Cataloguing Strategic Innovations and Publications
The Impact of Generative AI on Healthcare: A Prescription for Transformation
In the rapidly advancing realm of healthcare, Generative Artificial Intelligence (AI) stands as a beacon of transformation, promising to reshape the very essence of medical practice. This blog delves into the profound impact of Generative AI on healthcare, exploring its effective implementation, advantages, associated risks, mitigation strategies, and the pivotal role doctors play in this AI-driven revolution.
In the ever-evolving landscape of healthcare, technological advancements have the potential to reshape the way we approach diagnosis, treatment, and patient care. One such advancement, Generative Artificial Intelligence (Generative AI), holds the promise of revolutionizing the industry.
Generative AI, a rapidly evolving technology, holds immense promise in revolutionizing the healthcare and medical fields. Its applications are wide-ranging, and they span from research and diagnosis to treatment and patient care. Let's delve into how generative AI can impact the healthcare and medicine sector, considering its potential role in improving various aspects of the industry.
1. Medical Image Analysis: Generative AI can assist in the analysis of medical images such as X-rays, MRIs, and CT scans. Detecting anomalies, lesions, or tumors with high accuracy, helps radiologists in making more precise diagnoses. AI models can also generate synthetic images to expand datasets, which is particularly useful when real data is limited or challenging to obtain.
2. Drug Discovery and Development: AI-driven generative models can accelerate drug discovery processes by predicting potential drug candidates, simulating molecular interactions, and even optimizing drug compounds. This can significantly reduce the time and cost required to bring new medications to market.
3. Electronic Health Records (EHR) Management: In healthcare, the efficient management and analysis of Electronic Health Records are crucial. Generative AI can assist in extracting valuable insights from unstructured EHR data, making it easier to monitor patient histories, predict disease trends, and provide personalized treatment plans.
4. Natural Language Processing (NLP): Generative AI in the form of NLP can transcribe and analyze doctor-patient interactions, helping physicians maintain accurate records and ensuring the efficient exchange of medical information. It can also be used for automated medical coding and billing.
5. Patient Diagnosis and Risk Prediction: By analyzing patient data, including medical history, genetic information, and lifestyle factors, AI models can generate predictions related to disease risk. This enables early intervention and preventive healthcare measures.
6. Personalized Treatment Plans: Generative AI can develop personalized treatment plans for patients by considering their unique genetic makeup and medical history. These tailored recommendations can improve treatment outcomes and minimize adverse effects.
7. Medical Education: AI-powered educational platforms can generate realistic medical case simulations, enabling students and healthcare professionals to practice diagnosis and treatment in a risk-free environment.
8. Natural Language Generation (NLG): Generative AI can help in producing informative and customized patient reports and documentation, aiding in effective communication among healthcare providers and patients.
9. Telemedicine and Remote Monitoring: Generative AI can enhance telemedicine by providing remote monitoring of patients, offering automated reminders, and generating insights for healthcare providers, especially in cases of chronic diseases.
10. Mental Health Support: AI-driven chatbots and virtual mental health assistants can generate empathetic responses to patients, offering a source of support and assistance for individuals facing mental health challenges.
Generative AI has the potential to transform healthcare and medicine by improving diagnostics, drug discovery, patient care, and the overall efficiency of the healthcare system. It empowers healthcare professionals with valuable insights and tools to provide more personalized and effective treatments. However, it is important to address issues related to data privacy, security, and regulatory compliance as AI continues to integrate into the healthcare ecosystem.
The Potential
Generative AI, a subset of artificial intelligence, excels at generating human-like text, images, and other data. In the healthcare sector, it has far-reaching applications:
- Improved Diagnostics: Generative AI can assist doctors in the interpretation of medical images, such as X-rays and MRIs, by identifying anomalies with high precision.
- Drug Discovery: It accelerates drug development by predicting potential drug candidates, simulating molecular interactions, and optimizing drug compounds.
- Personalized Treatment Plans: Generative AI tailors treatment recommendations based on an individual's unique medical history and genetic makeup.
- Data Analysis: It can process vast amounts of patient data, extract valuable insights, and support clinical decision-making.
- Patient Education: AI-generated content can help patients better understand their conditions and treatment options.
