.
- IBM - IBM offers a range of server solutions including Power Systems servers, z Systems mainframes, and LinuxONE servers.
- Cisco - Cisco offers a range of server solutions including UCS C-Series rack servers, UCS B-Series blade servers, and UCS Mini servers.
- Fujitsu - Fujitsu offers a range of server solutions including PRIMERGY rack servers, PRIMEQUEST mission-critical servers, and SPARC servers.
- Oracle - Oracle offers a range of server solutions including SPARC servers, x86 servers, and Engineered Systems.
- Supermicro - Supermicro offers a range of server solutions including SuperServer rack servers, SuperBlade blade servers, and MicroBlade microservers.
- Huawei - Huawei offers a range of server solutions including KunLun high-end servers, FusionServer rack servers, and Atlas AI computing platforms.
This is not an exhaustive list, and many other companies manufacture servers. The products offered by these companies may vary based on the specific needs of the customer.
Here is a brief description of the server products offered by each of the companies mentioned:
- Dell Technologies: Dell's PowerEdge servers are a popular choice for businesses of all sizes. They offer a range of server options including rack servers, modular servers, tower servers, and blade servers. These servers are designed to provide high performance, reliability, and scalability to handle the demands of modern business applications.
- Hewlett-Packard Enterprise (HPE): HPE's ProLiant servers are designed for small and mid-sized businesses, as well as enterprise-level organizations. They offer a range of server options including rack and tower servers, blade servers, and high-performance computing servers. These servers are designed to deliver high performance, scalability, and energy efficiency.
- Lenovo: Lenovo's ThinkSystem servers are designed for data center environments and offer a range of server options including rack servers, tower servers, blade servers, and high-density servers. These servers are designed to provide high performance, scalability, and energy efficiency, while also offering advanced security and management features.
- IBM: IBM's server offerings include Power Systems servers, z Systems mainframes, and LinuxONE servers. Power Systems servers are designed for businesses of all sizes and are ideal for running mission-critical workloads. z Systems mainframes are designed for large-scale enterprise environments and offer unparalleled security and reliability. LinuxONE servers are designed for organizations looking to run Linux-based workloads at scale.
- Cisco: Cisco's UCS servers are designed for data center environments and offer a range of server options including rack servers, blade servers, and mini servers. These servers are designed to deliver high performance, scalability, and efficiency, while also offering advanced networking and management features.
- Fujitsu: Fujitsu's PRIMERGY servers are designed for small and mid-sized businesses, as well as enterprise-level organizations. They offer a range of server options including rack servers, tower servers, and mission-critical servers. These servers are designed to deliver high performance, scalability, and energy efficiency.
- Oracle: Oracle's server offerings include SPARC servers, x86 servers, and Engineered Systems. SPARC servers are designed for running mission-critical applications and offer high performance and reliability. x86 servers are designed for businesses of all sizes and offer a range of performance and scalability options. Engineered Systems are pre-configured hardware and software solutions designed to run specific workloads such as databases or analytics.
- Supermicro: Supermicro's server offerings include SuperServer rack servers, SuperBlade blade servers, and MicroBlade microservers. These servers are designed for a range of use cases including data center environments, cloud computing, and high-performance computing.
- Huawei: Huawei's server offerings include KunLun high-end servers, FusionServer rack servers, and Atlas AI computing platforms. These servers are designed for businesses of all sizes and offer a range of performance and scalability options, as well as advanced features such as AI acceleration and high-density computing.
All of the servers mentioned are still in production today, although some of them may have newer and more advanced models available.
For example, IBM zSeries mainframes have continued to evolve with new models and capabilities, and IBM iSeries servers have been rebranded as IBM Power Systems running IBM i.
DEC VAX and Alpha servers are no longer being produced, but OpenVMS continues to be supported and is used by some organizations for mission-critical applications.
Sun SPARC-based servers are still in production, with Oracle continuing to develop and support Solaris as well as their SPARC hardware platform.
IBM Power Systems servers are also still in production, with newer models available that offer improved performance and capabilities.
Hewlett Packard Enterprise continues to support HP-UX, although they have shifted their focus towards their newer Linux-based operating system, called HPE OpenVMS.
Fujitsu is a Japanese multinational information technology equipment and services company that offers a wide range of server products for various applications. Here are some of the server models offered by Fujitsu, along with the operating systems that are typically run on them:
- PRIMERGY servers: Fujitsu's PRIMERGY servers are designed for small, medium, and large enterprises, and can run a variety of operating systems, including Windows Server, VMware, and Linux (such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server).
- PRIMEQUEST servers: Fujitsu's PRIMEQUEST servers are designed for mission-critical applications and can run Windows Server, VMware, and Linux (such as Red Hat Enterprise Linux and SUSE Linux Enterprise Server), as well as Fujitsu's proprietary operating system, Solaris.
- SPARC M12 servers: Fujitsu's SPARC M12 servers are based on the Oracle SPARC architecture and can run the Oracle Solaris operating system.
- BS2000 servers: Fujitsu's BS2000 servers are designed for mainframe-class applications and can run Fujitsu's proprietary operating system, BS2000/OSD.
- ETERNUS storage systems: Fujitsu's ETERNUS storage systems can support a wide range of operating systems, including Windows, Linux, and Unix.
Note that Fujitsu offers many other server and storage products, and the specific operating system that can run on them may vary depending on the model and configuration.
BS2000/OSD is a proprietary operating system developed by Fujitsu for its mainframe-class BS2000 servers. The acronym "OSD" stands for "Operating System Division" and represents the division within Fujitsu that is responsible for developing and maintaining the operating system.
BS2000/OSD is designed for high reliability, availability, and scalability, and can support large-scale, mission-critical applications. It includes features such as virtualization, workload management, and fault tolerance to ensure that applications can run continuously and reliably even in the face of hardware failures.
The operating system is designed to support multiple programming languages, including COBOL, PL/I, Assembler, and C/C++, as well as various database systems such as Oracle, IBM DB2, and SAP HANA. It also includes built-in security features such as access control, authentication, and encryption to protect sensitive data and ensure compliance with regulatory requirements.
BS2000/OSD can be customized and configured to meet the specific requirements of a given application or workload and can run multiple instances of the operating system on a single physical server. This allows for efficient use of resources and can help to reduce costs and complexity in large-scale computing environments.
Servers typically use processors that are designed for high performance and high reliability, as they are expected to handle heavy workloads and operate continuously. Here are some of the most common types of processors used in servers:
- x86 processors: These processors are based on the Intel x86 architecture and are widely used in servers. They are known for their versatility, power efficiency, and high performance.
- ARM processors: These processors are based on the ARM architecture and are increasingly being used in servers, particularly for energy-efficient workloads. They are commonly used in low-power servers, IoT devices, and edge computing applications.
- Power processors: These processors are designed by IBM and are used in IBM Power Systems servers. They are known for their high performance and scalability, as well as their support for virtualization and workload consolidation.
- SPARC processors: These processors are designed by Oracle and are used in Sun SPARC-based servers. They are known for their high reliability, availability, and serviceability, as well as their support for mission-critical applications.
- MIPS processors: These processors are used in a variety of server and networking applications, particularly in embedded systems and routers. They are known for their power efficiency and low cost.
Each type of processor has its advantages and disadvantages, and the choice of a processor depends on the specific requirements of the server workload. Factors like performance, power efficiency, scalability, and compatibility with software applications all need to be considered when selecting a processor for a server.
SISC (Single Instruction Set Computer) and RISC (Reduced Instruction Set Computer) are two different types of processor architectures.
SISC processors are designed to handle a wide range of instructions and operations, making them more flexible but also more complex. They can execute instructions that perform a variety of tasks, which allows them to run a wide range of software applications. However, the complexity of SISC processors can make them slower and less efficient when executing certain types of instructions, which can limit their performance for specific workloads.
RISC processors, on the other hand, are designed to execute a smaller set of simple and efficient instructions. This allows them to perform specific operations quickly and efficiently, which can make them well-suited for certain types of workloads like database processing, scientific computing, and image processing. RISC processors also tend to have a simpler and more streamlined design, which can make them easier to manufacture and less expensive to produce.
Overall, the choice of processor architecture depends on the specific requirements of the server workload. Workloads that require a wide range of operations may benefit from SISC processors, while workloads that require fast and efficient execution of specific instructions may benefit from RISC processors.
Here is a list of processors in both SISC and RISC categories:
SISC processors:
- Intel x86 processors (e.g., Intel Core i7, Intel Xeon)
- AMD processors (e.g., AMD Ryzen, AMD EPYC)
- IBM System z processors (e.g., z14, z15)
- Fujitsu SPARC64 processors (e.g., SPARC64 IXfx, SPARC64 XIfx)
RISC processors:
- ARM processors (e.g., ARM Cortex-A, ARM Cortex-M)
- IBM POWER processors (e.g., POWER9, POWER10)
- Oracle SPARC processors (e.g., SPARC T8, SPARC M8)
- MIPS processors (e.g., MIPS32, MIPS64)
Note that some processors can fall into both categories, depending on how they are designed and optimized. For example, Intel Xeon processors are primarily SISC processors but have some RISC-like features and optimizations for specific workloads. Similarly, some ARM processors can support a wider range of instructions and may have more SISC-like characteristics, while others are optimized for specific tasks and have more RISC-like features.
A Comprehensive Guide to Digital Data Storage: Types, Architectures, and Switches
In today's digital age, storing data has become a crucial aspect of personal and business operations. However, with the multitude of storage options available, it can be challenging to choose the most suitable solution. This guide aims to provide a comprehensive overview of the most common storage types, including Hard Disk Drives (HDDs), Solid State Drives (SSDs), Hybrid Drives, Network-Attached Storage (NAS), and Storage Area Networks (SAN). It will also explain the architectures of SAN and NAS and their ideal use cases, followed by a comparison between the two. Finally, it will delve into the types of switches that can be used in a SAN environment, their features, and their pros and cons.
There are various types of storage available for storing digital data, each with its advantages and disadvantages. Here is an explanation of the most common storage types:
1. Hard Disk Drives (HDDs): HDDs are a traditional form of storage that has been used for decades. They are made up of spinning disks that store data magnetically. HDDs are affordable and can store large amounts of data, making them a popular choice for personal and enterprise storage. However, they are relatively slow in terms of read/write speeds and can be vulnerable to physical damage.
2. Solid State Drives (SSDs): SSDs are a newer form of storage that uses flash memory to store data. They are faster and more reliable than HDDs, making them a popular choice for high-performance applications. SSDs also consume less power, generate less heat, and are less vulnerable to physical damage than HDDs. However, SSDs are typically more expensive than HDDs and have a limited number of write cycles.
3. Hybrid Drives: Hybrid drives combine the benefits of both HDDs and SSDs by using both spinning disks and flash memory. The spinning disks store most of the data, while the flash memory is used as a cache to speed up frequently accessed files. Hybrid drives offer a good balance of performance and affordability, making them a popular choice for personal and business use.
4. Network-Attached Storage (NAS): NAS is a type of storage that is connected to a network and accessed over the network. NAS can be made up of one or more HDDs or SSDs, and it provides a central location for storing and sharing data. NAS is a scalable solution that can be easily expanded as needed. It is commonly used for personal and small business storage.
5. Storage Area Network (SAN): SAN is a high-performance storage solution that is typically used in enterprise environments. SAN consists of a dedicated network of storage devices that are connected to servers. SAN provides high-speed access to data and offers advanced features such as data replication, backup, and disaster recovery.
The choice of storage type will depend on the specific needs of the user or organization, including factors such as performance, reliability, cost, scalability, and data security.
SAN (Storage Area Network) and NAS (Network-Attached Storage) are two different storage architectures used to provide access to digital data. Here is an explanation of their architectures and ideal use cases, as well as a comparison between the two:
SAN Architecture: A SAN is a dedicated network of storage devices that are connected to servers. It uses Fibre Channel or iSCSI protocols to provide high-speed access to data. SANs are typically deployed in enterprise environments where high performance and reliability are critical. The architecture of SAN consists of the following components:
1. Storage devices: SANs use disk arrays or other types of storage devices that are connected to the SAN network.
2. Host Bus Adapters (HBAs): HBAs are specialized network adapters that connect servers to the SAN network.
3. Switches: SANs use switches to connect storage devices to servers and manage data traffic on the network.
4. Storage management software: SANs use management software to monitor and manage the storage devices and the SAN network.
NAS Architecture: NAS is a file-based storage architecture that provides a centralized location for storing and sharing data. NAS devices are connected to a network and accessed over the network using protocols such as NFS or SMB. The architecture of NAS consists of the following components:
1. NAS devices: NAS devices can be made up of one or more HDDs or SSDs and are connected to a network.
2. Network interface: NAS devices have a network interface that allows them to be accessed over the network.
3. File system: NAS devices use a file system to organize and store data.
4. NAS management software: NAS devices use management software to manage the file system and network access.
Ideal Uses of SAN and NAS: SANs are ideal for high-performance applications such as large-scale database storage, virtualization, and high-performance computing. They provide fast, reliable access to data and support advanced features such as data replication, backup, and disaster recovery. SANs are commonly used in enterprise environments such as data centers and large corporations.
NAS devices are ideal for personal and small business storage needs, such as file sharing, media streaming, and backup. NAS devices are simple to set up and use, and they provide a central location for storing and sharing data. NAS devices can be easily expanded as needed, making them a scalable solution for growing storage needs.
Comparison of SAN and NAS: The main difference between SAN and NAS is in their architecture and the way they provide access to data. SANs are block-based architecture that provides high-speed access to data, while NAS is a file-based architecture that provides a centralized location for storing and sharing data. SANs are typically used in enterprise environments where high performance and reliability are critical, while NAS devices are ideal for personal and small business storage needs.
Both SAN and NAS architectures have their own set of advantages and are suited for specific use cases. The choice between SAN and NAS will depend on the specific needs of the user or organization, including factors such as performance, reliability, cost, scalability, and data security.
Several types of switches can be used in a SAN (Storage Area Network) architecture. Here is a list of the most common types of SAN switches, along with their explanations and a comparison of their pros and cons:
1. Fibre Channel (FC) Switches: Fibre Channel switches are designed to handle high-speed data transfer in SAN environments. They are available in different port configurations and can support data rates of up to 32 Gbps. FC switches provide low latency, high throughput, and advanced features such as QoS (Quality of Service), fabric zoning, and ISL (Inter-Switch Link) trunking. However, they are typically more expensive than other types of switches and require specialized knowledge to set up and manage.
2. iSCSI (Internet Small Computer System Interface) Switches: iSCSI switches are designed to connect servers to SAN storage using Ethernet-based networks. They are more cost-effective than FC switches and can support data rates of up to 40 Gbps. iSCSI switches are easy to set up and manage, and they can be used with existing Ethernet networks. However, they can have higher latency and lower throughput than FC switches, and they may require additional hardware such as TCP offload engines (TOEs) to improve performance.
3. InfiniBand Switches: InfiniBand switches are designed for high-performance computing (HPC) environments and can support data rates of up to 200 Gbps. They provide low latency and high throughput, making them ideal for HPC applications such as scientific simulations and data analysis. However, they are less common in SAN environments than FC and iSCSI switches and may require specialized knowledge to set up and manage.
4. FCoE (Fibre Channel over Ethernet) Switches: FCoE switches are designed to allow Fibre Channel traffic to be transmitted over Ethernet networks. They can support data rates of up to 40 Gbps and provide a cost-effective way to integrate Fibre Channel storage into existing Ethernet networks. However, they may require specialized hardware such as converged network adapters (CNAs) and lossless Ethernet switches to ensure high performance and reliability.
5. Cisco MDS (Multilayer Data Switch) Switches: Cisco MDS switches are designed for enterprise SAN environments and provide advanced features such as fabric zoning, virtual SANs, and data encryption. They are available in a range of port configurations and can support data rates of up to 32 Gbps. However, they are typically more expensive than other types of switches and require specialized knowledge to set up and manage.
The choice of SAN switch will depend on the specific needs of the user or organization, including factors such as performance, scalability, reliability, and cost. FC switches provide the highest performance and advanced features but are typically more expensive, while iSCSI switches offer a cost-effective alternative that is easy to set up and manage. InfiniBand switches are ideal for HPC environments, while FCoE switches provide a way to integrate Fibre Channel storage into existing Ethernet networks. Cisco MDS switches provide advanced features for enterprise SAN environments but are typically more expensive and require specialized knowledge to manage.
Storage management software is used to manage and monitor the storage resources in SAN and NAS environments. Here are some common types of storage management software, along with their explanations and a comparison of their pros and cons:
1. SAN Management Software: SAN management software is designed to manage the storage resources in a SAN environment. It can provide features such as storage provisioning, capacity planning, performance monitoring, and troubleshooting. SAN management software can also provide features such as fabric zoning and virtual SANs, which allow administrators to segment the SAN into logical units. Some examples of SAN management software include IBM SAN Volume Controller, EMC ControlCenter, and NetApp OnCommand.
Pros: SAN management software provides advanced features for managing SAN environments and can help optimize performance and utilization. It can also provide centralized management and monitoring of multiple SAN devices.
Cons: SAN management software can be expensive and may require specialized knowledge to set up and manage. It can also be complex and may require additional hardware or software to function properly.
2. NAS Management Software: NAS management software is designed to manage the storage resources in a NAS environment. It can provide features such as file sharing, file access control, file system management, and backup and restore. NAS management software can also provide features such as data deduplication and compression, which can help reduce storage costs. Some examples of NAS management software include Microsoft Windows Storage Server, FreeNAS, and Openfiler.
Pros: NAS management software provides an easy-to-use interface for managing NAS environments and can be less expensive than SAN management software. It can also provide advanced features such as data deduplication and compression, which can help reduce storage costs.
Cons: NAS management software may not provide the advanced features of SAN management software, and may not be suitable for high-performance applications.
3. Storage Resource Management (SRM) Software: SRM software is designed to manage storage resources across both SAN and NAS environments. It can provide features such as capacity planning, performance monitoring, backup and restore, and file system management. SRM software can also provide features such as data classification and tiering, which can help optimize storage utilization. Some examples of SRM software include IBM Tivoli Storage Manager, EMC ControlCenter, and SolarWinds Storage Resource Monitor.
Pros: SRM software provides a comprehensive solution for managing both SAN and NAS environments, and can help optimize storage utilization and performance. It can also provide centralized management and monitoring of multiple storage devices.
Cons: SRM software can be expensive and may require specialized knowledge to set up and manage. It can also be complex and may require additional hardware or software to function properly.
The choice of storage management software will depend on the specific needs of the user or organization, including factors such as the type of storage environment, the level of complexity, and the desired features. SAN management software provides advanced features for managing SAN environments, while NAS management software provides an easy-to-use interface for managing NAS environments. SRM software provides a comprehensive solution for managing both SAN and NAS
There are several software products available for SAN and NAS management. Here are some common examples, along with their explanations and an evaluation of their efficiency and stability:
1. IBM SAN Volume Controller (SVC): IBM SVC is a SAN management software product that provides advanced features for managing SAN environments. It can provide features such as storage provisioning, capacity planning, performance monitoring, and troubleshooting. SVC also provides features such as fabric zoning and virtual SANs, which allow administrators to segment the SAN into logical units.
Efficiency: IBM SVC is a highly efficient SAN management software product that provides advanced features for managing complex SAN environments.
Stability: IBM SVC is a stable and reliable SAN management software product that has been used in enterprise environments for many years.
2. EMC ControlCenter: EMC ControlCenter is a SAN management software product that provides advanced features for managing SAN environments. It can provide features such as storage provisioning, capacity planning, performance monitoring, and troubleshooting. ControlCenter also provides features such as fabric zoning and virtual SANs, which allow administrators to segment the SAN into logical units.
Efficiency: EMC ControlCenter is a highly efficient SAN management software product that provides advanced features for managing complex SAN environments.
Stability: EMC ControlCenter is a stable and reliable SAN management software product that has been used in enterprise environments for many years.