Generative AI has the potential to be a valuable tool for doctors across various medical specialties. Its applications can assist healthcare professionals in improving patient care, diagnosis, treatment, and medical research. Here are some ways in which doctors can effectively use generative AI:
- Medical Imaging Analysis: Generative AI can assist radiologists and pathologists in interpreting medical images, such as X-rays, MRIs, CT scans, and histopathology slides. It can help detect abnormalities, lesions, or tumors with high accuracy, providing more precise diagnoses. Moreover, AI-generated synthetic images can expand datasets, improving diagnostic accuracy.
- Drug Discovery and Development: Doctors and medical researchers can use generative AI to accelerate drug discovery and development processes. AI models can predict potential drug candidates, simulate molecular interactions, and optimize drug compounds, thereby reducing the time and cost of bringing new medications to market.
- Clinical Decision Support: Generative AI can assist doctors in making clinical decisions by providing data-driven insights based on patient records, medical literature, and the latest research. It can help suggest treatment options and predict potential outcomes for individual patients.
- Personalized Treatment Plans: Doctors can use generative AI to create personalized treatment plans for patients. By considering a patient's unique medical history, genetic makeup, and lifestyle factors, AI can recommend tailored approaches to treatment, improving patient outcomes.
- Natural Language Processing (NLP): NLP-driven generative models can transcribe and analyze doctor-patient interactions, making it easier to maintain accurate patient records, extract valuable information, and facilitate efficient communication between healthcare providers.
- Medical Research and Literature Review: Generative AI can help doctors stay up to date with the latest medical research. It can generate summaries and insights from vast amounts of medical literature, saving time and ensuring that physicians have access to the most current information.
- Medical Education and Training: Medical schools and training programs can use generative AI to create realistic medical case simulations, virtual patients, and interactive learning modules. This enhances the education and training of medical professionals, allowing them to practice diagnosis and treatment in a controlled environment.
- Patient Communication and Education: Doctors can use generative AI for patient communication and education. AI-driven chatbots or virtual assistants can generate patient-friendly explanations of medical conditions, treatment options, and post-treatment care instructions.
- Telemedicine and Remote Monitoring: In the growing field of telemedicine, generative AI can assist doctors in remote patient monitoring. It can generate automated alerts and insights, enabling healthcare providers to remotely track patient progress and intervene when necessary.
- Mental Health Support: Doctors in mental health fields can use AI-driven chatbots and virtual mental health assistants to provide patients with empathetic and immediate support. These AI tools can generate responses that encourage communication and provide helpful resources.
Incorporating generative AI into medical practice requires careful consideration of ethical, privacy, and regulatory issues. Furthermore, healthcare professionals should be trained to effectively use these tools and interpret AI-generated recommendations to make informed clinical decisions. When used responsibly and in conjunction with human expertise, generative AI has the potential to enhance medical practice and improve patient outcomes.
Effective Implementation in Healthcare
For healthcare providers to harness the full potential of Generative AI, effective implementation is key. Here's how:
- Data Integration: Healthcare systems must ensure that patient data is securely and efficiently integrated into AI models to enable accurate diagnoses and treatment plans.
- Interdisciplinary Collaboration: Encourage collaboration between medical professionals, data scientists, and AI experts to develop tailored AI solutions that meet the unique needs of healthcare settings.
- Regulatory Compliance: Stay up-to-date with healthcare regulations and data privacy laws. Complying with HIPAA and GDPR is paramount when handling patient data.
- Ongoing Training: Medical professionals need training to effectively use AI tools and interpret AI-generated recommendations. This ensures that AI complements human expertise rather than replacing it.
Advantages
The integration of Generative AI offers several significant advantages:
- Precision Diagnostics: AI can analyze medical images and patient data with remarkable precision, reducing the likelihood of misdiagnosis.
- Efficient Drug Development: AI expedites drug discovery, potentially bringing life-saving medications to market faster.
- Personalized Care: Patients benefit from tailored treatment plans that consider their unique genetic makeup and medical history.
- Enhanced Productivity: AI tools can streamline administrative tasks, freeing up medical professionals to focus more on patient care.
Risks and Strategies for Mitigation
While the potential benefits of Generative AI are clear, it's crucial to address the associated risks:
- Data Privacy and Security: The storage and use of sensitive patient data require robust security measures. Encryption, access controls, and regular security audits are essential.
- Bias and Fairness: AI models can inherit biases from training data. Regular auditing and retraining can help mitigate bias and ensure fairness in AI-generated decisions.
- Accountability: Establish clear lines of accountability for AI-generated recommendations. Medical professionals should always make the final clinical decisions.
Changes Required from Doctors
To effectively integrate Generative AI into their workstreams, doctors need to embrace the following changes:
- Continuous Learning: Doctors should be open to ongoing training and upskilling to maximize the use of AI tools.