3. Microsoft Windows Storage Server: Microsoft Windows Storage Server is a NAS management software product that provides an easy-to-use interface for managing NAS environments. It can provide features such as file sharing, file access control, file system management, and backup and restore.
Efficiency: Microsoft Windows Storage Server is a relatively efficient NAS management software product that provides an easy-to-use interface for managing NAS environments.
Stability: Microsoft Windows Storage Server is a stable and reliable NAS management software product that has been used in enterprise environments for many years.
4. FreeNAS: FreeNAS is an open-source NAS management software product that provides an easy-to-use interface for managing NAS environments. It can provide features such as file sharing, file access control, file system management, and backup and restore.
Efficiency: FreeNAS is a relatively efficient NAS management software product that provides an easy-to-use interface for managing NAS environments.
Stability: FreeNAS is a stable and reliable NAS management software product, although being an open-source product, it may not have the same level of support as proprietary software.
5. SolarWinds Storage Resource Monitor: SolarWinds Storage Resource Monitor is a storage resource management (SRM) software product that provides features for managing both SAN and NAS environments. It can provide features such as capacity planning, performance monitoring, backup and restore, and file system management. It can also provide features such as data classification and tiering, which can help optimize storage utilization.
Efficiency: SolarWinds Storage Resource Monitor is a highly efficient SRM software product that provides a comprehensive solution for managing both SAN and NAS environments.
Stability: SolarWinds Storage Resource Monitor is a stable and reliable SRM software product that has been used in enterprise environments for many years.
The efficiency and stability of these software products can vary depending on the specific needs of the user or organization, as well as the complexity of the storage environment. It is important to evaluate the features, cost, and support of these software products before making a decision on which one to use.
Optimizing Data Center Infrastructure for Maximum ROI

The IT infrastructure deployed in a data center plays a critical role in the performance and efficiency of an organization's operations. A well-designed infrastructure can help organizations achieve maximum ROI, while a poorly optimized one can lead to significant inefficiencies, increased costs, and reduced productivity. This whitepaper provides an overview of the key components of data center infrastructure and explores strategies for optimizing these components to achieve maximum ROI.
The growth of data and digital technologies has led to an explosion in the demand for data center infrastructure. To meet this demand, organizations must deploy an IT infrastructure that is efficient, flexible, and scalable. However, designing and deploying an optimized IT infrastructure can be a complex and challenging task. In this whitepaper, we will explore the key components of data center infrastructure, and provide strategies for optimizing these components to achieve maximum ROI.
Key Components of Data Center Infrastructure:
Data center infrastructure typically consists of the following components:
- Servers: These are the physical machines that process data and perform computations.
- Storage: This includes the physical storage devices used to store data.
- Networking: This includes the hardware and software used to connect servers and storage devices to the outside world.
- Power and Cooling: Data centers consume a significant amount of energy, and require specialized infrastructure for power and cooling.
Optimizing Data Center Infrastructure for Maximum ROI:
To optimize data center infrastructure for maximum ROI, organizations should focus on the following strategies:
1. Consolidation: Consolidation involves reducing the number of servers and storage devices in a data center by using virtualization and other techniques. This can help reduce costs, simplify management, and increase efficiency.
Case Study: A large financial services company wanted to reduce its data center footprint and improve efficiency. By using virtualization and consolidation techniques, the company was able to reduce the number of physical servers from 1,800 to just 400, resulting in significant cost savings and improved performance.
2. Automation: Automation involves using software to automate repetitive tasks and processes. This can help reduce errors, improve efficiency, and increase productivity.
Case Study: A healthcare provider wanted to improve the efficiency of its IT infrastructure by automating routine tasks. By implementing a new automation platform, the company was able to automate tasks such as patch management, configuration changes, and software deployment, resulting in significant time and cost savings.
3. Cloud Computing: Cloud computing involves using remote servers to store, manage, and process data. This can help reduce costs, increase flexibility, and improve scalability.
Case Study: A large retail company wanted to improve its ability to handle spikes in web traffic during holiday shopping seasons. By migrating its e-commerce platform to a cloud-based infrastructure, the company was able to scale up its infrastructure quickly during peak periods, resulting in improved performance and increased sales.
4. Energy Efficiency: Energy efficiency involves using specialized infrastructure to reduce the amount of energy consumed by a data center. This can help reduce costs, improve sustainability, and increase ROI.
Case Study: A global technology company wanted to improve the sustainability of its data center operations. By implementing energy-efficient cooling equipment and optimizing its power usage, the company was able to reduce its energy consumption by 30%, resulting in significant cost savings and reduced carbon emissions.
Optimizing data center infrastructure for maximum ROI requires a holistic approach that involves a combination of consolidation, automation, cloud computing, and energy efficiency. By focusing on these strategies, organizations can reduce costs, improve efficiency, and increase productivity, while also positioning themselves for future growth and success.
In conclusion, optimizing data center infrastructure for maximum ROI requires a holistic approach that involves a combination of consolidation, automation, cloud computing, and energy efficiency. By focusing on these strategies, organizations can reduce costs, improve efficiency, and increase productivity, while also positioning themselves for future growth and success.
Guide to Cisco Network Protocols: From Basics to Advanced
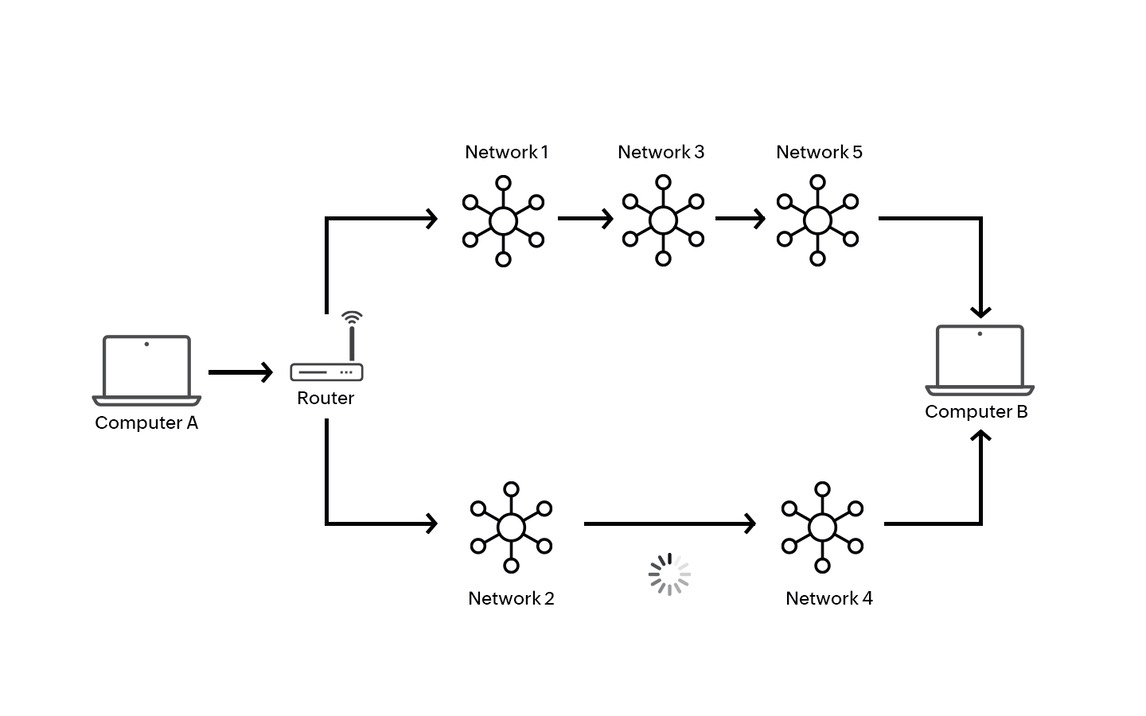
A Beginner's Guide to Understanding the Fundamentals of Cisco Networking for IT Leaders and Networking Professionals
In today's technologically advanced world, networking plays a vital role in the success of any business or organization. Cisco, as one of the world's leading networking technology providers, offers a wide range of network protocols that are essential for managing and maintaining a network. This guide will provide an in-depth understanding of Cisco network protocols for IT leaders and networking professionals who want to gain a comprehensive knowledge of Cisco networking.
In the connected world, networking plays an essential role in the success of any organization or business. Cisco, as one of the leading technology providers in the networking industry, offers a wide range of network protocols that are essential for managing and maintaining a network. In this article, we will list and explain the various Cisco network protocols that IT networking folks and IT leadership need to be aware of.
- Routing Protocols: Routing protocols are used to enable routers to communicate with each other and determine the best path for data transmission. Cisco offers three primary routing protocols:
- Routing Information Protocol (RIP): a distance-vector protocol that sends the entire routing table to its neighbors every 30 seconds.
- Open Shortest Path First (OSPF): a link-state protocol that exchanges link-state advertisements to construct a topology map of the network.
- Enhanced Interior Gateway Routing Protocol (EIGRP): a hybrid protocol that uses both distance-vector and link-state algorithms to determine the best path.
- Switching Protocols: Switching protocols are used to forward data packets between different network segments. Cisco offers two primary switching protocols:
- Spanning Tree Protocol (STP): a protocol that prevents network loops by shutting down redundant links.
- VLAN Trunking Protocol (VTP): a protocol that synchronizes VLAN configuration information between switches.
- Wide Area Network (WAN) Protocols: WAN protocols are used to connect remote networks over a wide geographic area. Cisco offers two primary WAN protocols:
- Point-to-Point Protocol (PPP): a protocol used to establish a direct connection between two devices over a serial link.
- High-Level Data Link Control (HDLC): a protocol used to encapsulate data over serial links.
- Security Protocols: Security protocols are used to secure the network and prevent unauthorized access. Cisco offers two primary security protocols:
- Internet Protocol Security (IPSec): a protocol used to secure IP packets by encrypting them.
- Secure Sockets Layer (SSL): a protocol used to establish a secure connection between a client and a server.
- Multi-Protocol Label Switching (MPLS): MPLS is a protocol used to optimize the speed and efficiency of data transmission. It uses labels to forward packets instead of IP addresses, which allows for faster routing and less congestion on the network.
- Border Gateway Protocol (BGP): BGP is a protocol used to route data between different autonomous systems (AS). It is commonly used by internet service providers to exchange routing information.
- Hot Standby Router Protocol (HSRP): HSRP is a protocol used to provide redundancy for IP networks. It allows for two or more routers to share a virtual IP address, so if one router fails, the other can take over seamlessly.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. It is commonly used in voice and video applications to prevent latency and ensure high-quality transmission.
Cisco network protocols are essential for maintaining and managing a network. Understanding these protocols is crucial for IT networking folks and IT leadership. By implementing Cisco network protocols, organizations can ensure that their network is secure, efficient, and reliable. Relevant examples and case studies can provide a better understanding of how these protocols work in real-life scenarios.
- Routing Protocols: Let's take a look at OSPF, which is a link-state protocol that exchanges link-state advertisements to construct a topology map of the network. This protocol is commonly used in enterprise networks to provide faster convergence and better scalability. For example, if there is a link failure in the network, OSPF routers can quickly recalculate the best path and update the routing table, ensuring that data is still transmitted efficiently.
- Switching Protocols: The Spanning Tree Protocol (STP) is a protocol that prevents network loops by shutting down redundant links. It works by selecting a single active path and blocking all other redundant paths, ensuring that there is no possibility of a loop forming. For example, if there are two switches connected via multiple links, STP will identify the shortest path and block the other links to prevent broadcast storms or other network issues.
- Wide Area Network (WAN) Protocols: The Point-to-Point Protocol (PPP) is a protocol used to establish a direct connection between two devices over a serial link. PPP provides authentication, compression, and error detection features, making it an ideal protocol for connecting remote sites. For example, if a company has a branch office in a remote location, it can use PPP to connect the remote site to the main office via a leased line.
- Security Protocols: Internet Protocol Security (IPSec) is a protocol used to secure IP packets by encrypting them. This protocol provides confidentiality, integrity, and authentication features, making it an ideal choice for securing data transmissions over the Internet. For example, if an organization needs to send sensitive data over the internet, it can use IPSec to encrypt the data, ensuring that it cannot be intercepted or modified by unauthorized parties.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. For example, if an organization is running voice and video applications on their network, they can use QoS to prioritize that traffic over other less critical traffic, ensuring that no latency or jitter could impact the quality of the transmission.
These are just a few examples of how Cisco network protocols work in real-life scenarios. By understanding how these protocols work and implementing them correctly, organizations can ensure that their network is secure, efficient, and reliable.
Cisco's networking devices, such as routers and switches, run on an operating system (OS) called Cisco IOS (Internetwork Operating System). IOS is a proprietary OS that is specifically designed to run on Cisco's networking hardware.
IOS provides the networking infrastructure with a wide range of features, including routing, switching, and security protocols. It also includes a command-line interface (CLI) that allows administrators to configure and manage the device's settings.
One of the key advantages of IOS is its modular design, which allows administrators to customize the OS by adding or removing specific features as needed. This modularity provides flexibility in managing the network devices and helps to keep the OS streamlined and efficient.
In addition to the traditional IOS, Cisco also offers a range of specialized operating systems for specific devices or environments, such as IOS XR for service provider networks or IOS XE for enterprise networks.
IOS is a reliable and flexible operating system that has been proven to be effective in managing and securing Cisco's networking devices. Its CLI is widely used by network administrators around the world, making it a valuable tool for managing networks of all sizes and complexities.
Commands are used in Cisco IOS, but it would not be feasible to explain every command in detail as it would require a significant amount of time and space. Instead, I can provide an overview of some of the essential commands used in Cisco IOS and their functions:
- enable: This command enables privileged mode, which provides access to configuration commands and advanced system settings.
- show: This command displays information about the system configuration, interface status, and device performance.
- configure terminal: This command enters global configuration mode, which allows users to configure the device settings and protocols.
- interface: This command configures individual interfaces on the device, such as Ethernet or serial ports.
- ip address: This command assigns IP addresses to network interfaces.
- hostname: This command sets the device hostname, which is used for identification purposes.
- ping: This command sends ICMP packets to test network connectivity.
- traceroute: This command traces the path that packets take from the source to the destination.
- Access list: This command configures access control lists to control traffic flow and filter packets.
- shutdown: This command disables an interface or a protocol.
- reload: This command reloads the device, which is useful for resetting configurations or troubleshooting issues.
These commands are just a few examples of the many commands available in Cisco IOS. Each command has specific syntax and options, and it's essential to use them correctly to avoid configuration errors and network issues. Cisco provides extensive documentation and training resources for users to learn about the commands and their functions. Network administrators must understand the basics of IOS commands to effectively manage and maintain their networks.
Here are some examples of how organizations can implement Cisco network protocols in their network infrastructure:
- Routing Protocols: An organization can implement the OSPF protocol by configuring OSPF on their routers and setting up areas to control network traffic. They can also use OSPF to optimize the path selection between routers by configuring the cost of the links based on bandwidth and delay.
- Switching Protocols: To implement the Spanning Tree Protocol (STP), an organization can configure STP on their switches to prevent network loops. They can also use Rapid Spanning Tree Protocol (RSTP) or Multiple Spanning Tree Protocol (MSTP) to reduce the convergence time and improve network performance.
- Wide Area Network (WAN) Protocols: An organization can implement the Point-to-Point Protocol (PPP) by configuring PPP on their routers to establish a direct connection between two devices over a serial link. They can also use PPP with authentication, compression, and error detection features to improve the security and efficiency of their network.
- Security Protocols: To implement the Internet Protocol Security (IPSec) protocol, an organization can configure IPSec on their routers and firewalls to encrypt data transmissions and provide secure communication over the Internet. They can also use IPSec with digital certificates to authenticate users and devices.
- Quality of Service (QoS): An organization can implement Quality of Service (QoS) by configuring QoS on their switches and routers to prioritize network traffic. They can also use QoS with Differentiated Services Code Point (DSCP) to classify and prioritize traffic based on its type and importance.
These are just a few examples of how organizations can implement Cisco network protocols in their network infrastructure. By implementing these protocols correctly, organizations can ensure that their network is secure, efficient, and reliable, providing the necessary tools to support business-critical applications and services.
Here's a tutorial on how to configure some of the Cisco network protocols on routers and switches.
1. Routing Protocols:
Step 1: Enable the routing protocol on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the router ID and set up the interfaces by using the "router ospf" command.
Step 3: Set up the areas to control network traffic by using the "area" command.
Step 4: Configure the cost of the links based on bandwidth and delay by using the "ip ospf cost" command.
Step 5: Verify the OSPF configuration by using the "show ip ospf" command.
2. Switching Protocols:
Step 1: Enable the Spanning Tree Protocol (STP) on the switch by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the bridge priority by using the "spanning-tree vlan [vlan-id] root" command.
Step 3: Set up the port priority and cost by using the "spanning-tree vlan [vlan-id] [port-id] priority [priority]" and "spanning-tree vlan [vlan-id] [port-id] cost [cost]" commands.
Step 4: Verify the STP configuration by using the "show spanning tree" command.
3. Wide Area Network (WAN) Protocols:
Step 1: Enable the Point-to-Point Protocol (PPP) on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the PPP authentication by using the "ppp authentication [chap/pap]" command.
Step 3: Set up the PPP options by using the "ppp multilink" and "ppp multilink fragment delay [delay]" commands.
Step 4: Verify the PPP configuration by using the "show ppp multilink" command.
4. Security Protocols:
Step 1: Enable the Internet Protocol Security (IPSec) protocol on the router or firewall by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the crypto map and set up the IP address and the pre-shared key by using the "crypto map [map-name] [seq-num] ipsec-isakmp" and "set peer [peer-address] key [pre-shared-key]" commands.
Step 3: Configure the access list to specify the traffic to be encrypted by using the "access-list [acl-number] permit [source-address] [destination-address]" command.
Step 4: Verify the IPSec configuration by using the "show crypto map" command.
5. Quality of Service (QoS):
Step 1: Enable the Quality of Service (QoS) on the switch or router by entering the configuration mode using the "configure terminal" command.
Step 2: Set up the class map and the match criteria by using the "class-map [class-name]" and "match [criteria]" commands.
Step 3: Configure the policy map and the traffic shaping by using the "policy-map [policy-name]" and "shape average [bandwidth]" commands.
Step 4: Apply the QoS policy to the interface by using the "service-policy output [policy-name]" command.
Step 5: Verify the QoS configuration by using the "show policy-map interface [interface-name]" command.
These are just some basic steps for configuring some of the Cisco network protocols on routers and switches. Depending on your specific network requirements, you may need to configure additional settings or features. Always make sure to test and verify your configuration to ensure that it is working as expected.
Cisco's networking devices, such as routers and switches, run on an operating system (OS) called Cisco IOS (Internetwork Operating System). IOS is a proprietary OS that is specifically designed to run on Cisco's networking hardware.
IOS provides the networking infrastructure with a wide range of features, including routing, switching, and security protocols. It also includes a command-line interface (CLI) that allows administrators to configure and manage the device's settings.
One of the key advantages of IOS is its modular design, which allows administrators to customize the OS by adding or removing specific features as needed. This modularity provides flexibility in managing the network devices and helps to keep the OS streamlined and efficient.
In addition to the traditional IOS, Cisco also offers a range of specialized operating systems for specific devices or environments, such as IOS XR for service provider networks or IOS XE for enterprise networks.
Ethical Hacking and Cybercrime: Protecting Systems and Networks

White Hat Hacking and Ethical Hacking are critical for protecting computer systems and networks from cyber threats. This article explores the basics of ethical hacking, including tools and techniques, and the importance of maintaining an ethical mindset.
White Hat Hacking and Ethical Hacking are critical for protecting computer systems and networks from cyber threats. This article explores the basics of ethical hacking, including tools and techniques, and the importance of maintaining an ethical mindset.