- Collaboration: Working collaboratively with AI experts and data scientists is vital to harness the full potential of Generative AI.
- Ethical Decision-Making: Doctors must retain their ethical responsibility to make final patient care decisions, even when supported by AI.
Generative AI has the potential to be a game-changer in healthcare. To realize its benefits, effective implementation, addressing risks, and a willingness to adapt is crucial. As AI continues to evolve, doctors need to embrace this transformative technology as a powerful ally in their mission to provide better healthcare and improved patient outcomes. With the right approach, Generative AI can lead to a brighter and healthier future for all.
Generative AI is increasingly being integrated into various healthcare products and applications, revolutionizing the industry. Here are some products and applications that use generative AI in healthcare:
- PathAI: PathAI uses generative AI to assist pathologists in diagnosing diseases from medical images, including cancer detection and classification.
- Zebra Medical Vision: Zebra Medical Vision employs AI algorithms for the analysis of medical imaging data, such as X-rays and CT scans, to detect various diseases.
- IBM Watson for Healthcare: IBM Watson offers AI-powered solutions for healthcare, including AI chatbots for patient engagement and AI image analysis for radiology.
- Caption Health: This AI-driven product aids healthcare professionals by providing guidance and quality assessment during medical ultrasound imaging.
- Tempus: Tempus uses generative AI for genomic sequencing and clinical data analysis to help doctors make more informed decisions in cancer care.
- PathAI: PathAI employs AI for pathology diagnoses, improving accuracy and efficiency in the interpretation of pathology slides.
- Babylon Health: Babylon Health offers an AI chatbot for patient symptom analysis, triage, and virtual consultations with doctors.
- DreaMed Diabetes: DreaMed Diabetes utilizes AI for personalized insulin recommendations for people with diabetes, optimizing blood sugar management.
- **Google Health: Google Health is involved in various healthcare AI projects, including medical image analysis, predictive analytics, and EHR management.
- Nanox: Nanox is working on an AI-driven digital X-ray system to make medical imaging more accessible and affordable.
- Butterfly Network: Butterfly Network produces handheld, AI-enabled ultrasound devices that provide high-quality imaging for various medical applications.
- Nuance Healthcare Solutions: Nuance's AI-driven solutions help with medical transcription, clinical documentation, and radiology reporting.
These are just a few examples of products and applications that harness generative AI to improve healthcare outcomes, diagnostics, and patient care. As the field of AI in healthcare continues to advance, we can expect more innovative products to emerge, enhancing the quality and efficiency of medical services.
Generative AI is poised to usher in a new era of healthcare, with benefits ranging from precise diagnostics to personalized treatments. However, the path forward requires a careful balance between innovation and ethics, emphasizing data security and fair decision-making. Doctors are at the forefront of this transformation, blending human expertise with AI support to improve patient outcomes.
Implementation of Smart Shopping Carts for Large Retail Chain

In the ever-evolving retail landscape, the implementation of smart shopping carts represents a transformative approach to enhance the shopping experience for customers and streamline store operations. This concept note outlines the framework for implementing a solution similar to Amazon's Smart Carts for a large retail chain, with a focus on technological innovation, customer experience, and operational efficiency.
Objectives:
· To leverage cutting-edge technology to enhance the customer shopping experience.
· To streamline store operations, reduce checkout times, and improve inventory management.
· To gather and analyze data for improved customer insights and personalized marketing.
· To remain competitive in the retail market and set new industry standards.
Key Components:
Smart Carts:
· Develop or acquire smart shopping carts equipped with cameras, sensors, and computer vision technology for item recognition.
· Implement weight sensors to track items added or removed.
· Incorporate a user-friendly touchscreen interface for customer interaction.
Connectivity and Data Management:
· Ensure wireless connectivity for real-time updates and communication with store databases.
· Develop robust back-end systems for data collection, storage, and analysis.
· Implement data security measures to protect customer information.
Staff Training and Integration:
· Train store personnel in handling and maintaining smart carts.
· Integrate smart carts into existing store operations and processes.
Customer-Facing Features:
· Provide in-cart navigation assistance for item location.
· Offer personalized recommendations and promotions based on customer preferences.
· Automate the checkout process, linking to customer accounts for seamless billing.
Implementation Steps:
Pilot Program:
· Begin with a pilot program in select store locations to test the technology, receive customer feedback, and make necessary adjustments.
Cart Deployment:
· Gradually deploy smart shopping carts to additional stores based on the pilot's success.
Customer Training:
· Offer in-store training sessions and clear instructions for customers on how to use smart carts effectively.
Data Collection and Analysis:
· Collect and analyze customer data to gain insights into shopping behavior, preferences, and trends.
Continuous Improvement:
· Continuously update and enhance the technology based on customer feedback and emerging innovations.
Financial Implications:
· Estimate the initial investment for smart cart development, training, and back-end systems.
· Assess long-term financial implications and the expected return on investment.
Customer Relationship Management (CRM):
· Leverage data from smart carts for personalized marketing, product recommendations, and customer loyalty programs.
Impact on Business:
· Assess the impact on operational efficiency, customer satisfaction, and financial performance.
· Measure the success of the smart cart implementation through key performance indicators (KPIs).
The implementation of smart shopping carts offers an opportunity for a large retail chain to redefine the shopping experience, improve operational efficiency, and stay competitive in a rapidly changing industry. By focusing on technology, data insights, and customer-centric features, the retail chain can set new standards and enhance its position in the market.
Next Steps:
· Develop a detailed project plan with timelines, responsibilities, and resource allocation.
· Secure necessary resources and partnerships for technology development and deployment.
· Launch the pilot program and collect feedback to fine-tune the implementation strategy.
By embracing innovation and investing in smart shopping carts, the large retail chain can revolutionize the retail shopping experience and remain at the forefront of the industry.
The implementation of smart shopping carts in a retail chain involves several cutting-edge technologies. Here's a list of key technologies required, along with brief explanations of how they work:
- Computer Vision Technology:
- Explanation: Computer vision technology allows smart carts to recognize and identify items placed in the cart. It works by analyzing images or video data from onboard cameras to identify products, quantities, and even product conditions.
- Sensors (Weight, RFID, etc.):
- Explanation: Various sensors are embedded in the smart carts to detect item additions, removals, and tampering. Weight sensors, for instance, help track the changing weight of items, while RFID tags can be used for more precise item tracking.
- Wireless Connectivity (Wi-Fi, Cellular):
- Explanation: Smart carts need wireless connectivity to stay connected to the store's database and the customer's account. This enables real-time updates and automatic checkout, ensuring that the cart always reflects the most up-to-date information.
- Machine Learning and Artificial Intelligence (AI):
- Explanation: Machine learning and AI algorithms are used to improve item recognition over time. These algorithms continually learn from the data they collect, becoming more accurate at identifying products and ensuring correct billing.
- Geolocation Technology:
- Explanation: Geolocation technology helps customers navigate the store efficiently. It can provide a map of the store, pinpoint the customer's location, and offer directions to items on the shopping list.
- Touchscreen Interface:
- Explanation: Smart carts are equipped with user-friendly touchscreen interfaces. Customers interact with the cart through this interface, accessing their shopping list, item information, and navigation assistance.
- Data Analytics and Back-End Systems:
- Explanation: Data analytics and back-end systems collect and process data generated by smart carts. These systems are responsible for storing and analyzing data related to customer behavior, popular products, and store traffic patterns. They provide valuable insights for optimizing inventory management and the shopping experience.
- Security Measures:
- Explanation: Security features, such as weight sensors and anti-tampering mechanisms, are implemented to prevent theft and tampering of items and the cart itself. These measures protect the integrity of the shopping process.
- Battery and Power Management:
- Explanation: Smart carts require efficient battery and power management systems to ensure the cart functions throughout a shopping session. These systems are responsible for maintaining the cart's power supply and ensuring it lasts for an average shopping trip.
- Navigation and Wayfinding Technology:
- Explanation: Navigation and wayfinding technology provides customers with maps and directions to help them efficiently find items within the store. It combines data from sensors, geolocation, and store layouts to guide customers.
- Data Security and Privacy Measures:
- Explanation: As smart carts collect and transmit customer data, robust data security and privacy measures are essential to protect sensitive information. Encryption and access controls help safeguard customer data.
- Communication Protocols:
- Explanation: These protocols enable communication between smart carts and the store's database, as well as with other systems within the store. Communication protocols ensure that data is transmitted securely and efficiently.
- In-Store Infrastructure:
- Explanation: Smart carts rely on the store's infrastructure, including Wi-Fi networks, sensors, and communication equipment, to function properly. The store's physical layout and technology infrastructure play a crucial role in supporting these smart cart systems.