Ethical Hacking
White hat hacking, also known as ethical hacking, refers to the practice of using hacking techniques to identify and fix security vulnerabilities in computer systems, networks, and applications.
White hat hackers are usually employed by organizations to perform penetration testing, vulnerability assessments, and other security audits to identify potential weaknesses in their systems before they can be exploited by malicious hackers.
Unlike black hat hackers, who use hacking techniques for personal gain or to cause harm, white hat hackers operate within a legal and ethical framework. They obtain permission from the target organization before conducting any security testing and ensure that any vulnerabilities they discover are reported to the organization's security team so that they can be addressed.
White hat hacking is an important aspect of modern cybersecurity, as it helps organizations proactively identify and address security vulnerabilities before they can be exploited by attackers.
How to Become an Ethical Hacker?
Becoming an ethical hacker involves acquiring a combination of technical skills, practical experience, and an ethical mindset. The following steps can guide you toward becoming an ethical hacker:
- Develop a strong foundation in computer science: This involves gaining knowledge in computer networking, operating systems, programming languages, and database management.
- Learn about cybersecurity: Understand the different types of cyber-attacks, vulnerabilities, and security measures.
- Get certified: Industry-standard certifications such as Certified Ethical Hacker (CEH), CompTIA Security+, and Certified Information Systems Security Professional (CISSP) can help demonstrate your skills and knowledge to potential employers.
- Gain practical experience: Practice your skills by participating in bug bounty programs, capture-the-flag events, or by performing penetration testing on your systems.
- Stay up-to-date: Keep up with the latest security trends, techniques, and technologies by attending industry events, reading blogs, and following security experts on social media.
- Develop an ethical mindset: As an ethical hacker, it is important to maintain a strong ethical mindset and to abide by the law and ethical guidelines.
There are many resources available for learning and training in ethical hacking, including online courses, certification programs, and community forums. Some popular resources include:
- Udemy: Offers a variety of online courses in ethical hacking and cybersecurity.
- Cybrary: Offers a range of free online courses in cybersecurity, including ethical hacking.
- Offensive Security: Offers industry-standard certifications such as the OSCP and OSCE, as well as online training courses.
- SANS Institute: Offers a variety of cybersecurity training courses and certifications, including ethical hacking.
- HackerOne and Bugcrowd: Platforms for participating in bug bounty programs and practicing ethical hacking.
It is important to note that ethical hacking should always be done with proper authorization and ethical guidelines. Unauthorized hacking can have serious legal and ethical consequences. Therefore, it is essential to approach ethical hacking with a strong ethical mindset and respect for others' privacy and security.
Tools are required.
There are a variety of tools that can be used for ethical hacking, each with its specific purpose. Here are some of the commonly used tools and their brief explanations:
- Nmap: Network Mapper (Nmap) is a tool used to scan networks and identify hosts, ports, and services. It can be used to determine which ports are open and vulnerable to attack, and what services are running on those ports.
- Metasploit: Metasploit is a penetration testing framework that enables ethical hackers to test and exploit vulnerabilities in computer systems and applications. It contains a collection of modules and exploits that can be used to launch various types of attacks.
- Wireshark: Wireshark is a network protocol analyzer that allows ethical hackers to capture and analyze network traffic. It can be used to detect suspicious activity on a network, identify potential security vulnerabilities, and monitor network performance.
- John the Ripper: John the Ripper is a password-cracking tool that can be used to test the strength of passwords. It uses various techniques to crack passwords, including dictionary attacks, brute force attacks, and hybrid attacks.
- Burp Suite: Burp Suite is a web application security testing tool that can be used to identify and exploit vulnerabilities in web applications. It includes various modules such as a web proxy, a vulnerability scanner, and an intruder that can be used to perform different types of attacks.
- Aircrack-ng: Aircrack-ng is a tool used to test the security of wireless networks. It can be used to capture and analyze packets transmitted over a wireless network, crack WEP and WPA encryption keys, and test the strength of wireless network passwords.
- Nessus: Nessus is a vulnerability scanner that can be used to identify potential security vulnerabilities in computer systems and networks. It includes a database of known vulnerabilities that can be used to scan and detect vulnerabilities in a target system.
These are just a few examples of the many tools available for ethical hacking. It is important to note that these tools should only be used for ethical purposes, and with the permission of the target organization.
Basic Skill required
To become an ethical hacker, certain basic skill sets are required. Here are some of the key skills that are essential for ethical hacking:
- Understanding of networking protocols: A basic understanding of networking protocols and technologies such as TCP/IP, DNS, HTTP, and SSL is essential for ethical hacking. This knowledge helps in understanding how networks and systems communicate with each other, and how to identify potential vulnerabilities.
- Operating system knowledge: A good knowledge of operating systems such as Windows, Linux, and Unix is important for ethical hacking. This includes knowledge of the command line interface, system files, and how to modify system settings.
- Programming skills: A basic understanding of programming languages such as Python, Java, and C is essential for ethical hacking. This helps in writing scripts to automate tasks and developing custom tools for specific hacking scenarios.
- Knowledge of security tools: Familiarity with various security tools such as vulnerability scanners, password crackers, and network analyzers is important for ethical hacking. It is essential to understand how these tools work, and how to use them effectively.
- Analytical skills: Ethical hackers need to have strong analytical skills to be able to identify and exploit vulnerabilities in computer systems and networks. This includes being able to think creatively and outside the box and being able to analyze data and information to identify potential security weaknesses.
- Communication skills: Ethical hackers need to have strong communication skills to be able to communicate effectively with clients and team members. This includes being able to explain technical concepts in non-technical terms and being able to present findings clearly and concisely.
Becoming an ethical hacker requires a combination of technical skills, analytical thinking, and strong communication skills. It is also important to stay up-to-date with the latest security threats and vulnerabilities and to constantly improve your knowledge and skills in the field.
Ethical Hackers Mind Map
A hacker's mind map is a visual representation of the thought process and techniques used by a hacker to identify and exploit vulnerabilities in computer systems and networks. The mind map typically includes various steps and techniques that are used by hackers to achieve their goals. Here is an overview of some of the key elements of a hacker's mind map:
- Reconnaissance: This involves gathering information about the target system or network. It can include techniques such as network scanning, port scanning, and information gathering from social media, job postings, or other public sources.
- Vulnerability scanning: This involves using automated tools to scan the target system or network for known vulnerabilities. This can include tools such as Nessus, OpenVAS, and Qualys.
- Exploitation: This involves using the information gathered during reconnaissance and vulnerability scanning to identify and exploit vulnerabilities in the target system or network. This can include techniques such as SQL injection, cross-site scripting (XSS), and buffer overflow attacks.
- Privilege escalation: Once a hacker has gained access to a target system or network, the next step is to escalate privileges to gain deeper access and control. This can include techniques such as password cracking, privilege escalation exploits, and social engineering.
- Post-exploitation: After gaining access and control of the target system or network, the hacker can use this access to gather sensitive data, install malware, or launch further attacks.
- Covering tracks: To avoid detection, the hacker may try to cover their tracks by deleting logs, hiding files, or altering timestamps.
It is important to note that while this mind map represents the thought process of a malicious hacker, these techniques can also be used by ethical hackers to identify and fix vulnerabilities in computer systems and networks. The key difference is that ethical hackers operate within a legal and ethical framework, and work to improve security rather than cause harm.
Introduction to Kali Linux.
Kali Linux is a Debian-based Linux distribution designed specifically for penetration testing and ethical hacking. It is a powerful and customizable operating system that comes preloaded with a wide range of hacking tools and utilities that are used by ethical hackers to test the security of computer systems and networks. Some of the key features of Kali Linux include:
- Preloaded with hacking tools: Kali Linux comes with a wide range of preinstalled hacking tools and utilities that are used by ethical hackers for various purposes such as network scanning, vulnerability assessment, password cracking, and exploitation.
- Customizable and flexible: Kali Linux is highly customizable and can be tailored to meet the specific needs of the ethical hacker. It can be easily configured with different desktop environments and tools, depending on the nature of the task at hand.
- Regularly updated: Kali Linux is regularly updated with the latest security tools and patches, ensuring that ethical hackers have access to the latest and most powerful hacking tools.
- Easy to use: Despite being a complex and powerful operating system, Kali Linux is relatively easy to use and comes with a user-friendly interface that simplifies the process of performing complex hacking tasks.
- Community support: Kali Linux has a large and active community of ethical hackers, developers, and security professionals who contribute to the development and support of the operating system. This community provides a wealth of resources and support for ethical hackers using Kali Linux.
Kali Linux is preferred by ethical hackers because it is designed specifically for their needs, and provides them with a powerful and flexible platform for performing various hacking tasks. It allows ethical hackers to identify and fix vulnerabilities in computer systems and networks, and to stay ahead of the latest security threats and exploits.
Tools available in Kali Linux.
Kali Linux is a powerful Linux distribution that comes preloaded with a wide range of hacking tools and utilities for penetration testing and ethical hacking. Here is an overview of some of the key tools available in Kali Linux:
- Nmap: A powerful network exploration tool used for network discovery, port scanning, and vulnerability testing.
- Metasploit Framework: An open-source exploitation framework used for developing and executing exploit code against remote target systems.
- Aircrack-ng: A set of tools used for wireless network monitoring, packet capture analysis, and WEP/WPA/WPA2 password cracking.
- Wireshark: A network protocol analyzer used for deep packet inspection and network troubleshooting.
- John the Ripper: A password-cracking tool used for brute-force and dictionary attacks against password-protected systems and files.
- Hydra: A password-cracking tool that can be used to perform brute-force attacks against various network services such as SSH, FTP, and Telnet.
- Burp Suite: An integrated platform used for web application security testing, including vulnerability scanning, penetration testing, and automated scanning.
- Social Engineering Toolkit (SET): A framework used for creating custom attacks against human targets, such as phishing and spear-phishing attacks.
- SQLMap: A tool used for detecting and exploiting SQL injection vulnerabilities in web applications.
- Maltego: A powerful information gathering and reconnaissance tool used for gathering intelligence on target systems and networks.
- Hashcat: A password cracking tool that can be used to perform advanced attacks against various password hashing algorithms, including MD5, SHA-1, and bcrypt.
- Netcat: A versatile networking tool that can be used for various purposes such as port scanning, file transfer, and remote access.
These are just some of the key tools available in Kali Linux. The operating system comes with many more tools and utilities that can be used for a wide range of hacking and security testing purposes. It is important to note that these tools should only be used for ethical and legal purposes, and not for any illegal activities.
Let's take a deep dive into the use of these tools.
It is important to note that the tools available in Kali Linux should only be used for ethical and legal purposes. Using these tools for any illegal activities can result in serious legal consequences. With that said, here are some brief instructions on how to use some of the tools available in Kali Linux:
- Nmap: Nmap is a powerful network exploration tool that can be used for network discovery, port scanning, and vulnerability testing. To use Nmap, simply open a terminal window and type "nmap" followed by the target IP address or hostname. For example, "nmap 192.168.0.1" will scan the network at IP address 192.168.0.1.
- Metasploit Framework: Metasploit Framework is an open-source exploitation framework used for developing and executing exploit code against remote target systems. To use Metasploit, simply open a terminal window and type "msfconsole" to start the Metasploit console. From there, you can search for exploits using the "search" command, and launch exploits using the "use" command followed by the name of the exploit.
- Aircrack-ng: Aircrack-ng is a set of tools used for wireless network monitoring, packet capture analysis, and WEP/WPA/WPA2 password cracking. To use Aircrack-ng, you will need a wireless adapter that supports monitor mode. Once you have the adapter set up, open a terminal window and type "airmon-ng start wlan0" to put the adapter into monitor mode. Then, use the "airodump-ng" command to capture packets on the wireless network, and use the "aircrack-ng" command to crack the wireless network password.
- Wireshark: Wireshark is a network protocol analyzer used for deep packet inspection and network troubleshooting. To use Wireshark, simply open the Wireshark application and select the network interface you want to capture packets on. You can then apply filters to view specific types of network traffic and analyze the captured packets.
- John the Ripper: John the Ripper is a password-cracking tool used for brute-force and dictionary attacks against password-protected systems and files. To use John the Ripper, simply open a terminal window and use the "john" command followed by the file containing the password hashes you want to crack. For example, "john /etc/shadow" will crack the password hashes in the /etc/shadow file.
- Hydra: Hydra is a password-cracking tool that can be used to perform brute-force attacks against various network services such as SSH, FTP, and Telnet. To use Hydra, open a terminal window and use the "hydra" command followed by the target hostname or IP address, the service you want to attack, and the username and password list you want to use. For example, "hydra -l admin -P passwordlist.txt ssh://192.168.0.1" will use the "admin" username and the passwords in the "passwordlist.txt" file to perform a brute-force attack against the SSH service on the 192.168.0.1 IP address.
- Burp Suite: Burp Suite is an integrated platform used for web application security testing, including vulnerability scanning, penetration testing, and automated scanning. To use Burp Suite, simply open the Burp Suite application and configure your browser to use the Burp Suite proxy. You can then use Burp Suite to intercept and analyze HTTP requests and responses and perform various security testing tasks.
- Social Engineering Toolkit (SET): SET is a framework used for creating custom attacks against human targets, such as phishing and spear-phishing attacks. To use SET, open a terminal window and type "setool
Forensic Hacking, Computer Forensics, and Malware Analysis
Forensic hacking, also known as digital forensics, is the process of gathering, analyzing, and preserving electronic data to investigate and resolve cyber crimes. It involves the use of specialized techniques and tools to uncover digital evidence that can be used in legal proceedings.
Forensic Hacking is a critical tool for investigating and resolving cyber crimes. The techniques and tools used in digital forensics can help investigators uncover valuable evidence and bring cyber criminals to justice.
Computer forensics is a branch of digital forensics that focuses on the investigation of computer systems and storage media. It involves the collection and analysis of data from computers, including files, log files, network traffic, and system configurations. Computer forensics can be used to investigate cyber crimes such as hacking, data theft, and intellectual property theft.
Malware analysis is the process of examining malicious software to understand its behavior, purpose, and potential impact. It involves analyzing the code and behavior of the malware to identify its characteristics and determine how it works. Malware analysis can be used to understand the capabilities of a piece of malware and to develop countermeasures to prevent or mitigate its effects.
There are many tools and techniques involved in forensic hacking, it would be impossible to provide detailed instructions for each one. However, I can give a general overview of how to use these tools:
- Computer Forensics: The process of computer forensics involves analyzing data from computers, including files, log files, network traffic, and system configurations. To use computer forensics tools, you need to have access to the device or system you want to analyze. Some popular computer forensics tools include EnCase, FTK Imager, and Autopsy.
- Malware Analysis: The process of malware analysis involves analyzing malicious software to understand its behavior, purpose, and potential impact. There are many tools available for malware analysis, including OllyDbg, IDA Pro, and Immunity Debugger.
It's important to note that forensic hacking should only be done by trained professionals with the proper legal authorization. Any unauthorized access or use of these tools can result in criminal charges.
Cybercrime Investigation.
Cybercrime investigation is the process of identifying, tracking, and prosecuting individuals or groups who have committed cybercrimes. Cybercrime can take many forms, including hacking, phishing, identity theft, and financial fraud. Financial crime is a type of cybercrime that involves the use of deception or other illegal means to obtain money or other financial benefits.
Financial crimes can be perpetrated through various means, such as stealing credit card information, forging checks, or creating fake online identities. These crimes can be difficult to detect and can have significant financial consequences for individuals and organizations.
The investigation of financial crimes typically involves a few steps:
- Identify the crime: The first step in investigating a financial crime is to identify the type of crime that has occurred. This may involve analyzing financial transactions, interviewing witnesses, or conducting forensic analysis of digital evidence.
- Gather evidence: Once the type of crime has been identified, investigators will gather evidence to build a case against the perpetrators. This may include collecting financial records, conducting interviews, or analyzing digital devices or networks.
- Trace the money: Financial crimes often involve the movement of money through various channels. Investigators will use financial analysis techniques to trace the flow of money and identify the individuals or organizations involved.
- Build a case: Based on the evidence gathered, investigators will build a case against the individuals or groups responsible for the crime. This may involve working with law enforcement agencies, prosecutors, or financial regulators.
- Prosecute the offenders: Once a case has been built, offenders can be prosecuted in a court of law. Depending on the severity of the crime, penalties can range from fines to imprisonment.
Financial crimes can have significant financial and reputational consequences for individuals and organizations. Therefore, it's important to take appropriate measures to protect your financial information, such as using strong passwords, monitoring financial statements, and reporting suspicious activity to financial institutions or law enforcement agencies.
Social Media Crime.
Social media crimes refer to any illegal or unethical activities that are committed on social media platforms such as cyberbullying, harassment, defamation, identity theft, and fraud.
These are the different types of social media crimes and how they are typically committed:
- Cyberbullying: Cyberbullying involves using social media to harass, threaten, or intimidate another person. This can include posting hurtful comments, spreading rumors, or sharing embarrassing photos or videos.
- Harassment: Social media can also be used for sexual harassment or stalking. This can include sending unwanted messages or images, creating fake profiles, or monitoring someone's online activity without their consent.
- Defamation: Defamation involves making false statements about someone that can harm their reputation. This can include posting false information about a person's character, actions, or beliefs on social media.
- Identity theft: Identity theft involves stealing someone's personal information and using it to commit fraud or other illegal activities. This can include creating fake profiles or accounts in someone else's name, stealing credit card information, or accessing someone's bank accounts.
- Fraud: Social media can also be used to commit various types of fraud, such as phishing scams, fake investment schemes, or online shopping scams.
To prevent social media crimes, it's important to practice safe social media habits such as keeping personal information private, reporting suspicious activity to social media platforms or law enforcement, and being careful about what you share online. If you are a victim of social media crime, it's important to report it to the relevant authorities and seek legal assistance if necessary.
Where do Ethical Hackers come in?
Ethical hacking can help solve cybercrimes in several ways. Ethical hackers, also known as white hat hackers, use their knowledge and skills to identify vulnerabilities in computer systems and networks and provide recommendations on how to improve security.
In the case of cybercrime, an ethical hacker can be brought in to investigate the incident and determine how it was carried out. This can involve analyzing computer systems, networks, and data to identify any security weaknesses or breaches that were exploited by the perpetrator.
Once the vulnerabilities have been identified, the ethical hacker can then make recommendations on how to improve security and prevent future attacks. This can involve implementing stronger passwords, improving network security protocols, or installing additional security software.
In addition to investigating cybercrimes, ethical hackers can also help prevent them from occurring in the first place. By conducting regular security assessments and identifying potential vulnerabilities, ethical hackers can help organizations stay one step ahead of cyber criminals and protect their data and assets.
As explained, ethical hacking is a valuable tool in the fight against cybercrime. By identifying vulnerabilities and improving security, ethical hackers can help prevent cyber crimes from occurring and assist in the investigation and resolution of those that do occur.
Website Hacking
Website hacking involves gaining unauthorized access to a website or web application to cause harm or steal sensitive information. This can include defacing a website, stealing customer data, or inserting malicious code that can be used to carry out further attacks.
Ethical hackers can help prevent website hacking by identifying vulnerabilities in the website or web application before attackers can exploit them. This involves conducting a thorough security assessment, which can include testing for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure server configurations.
Once vulnerabilities have been identified, the ethical hacker can provide recommendations on how to address them. This may involve implementing software patches, upgrading to a more secure web application framework, or improving password policies.
In addition to prevention, ethical hackers can also assist in the investigation and resolution of website hacking incidents. This may involve analyzing server logs, identifying the attacker's methods and motivations, and working with law enforcement to track down the perpetrator.
Thus, ethical hacking plays an important role in the prevention and resolution of website hacking incidents. By identifying vulnerabilities and providing recommendations on how to address them, ethical hackers can help organizations stay one step ahead of attackers and protect their websites and web applications from harm.