Implementing these technologies in smart shopping carts requires careful planning, integration, and testing to create a seamless and efficient shopping experience for customers while optimizing store operations. These technologies are at the heart of the transformation of retail into a more convenient, data-driven, and customer-centric industry.
The implementation of a smart shopping cart solution for a retail chain involves various products and components. Here is a list of products and their explanations:
- Smart Shopping Carts:
- Explanation: Smart shopping carts are equipped with advanced technology, including cameras, sensors, a touchscreen interface, and connectivity features. These carts serve as the core element of the solution, offering item recognition, navigation assistance, and automated checkout.
- Computer Vision Software:
- Explanation: Computer vision software is responsible for recognizing and identifying items placed in the smart cart. It uses image and video analysis to identify products, quantities, and product conditions.
- Sensor Components:
- Explanation: These components include weight sensors, RFID readers, and other sensor types. Weight sensors detect changes in the cart's weight as items are added or removed. RFID readers enable precise item tracking when RFID tags are used.
- Wireless Connectivity Devices:
- Explanation: Wireless connectivity devices, such as Wi-Fi modules or cellular modems, ensure the smart carts can communicate with the store's database and customer accounts in real-time, enabling automatic updates and checkout.
- Machine Learning and AI Algorithms:
- Explanation: Machine learning and AI algorithms are implemented to improve item recognition over time. These algorithms continuously analyze data from the smart carts, learning to identify products accurately and optimize the shopping experience.
- Geolocation Technology Components:
- Explanation: Geolocation technology components include GPS modules and software. They enable the smart carts to provide in-store navigation and wayfinding, helping customers locate items efficiently.
- Touchscreen Interface Components:
- Explanation: These components include touchscreen displays and associated software. They offer a user-friendly interface for customers to interact with the smart cart, access their shopping lists, and receive item information.
- Data Analytics and Back-End Systems Software:
- Explanation: Data analytics and back-end systems software are responsible for collecting, processing, and storing data generated by the smart carts. It provides insights into customer behavior and helps optimize store operations.
- Security Features:
- Explanation: Security features include anti-tampering mechanisms, security sensors, and encryption components. They protect the Smart Cart from theft or tampering and secure customer data.
- Battery and Power Management Components:
- Explanation: These components include batteries, power management circuits, and charging systems. They ensure the smart carts have a reliable power source and can function for an entire shopping trip.
- Navigation and Wayfinding Software:
- Explanation: Navigation and wayfinding software combines data from sensors, geolocation, and store layouts to provide customers with maps and directions to locate items efficiently.
- Data Security and Privacy Measures Software:
- Explanation: This software implements data security and privacy measures, such as encryption and access controls, to protect customer data.
- Communication Protocol Components:
- Explanation: These components establish communication between the smart carts and the store's database, as well as other systems within the store, ensuring secure and efficient data transmission.
- In-Store Infrastructure Components:
- Explanation: These components include the necessary infrastructure within the store, such as Wi-Fi networks, sensors, and communication equipment, to support the functionality of smart carts.
These products and components work together to create a seamless and efficient shopping experience for customers while optimizing store operations and providing valuable data insights for the retail chain. The successful integration of these products is essential for the smart shopping cart solution to function effectively and enhance the overall retail experience.
Revolutionizing Grocery Shopping: Amazon Fresh's Smart Carts

In the ever-evolving landscape of retail, Amazon Fresh has once again redefined the way we shop for groceries. The introduction of smart shopping carts in Amazon Fresh stores has taken convenience and efficiency to a whole new level. In this blog post, we'll dive into how these carts operate, the advanced technologies behind them, the intricacies of their back-end systems, their contribution to Customer Relationship Management (CRM), and the significant impact they have on Amazon Fresh's business.
In the fast-paced world of retail, Amazon Fresh has once again pushed the boundaries of innovation. Step into the future of grocery shopping as we explore the remarkable journey of Amazon Fresh's smart shopping carts. These technological marvels are transforming the way we fill our grocery baskets, offering a unique blend of convenience and efficiency. From their operational intricacies to the groundbreaking technologies they employ, these smart carts are changing the game. Join us as we uncover the impact they're making on both customers and the business itself.
Amazon Fresh is a grocery delivery and pickup service offered by Amazon. It allows customers to order fresh groceries, including produce, dairy, meat, and other household items, and have them delivered to their doorstep or prepared for pickup at a designated location. Amazon Fresh has played a significant role in the e-commerce giant's expansion into the grocery market, providing customers with the convenience of online grocery shopping.
Amazon Fresh operations involve a complex logistical network, including specialized warehouses and delivery routes to ensure the timely delivery of perishable goods. The service often includes features like same-day or next-day delivery, giving customers a quick and convenient way to access fresh produce and everyday essentials.
Amazon's acquisition of Whole Foods Market in 2017 also contributed to the enhancement of its grocery operations, allowing Amazon Fresh to offer a wider range of organic and high-quality products.
This blend of technological innovation, extensive product offerings, and reliable logistics has made Amazon Fresh a significant player in the grocery delivery space. As Amazon continually evolves its services, Amazon Fresh is likely to remain a prominent aspect of its operations, aiming to meet the ever-growing demand for convenient and efficient grocery shopping.
Smart carts are a remarkable innovation utilized at Amazon Fresh stores, designed to enhance the shopping experience for customers. These high-tech shopping carts incorporate a range of features and cutting-edge technology, providing a seamless and efficient grocery shopping experience. Let's delve into the intricacies of these smart carts:
- Automated Checkout: One of the standout features of smart carts is their ability to enable automated checkout. Customers can link their Amazon accounts to the cart when they enter the store. As they add items to their cart, sensors and cameras within the cart keep track of the items. This eliminates the need to stand in traditional checkout lines, as the cart automatically tallies the bill, and the payment is processed through the customer's Amazon account upon exiting the store.
- Sensors and Cameras: Smart carts are equipped with a variety of sensors and cameras that can identify items as they are placed into the cart. These sensors help in keeping an accurate tally of the items in the cart and ensure that the customer is charged correctly.
- Weight Sensors: The carts have built-in weight sensors to detect when items are added or removed, ensuring that the cart always has an up-to-date list of the items inside.
- Item Location Assistance: Customers can also use the smart cart to locate items within the store. The cart's display screen can show a map of the store and guide the customer to the exact location of the items on their shopping list.
- Customizable Lists: Customers can create and edit their shopping lists on the cart's interface. The cart can then guide them to each item on their list in the most efficient order.
- Ergonomic Design: Amazon has paid attention to the design and ergonomics of these smart carts, ensuring they are easy to maneuver and use within the store.
- Security Measures: To prevent theft and ensure the integrity of the automated checkout process, the smart carts are equipped with security features, such as weight sensors to detect any tampering.
- Sustainability: Some smart carts are designed with sustainability in mind, featuring built-in bags or compartments for groceries, reducing the need for disposable bags.
- User-Friendly Interface: The interface of the cart is user-friendly and easy to navigate, making it accessible to a wide range of shoppers.
- Customer Insights: Amazon can gather valuable data about shopping preferences, habits, and trends through smart cart technology, helping them optimize inventory and enhance the overall shopping experience.
Smart carts at Amazon Fresh stores represent a paradigm shift in the way we shop for groceries. They not only streamline the shopping process but also offer a glimpse into the future of retail, where technology and automation work together to make our lives more convenient. These carts are a prime example of how technology is transforming the retail industry and providing customers with an innovative and efficient shopping experience.
How Do Amazon Fresh's Smart Carts Work?
Smart carts at Amazon Fresh stores incorporate a range of cutting-edge technologies to enable their advanced features and functionalities. These technologies work together to provide an efficient and convenient shopping experience. Here are some of the key technologies used in these smart shopping carts:
- Computer Vision: Smart carts are equipped with cameras and computer vision technology. These cameras can identify items as they are placed in the cart. Computer vision helps in recognizing products, quantities, and even potential issues like damaged items.
- Sensors: Weight sensors are embedded in the cart's shelves and bottom to detect when items are added or removed. This ensures the cart maintains an accurate tally of the items inside.
- RFID (Radio-Frequency Identification): Some smart carts use RFID technology to tag products. This allows for even more precise tracking of items and helps with inventory management.
- Touchscreen Interface: Smart carts feature a user-friendly touchscreen interface. Shoppers can interact with the cart, view their shopping list, access product information, and even request assistance or additional information.
- Wireless Connectivity: Carts are equipped with wireless connectivity (such as Wi-Fi or cellular) to stay connected to the store's database and the customer's Amazon account. This enables real-time updates and automatic checkout.
- Machine Learning and AI: Machine learning algorithms are used to improve item recognition and tracking. Over time, these systems can become more accurate at identifying products and ensuring correct billing.
- Geolocation: Carts may use geolocation technology to help customers locate items within the store. The cart's display can show a store map and provide directions to the desired product.