Mobile crimes
Mobile crime refers to any illegal or unethical activities that are carried out on or through mobile devices such as smartphones and tablets. This can include mobile malware, phishing scams, identity theft, and unauthorized access to sensitive data.
One common method for investigating mobile crime is through the analysis of Call Detail Records (CDRs). CDRs are detailed records of all calls and messages made or received by a mobile device and can provide valuable insights into the activities of the device's user.
Ethical hackers can use CDR analysis to identify suspicious or unusual activity, such as calls or messages to known criminal organizations, or large amounts of data being transferred to unauthorized locations. They can also analyze the device's network traffic to identify any unusual patterns or indicators of malware infection.
Once a suspicious activity has been identified, ethical hackers can then investigate further to determine the source of the activity and how it is being carried out. This may involve analyzing the device's operating system and installed applications for vulnerabilities or conducting a forensic analysis of the device's memory and storage to identify any malicious code or activity.
Once the source of the activity has been identified, ethical hackers can provide recommendations on how to mitigate the risks and prevent future incidents. This may involve installing security software, implementing stronger password policies, or improving network security protocols.
Ethical hacking plays an important role in the prevention and investigation of mobile crime. By using CDR analysis and other techniques, ethical hackers can help identify and address suspicious activity on mobile devices and protect users from the potentially devastating consequences of mobile crime.
What tools are used to solve cybercrimes?
Ethical hackers use a variety of tools to help prevent and solve cybercrimes. Below are some commonly used tools and instructions on how to use them:
1. Nmap - Nmap is a network exploration and security auditing tool. It can be used to identify hosts and services on a network, as well as detect potential security vulnerabilities.
To use Nmap, open a command prompt and type "nmap [target IP or hostname]". This will start a scan of the specified target. You can also use various options and flags to customize the scan, such as "-sS" to perform an SYN scan or "-A" to enable OS and version detection.
2. Metasploit - Metasploit is a framework for developing and executing exploits against vulnerable systems. It can be used to test the security of a network or web application, as well as simulate attacks to identify potential weaknesses.
To use Metasploit, open a terminal and type "msfconsole". This will launch the Metasploit console. From there, you can search for exploits using the "search" command, select a module using the "use" command, and configure the exploit options using the "set" command. Once configured, you can launch the exploit using the "exploit" command.
3. Wireshark - Wireshark is a network protocol analyzer. It can be used to capture and analyze network traffic and detect potential security issues such as unauthorized access or data leaks.
To use Wireshark, open the program and select the network interface you want to capture traffic on. You can then start a capture and analyze the packets as they are captured. You can also apply filters to only capture specific types of traffic, such as HTTP requests or SMTP traffic.
4. Burp Suite - Burp Suite is a web application security testing tool. It can be used to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflows.
To use Burp Suite, start by configuring your web browser to use the Burp Suite proxy. Then, navigate to the web application you want to test and perform actions such as filling out forms or clicking links. Burp Suite will capture and analyze the traffic, allowing you to identify potential vulnerabilities. You can also use various features such as the intruder tool to automate attacks against the application.
5. Aircrack-ng - Aircrack-ng is a tool for testing the security of wireless networks. It can be used to capture and analyze network traffic, as well as test the strength of wireless encryption.
To use Aircrack-ng, start by putting your wireless card into monitor mode. Then, use the "airodump-ng" command to capture traffic on the network you want to test. Once you have captured enough data, you can use the "aircrack-ng" command to test the strength of the encryption and attempt to crack the password.
It's important to note that these tools should only be used for ethical hacking purposes, and should not be used to carry out illegal activities. Additionally, it's recommended that you only use these tools on systems and networks that you have permission to test, to avoid causing unintended harm or damage.
Deep dive into Metasploit.
Metasploit is a powerful penetration testing framework that can be used to identify vulnerabilities in a network or system and to simulate attacks to test the security of the network or system. It provides a collection of exploit modules, payloads, and auxiliary modules, and can be used to develop and execute custom exploits against a target.
Metasploit is open-source software and is available for download from the Metasploit website. Once installed, it can be launched from the command line using the "msfconsole" command.
One of the key features of Metasploit is its ability to automate the process of identifying and exploiting vulnerabilities. This can save time and effort for security researchers, and can also help to ensure that all potential vulnerabilities are identified and addressed.
To use Metasploit, you first need to identify a target system or network that you want to test. This can be done using tools like Nmap or Metasploit's port scanner.
Once you have identified a target, you can use Metasploit to search for and select an exploit module that is relevant to the target. Metasploit includes a large library of exploit modules, which can be searched using the "search" command in the Metasploit console.
For example, if you want to test a target that is running an outdated version of the Apache web server, you could use the "search Apache" command to search for exploit modules that target Apache vulnerabilities. Once you have identified a relevant exploit module, you can select it using the "use" command.
Next, you will need to configure the exploit module to match the specifics of your target system. This can include specifying the target IP address, port number, and other relevant details. This can be done using the "set" command.
Once the exploit module is configured, you can launch the exploit using the "exploit" command. This will attempt to exploit the vulnerability in the target system, and if successful, will give you access to the target system or network.
Metasploit also includes a range of post-exploitation modules, which can be used to further explore the target system or network and to maintain access to the system even if the initial exploit is discovered and patched.
Overall, Metasploit is a powerful tool for identifying and exploiting vulnerabilities and can be an important part of a comprehensive security testing strategy. However, it should only be used for ethical hacking purposes, and should not be used to carry out illegal activities. Additionally, it's recommended that you only use Metasploit on systems and networks that you have permission to test, to avoid causing unintended harm or damage.
Hardware required.
The hardware required for white hat hacking can vary depending on the specific tasks being performed, but generally, the following components are essential:
- Computer: A high-performance computer is required to run various software tools used for hacking. The computer should have a multi-core processor, sufficient RAM (at least 8GB), and a fast solid-state drive (SSD) to enable quick access to data.
- Network Interface Cards (NIC): Network interface cards are required for connecting to wired and wireless networks. A wireless NIC that supports packet injection is necessary for performing wireless penetration testing.
- External Storage Devices: External hard drives or USB drives are essential for storing and transporting large amounts of data collected during a security assessment.
- Display: A high-resolution monitor or multiple monitors are useful for displaying multiple windows and tools at the same time.
- Peripherals: A keyboard, mouse, and speakers are necessary for operating the computer and receiving audio feedback from software tools.
- Virtualization Software: Virtualization software such as VMware or VirtualBox is necessary for creating virtual machines to test different operating systems and configurations.
- USB Rubber Ducky: A USB Rubber Ducky is a tool used to automate keystrokes on a target machine. It can be used to quickly execute commands or upload malware onto a target machine.
- Raspberry Pi: A Raspberry Pi is a credit-card-sized computer that can be used to run various hacking tools. It is portable, low-cost, and can be used for tasks such as wireless sniffing or as a drop box to collect data.
Configuration: The configuration of the hardware components should be optimized for performance and security. This can include:
- Installing a high-performance operating system such as Kali Linux, which is specifically designed for hacking.
- Enabling encryption on the hard drive and USB drives to protect sensitive data.
- Using a Virtual Private Network (VPN) to encrypt all internet traffic and protect the user's identity and location.
- Disabling unnecessary services and features to reduce the attack surface of the computer.
- Configuring a firewall to prevent unauthorized access to the computer and network.
- Using multi-factor authentication for accessing sensitive accounts and data.
- Regularly updating the operating system and software tools to ensure that the latest security patches and updates are installed.
Overall, the hardware configuration for white hat hacking should be designed to maximize performance, portability, and security, while minimizing the risk of compromise or exposure. It's important to note that white hat hacking should only be performed with permission and within the bounds of ethical and legal guidelines.
How can a Windows, Linux, Android, IOS, or Mac machine be accessed without passwords?
As an ethical hacker, it is important to respect the legal and ethical boundaries surrounding the recovery of data from devices seized by law enforcement agencies. It is illegal to access a seized device without proper authorization or a court order.
However, in some cases, it may be necessary for a legitimate forensic investigation to recover data from a seized device without passwords. In such cases, the following methods may be used:
- Password Cracking: The most straightforward approach is to use password cracking tools such as John the Ripper, Hashcat, or L0phtCrack to attempt to crack the passwords on the device. These tools work by attempting to guess or brute-force the password by trying different combinations of characters until the correct password is found.
- Password Reset: In some cases, it may be possible to reset the password on the device using a bootable USB or CD that contains a password reset tool such as Ophcrack, Trinity Rescue Kit, or Kon-Boot. These tools work by bypassing the existing password and allowing the user to reset it to a new password of their choice.
- Live Boot: A live boot is a bootable USB or CD that contains an operating system that can be run directly from the USB or CD without being installed on the hard drive. This can be useful for accessing the files on the hard drive without needing to enter a password. Linux-based live boot operating systems such as Kali Linux, BackTrack, or Ubuntu are commonly used for this purpose.
- Forensic Imaging: In some cases, it may be necessary to create a forensic image of the hard drive or storage media to recover the data. This can be done using tools such as FTK Imager, Encase, or DD. Once the forensic image is created, it can be analyzed to recover deleted files, passwords, and other data.
It is important to note that attempting to access a seized device without proper authorization or legal clearance can result in serious legal consequences. As such, it is essential to obtain proper authorization and follow legal and ethical guidelines when attempting to recover data from seized devices.
How to Decrypt an Encrypted Drive.
As an ethical hacker, it is important to respect the privacy and security of encrypted drives and only attempt to decrypt them with proper authorization or legal clearance. Attempting to decrypt encrypted drives without proper authorization or legal clearance can result in serious legal consequences.
In some cases, a legitimate forensic investigation may require the decryption of an encrypted drive. The following methods may be used:
- Brute-Force Attack: A brute-force attack involves trying every possible combination of characters until the correct decryption key is found. This method can be time-consuming and may not be practical for strong encryption algorithms. However, it can be effective for weak encryption schemes.
- Dictionary Attack: A dictionary attack involves using a pre-defined list of commonly used passwords or phrases to attempt to decrypt the drive. This method is often more effective than a brute-force attack and can be useful for weak passwords or encryption schemes.
- Rainbow Table Attack: A rainbow table attack involves using pre-computed tables of hashed passwords to attempt to find the decryption key. This method can be faster than brute-force or dictionary attacks but requires a large amount of pre-computation to generate the rainbow tables.
- Key Recovery: In some cases, it may be possible to recover the decryption key from the system memory or registry. This can be done using tools such as Volatility or FTK Imager.
Tools used for Decrypting Encrypted drives include:
- BitCracker: A tool that can perform a dictionary attack on BitLocker, TrueCrypt, and VeraCrypt encrypted volumes.
- John the Ripper: A tool that can perform brute-force attacks on a wide range of encryption algorithms.
- Hashcat: A tool that can perform brute-force and dictionary attacks on a wide range of encryption algorithms.
- Elcomsoft Forensic Disk Decryptor: A tool that can recover the encryption keys for BitLocker, TrueCrypt, and VeraCrypt volumes from system memory or hibernation files.
It is important to note that attempting to decrypt an encrypted drive without proper authorization or legal clearance can result in serious legal consequences. As such, it is essential to obtain proper authorization and follow legal and ethical guidelines when attempting to decrypt encrypted drives.
How to Recover Deleted Files, Partitions, and Data?
Ethical hackers can recover deleted or formatted files, partitions, and data by using specialized data recovery software tools. These tools use various techniques to scan the storage devices and attempt to recover lost or deleted data.
One such tool is TestDisk, which is a free and open-source tool that can recover lost partitions and make non-booting disks bootable again. It supports various file systems, including FAT, NTFS, and ext, and can run on Windows, Linux, and macOS.
Another popular tool is Recuva, which is a free data recovery tool for Windows. It can recover files that have been accidentally deleted, formatted, or damaged. It supports various file systems, including FAT, NTFS, and exFAT, and can recover files from various storage devices, including hard drives, USB drives, and memory cards.
PhotoRec is another tool from the same developers as TestDisk that can recover lost or deleted files from various file systems, including FAT, NTFS, and ext, as well as from CDs/DVDs, and memory cards. It can run on Windows, Linux, and MacOS.
Foremost is another tool that can recover files based on their headers, footers, and internal data structures. It can recover various file formats, including images, documents, and multimedia files.
Ethical hackers can use these data recovery tools to recover lost or deleted data and help protect systems and networks from data loss caused by accidental deletion or formatting.
List of software used for Cyber Investigation.
There are many software tools used for cyber investigation, and the specific tools required depend on the nature of the investigation. Some commonly used tools include:
1. Encase: Encase is a digital forensics software tool that is widely used by law enforcement agencies and forensic investigators to conduct digital investigations. It can acquire, analyze, and report data from various devices, including computers, mobile devices, and cloud storage.
2. Autopsy: Autopsy is a free and open-source digital forensics tool that can analyze data from various sources, including hard drives, mobile devices, and memory cards. It includes a powerful search engine and supports various file systems and data types.
3. Wireshark: Wireshark is a network protocol analyzer that allows investigators to capture and analyze network traffic. It can decode various protocols and help identify network anomalies and security threats.
4. FTK Imager: FTK Imager is a digital forensic tool that can create forensic images of storage devices and analyze them for evidence. It supports various file systems and data types and can recover deleted files and data.
5. Volatility: Volatility is a memory forensics tool that can analyze the volatile memory of a computer system. It can help identify malicious processes and malware that may be running on the system.
6. OSForensics: OSForensics is a digital forensics tool that can analyze data from various sources, including hard drives, mobile devices, and memory cards. It includes a powerful search engine and supports various file systems and data types.
7. Nessus: Nessus is a vulnerability scanning tool that can identify vulnerabilities in computer systems and networks. It can help identify security weaknesses and recommend fixes to mitigate them.
8. NetWitness: NetWitness is a network security tool that can monitor network traffic and identify security threats in real time. It includes various security analytics features and can help identify and respond to network attacks.
9. Maltego: Maltego is a data mining and analysis tool that can be used to gather and analyze information about a target. It can help identify relationships between various entities and provide insights into their behavior.
10. Cellebrite UFED: Cellebrite UFED is a mobile forensic tool that can extract data from various mobile devices, including smartphones and tablets. It can recover deleted data and analyze various data types, including call logs, text messages, and social media data.
These are just a few examples of the software tools used for cyber investigation, and there are many other specialized tools available for specific types of investigations. Investigators need to choose the right tools for the job and have the necessary training and expertise to use them effectively.
Explore the evolution of the Internet

The internet has transformed the way we communicate, work, and access information. It has become an integral part of modern life and has revolutionized many industries. This article will provide a detailed history of the internet, the various phases of its growth, reflect on its current state, and speculate on its future.
The Internet began as a small research network created by the United States Department of Defense in the 1960s. Known as ARPANET, the network connected computers at several universities and research centers. The primary goal of the network was to allow researchers to share information and communicate more efficiently.
Over the next few decades, the internet grew rapidly, and various technologies and protocols were developed to facilitate this growth. In the 1980s, the introduction of the Transmission Control Protocol/Internet Protocol (TCP/IP) made it easier for different computer networks to communicate with each other. This laid the foundation for the modern internet we know today.
The early 1990s marked a turning point for the internet. The introduction of the World Wide Web made it easier for people to access and share information over the internet. This led to a surge in internet usage and the creation of numerous websites.
By the late 1990s, the internet had become a global phenomenon. The introduction of high-speed internet connections and the proliferation of mobile devices further increased internet usage. Companies began to recognize the potential of the Internet for business, and e-commerce sites like Amazon and eBay emerged.
In the 2000s, the internet continued to grow, and social media platforms like Facebook, Twitter, and YouTube emerged, revolutionizing the way people communicate and share information. The rise of cloud computing and big data also transformed the way businesses operate and store information.
Today, the internet has become an essential part of daily life for billions of people worldwide. It is used for everything from communication and entertainment to shopping and education. The Internet has also become a vital tool for businesses, enabling them to reach a global audience and operate more efficiently.
Looking ahead, the future of the internet is likely to be shaped by a range of factors. The proliferation of connected devices and the Internet of Things (IoT) is likely to continue, with more and more devices being connected to the Internet. Artificial intelligence (AI) and machine learning are also likely to play an increasingly significant role in shaping the future of the Internet. These technologies will enable more personalized and tailored experiences for users, as well as more efficient and effective operations for businesses.
The internet has come a long way since its humble beginnings as a research network. It has revolutionized the way we communicate, work, and access information, and has become an essential part of modern life. As we look to the future, it is clear that the internet will continue to evolve and transform, shaping the way we live and work for years to come.
Many pioneers of the internet made significant contributions to its development. Here are a few of the most important figures and their key contributions:
- Vint Cerf and Bob Kahn: Cerf and Kahn are often referred to as the "fathers of the internet" because they were instrumental in the development of the TCP/IP protocol, which forms the basis of modern internet communication. They co-designed TCP/IP in the 1970s, and their work allowed different computer networks to communicate with each other, paving the way for the global internet we know today.
- Tim Berners-Lee: Berners-Lee invented the World Wide Web in the early 1990s while working at the European Organization for Nuclear Research (CERN). He created the first web browser and web server and developed the basic protocols that enable web pages to be accessed and shared over the internet. His work democratized access to information and transformed the way we communicate and share knowledge.
- Larry Page and Sergey Brin: Page and Brin co-founded Google in 1998, which has become the world's most popular search engine. They developed a revolutionary algorithm that allowed Google to return more relevant search results than any other search engine at the time. Their work has transformed the way we find and access information on the internet.
- Steve Jobs and Steve Wozniak: Jobs and Wozniak co-founded Apple in 1976, and their work revolutionized personal computing. They developed the first commercially successful personal computer, the Apple II, and later introduced the Macintosh, which introduced many of the graphical user interface elements that are now commonplace in modern computing. Apple's innovations have had a significant impact on the way we interact with technology.
- Marc Andreessen: Andreessen co-founded Netscape Communications Corporation in 1994, which developed the first widely-used web browser, Netscape Navigator. This allowed users to easily access and navigate the web and paved the way for the widespread adoption of the World Wide Web. Andreessen has since gone on to become a successful venture capitalist and has invested in many successful technology companies.
These are just a few of the pioneers of the internet who played critical roles in its development. Their contributions have transformed the way we live and work, and their legacy continues to shape the future of technology and the internet.
The World Wide Web (WWW or Web) is a fundamental component of the Internet and has revolutionized the way people communicate, learn, and conduct business. It has become an integral part of our daily lives and continues to evolve and shape the world around us.
The World Wide Web (WWW or Web) is an interconnected system of electronic documents and resources, which are accessed via the Internet using a web browser. The Web was invented by Sir Tim Berners-Lee in 1989 as a way for scientists to share information more easily. Since then, it has grown to become a ubiquitous tool used by billions of people worldwide for communication, research, entertainment, and more.
Size of the World Wide Web: The size of the World Wide Web is difficult to estimate precisely, as it is constantly changing and growing. As of 2021, it is estimated that the web contains over 1.8 billion websites and more than 6 billion web pages. The total size of the web is estimated to be around 10 petabytes (10,000 terabytes).
Uses of the World Wide Web:
The World Wide Web has a wide range of uses, including:
- Communication: The Web is widely used for communication, including email, messaging, social media, and video conferencing.
- Information sharing: The Web is a vast repository of information on a wide range of topics, and is used for research, education, and news.
- Entertainment: The Web is used for entertainment purposes such as streaming movies, music, and games.
- E-commerce: The Web is widely used for online shopping, banking, and other financial transactions.
- Advertising: The Web is a major platform for advertising and marketing, with many businesses using the Web to promote their products and services.
- Collaboration: The Web is used for collaborative work, such as online document editing, project management, and virtual team communication.
The World Wide Web is divided into 3 parts explained below:
- Surface Web: This is part of the web that is publicly accessible and indexed by search engines. It includes websites that are designed to be accessed by anyone with an internet connection.
- Deep Web: This is part of the web that is not indexed by search engines and is not accessible through standard web browsers. It includes data that is not intended for public consumption, such as databases, private networks, and internal company information.