- Payment Processing: Integrated payment processing technology allows customers to make a seamless payment through their linked Amazon accounts. This technology ensures that customers are accurately charged for the items in their cart.
- Navigation and Wayfinding: Smart carts can guide customers through the store to efficiently find all the items on their shopping list. This is achieved through a combination of sensors and geolocation data.
- Security Features: To prevent theft or tampering, smart carts are equipped with security features such as weight sensors and anti-tampering mechanisms.
- Data Analytics: Amazon can collect and analyze data from these smart carts to gain insights into customer behavior, popular products, and store traffic patterns. This data is valuable for optimizing the shopping experience and inventory management.
- Battery and Power Management: To ensure the cart functions throughout a shopping trip, it needs efficient battery and power management systems. Carts are designed to have sufficient power to last a typical shopping session.
- Self-Driving and Autonomous Features: Some smart carts may include self-driving or autonomous capabilities to follow the shopper around the store or return to a designated location after use.
These technologies work in concert to create a sophisticated and seamless shopping experience for customers at Amazon Fresh stores. The integration of computer vision, sensors, connectivity, and automation has the potential to revolutionize the grocery shopping process and make it more efficient and convenient.
Smart shopping carts used at Amazon Fresh stores operate through a combination of advanced technologies and intricate processes to provide a seamless and efficient shopping experience. Here is a step-by-step explanation of how these carts work:
- Customer Setup:
- Customers start by setting up their smart cart experience. They typically need to link their Amazon account with the cart, either through a mobile app or directly on the cart's interface.
- Item Selection:
- As customers shop, they place items in the cart as they would with a traditional cart. The cart is equipped with cameras, sensors, and computer vision technology.
- Item Recognition:
- The cameras and sensors within the cart identify and track the items placed in it. Computer vision technology plays a crucial role in recognizing products, quantities, and even potential issues like damaged items. This information is constantly updated in real-time.
- Shopping List Assistance:
- The cart's touchscreen interface displays the customer's shopping list and helps guide them to the location of each item within the store. It may also offer additional information about products, including pricing and nutritional details.
- Navigation and Wayfinding:
- The cart can assist customers in navigating the store efficiently. It uses geolocation technology to provide a map of the store and directions to items on the shopping list. This minimizes the time and effort required to find specific products.
- Automatic Checkout:
- As customers continue to shop and add items to their cart, the cart keeps an accurate tally of the items, their prices, and quantities. There is no need for traditional checkout lines. Payment processing is automatic, and the customer's Amazon account is charged accordingly when they exit the store.
- Real-time Updates:
- The cart maintains a constant connection to the store's database and the customer's Amazon account via wireless connectivity. This ensures that the cart always reflects the most up-to-date information on the shopping list and billing.
- Security Measures:
- The cart is equipped with security features to prevent theft and tampering. Weight sensors help detect any unusual activity within the cart, and anti-tampering mechanisms ensure the integrity of the shopping process.
- Data Collection and Analysis:
- Amazon collects and analyzes data from these smart carts, including customer behavior, popular products, and store traffic patterns. This data helps optimize the shopping experience and store operations.
- Exit and Payment:
- After customers have completed their shopping, they exit the store, and the cart's automated checkout system calculates the total bill based on the items in the cart. Payment is processed through the customer's Amazon account.
- Post-Transaction:
- The customer receives a digital receipt and a record of their purchase in their Amazon account. The cart can then be returned to a designated area or, in some cases, may even have self-driving or autonomous capabilities to follow the customer.
Smart Shopping Carts at Amazon Fresh stores streamline the shopping process by automating item recognition, navigation, and checkout. They leverage technologies like computer vision, sensors, geolocation, and wireless connectivity to enhance the shopping experience and offer a glimpse into the future of retail, where technology and automation work together to provide customers with a more convenient and efficient way to shop for groceries.
Smart shopping carts at Amazon Fresh stores are designed to simplify the grocery shopping experience. Here's how they operate:
1. Customer Setup: Shoppers begin by linking their Amazon accounts to the smart cart when they enter the store. This step initiates a seamless shopping journey.
2. Item Selection: As customers shop, they place items in the cart as they normally would in a traditional cart. What sets these carts apart is the integration of advanced technology.
3. Item Recognition: Equipped with cameras, sensors, and computer vision technology, the cart automatically recognizes the items placed inside it. This real-time recognition includes product types, quantities, and even the condition of items.
4. Shopping List Assistance: The cart's touchscreen interface displays the customer's shopping list, making it easy for shoppers to locate and track the items they need within the store.