- Dark Web: This is a small part of the deep web that is intentionally hidden and can only be accessed using specialized software. It is often used for illegal activities such as the sale of drugs, weapons, and stolen data.
In summary, the World Wide Web is a vast and constantly evolving network of interconnected electronic resources, which is used for a wide range of purposes by billions of people around the world.
1. The Surface Web:
The surface Web, also known as the visible Web or indexable Web, refers to the part of the World Wide Web that can be indexed and searched by search engines such as Google, Yahoo, and Bing. This portion of the Web is publicly accessible and contains billions of websites and pages that cover a wide range of topics, from news and entertainment to e-commerce and education.
The Surface Web is an indispensable aspect of the World Wide Web, providing users with a vast array of information and resources. However, it is not without its challenges. As users, we must be vigilant about protecting our privacy and security online, as well as discerning when it comes to the information we consume and share. By understanding the Surface Web's uses, size, users, and challenges, we can become better informed and responsible digital citizens.
The Surface Web is the most familiar and widely used aspect of the World Wide Web, providing a vast array of information and resources to users around the world. However, this accessibility and openness also make it vulnerable to various risks and challenges that users must be aware of to keep themselves safe online.
Uses of Surface Web: The surface Web has become an essential tool for communication, research, education, entertainment, and business. It is widely used for accessing information, connecting with others, and conducting online transactions.
Size of Surface Web: The size of the surface Web is difficult to estimate accurately, as it is constantly changing and growing. As of 2021, it is estimated that the surface Web contains over 4.6 billion indexed pages.
Users of Surface Web: The Surface Web is used by a wide range of people, including students, researchers, business owners, journalists, and everyday internet users.
Challenges Faced by the Surface Web
One of the most significant challenges faced by the Surface Web is the proliferation of fake news, propaganda, and disinformation. With the ease of access and the abundance of information available on the Surface Web, it is becoming increasingly difficult to differentiate between credible and false information. The spread of misinformation can have severe consequences, ranging from harm to personal reputation to influencing public opinion and even undermining democratic processes.
Another significant challenge is the risk of cyberattacks, identity theft, and privacy violations. As more and more personal information is shared online, the risk of this information falling into the wrong hands increases. Cybercriminals can use this information for financial gain, or worse, to carry out malicious activities such as fraud, cyberbullying, and cyberstalking.
Uses and Users of the Surface Web
Despite these challenges, the Surface Web remains an indispensable tool for communication, education, entertainment, and e-commerce. Millions of users around the world access it daily, making it a crucial platform for information sharing and collaboration. From online banking to social media, the Surface Web has become an integral part of modern life.
Keeping the Surface Web Safe
To keep the Surface Web safe, users must take proactive measures to protect their privacy and security. This includes using strong and unique passwords, enabling two-factor authentication, and avoiding clicking on suspicious links or downloading unverified files. Users should also be cautious about the information they share online and the websites they visit. Avoid sharing personal information such as your full name, address, or date of birth online, and make sure to only visit reputable and trustworthy websites.
The Surface Web is a valuable resource that has transformed the way we communicate, learn, and conduct business. However, it also faces numerous challenges that users must be aware of to stay safe online. By understanding these challenges and taking proactive measures to protect our privacy and security, we can continue to benefit from the vast array of information and resources available on the Surface Web.
2. Deep Web
When people talk about the Internet, they often refer to the World Wide Web, which is a vast network of interconnected websites and pages that are accessible to anyone with an Internet connection. However, there is a part of the internet that is not indexed by search engines and not accessible through standard web browsers - the Deep Web. The Deep Web is often associated with illegal activities, but it is also used for legitimate purposes. In this article, we will explore what the Deep Web is, its uses, size, users, challenges it faces, and how to keep it safe.
The Deep Web is a part of the internet that is not accessible through standard web browsers and is not indexed by search engines. It includes websites and pages that are not intended for public consumption, such as databases, private networks, and internal company information. The Deep Web is often confused with the Dark Web, which is a small part of the Deep Web that is intentionally hidden and can only be accessed using specialized software.
Uses of the Deep Web:
The Deep Web is used for a variety of purposes, both legal and illegal. For example, it is used by researchers and journalists to access information that is not publicly available, such as academic articles and government reports. It is also used by businesses to protect sensitive information and to communicate with customers and suppliers anonymously.
However, the Deep Web is also used for illegal activities, such as the sale of drugs, weapons, and stolen data. It is also a haven for hackers and cybercriminals who can use anonymity and lack of oversight to carry out attacks and steal data.
Size and Users of the Deep Web:
The size of the Deep Web is difficult to estimate, as it is constantly changing and growing. However, some estimates suggest that it is several orders of magnitude larger than the surface web. It is used by a wide range of people, including researchers, journalists, businesses, and cybercriminals.
Challenges and Risks:
One of the main challenges of the Deep Web is its lack of oversight and regulation. This makes it a breeding ground for illegal activities and cybercrime. Additionally, because it is not indexed by search engines, it can be difficult to find information, and users can easily stumble upon dangerous or illegal content.
How to Stay Safe on the Deep Web:
If you choose to access the Deep Web, it is important to take steps to protect your privacy and security. This includes using a secure browser, such as Tor, which encrypts your traffic and masks your IP address. It is also important to use a VPN (Virtual Private Network) to further protect your identity and to avoid clicking on unfamiliar links or downloading unknown files.
The Deep Web can be a valuable resource for researchers, businesses, and individuals who value privacy and anonymity. However, it is also a risky place that can expose users to illegal activities and cybercrime. By taking steps to protect your privacy and security, you can safely explore the Deep Web and use it for legitimate purposes.
3. The Dark Web:
The dark web is a part of the internet that is often associated with illegal activities such as drug trafficking, weapons trading, and other illicit transactions. However, not everything on the dark web is illegal. This article will explore what the dark web is, how it is used, its size, and its users. We will also discuss the challenges it faces and provide tips on how to stay safe while using it.
The dark web is a part of the internet that is not indexed by search engines and can only be accessed using special software, such as the Tor network. It is often associated with illegal activities such as drug trafficking, weapons trading, and other illicit transactions. However, not everything on the dark web is illegal. There are legitimate uses for the dark web, such as providing a secure and anonymous platform for whistle-blowers and journalists.
Size and Users of the Dark Web
The size of the dark web is difficult to estimate, as it is not indexed and constantly changing. However, it is believed to be significantly smaller than the surface web, which is publicly accessible and indexed by search engines. The dark web is also believed to have a much smaller user base, consisting mostly of individuals who require anonymity for legitimate or illicit reasons.
Uses of the Dark Web
The dark web is primarily used for anonymity and privacy, as it allows users to communicate and conduct transactions without revealing their identity or location. This makes it a popular platform for whistle-blowers, journalists, activists, and individuals living in countries with strict censorship laws. However, it is also used for illegal activities, such as drug trafficking, weapons trading, and the sale of stolen data.
Challenges Faced by the Dark Web
The dark web faces several challenges, such as the risk of cybercrime, law enforcement efforts, and the potential for scams and fraud. Users of the dark web must be cautious and take steps to protect their privacy and security, such as using strong encryption and avoiding sharing personal information.
How to Stay Safe on the Dark Web
If you choose to explore the dark web, it is important to take precautions to protect your privacy and security. This includes using strong passwords, encryption, and avoiding sharing personal information. It is also recommended to use a reputable VPN service to hide your location and prevent tracking. Above all, use common sense and avoid any activities that could potentially harm yourself or others.
The dark web is a complex and often dangerous part of the internet. While there are legitimate uses for the dark web, it is important to exercise caution and take steps to protect your privacy and security. By staying informed and using the right tools and techniques, you can explore the dark web safely and responsibly.
Surface, deep, and dark net are three different parts of the internet, each with distinct characteristics.
Similarities:
All three nets are parts of the World Wide Web and are accessible through the Internet. Each of them contains various websites, online services, and resources that users can access. Additionally, they are all vulnerable to cybersecurity risks, such as hacking, data breaches, and identity theft.
Differences:
Surface Net:
Surface net, also known as the Clearnet, is the most commonly used and easily accessible part of the internet. It comprises websites and services that are indexed by search engines and accessible through web browsers. Surface net websites are designed to be accessed by anyone, and users do not need special software or knowledge to access them. Examples of surface net websites include social media platforms, e-commerce sites, and news websites.
Deep Net:
The deep net, also called the Hidden Web, is a subset of the internet that is not indexed by search engines. This means that the content on the deep net is not easily accessible through traditional web browsers. It includes databases, private networks, and websites that require specific login credentials or permissions to access. The deep net is often used for secure communication, such as online banking or corporate intranets.
Dark Net:
The dark net is a part of the internet that is intentionally hidden and designed to be accessed anonymously. It includes websites that use encryption and specialized software such as Tor to conceal their IP addresses and location. The dark net is known for its illicit activities, such as illegal marketplaces, hacking forums, and other criminal activities.
The Surface, Deep, and Dark nets are different parts of the internet, each with unique characteristics and accessibility. While the Surface net is easily accessible and contains openly available information, the Deep and Dark nets are hidden and require special permissions or software to access. Understanding the differences between these three parts of the internet is essential for users to stay safe and secure online.
Driving Successful Digital Transformation: Key Factors and Risks

Digital transformation is no longer a buzzword but a critical business imperative for companies looking to stay competitive and thrive in the digital age. However, digital transformation is not just about implementing new technologies but also about transforming the way companies operate, engage with customers, and deliver value. In this paper, we will discuss the key steps, success factors, and risks involved in driving a successful digital transformation in companies. By understanding these factors and developing a comprehensive digital transformation strategy, organizations can mitigate risks and reap the benefits of digital transformation.
The world has witnessed an unprecedented shift towards digitalization over the past decade, and companies have been forced to adapt to this change to stay relevant and competitive. In particular, a company needs to embrace digital transformation to remain agile, innovative, and customer-focused. But what exactly does it take to drive a successful digital transformation in a company?
First and foremost, it is essential to have a clear understanding of what digital transformation entails. Digital transformation is the integration of digital technologies into all areas of a business, resulting in fundamental changes to how the business operates and delivers value to its customers. It is not just about implementing new software or hardware; it is about transforming the entire organization to be more data-driven, customer-centric, and innovative.
One of the main benefits of a successful digital transformation is increased efficiency and productivity. For example, the use of automation technologies can streamline processes and reduce the need for manual labor. This frees up employees to focus on higher-level tasks that require human creativity and problem-solving skills. Additionally, the use of data analytics can provide valuable insights into customer behavior, enabling companies to make more informed decisions about product development, marketing, and customer service.
Another benefit of digital transformation is improved customer experiences. With the rise of e-commerce and social media, customers now have higher expectations for personalized, seamless, and omnichannel experiences. Digital technologies can help companies meet these expectations by enabling them to gather customer data, analyze it, and use it to deliver targeted marketing campaigns and personalized product recommendations. Furthermore, the use of chatbots and other AI-powered tools can improve customer service by providing quick and accurate responses to customer inquiries.
One example of a company that has successfully undergone digital transformation is Domino's Pizza. In 2009, the company launched its "Pizza Tracker" app, which allowed customers to track the progress of their pizza orders in real-time. Since then, the company has continued to invest in digital technologies, including mobile ordering, voice-activated ordering, and AI-powered chatbots. As a result, Domino's has experienced a significant increase in online orders and a corresponding decrease in phone orders, while also improving customer satisfaction.
However, driving a successful digital transformation is not without its challenges. One of the main obstacles is resistance to change among employees. To overcome this, it is important to involve employees in the digital transformation process and to provide them with the training and resources they need to adapt to new technologies. Additionally, it is important to have a clear and compelling vision for the digital transformation, as well as a strong leadership team to drive it forward.
Driving a successful digital transformation in a company requires a strategic approach that takes into account various factors, such as organizational culture, leadership, technology infrastructure, and employee engagement. In this paper, we will explore the key elements that are essential to achieving a successful digital transformation, as well as the benefits that such a transformation can bring to the organization.
First and foremost, it is important to have a clear vision and strategy for digital transformation. This involves identifying the areas of the organization that need to be transformed and determining the objectives and outcomes that are desired. The strategy should be communicated clearly and consistently to all stakeholders in the organization to ensure alignment and understanding.
Secondly, the leadership of the organization plays a critical role in driving digital transformation. Leaders need to be champions of the transformation, setting the tone and providing the necessary resources and support for the transformation to succeed. They also need to be able to communicate the vision and strategy effectively and lead by example, embracing the changes that come with the transformation.
Another critical factor in driving a successful digital transformation is the technology infrastructure of the organization. This involves assessing the current technology landscape and identifying the gaps and areas that need to be improved. Organizations should invest in robust and scalable technology solutions that are capable of supporting digital transformation initiatives.
Employee engagement is also a key element in driving a successful digital transformation. Organizations should involve employees in the planning and execution of the transformation, ensuring that they understand the rationale behind the changes and are equipped with the necessary skills to adapt to the new technology and processes. Providing training and development opportunities is essential to build the capabilities and confidence of employees.
A successful digital transformation can bring numerous benefits to the organization. These include improved efficiency, productivity, and agility, as well as better customer experience and engagement. For example, a bank that invested in digital transformation initiatives was able to reduce its loan application processing time from weeks to hours, resulting in improved customer satisfaction and increased revenue.
Another example is a retail company that implemented a digital supply chain management system, which enabled it to optimize inventory levels, reduce costs, and improve delivery times. This resulted in increased profitability and better customer satisfaction.
Driving a successful digital transformation in a company requires a strategic approach that involves a clear vision and strategy, strong leadership, robust technology infrastructure, and employee engagement. The benefits of a successful digital transformation are numerous, including improved efficiency, productivity, customer experience, and profitability. Organizations that embrace digital transformation are well-positioned to succeed in an increasingly digital and competitive business landscape.
Digital transformation is a critical component of a company's success in today's digital age. By embracing digital technologies and transforming the organization, companies can experience increased efficiency, improved customer experiences, and greater innovation. However, it is important to recognize the challenges involved in driving a successful digital transformation and to address these challenges proactively. With the right strategy, leadership, and support, a company can successfully navigate the digital landscape and thrive in the years to come.
Driving a successful digital transformation in a company requires a well-planned and executed strategy. The following are detailed steps that organizations can follow to drive such a transformation:
- Define your digital transformation strategy: Before embarking on a digital transformation journey, it is important to define your strategy. This should include a clear understanding of the business objectives and how digital technologies can help achieve them. Identify the areas of the business that would benefit the most from digital transformation and set specific goals that will be achieved through the transformation.
- Secure leadership buy-in: Driving a successful digital transformation requires leadership buy-in from the top down. Leaders need to be committed to the transformation and be willing to provide the necessary resources and support.
- Involve employees in the process: It is important to involve employees in the digital transformation process from the beginning. This helps to minimize resistance to change and increase employee buy-in. Employees should be provided with training and support to adapt to new technologies and processes.
- Identify the right technology partners: Finding the right technology partners is critical to the success of a digital transformation. Look for partners with experience in digital transformation who can provide the necessary expertise and support throughout the process.
- Develop a roadmap: Develop a detailed roadmap that outlines the steps involved in the digital transformation journey. This should include a timeline, milestones, and the resources required at each stage of the process.
- Implement new technologies: Implement the necessary technologies to support the digital transformation strategy. This may include software applications, cloud computing, IoT devices, and AI-powered tools.
- Collect and analyze data: Collect and analyze data to gain insights into customer behavior, business operations, and market trends. Use this data to inform business decisions and improve the customer experience.
- Optimize processes: Use digital technologies to optimize business processes and improve efficiency. This may include the use of automation, AI-powered tools, and robotics.
- Foster a culture of innovation: Foster a culture of innovation within the organization. Encourage employees to think creatively and come up with new ideas to improve business operations and customer experiences.
- Continuously evaluate and adapt: Digital transformation is an ongoing process that requires continuous evaluation and adaptation. Regularly review the strategy, assess the results, and make necessary adjustments to ensure that the transformation is achieving the desired outcomes.
Driving a successful digital transformation in a company requires a strategic and holistic approach. By following these detailed steps, organizations can successfully navigate the digital landscape and achieve the benefits of digital transformation.
Several key factors can ensure the success of a digital transformation in a company. These factors include:
- Leadership support and engagement: A clear commitment to digital transformation from senior leaders and management is crucial for the success of the initiative. Leaders must champion the change, provide resources and support, and ensure that the entire organization is aligned with the vision and goals of the transformation.
- Robust digital strategy: A well-defined digital strategy that aligns with the organization's goals, objectives, and customer needs is critical. This strategy should be developed with input from stakeholders across the organization and should outline clear goals, milestones, and success metrics.
- Focus on the customer experience: Customer experience should be at the forefront of the digital transformation effort. All initiatives should be designed to enhance the customer experience, and organizations should continuously gather customer feedback and use it to refine their approach.
- Agile approach: The digital landscape is constantly changing, and organizations need to be able to respond quickly and effectively to these changes. An agile approach that prioritizes flexibility, adaptability, and speed is essential for the success of a digital transformation.
- Employee engagement and empowerment: Employees are key to the success of a digital transformation initiative. They must be engaged and empowered to drive the change and adapt to new ways of working. This includes providing training and development opportunities, as well as creating a culture that fosters innovation and continuous improvement.
- Robust data analytics: Data analytics is a crucial component of any digital transformation initiative. Organizations should invest in tools and technologies that enable them to collect, analyze, and interpret data to drive decision-making and improve business outcomes.
- Collaboration and partnerships: Collaboration and partnerships with external stakeholders such as technology providers, industry peers, and academia can help organizations stay at the forefront of digital innovation and drive successful transformation.
A successful digital transformation requires a combination of factors, including strong leadership support, a well-defined strategy, a focus on customer experience, an agile approach, engaged employees, robust data analytics, and collaboration and partnerships. Organizations that prioritize these factors are more likely to achieve the desired outcomes of their digital transformation efforts.
As with any major business initiative, there are risks associated with digital transformation. The following are some of the key risks that organizations may encounter when driving a digital transformation in a company:
- Cost overruns: Digital transformation initiatives can be expensive, and there is a risk of cost overruns if the project is not properly scoped and managed.
- Implementation challenges: Implementing new technologies and processes can be complex and challenging, and there is a risk of delays, errors, and other implementation challenges that could impact the success of the initiative.
- Resistance to change: Change is difficult for many people, and there is a risk of resistance to change from employees who may be comfortable with existing processes and technologies.
- Cybersecurity threats: As companies become more reliant on digital technologies, there is a higher risk of cyber threats such as data breaches, hacking, and ransomware attacks.
- Data privacy and compliance: As organizations collect and analyze more data, there is a risk of violating data privacy regulations such as GDPR and CCPA, which can result in legal and financial penalties.
- Talent shortage: Digital transformation requires specialized skills and expertise, and there is a risk of a talent shortage if the organization does not have the necessary skills in-house or is unable to attract and retain top talent.
- Business continuity: There is a risk that digital transformation initiatives may disrupt existing business operations and impact customer service, leading to a negative impact on revenue and customer satisfaction.
- Failure to achieve desired outcomes: Despite best efforts, there is always a risk that the digital transformation initiative may not deliver the desired outcomes, resulting in a waste of resources and time.
Organizations must be aware of the risks associated with digital transformation and take steps to mitigate them through careful planning, risk assessment, and ongoing monitoring and management. With the right approach, organizations can successfully navigate these risks and achieve the desired outcomes of their digital transformation initiatives.
Several key factors can ensure the success of a digital transformation initiative in a company. These include:
1. Strong leadership: The commitment and support of senior leadership are critical to the success of a digital transformation initiative. Leaders should set the tone, communicate the vision and strategy effectively, and provide the necessary resources and support to ensure the success of the initiative.
2. Clear and consistent vision and strategy: A clear and consistent vision and strategy are essential to align stakeholders and ensure that everyone is working towards the same goals.
3. Robust technology infrastructure: A robust and scalable technology infrastructure is necessary to support digital transformation initiatives. This includes upgrading or replacing legacy systems, implementing new technologies, and ensuring that the technology infrastructure can support the growth and evolution of the organization.
4. Employee engagement: Employee engagement is critical to the success of a digital transformation initiative. Employees should be involved in the planning and execution of the initiative, provided with the necessary training and development, and encouraged to embrace the changes that come with digital transformation.
5. Effective change management: Effective change management is essential to address the organizational and cultural changes that come with a digital transformation initiative. This includes communication strategies, training and development programs, and other initiatives to support employee engagement and adoption of new technology and processes.
6. Data-driven decision-making: Data-driven decision-making is critical to the success of a digital transformation initiative. Organizations should invest in data analytics and other tools that can help them make informed decisions and monitor progress toward the desired outcomes.
7. Continuous improvement: Digital transformation is an ongoing process, and organizations should continuously assess and improve their technology landscape, processes, and organizational culture to stay competitive in an increasingly digital business environment.
A successful digital transformation initiative in a company requires a strategic approach that takes into account various factors, including strong leadership, a clear and consistent vision and strategy, robust technology infrastructure, employee engagement, effective change management, data-driven decision-making, and continuous improvement. By addressing these factors, organizations can ensure the success of their digital transformation initiatives and realize the benefits of digital transformation.
While digital transformation can offer many benefits to companies, it also involves several risks that organizations need to be aware of. Here are some of the key risks associated with digital transformation:
1. Technology failures: Implementing new technologies can be challenging and may result in technical failures or downtime, which can impact business operations and customer experience.
2. Cybersecurity threats: With increased reliance on digital technologies, organizations may face increased cybersecurity risks, such as data breaches, hacking, and malware attacks.
3. Employee resistance: Employees may resist changes associated with digital transformation, such as new processes, tools, and ways of working, which can impact productivity, morale, and engagement.
4. Cost overruns: Digital transformation initiatives can be expensive, and there is a risk of cost overruns if the implementation is not properly planned and managed.
5. Data quality issues: Poor data quality can undermine the effectiveness of digital transformation initiatives, leading to inaccurate or incomplete data analysis, decision-making, and reporting.
6. Integration challenges: Integrating new technologies and processes with existing systems and processes can be complex and may result in integration challenges, such as data incompatibility and process gaps.
7. Regulatory compliance: Digital transformation initiatives may face regulatory compliance risks, such as non-compliance with data privacy laws or regulations related to data security.
Digital transformation involves several risks that organizations need to be aware of and plan for. By addressing these risks and developing a comprehensive risk management plan, organizations can mitigate the risks and realize the benefits of digital transformation.
Protecting Your Business from Cyber Threats in Remote Working Environments

Cyber attacks are becoming increasingly common, and black hat hackers are constantly finding new ways to exploit vulnerabilities in computer systems. To protect yourself and your organization from cyber attacks, it's important to know how to catch a black hat hacker. In this article, we'll explore the essential tools and skills you need to identify and catch a black hat hacker, including gathering evidence, analyzing data, tracing the source of the attack, and collaborating with law enforcement. Whether you're a cybersecurity professional, a business owner, or simply interested in online security, this guide will provide you with the knowledge and resources you need to protect yourself from cyber threats.

Catching a black hat hacker requires a set of skills, tools, and techniques to identify and prevent illegal activities. In this article, we'll guide you through the essential steps to catch a black hat hacker, including gathering evidence, analyzing data, tracing the source of the attack, and collaborating with law enforcement.
Catching a black hat hacker is a complex and challenging task that requires a variety of skills and tools. Here are some steps and requirements that can help in catching a black hat hacker:
- Gather evidence: To catch a black hat hacker, you need to collect evidence that can link them to illegal activities. This can include network logs, system logs, firewall logs, and any other data that can help identify the hacker's activity. For example, if a hacker gains unauthorized access to a company's network and steals sensitive data, you can collect evidence by examining the logs of the network activity to identify the IP addresses used by the hacker and the time of the attack.
- Analyze the evidence: Once you have gathered evidence, you need to analyze it to identify patterns and trends that can help identify the hacker's activities. This requires skills in data analysis and network security. For example, you can use data analysis tools like Microsoft Excel or Python to identify patterns in the network traffic or log files that indicate suspicious activity, such as repeated login attempts or traffic from a foreign IP address.
- Trace the source: To catch a black hat hacker, you need to trace the source of their attacks. This requires knowledge of network protocols and the ability to analyze network traffic.
- Identify vulnerabilities: Black hat hackers exploit vulnerabilities in software and systems. To catch them, you need to identify these vulnerabilities and patch them to prevent future attacks. This requires skills in vulnerability scanning and penetration testing.
- Collaborate with law enforcement: Catching a black hat hacker often requires collaboration with law enforcement agencies. You need to have good communication skills and knowledge of legal procedures.
- Stay up-to-date: Black hat hackers are constantly evolving their tactics and techniques. To catch them, you need to stay up-to-date with the latest security trends and technologies.
Here are some tools that can aid in catching a black hat hacker:
- Wireshark: A network protocol analyzer that can help in capturing and analyzing network traffic.
- Snort: An IDS that can detect and alert suspicious network activity.
- Metasploit: A penetration testing tool that can identify vulnerabilities in systems.
- Nmap: A network scanner that can identify hosts and services on a network.
- Security information and event management (SIEM) systems: Tools that collect and analyze security information from multiple sources to identify potential security threats.
Note: Catching a black hat hacker requires a combination of technical skills, analytical abilities, and collaboration with law enforcement agencies.
Protecting Your Business from Cyber Threats in Remote Working Environments
Protecting yourself from black hat hackers and cyber attacks requires a combination of tools and skills. In this article, we will explore the essential steps you need to take to protect yourself from cyber threats, including the tools you can deploy and the skills you need to master.
Step 1: Conduct Regular Security Audits
The first step to protecting yourself from cyber attacks is to conduct regular security audits. This involves analyzing your computer systems and networks to identify any vulnerabilities or weaknesses that could be exploited by hackers. A thorough security audit should cover all aspects of your system, including hardware, software, and network infrastructure.
Tools to Deploy:
- Vulnerability Scanners: Vulnerability scanners are tools that identify potential vulnerabilities in your system. Some popular vulnerability scanners include Nessus, OpenVAS, and Qualys.
- Penetration Testing Tools: Penetration testing tools simulate real-world attacks to identify vulnerabilities that could be exploited by hackers. Some popular penetration testing tools include Metasploit, Nmap, and Burp Suite.
Skills Required:
- Technical Knowledge: Conducting a thorough security audit requires technical knowledge of computer systems and networks.
- Attention to Detail: A successful security audit requires attention to detail to identify even the smallest vulnerabilities.
Step 2: Use Antivirus Software and Firewalls
Antivirus software and firewalls are essential tools to protect yourself from cyber-attacks. Antivirus software detects and removes malware from your system, while firewalls monitor and control incoming and outgoing network traffic.
Tools to Deploy:
- Antivirus Software: Some popular antivirus software includes Norton, McAfee, and Kaspersky.
- Firewalls: Windows and Mac OS come with built-in firewalls, but you can also use third-party firewalls such as ZoneAlarm and Comodo Firewall.
Skills Required:
- Knowledge of Firewall Rules: To configure your firewall properly, you need to know firewall rules.
- Familiarity with Antivirus Software: To use antivirus software effectively, you need to be familiar with how it works and how to update it regularly.
Step 3: Use Strong Passwords and Two-Factor Authentication
Weak passwords are a common vulnerability that hackers can exploit to gain access to your system. To protect yourself from cyber attacks, you need to use strong passwords and two-factor authentication.
Tools to Deploy:
- Password Managers: Password managers such as LastPass, Dashlane, and 1Password can help you generate and manage strong passwords.
- Two-Factor Authentication Apps: Two-factor authentication apps such as Google Authenticator and Authy provide an extra layer of security by requiring a second form of authentication.
Skills Required:
- Password Management: To use password managers effectively, you need to understand how they work and how to use them to generate and manage strong passwords.
- Familiarity with Two-Factor Authentication: To use two-factor authentication effectively, you need to be familiar with how it works and how to set it up on your accounts.
Step 4: Keep Your Software and Operating System Up-to-Date
Keeping your software and operating system up-to-date is essential to protect yourself from cyber-attacks. Software updates often include security patches that address vulnerabilities that hackers could exploit.
Tools to Deploy:
- Automatic Updates: Most software and operating systems have an automatic update feature that you can enable.
- Vulnerability Scanners: Vulnerability scanners can help you identify software and operating systems that need to be updated.
Skills Required:
- Familiarity with Software and Operating System Updates: To keep your software and operating system up-to-date, you need to be familiar with how to check for updates and install them.
- Patience: Software updates can take time, so you need to be patient and allow enough time for the updates to be completed.
Protecting yourself from cyber attacks requires a combination of tools, skills, and awareness. In addition to the steps outlined above, there are other best practices you should follow to protect yourself from cyber threats, including:
- Be wary of suspicious emails and phishing scams.
- Regularly back up your data to protect against data loss.
- Educate yourself on the latest cyber threats and trends.
Ultimately, the best defense against cyber attacks is a multi-layered approach that involves a combination of tools, skills, and awareness. By following the steps outlined in this article, you can significantly reduce your risk of falling victim to a cyber attack. However, it's important to remain vigilant and continue to educate yourself on the latest cyber threats to ensure that you stay protected.
The increase in remote working has added several challenges to protecting against cyber threats. Here are some of the main challenges and how to address them:
1. Increased Vulnerability to Phishing Attacks: With remote working, employees are more likely to use personal devices and networks that may not have the same level of security as corporate networks. This increases the risk of phishing attacks, where cyber criminals send fraudulent emails to trick users into divulging sensitive information.
How to Address: Educate employees on how to identify and report phishing attacks. Implement a multi-factor authentication system to prevent unauthorized access to corporate accounts.
2. Lack of Physical Security: With remote working, devices, and data may not be physically secured as they would be in an office environment. This increases the risk of theft or loss of sensitive information.
How to Address: Implement policies for securing devices, such as encrypting hard drives and using remote wipe capabilities. Educate employees on the importance of physical security and how to secure their devices.
3. Unsecured Networks: When working remotely, employees may connect to public Wi-Fi networks that are not secure, leaving them vulnerable to cyber-attacks.
How to Address: Encourage employees to use a virtual private network (VPN) to connect to the company network securely. Provide guidelines on how to connect to secure Wi-Fi networks and avoid public networks.
4. Shadow IT: With remote working, employees may be more likely to use unauthorized software or services that could compromise security.
How to Address: Establish clear policies on the use of software and services. Educate employees on the risks of using unauthorized software and services and provide them with alternatives.
5. Lack of Communication and Collaboration: Remote working can lead to a lack of communication and collaboration, making it more difficult to identify and address security issues.
How to Address: Establish regular communication channels between employees and IT staff to ensure that security issues are identified and addressed promptly. Use collaboration tools to facilitate communication and collaboration between remote workers.
Here are some examples to illustrate the challenges and solutions for protecting against cyber threats in remote working environments:
1. Increased Vulnerability to Phishing Attacks:
Challenge: An employee receives an email on their device that appears to be from a trusted source, such as their bank or a company they do business with. The email contains a link that takes the employee to a fraudulent website that looks like the real one. The employee unwittingly enters their login credentials, giving the cybercriminal access to their sensitive information.
Solution: The company provides training on how to identify phishing emails and what to do if an employee receives one. The company also implements a multi-factor authentication system that requires additional verification beyond a password to access corporate accounts, making it more difficult for cybercriminals to gain unauthorized access.
2. Lack of Physical Security:
Challenge: An employee working from home leaves their laptop unattended in a public place, such as a coffee shop or library. The laptop is stolen, along with sensitive information stored on it.
Solution: The company requires employees to encrypt their hard drives and use remote wipe capabilities to erase data in case of theft or loss. The company also provides training on the importance of physical security and how to secure devices, such as locking screens when stepping away from a computer.
3. Unsecured Networks:
Challenge: An employee connects to a public Wi-Fi network to work remotely without realizing that it is not secure. A cybercriminal intercepts data transmitted over the network, including login credentials and sensitive information.
Solution: The company provides guidelines on how to connect to secure Wi-Fi networks and encourages the use of a virtual private network (VPN) to connect to the company network securely. The company also educates employees on the risks of using public Wi-Fi networks and how to avoid them.
4. Shadow IT:
Challenge: An employee downloads an unauthorized software program to help them work more efficiently without realizing that it contains malware that compromises the security of the company network.
Solution: The company establishes clear policies on the use of software and services and provides alternatives to employees. The company also educates employees on the risks of using unauthorized software and services and the importance of following company policies.
5. Lack of Communication and Collaboration:
Challenge: An employee working remotely encounters a security issue, but does not report it to IT staff because they feel disconnected and out of the loop.
Solution: The company establishes regular communication channels between employees and IT staff to ensure that security issues are identified and addressed promptly. The company also uses collaboration tools to facilitate communication and collaboration between remote workers, such as video conferencing and instant messaging.
In summary, the increase in remote working has added several challenges to protecting against cyber threats. However, by implementing the appropriate policies, educating employees, and using the right tools, organizations can effectively address these challenges and ensure that their remote workers are protected from cyber-attacks.
Investigating Crimes on the Dark Net: Techniques and Challenges

The dark net is a portion of the internet that is not accessible through traditional search engines or browsers and is known for being a hub of criminal activities. Investigating crimes on the dark net presents a unique set of challenges for enforcement agencies and ethical hackers. This article will delve into the techniques used to investigate crimes on the dark net and the challenges that investigators face. It will also provide examples of successful investigations and discuss the constantly evolving nature of the dark net.
Learn about how enforcement agencies and ethical hackers investigate crimes on the dark net, including techniques used and challenges faced. Discover examples of dark net investigations and how anonymity and the evolving nature of the dark net make it difficult to track down criminals.
The dark net, also known as the dark web, refers to a portion of the internet that is not accessible through traditional search engines or browsers. It is a hub for criminal activities, ranging from illegal drug sales to human trafficking, and the exchange of stolen personal information. Law enforcement agencies and ethical hackers have a responsibility to investigate crimes that occur on the dark net to ensure that perpetrators are brought to justice. However, investigating crimes on the dark net presents a unique set of challenges that require specialized skills and tools.
Enforcement agencies, such as the Federal Bureau of Investigation (FBI) and the Drug Enforcement Administration (DEA), investigate crimes on the dark net by utilizing various techniques, including computer forensics, undercover operations, and advanced data analysis. One example of how enforcement agencies investigate crimes on the dark net is the case of Ross Ulbricht, the founder of the Silk Road marketplace. The Silk Road was an online marketplace that facilitated the sale of illegal drugs and other illicit goods. The FBI was able to bring down the Silk Road by using sophisticated techniques, including tracking the Bitcoin transactions used to purchase drugs on the site.
In addition to enforcement agencies, ethical hackers also play a role in investigating crimes on the dark net. Ethical hackers, also known as white hat hackers, are computer experts who use their skills to identify and fix security vulnerabilities. They may be hired by law enforcement agencies to conduct penetration testing on dark net marketplaces to identify security weaknesses that can be exploited by criminals. Ethical hackers can also use their skills to infiltrate dark net marketplaces to gather intelligence on criminal activities. One example of how ethical hackers have helped to investigate crimes on the dark net is the case of the AlphaBay marketplace. Ethical hackers were able to infiltrate the AlphaBay marketplace and gather the information that led to the arrest and prosecution of its founder, Alexandre Cazes.
However, investigating crimes on the dark net is not without its challenges. One of the biggest challenges is the anonymity provided by the dark net. Criminals can use tools such as Tor and virtual private networks (VPNs) to hide their identity and location, making it difficult for enforcement agencies and ethical hackers to track them down. Another challenge is the constantly evolving nature of the dark net. Criminals are constantly developing new techniques to evade detection and law enforcement agencies and ethical hackers must stay up-to-date with the latest trends and technologies to keep up.
The dark net is a part of the internet that is not accessible through traditional search engines and can only be accessed through specialized software such as Tor (The Onion Router) or I2P (Invisible Internet Project). This anonymity makes it a breeding ground for criminal activities, including drug trafficking, weapons sales, and child pornography.
Enforcement agencies and ethical hackers play an essential role in investigating crimes on the dark net. However, their approach differs significantly, with enforcement agencies using legal means, while ethical hackers use technical means to uncover and report cybercriminal activities.
Enforcement agencies typically rely on their authority and investigative powers to identify and prosecute criminals operating in the dark net. They use various tactics to infiltrate dark net marketplaces and forums to gather evidence, including:
- Covert Operations: Law enforcement agencies can conduct covert operations in the dark net, posing as potential buyers or sellers to identify criminal activities. These operations can involve creating fake identities, using hidden cameras, and intercepting communications to gather evidence.
- Digital Forensics: Enforcing agencies can also rely on digital forensics to collect and analyze data from seized devices, including mobile phones, computers, and other electronic devices. This data can provide evidence of criminal activities, including communications, financial transactions, and IP addresses.
- Surveillance: Law enforcement agencies can also use advanced surveillance techniques to monitor dark net activities. These techniques can include wiretapping, GPS tracking, and other forms of electronic surveillance.
- Cooperation with other agencies: To investigate and prosecute crimes in the dark net, enforcement agencies often collaborate with other law enforcement agencies, including international agencies, to share information and resources.
Examples of law enforcement agencies' successful operations in the dark net include:
- Operation Onymous: In 2014, law enforcement agencies from 17 countries, including the FBI and Europol, shut down several dark net marketplaces, including Silk Road 2.0 and Hydra. This operation led to the arrest of several individuals and the seizure of millions of dollars in cryptocurrencies.
- Operation Bayonet: In 2019, law enforcement agencies from the US, Germany, the Netherlands, and other countries shut down the dark net marketplace, the Wall Street Market. This operation led to the arrest of three individuals and the seizure of several million dollars in cryptocurrencies.
On the other hand, ethical hackers use their technical expertise to uncover cybercriminal activities and report them to relevant authorities. Ethical hackers, also known as white hat hackers, operate within the boundaries of the law and follow ethical guidelines to identify security vulnerabilities and potential cyber threats.
Ethical hackers can use various techniques to investigate crimes in the dark net, including:
- OSINT (Open-Source Intelligence): Ethical hackers can use OSINT techniques to collect and analyze publicly available information on the dark net. This information can include forum discussions, blog posts, and social media accounts used by cybercriminals.
- Web Application Testing: Ethical hackers can use web application testing techniques to identify security vulnerabilities in dark net marketplaces and forums. These vulnerabilities can include SQL injection, cross-site scripting, and other forms of web application attacks.
- Traffic Analysis: Ethical hackers can use traffic analysis to monitor dark net activities and identify potential cyber threats. This technique involves analyzing network traffic to identify patterns and anomalies in dark net communications.
Successful operations in the dark net by ethical hackers' include:
1. Operation Darknet: Operation Darknet was a law enforcement operation that took place in 2011 and targeted illegal activities on the dark web. The operation was a joint effort between several international law enforcement agencies, including the FBI, Europol, and the German Federal Criminal Police Office.
The operation focused on taking down websites and forums on the Tor network that were involved in the distribution of illegal goods and services, including drugs, firearms, and stolen credit card information. The operation was successful in taking down several high-profile websites, including the notorious Silk Road marketplace.
In addition to taking down these websites, Operation Darknet also resulted in the arrest of several individuals involved in illegal activities on the dark web. This included the arrest of Ross Ulbricht, the founder of Silk Road, who was sentenced to life in prison for his role in the operation of the marketplace.
Overall, Operation Darknet was a significant success in the fight against illegal activities on the dark web. It demonstrated the ability of law enforcement agencies to work together across international borders to target criminal activity online and served as a warning to others who may be involved in illegal activities on the dark web.
- Project Vigilant: Project Vigilant was a controversial private organization that claimed to operate as a non-profit, ethical hacking group in the United States. Founded in 2004, the organization gained attention in 2010 when it was revealed that it had been working with the US government and law enforcement agencies to provide information on potential cyber threats and criminal activity.
Project Vigilant claimed to use a variety of techniques, including data mining and monitoring of internet traffic, to identify potential threats to national security and public safety. However, the organization's methods and the extent of its cooperation with government agencies raised concerns about privacy and civil liberties.
In 2010, it was reported that the founder of Project Vigilant, Chet Uber, had been working with the US government and law enforcement agencies for several years, providing them with information on potential cyber threats and criminal activity. The organization was said to have been particularly active in monitoring internet traffic and social media activity and had reportedly uncovered several high-profile cyber attacks.
However, the revelation of Project Vigilant's cooperation with government agencies led to criticism from civil liberties groups, who raised concerns about the organization's lack of transparency and accountability. Some also questioned the legality of the group's methods, particularly its use of data mining and monitoring of internet traffic.
Despite the controversy, Project Vigilant continued to operate for several years but appears to have largely faded from public view in recent years. The organization's legacy remains a subject of debate, with some seeing it as a necessary tool in the fight against cybercrime and terrorism, while others view it as an example of the dangers of unchecked government surveillance and private sector involvement in intelligence gathering.
Tools used
There are various tools used by both enforcement agencies and ethical hackers to investigate crimes on the dark net. These tools vary depending on the specific needs and goals of the investigation.
- Tor Browser: The Tor Browser is a web browser that allows users to access the dark net through the Tor network. It provides anonymity by routing internet traffic through a series of servers, making it difficult to trace users' activities. To use the Tor Browser, download and install it on your computer, launch the browser, and type in the .onion URL of the website you want to access.
- Virtual Private Network (VPN): A VPN allows users to access the internet securely and privately by encrypting internet traffic and routing it through a remote server. It can help to mask the user's IP address and location. To use a VPN, download and install a VPN client on your computer, connect to a server, and then access the dark net through the Tor Browser.
- Maltego: Maltego is an open-source intelligence and forensics tool that allows investigators to collect and analyze data from various sources. It can help to visualize relationships between data and identify patterns and anomalies. To use Maltego, download and install it on your computer, and then create a new project. Add data sources and start analyzing the data.
- Wireshark: Wireshark is a network protocol analyzer that allows investigators to capture and analyze network traffic. It can help to identify suspicious activity, including malicious traffic and potential cyber threats. To use Wireshark, download and install it on your computer, start capturing network traffic, and then analyze the captured data.
- Nmap: Nmap is a network exploration tool that allows investigators to scan networks and identify potential vulnerabilities. It can help to identify open ports, operating systems, and potential security weaknesses. To use Nmap, download and install it on your computer, enter the target IP address, and start the scan.
- Metasploit: Metasploit is a penetration testing framework that allows investigators to simulate cyber attacks and identify potential vulnerabilities in systems and networks. It can help to test the effectiveness of security measures and identify areas that need improvement. To use Metasploit, download and install it on your computer, select a vulnerability to exploit, and launch the attack.
The darknet is a part of the internet that is not indexed by search engines and is only accessible through special software such as Tor. While the darknet has legitimate uses, it is also a haven for criminal activity, including drug trafficking, human trafficking, and cybercrime. Law enforcement agencies, researchers, and journalists often use various tools to investigate the dark net and uncover criminal activities.
In this article, we will explore some of the commonly used tools for investigating the darknet and how to use them.
1. Tor Browser Tor is the most popular software for accessing the darknet, and the Tor browser is a modified version of the Firefox browser that is designed to access Tor’s hidden services. The browser is easy to download and install, and it allows users to access the darknet anonymously. To use the Tor browser, simply download it from the official website, install it, and start browsing.
2. Virtual Private Networks (VPNs) VPNs are another tool that can be used to investigate the darknet. A VPN encrypts a user's internet traffic and routes it through a remote server, making it difficult to track the user's location and online activities. VPNs can be used to access the darknet and browse anonymously. However, it is important to note that not all VPNs are created equal, and some may not provide adequate protection against government surveillance or other forms of monitoring.
3. Darknet Search Engines Unlike regular search engines like Google, darknet search engines are designed to search for content on the darknet. These search engines are typically accessed through Tor and allow users to find hidden services and other content that is not indexed by regular search engines. Some popular darknet search engines include Torch, Grams, and Ahmia.
4. Bitcoin Analysis Tools Bitcoin is the most commonly used currency on the darknet, and it is often used for illegal transactions. Bitcoin analysis tools can be used to track Bitcoin transactions and uncover criminal activities. These tools include blockchain explorers, which allow users to view all Bitcoin transactions, and Bitcoin mixers, which are used to obfuscate the origin and destination of Bitcoin transactions.
5. Social Media Analysis Tools Social media is often used by criminals on the dark net to communicate and coordinate their activities. Social media analysis tools can be used to monitor these communications and uncover criminal networks. These tools include sentiment analysis tools, which analyze the tone and context of social media posts, and network analysis tools, which identify patterns and connections between social media accounts.
It is important to note that some of these tools, such as Metasploit, are powerful and potentially dangerous if used improperly. It is essential to use these tools only for legal and ethical purposes and with proper authorization. Moreover, before using any tool, it is advisable to seek guidance from experienced professionals or to receive proper training to avoid legal and ethical issues.
Investigating crimes on the dark net requires specialized skills and tools. By using tools like Tor, VPNs, darknet search engines, Bitcoin analysis tools, and social media analysis tools, investigators can uncover criminal activities and bring perpetrators to justice. However, it is important to note that investigating the darknet can be dangerous and should only be done by trained professionals who understand the risks involved.
Enforcement agencies and ethical hackers play a critical role in identifying and bringing criminals to justice. However, the challenges of anonymity and the constantly evolving nature of the dark net make it a complex and difficult task. As the dark net continues to grow, law enforcement agencies and ethical hackers must continue to develop new techniques and technologies to keep up with the ever-changing landscape of cybercrime.
Types of hackers and how to Safeguard Against them.

Hackers are a constant threat in today's digital age. From stealing personal information to launching large-scale cyber-attacks, hackers come in many different forms with varying motives. In this article, we will explore the different types of hackers and their techniques and best practices for safeguarding against cyber threats. We will also examine the enforcement agencies involved in apprehending cybercriminals and bringing them to justice.
The rise of digital technology has revolutionized the way we live, work, and communicate. However, it has also given rise to a new breed of criminal: the hacker. Hackers are individuals who use their technical skills to gain unauthorized access to computer systems and networks. The motives of hackers can vary from financial gain to political activism, but they all share one common goal: to exploit vulnerabilities in computer systems for their purposes. In this article, we will examine the different types of hackers, how to safeguard against them, and the enforcement agencies involved in apprehending these criminals.
Types of Hackers
Hackers can be classified into different types based on their motives and techniques. Here are the most common types of hackers:
- White Hat Hackers - Also known as ethical hackers, these are individuals who use their skills to identify vulnerabilities in computer systems and networks to improve security. They are often hired by organizations to test their systems and identify potential weaknesses.
- Black Hat Hackers - These are individuals who use their skills to gain unauthorized access to computer systems and networks for malicious purposes, such as stealing sensitive information or disrupting systems.
- Grey Hat Hackers - This is a term used to describe hackers who operate somewhere in between white hat and black hat hackers. They may identify vulnerabilities in computer systems and networks without permission but do not use the information they find for malicious purposes.
- Script Kiddies - These are individuals who lack the technical skills to hack into computer systems and networks on their own. Instead, they use pre-packaged software and tools to launch attacks on targets.
- State-Sponsored Hackers - These are individuals or groups who are sponsored by governments to conduct cyber-espionage or cyber-attacks against other countries or organizations.
How to Safeguard Against Hackers
To safeguard against hackers, organizations and individuals must take steps to improve their cybersecurity. Here are some best practices for safeguarding against hackers:
- Use strong passwords - Use complex passwords that include a combination of upper and lowercase letters, numbers, and symbols. Avoid using the same password for multiple accounts.
- Keep software up to date - Regularly update software to ensure that any known vulnerabilities are patched.
- Use antivirus software - Install and regularly update antivirus software to protect against malware and viruses.
- Use two-factor authentication - Use two-factor authentication for online accounts to provide an extra layer of security.
- Train employees - Train employees on best practices for cybersecurity, including how to identify phishing scams and how to handle sensitive information.
Enforcement Agencies Involved in Apprehending Hackers
Apprehending hackers can be a complex process that often involves multiple law enforcement agencies. Here are some of the enforcement agencies involved in apprehending hackers:
- Federal Bureau of Investigation (FBI) - The FBI is responsible for investigating cybercrime in the United States. They have a Cyber Division that focuses specifically on cybercrime.
- Department of Homeland Security (DHS) - The DHS is responsible for protecting the nation's critical infrastructure from cyber threats.
- National Security Agency (NSA) - The NSA is responsible for collecting and analyzing foreign communications and intelligence.
- International Criminal Police Organization (INTERPOL) - INTERPOL is an international organization that helps coordinate law enforcement efforts across borders.
- Europol - Europol is the law enforcement agency of the European Union. It is responsible for coordinating law enforcement efforts across member states.
Hackers pose a serious threat to organizations and individuals alike. To safeguard against hackers, it is important to understand the different types of hackers and their motives. By taking steps to improve cybersecurity, organizations, and individuals can protect themselves against cyber threats. In the event of a cyber-attack, law enforcement agencies can work together to apprehend the perpetrators and
Let's dive deeper.
- White Hat Hackers: White hat hackers are also known as ethical hackers. They use their technical skills to identify vulnerabilities in computer systems and networks to improve security. They are often hired by organizations to test their systems and identify potential weaknesses. They typically have a background in cybersecurity and are certified professionals. They use various tools such as vulnerability scanners, network analyzers, and password-cracking software to identify weaknesses in systems. White hat hackers are often associated with penetration testing and vulnerability assessments.
In 2019, a white hat hacker named Bill Demirkapi discovered a security flaw in a software program used by U.S. schools to manage student information. He reported the flaw to the software vendor and the Department of Education, who worked to fix the issue.
- Black Hat Hackers: Black hat hackers are individuals who use their skills to gain unauthorized access to computer systems and networks for malicious purposes. They often seek financial gain or personal satisfaction from their actions. They may use a variety of techniques to infiltrate systems, such as social engineering, malware, and phishing attacks. Black hat hackers are associated with cybercrime and cyber espionage.
In 2013, a group of black hat hackers from China infiltrated the computer systems of several U.S. companies, including Google and Adobe. They stole confidential information and intellectual property, leading to charges from the U.S. government.
- Grey Hat Hackers: Grey hat hackers operate somewhere between white hat and black hat hackers. They may identify vulnerabilities in computer systems and networks without permission but do not use the information they find for malicious purposes. They may seek recognition for their skills or draw attention to security flaws. Grey hat hackers are often unaffiliated with organizations and may operate independently.
In 2017, a grey hat hacker named Marcus Hutchins discovered a vulnerability in the WannaCry ransomware that had affected computer systems worldwide. He was able to halt the spread of the ransomware by registering a domain name associated with the malware, which triggered a "kill switch" and prevented further infections.
- Script Kiddies: Script kiddies are individuals who lack the technical skills to hack into computer systems and networks on their own. Instead, they use pre-packaged software and tools to launch attacks on targets. They often do not have a specific motive for their actions and may engage in hacking for fun or to prove their skills.
In 2015, a group of script kiddies launched a DDoS attack against several gaming companies, causing widespread disruptions to online gaming services.
- State-Sponsored Hackers: State-sponsored hackers are individuals or groups who are sponsored by governments to conduct cyber-espionage or cyber-attacks against other countries or organizations. They often have advanced technical skills and may have access to government resources to carry out their activities.
In 2020, the U.S. government accused hackers from Russia, China, and Iran of attempting to interfere in the U.S. presidential election. The hackers allegedly targeted political campaigns and election infrastructure in an attempt to influence the outcome of the election.
Safeguard Against Hackers:
- Use Strong Passwords: Use complex passwords that include a combination of upper and lowercase letters, numbers, and symbols. Avoid using the same password for multiple accounts.
A strong password might look like this: G4$8sB6#tZ!2q
- Keep Software Up to Date: Regularly update software to ensure that any known vulnerabilities are patched.
If you receive a notification to update your computer's operating system, do not ignore it. Install the update as soon as possible to keep your system secure.
- Use Antivirus Software: Install antivirus software on your computer to protect against malware and other threats. Keep the software up to date and run regular scans.
Popular antivirus software options include Norton, McAfee, and Kaspersky.
- Enable Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. This adds a layer of security to your accounts by requiring a second form of authentication, such as a code sent to your phone or a biometric scan.
Many popular social media platforms, such as Facebook and Twitter, offer 2FA as an option.
- Be Aware of Phishing Scams: Be cautious of suspicious emails or text messages that ask you to provide personal information or click on a link. Verify the source of the message before taking any action.
You receive an email from what appears to be your bank, asking you to click on a link to verify your account information. Instead of clicking the link, go directly to the bank's website and log in to your account to verify if the message is legitimate.
Enforcement Agencies Involved:
- Federal Bureau of Investigation (FBI): The FBI investigates and prosecutes cybercrime cases that involve federal law violations, including hacking and other computer-related crimes.
In 2020, the FBI charged two Chinese hackers with attempting to steal intellectual property from U.S. companies, including COVID-19 research data.
- Department of Justice (DOJ): The DOJ is responsible for prosecuting cybercrime cases involving federal law violations. They work closely with other law enforcement agencies to investigate and prosecute cybercriminals.
In 2019, the DOJ charged two Iranian hackers with hacking into several U.S. government agencies and organizations.
- Department of Homeland Security (DHS): The DHS is responsible for protecting the nation's critical infrastructure from cyber threats. They work with government agencies and private organizations to prevent cyber-attacks and respond to incidents.
In 2021, the DHS issued a warning about a vulnerability in Microsoft Exchange servers that was being exploited by hackers.
- International Criminal Police Organization (INTERPOL): INTERPOL is an international police organization that works to coordinate law enforcement efforts across borders. They help to track down cybercriminals and bring them to justice.
In 2018, INTERPOL led an operation to dismantle a cybercrime ring that had stolen over $100 million from banks around the world.
Hackers come in many different forms, each with their own motives and techniques. It's important to be aware of the different types of hackers and how they operate to better protect yourself and your organization from cyber threats. By following best practices, such as using strong passwords and keeping software up to date, you can reduce the risk of falling victim to a cyber-attack. If you do experience a cyber-attack, it's important to report it to law enforcement agencies, who can work to bring the perpetrators to justice.
Addressing the Biggest Digital Transformation Challenges: A Guide for IT Leadership

Digital transformation is essential for organizations to remain competitive and thrive in the digital age. However, it comes with various challenges that IT and organizational leadership must address to ensure a successful transformation. In this article, we explore the biggest challenges faced by organizations during digital transformation and provide practical solutions to overcome them. We will also discuss how organizational leadership can support IT leadership in overcoming these challenges and positioning the organization for success in the digital age.
Given that Digital transformation is a vital process for any organization that seeks to remain relevant in today's fast-paced business environment. However, the journey to digital transformation is not without its challenges. In this article, we will discuss the biggest digital transformation challenges that organizations face and provide actionable strategies for IT leadership to address them effectively.
Lack of Change Management Strategy
One of the most significant challenges facing organizations during digital transformation is the lack of a change management strategy. Organizations that fail to address change management often face significant resistance from employees who are not willing to embrace new technologies or processes.
To address this challenge, IT leadership should:
- Communicate the vision of the digital transformation to all employees
- Identify the stakeholders who will be impacted by the transformation and involve them in the planning process
- Develop a clear roadmap that outlines the steps involved in the digital transformation process
- Provide adequate training to employees to help them adapt to the new technologies and processes
Organizational leadership can support IT leadership in addressing this challenge by providing the necessary resources and support to ensure a smooth transition.
Complex Software & Technology
The complexity of software and technology is another significant challenge that organizations face during digital transformation. The process of integrating new technologies can be complicated, and it can be challenging to find the right tools to support the organization's needs.
To address this challenge, IT leadership should:
- Conduct thorough research on available technologies and identify the best tools to support the organization's needs
- Develop a clear plan for integrating new technologies and ensure that all stakeholders are involved in the process
- Provide adequate training to employees to ensure that they are comfortable using new technologies
Organizational leadership can support IT leadership by providing the necessary resources and funding to ensure that the organization has access to the best technologies to support its digital transformation process.
Driving the Adoption of New Tools & Processes
Even after the successful integration of new technologies, organizations often face challenges in driving the adoption of new tools and processes. Many employees may be resistant to change, and it can be challenging to convince them to embrace new technologies and processes.
To address this challenge, IT leadership should:
- Provide adequate training and support to employees to ensure that they are comfortable using new technologies and processes
- Communicate the benefits of new technologies and processes to employees
- Provide incentives for employees who embrace new technologies and processes
Organizational leadership can support IT leadership by providing a culture that supports change and innovation. This can be achieved by promoting a culture of experimentation and recognizing employees who embrace change and contribute to the organization's digital transformation process.
Continuous Evolution of Customer Needs
Organizations must stay up-to-date with their customers' evolving needs to remain relevant. However, it can be challenging to keep up with the pace of change, and many organizations struggle to keep up with customer demands.
To address this challenge, IT leadership should:
- Conduct regular market research to understand customer needs and expectations
- Develop a flexible and scalable digital infrastructure that can adapt to changing customer needs
- Develop a culture of innovation that encourages employees to experiment with new ideas and technologies
Organizational leadership can support IT leadership by providing the necessary resources and support to ensure that the organization has access to the best market research tools and technologies to stay up-to-date with customer needs.
Lack of a Digital Transformation Strategy
The lack of a digital transformation strategy is another significant challenge that organizations face. Many organizations may have a collection of individual digital projects but lack an overarching strategy that ties them together.
To address this challenge, IT leadership should:
- Develop a clear digital transformation strategy that outlines the organization's goals, objectives, and the steps involved in achieving them
- Ensure that all stakeholders are involved in the planning process
- Develop a roadmap that outlines the steps involved in the digital transformation process
Organizational leadership can support IT leadership by providing the necessary resources and funding to ensure that the digital transformation strategy is properly executed. Additionally, organizational leadership can ensure that the digital transformation strategy aligns with the organization's overall business strategy.
Lack of Proper IT Skills
The lack of proper IT skills is another significant challenge that organizations face during digital transformation. The fast-paced nature of technology means that many employees may not have the necessary skills to keep up with the latest trends.
To address this challenge, IT leadership should:
- Develop a comprehensive training program to upskill employees in the latest technologies and trends
- Hire new talent with the necessary skills to support the organization's digital transformation process
- Provide ongoing support and mentoring to employees to help them improve their skills
Organizational leadership can support IT leadership by providing the necessary resources and funding to ensure that employees have access to the latest training programs and technologies.
Security Concerns
The digital transformation process introduces new security risks that organizations must address. The use of new technologies and processes can create new vulnerabilities that can be exploited by cybercriminals.
To address this challenge, IT leadership should:
- Develop a comprehensive security strategy that outlines the organization's security protocols and processes
- Conduct regular security audits to identify vulnerabilities and address them promptly
- Provide regular training to employees to help them identify and prevent security breaches
Organizational leadership can support IT leadership by providing the necessary resources and funding to ensure that the organization has access to the latest security technologies and processes.
Budget Constraints
Budget constraints can also pose a significant challenge to organizations during digital transformation. Implementing new technologies and processes can be expensive, and many organizations may not have the necessary funding to support the transformation process fully.
To address this challenge, IT leadership should:
- Develop a clear budget plan that outlines the costs involved in the digital transformation process
- Prioritize investments in technologies and processes that will have the most significant impact on the organization's goals and objectives
- Explore alternative funding options, such as grants and loans, to support the digital transformation process
Organizational leadership can support IT leadership by providing the necessary funding to support the digital transformation process. Additionally, organizational leadership can ensure that the digital transformation process aligns with the organization's overall business strategy to maximize the return on investment.
Culture Mindset
Cultural mindset is another significant challenge that organizations face during digital transformation. Many employees may be resistant to change, and it can be challenging to create a culture that supports innovation and experimentation.
To address this challenge, IT leadership should:
- Develop a culture of experimentation that encourages employees to try new ideas and technologies
- Provide incentives for employees who embrace change and contribute to the digital transformation process
- Communicate the benefits of the digital transformation process to employees and involve them in the planning process
Organizational leadership can support IT leadership by promoting a culture of innovation and experimentation. Additionally, organizational leadership can recognize and reward employees who embrace change and contribute to the digital transformation process.
Making the most of what the cloud offers
Cloud technology can provide significant benefits to organizations during digital transformation. However, many organizations may not be fully utilizing the cloud's capabilities, leading to missed opportunities.
To address this challenge, IT leadership should:
- Conduct a comprehensive analysis of the organization's cloud infrastructure and identify areas where the cloud can be leveraged to improve efficiency and effectiveness
- Develop a clear plan for leveraging the cloud's capabilities to support the digital transformation process
- Provide training to employees to ensure that they are comfortable using cloud technologies
Organizational leadership can support IT leadership by providing the necessary resources and funding to support the organization's cloud infrastructure. Additionally, organizational leadership can ensure that the organization's cloud infrastructure aligns with the organization's overall business strategy.
Economic uncertainty
Economic uncertainty can pose a significant challenge to organizations during digital transformation
To address this challenge, IT leadership should:
- Develop a clear understanding of the economic landscape and identify potential risks and opportunities
- Develop contingency plans to address potential economic challenges, such as budget cuts or a decrease in revenue
- Focus on investments that can help the organization become more resilient in the face of economic uncertainty, such as automation or process improvements
Organizational leadership can support IT leadership by providing the necessary resources and funding to support the organization's digital transformation process, even during times of economic uncertainty.
Worker Burnout
The digital transformation process can be a stressful and demanding time for employees, which can lead to burnout.
To address this challenge, IT leadership should:
- Develop a clear understanding of the causes of burnout and take steps to address them, such as reducing workload or providing additional support
- Encourage work-life balance and provide opportunities for employees to recharge and rejuvenate
- Promote a culture of employee wellness and mental health
Organizational leadership can support IT leadership by promoting a culture of employee wellness and mental health. Additionally, organizational leadership can provide the necessary resources and funding to support employee wellness initiatives.
Managing Remote Workers
The shift to remote work during the COVID-19 pandemic has introduced new challenges for organizations during digital transformation. Managing remote workers can be challenging, and it can be difficult to maintain a sense of team cohesion and collaboration.
To address this challenge, IT leadership should:
- Develop clear communication protocols to ensure that remote workers are kept up to date on the organization's digital transformation process
- Provide the necessary tools and technologies to support remote work, such as video conferencing and collaboration software
- Encourage regular virtual team building and social events to maintain a sense of team cohesion
Organizational leadership can support IT leadership by providing the necessary resources and funding to support remote work initiatives. Additionally, organizational leadership can promote a culture of flexibility and adaptability to support remote work during the digital transformation process.
Conclusion
Digital transformation can be a challenging process for organizations, but with the right support and leadership, it can be a significant opportunity for growth and innovation. IT leadership must address these challenges head-on and develop strategies that support the organization's goals and objectives.
Organizational leadership can support IT leadership by providing the necessary resources and funding to support the digital transformation process. Additionally, organizational leadership can promote a culture of innovation and experimentation to support the organization's digital transformation goals.
In summary, the biggest challenges that organizations face during digital transformation include a lack of change management strategy, complex software, and technology, driving adoption of new tools and processes, a continuous evolution of customer needs, lack of a digital transformation strategy, lack of proper IT skills, security concerns, budget constraints, culture mindset, making the most of what the cloud offers, economic uncertainty, the need to grow smartly, making remote work rewarding, rising costs, worker burnout, managing remote workers, the uneven workflow of an IT team, low productivity, high turnover among specialists, and the gap between IT and business departments.
To address these challenges, IT leadership should develop clear strategies and plans that address each challenge. Organizational leadership can support IT leadership by providing the necessary resources and funding to support the digital transformation process. Additionally, organizational leadership can promote a culture of innovation, experimentation, and employee wellness to support the organization's digital transformation goals.
Digital transformation can be a significant opportunity for organizations to innovate and grow, but it requires a clear vision, leadership, and support. By addressing the challenges of digital transformation head-on and developing a clear strategy, organizations can position themselves for success in the digital age.
Understanding Chat GPT: Advantages, Growth Prospects, and Ethical Checks
Chat GPT is a powerful language model that is transforming the way we interact with technology. This article discusses its advantages, growth prospects, and ethical considerations.
ChatGPT is a large language model trained by OpenAI to communicate with humans in natural language. It is based on the Generative Pre-trained Transformer (GPT) architecture, which uses deep learning techniques to generate text that resembles natural language. ChatGPT can answer a wide range of questions, provide advice, and engage in conversations on a variety of topics. It is designed to continuously learn from its interactions with humans and improve over time.
ChatGPT is used for a wide range of applications that involve natural language processing, including:
- Customer support: ChatGPT can be used to provide automated customer support services, answering frequently asked questions and resolving common issues.
- Personal assistants: ChatGPT can act as a personal assistant, helping users schedule appointments, set reminders, and answer general questions.
- Language translation: ChatGPT can be used to translate text from one language to another, providing a convenient and accessible tool for language learners and travelers.
- Content generation: ChatGPT can be used to generate content such as news articles, product descriptions, and social media posts, freeing up human writers to focus on more creative tasks.
- Education: ChatGPT can be used in educational settings to provide personalized learning experiences and answer student questions.
ChatGPT's flexibility and ability to generate natural-sounding responses make it a valuable tool in a variety of applications where natural language processing is required.
ChatGPT and Google differ in terms of the services they offer and how they process language.
Google is a search engine that provides information in response to user queries, whereas ChatGPT is an AI model designed to generate natural language responses to a wide range of inputs, including questions, statements, and prompts.
Google uses a combination of keyword-based search and machine learning algorithms to provide relevant results to user queries. In contrast, ChatGPT uses deep learning techniques to generate natural-sounding text that resembles human language.
Additionally, while Google can provide factual answers to specific questions, ChatGPT can engage in more conversational exchanges and provide more personalized responses.
While both ChatGPT and Google use natural language processing techniques, they have different purposes and approaches and can be used in complementary ways to provide a range of services to users.
Can chat GPT replace Google
ChatGPT and Google serve different purposes and have different strengths and limitations, so it's unlikely that ChatGPT will completely replace Google.
Google is a search engine that provides access to a vast repository of information on the web, while ChatGPT is an AI language model designed to generate natural language responses to a wide range of inputs. While ChatGPT can be used to answer questions and provide information, it doesn't have the same level of access to information as Google.
Moreover, Google's search algorithms are highly optimized and provide highly accurate and relevant results to user queries, while ChatGPT's responses can be more variable in quality, depending on the input it receives and the context in which it's used.
While ChatGPT and Google can be used in complementary ways to provide a range of services to users, it's unlikely that ChatGPT will completely replace Google anytime soon.
Advantages and disadvantages:
Advantages of ChatGPT:
- Natural language processing: ChatGPT can understand and generate natural language, making it easy for users to communicate with it conversationally.
- Flexibility: ChatGPT can be trained on a wide range of tasks and can be customized to fit specific use cases, making it a versatile tool for a variety of applications.
- Continuous learning: ChatGPT can learn from its interactions with users, improving its responses and becoming more accurate over time.
- Accessible: ChatGPT can be accessed through a variety of platforms, including chatbots and virtual assistants, making it widely available to users.
Disadvantages of ChatGPT:
- Limited understanding of context: ChatGPT may have difficulty understanding the context of a conversation or input, leading to inaccurate or irrelevant responses.
- Biases: Like any machine learning model, ChatGPT can develop biases based on the data it's trained on, leading to potentially problematic responses.
- Lack of emotional intelligence: ChatGPT may not be able to pick up on emotional cues or provide emotional support in the way that a human could.
- Language barriers: ChatGPT may have difficulty understanding and generating text in languages other than the ones it's been trained on, limiting its usefulness in multilingual contexts.
While ChatGPT has many advantages, it's important to be aware of its limitations and potential biases and to use it appropriately based on the specific context and use case.
Growth prospects
The growth prospects for Chat GPT are significant and are likely to continue to increase in the coming years. Several factors contribute to this positive outlook:
- Increasing demand for conversational AI: As businesses and individuals seek to automate their interactions with customers, there is a growing demand for conversational AI technologies like Chat GPT that can provide a personalized and responsive experience.
- Advancements in natural language processing: The field of natural language processing is rapidly evolving, with new techniques and technologies being developed to improve the accuracy and efficiency of language models like Chat GPT.
- Expansion into new domains: Chat GPT is being applied in a growing number of domains, including education, healthcare, finance, and e-commerce, expanding its potential user base and use cases.
- Integration with other technologies: Chat GPT is being integrated with other technologies such as virtual and augmented reality, making it possible to create even more immersive and engaging experiences for users.
The growth prospects for Chat GPT are strong, and the technology is likely to continue to evolve and improve in the coming years, creating new opportunities for businesses and individuals alike.
Does Chat GPT evolve?
Yes, Chat GPT can evolve with use cases as it learns from its interactions with users. As an AI language model, Chat GPT uses machine learning algorithms to analyze and understand text inputs and generate natural language responses. It can improve over time as it receives more data and feedback from users.
For example, if Chat GPT is being used for customer support, it can learn from its interactions with customers to provide more accurate and relevant responses to their queries. Similarly, if it's being used as a personal assistant, it can learn from the user's behavior and preferences to provide more personalized and helpful suggestions.
Additionally, Chat GPT can be fine-tuned and customized for specific use cases and domains through a process called "training." During training, the model is fed large amounts of data relevant to the target use case, allowing it to learn more about the specific domain and improve its performance accordingly.
Chat GPT can evolve and improve over time based on its interactions with users and the data it receives, making it a powerful and adaptable tool for a wide range of applications.
As an AI language model, Chat GPT can be programmed with ethical checks to promote responsible and ethical use. Some of the ethical checks that can be implemented in Chat GPT include:
- Bias detection and mitigation: Chat GPT can be programmed to detect and mitigate bias in the data it's trained on, helping to ensure that its responses are fair and unbiased.
- Privacy protection: Chat GPT can be designed to protect user privacy by anonymizing user data and ensuring that user information is only used for its intended purpose.
- Transparency: Chat GPT can be programmed to provide explanations for its responses, helping to ensure that users understand how the model arrived at its conclusions.
- Robustness: Chat GPT can be designed to withstand attacks or attempts to manipulate it, ensuring that its responses are accurate and reliable.
- Respect for human dignity: Chat GPT can be programmed to respect human dignity by avoiding offensive or harmful language and ensuring that its responses are appropriate and respectful.
The ethical checks programmed into Chat GPT can help to ensure that it's used responsibly and ethically, promoting trust and confidence in the technology and its applications.
Yes, many of these ethical checks are currently being incorporated into the development and deployment of Chat GPT and other AI language models. Some examples include:
- Bias detection and mitigation: Researchers and developers are working on methods to detect and mitigate bias in AI language models, such as using diverse training data and evaluating models for fairness and accuracy across different groups.
- Privacy protection: Chat GPT developers are implementing measures to protect user privacy, such as limiting the collection and storage of user data and implementing strong encryption and security protocols.
- Transparency: Chat GPT developers are working on methods to provide explanations for the model's responses, such as using attention mechanisms to highlight which parts of the input text were most influential in generating a particular response.
- Robustness: Developers are working on methods to increase the robustness of Chat GPT and other AI language models, such as using adversarial training to train models to withstand attacks and attempting to generate more diverse and varied training data.
- Respect for human dignity: Chat GPT developers are working on methods to ensure that the language generated by the model is respectful and appropriate, such as using filters to avoid offensive or harmful language and incorporating cultural and social sensitivity into the training data.
While there is still work to be done to ensure that these ethical checks are fully incorporated into Chat GPT and other AI language models, there is growing awareness of the importance of responsible and ethical AI development and deployment, and progress is being made in this area.
Cloud-Based vs On-Premises ERP Implementation: Which is Best for Your Organization?
In this article, we explore the differences between cloud-based and on-premises ERP implementation and discuss the key factors to consider when choosing the right solution for your organization. We cover factors such as cost, scalability, data security, accessibility, and customization, and provide examples of both cloud-based and on-premises ERP solutions. Whether you are a small business or a large enterprise, this article will help you make an informed decision about which ERP implementation approach is best suited for your organization.
In today's digital age, the implementation of an Enterprise Resource Planning (ERP) system has become a necessity for organizations to streamline their business processes and improve overall efficiency. An ERP system integrates various departments within an organization, such as finance, human resources, operations, and logistics, into a single software solution. However, organizations often face a dilemma when it comes to choosing between cloud-based ERP or on-premises ERP implementation.
Cloud-Based ERP Implementation
Cloud-based ERP implementation involves deploying the ERP system on the cloud, which means that the software solution is hosted on remote servers and accessed through the internet. Here are some advantages and disadvantages of cloud-based ERP implementation:
Advantages:
- Lower upfront costs: Since there is no need to invest in expensive hardware and infrastructure, organizations can save money on upfront costs when implementing a cloud-based ERP system.
- Scalability: Cloud-based ERP solutions offer scalability, meaning that organizations can easily scale up or down as per their business needs. This makes it easier for organizations to adapt to changing market conditions and growth.
- Accessibility: Cloud-based ERP solutions can be accessed from anywhere and at any time, as long as there is an internet connection. This makes it easier for remote teams to access the system and collaborate.
- Maintenance and Upgrades: Maintenance and upgrades are the responsibility of the cloud service provider. This means that organizations do not need to worry about maintaining and upgrading the software solution themselves.
Disadvantages:
- Dependence on the Internet: Cloud-based ERP solutions require a stable Internet connection for optimal performance. If the internet connection is slow or unstable, it can impact the system's performance.
- Data Security: With cloud-based ERP solutions, data security is a concern as the data is stored on remote servers. This can make it more vulnerable to security breaches and cyber-attacks.
- Customization: Cloud-based ERP solutions may not offer as much customization as on-premises solutions, which can limit the organization's ability to tailor the system to its specific needs.
On-Premises ERP Implementation
On-premises ERP implementation involves deploying the ERP system on local servers within the organization. Here are some advantages and disadvantages of on-premises ERP implementation:
Advantages:
- Complete control: With on-premises ERP implementation, organizations have complete control over the software solution, including customization and upgrades.
- Data Security: With on-premises ERP implementation, data is stored locally, which can make it more secure and less vulnerable to cyber-attacks.
- No dependence on the Internet: On-premises ERP solutions do not require a stable Internet connection for optimal performance.
Disadvantages:
- Higher upfront costs: On-premises ERP implementation requires the organization to invest in expensive hardware and infrastructure, which can be a significant upfront cost.
- Maintenance and upgrades: Maintenance and upgrades are the responsibility of the organization, which can be time-consuming and costly.
- Scalability: On-premises ERP solutions may not be as scalable as cloud-based solutions, which can make it difficult for organizations to adapt to changing market conditions and growth.
When it comes to choosing between cloud-based and on-premises ERP implementation, there is no one-size-fits-all solution. Both options have their advantages and disadvantages, and the decision should be based on the organization's specific needs and priorities. Organizations that prioritize scalability, accessibility, and lower upfront costs may opt for cloud-based ERP implementation, while those that prioritize complete control and data security may opt for on-premises ERP implementation. Ultimately, the right choice will depend on the organization's budget, resources, and long-term goals.
Factors to Consider when Choosing Between Cloud-Based and On-Premises ERP Implementation
- Cost: Cost is an essential factor to consider when choosing between cloud-based and on-premises ERP implementation. Cloud-based solutions typically have lower upfront costs as the organization does not need to invest in expensive hardware and infrastructure. On the other hand, on-premises solutions require the organization to invest in servers, networking equipment, and other hardware, which can be a significant upfront cost. However, the long-term costs of both solutions may differ based on maintenance, upgrades, and other factors.
- Scalability: Scalability is another critical factor to consider when choosing between cloud-based and on-premises ERP implementation. Cloud-based ERP solutions are typically more scalable than on-premises solutions as they can be easily scaled up or down as per the organization's business needs. This makes it easier for organizations to adapt to changing market conditions and growth. On-premises solutions may not be as scalable and may require significant investment in hardware and infrastructure to scale up.
- Data Security: Data security is a crucial factor to consider when choosing between cloud-based and on-premises ERP implementation. Cloud-based solutions store data on remote servers, making them more vulnerable to security breaches and cyber-attacks. On the other hand, on-premises solutions store data locally, making it more secure and less vulnerable to cyber attacks.
- Accessibility: Accessibility is another factor to consider when choosing between cloud-based and on-premises ERP implementation. Cloud-based solutions can be accessed from anywhere and at any time, as long as there is an internet connection. This makes it easier for remote teams to access the system and collaborate. On-premises solutions require access to the local network, which may not be possible for remote teams.
- Customization: Customization is another factor to consider when choosing between cloud-based and on-premises ERP implementation. On-premises solutions offer more customization options than cloud-based solutions, allowing organizations to tailor the system to their specific needs. Cloud-based solutions may have limited customization options, which can limit the organization's ability to tailor the system to its specific needs.
In conclusion, both cloud-based and on-premises ERP implementation have their advantages and disadvantages, and the decision should be based on the organization's specific needs and priorities. Organizations that prioritize accessibility, scalability, and lower upfront costs may opt for cloud-based ERP implementation, while those that prioritize complete control, data security, and customization may opt for on-premises ERP implementation. Ultimately, the right choice will depend on the organization's budget, resources, and long-term goals.
Examples of Cloud-Based and On-Premises ERP Solutions
There are several cloud-based and on-premises ERP solutions available in the market. Here are a few examples:
Cloud-Based ERP Solutions:
- NetSuite: NetSuite is a cloud-based ERP solution that offers a suite of applications for financials, customer relationship management, e-commerce, and more. It is designed for mid-sized businesses and can be easily scaled up or down as per the organization's needs.
- Microsoft Dynamics 365: Microsoft Dynamics 365 is a cloud-based ERP solution that offers a suite of applications for finance, sales, customer service, and more. It integrates with Microsoft Office 365 and can be accessed from anywhere and at any time.
- SAP Business ByDesign: SAP Business ByDesign is a cloud-based ERP solution that offers a suite of applications for finance, sales, supply chain management, and more. It is designed for small and mid-sized businesses and can be easily customized to meet the organization's specific needs.
On-Premises ERP Solutions:
- Oracle E-Business Suite: Oracle E-Business Suite is an on-premises ERP solution that offers a suite of applications for finance, procurement, human resources, and more. It is designed for large enterprises and offers extensive customization options.
- SAP ERP: SAP ERP is an on-premises ERP solution that offers a suite of applications for finance, sales, procurement, and more. It is designed for large enterprises and offers extensive customization options.
- Microsoft Dynamics GP: Microsoft Dynamics GP is an on-premises ERP solution that offers a suite of applications for finance, inventory, sales, and more. It is designed for small and mid-sized businesses and offers extensive customization options.
Choosing between cloud-based and on-premises ERP implementation can be a challenging decision for any organization. While cloud-based solutions offer lower upfront costs, scalability, and accessibility, on-premises solutions offer complete control, data security, and customization. Ultimately, the decision should be based on the organization's specific needs and priorities, and the right solution will depend on the organization's budget, resources, and long-term goals. It is essential to carefully evaluate the options available and choose the solution that best meets the organization's requirements.