5. Navigation and Wayfinding: The smart cart assists customers in finding items efficiently by providing a map of the store and directions to the products on their shopping list.
6. Automatic Checkout: An automated checkout process eliminates the need for traditional checkout lines. As customers continue to shop, the cart calculates the bill based on the items inside, ensuring an accurate and stress-free checkout experience.
7. Real-time Updates: The cart maintains a constant connection to the store's database and the customer's Amazon account via wireless connectivity. This ensures that the cart always reflects the most up-to-date information on the shopping list and billing.
8. Security Measures: The cart is equipped with security features like weight sensors to prevent theft and tampering, ensuring the integrity of the shopping process.
9. Data Collection and Analysis: Amazon Fresh collects valuable data from these smart carts, offering insights into customer behavior, popular products, and store traffic patterns, all of which are crucial for optimizing the shopping experience and store operations.
10. Exit and Payment: After completing their shopping, customers simply exit the store. The cart's automated checkout system calculates the total bill based on the items inside, and payment is processed through the customer's Amazon account.
The Technologies Behind Smart Carts
Smart shopping carts leverage a range of cutting-edge technologies:
- Computer Vision: Cameras and computer vision technology identify and track items.
- Sensors: Weight sensors, RFID, and other sensors detect item additions, removals, and tampering.
- Wireless Connectivity: Carts remain connected to the store's database and customer accounts.
- Machine Learning and AI: Algorithms improve item recognition and tracking over time.
- Geolocation: Carts guide customers with maps and directions.
- Security Features: Anti-tampering mechanisms and security sensors deter theft.
Smart shopping carts offer a range of benefits to both customers and the organization, such as Amazon Fresh. Let's explore how these carts are advantageous to each party:
Benefits for Customers:
- Efficiency and Time Savings: Smart carts significantly reduce the time spent in a store. Customers can quickly locate items on their shopping list, and the automated checkout process eliminates the need to wait in traditional checkout lines. This makes the shopping experience more efficient and time-saving.
- Convenience: Customers can shop for groceries with ease. The cart provides item information, navigation assistance, and automatic payment, minimizing the need to carry heavy baskets or bags and simplifying the entire shopping process.
- Accurate Billing: Smart carts use advanced technology to ensure accurate billing. Customers can trust that they are charged correctly for the items they've selected, reducing concerns about pricing discrepancies.
- Enhanced Shopping Experience: The interactive touchscreen interface offers a more engaging and informative shopping experience. Customers can access product details, and dietary information, and even receive suggestions for related items.
- Reduced Checkout Stress: The elimination of traditional checkout lines reduces checkout-related stress. Customers can simply exit the store, and payment is processed automatically, streamlining the shopping process.
- Personalization: The cart can provide personalized product recommendations based on a customer's shopping history and preferences, making it easier to discover new items.
Benefits for the Organization (Amazon Fresh):
- Operational Efficiency: Smart shopping carts enhance the efficiency of store operations. The automation of checkout and billing processes reduces the need for cashiers and speeds up the shopping process, allowing for a higher customer turnover.
- Data Insights: The technology embedded in smart carts enables the collection of valuable data on customer behavior and product preferences. This data can be analyzed to optimize inventory management, product placement, and store layout.
- Improved Inventory Management: Real-time tracking of items in the cart allows for better inventory management. It can help the organization restock products more efficiently and reduce waste from overstocked items.
- Reduced Shoplifting: Security features like weight sensors and anti-tampering mechanisms can help deter shoplifting and protect against theft, benefiting the organization's bottom line.
- Customer Loyalty: Providing an innovative and convenient shopping experience enhances customer loyalty. Shoppers are more likely to return to stores that offer a hassle-free and efficient shopping experience.
- Cost Savings: Over time, as the technology becomes more widespread, smart shopping carts can reduce the need for traditional cashiers, leading to cost savings for the organization.
- Competitive Advantage: Organizations like Amazon Fresh gain a competitive edge by offering a unique and cutting-edge shopping experience, attracting tech-savvy customers, and positioning themselves as leaders in the grocery retail industry.
Smart Shopping Carts benefit customers by enhancing convenience, efficiency, and the overall shopping experience. For organizations like Amazon Fresh, these carts contribute to operational efficiency, data-driven insights, improved inventory management, and a competitive advantage in the market. It's a win-win scenario, where customers enjoy a more seamless shopping experience, and the organization benefits from increased customer satisfaction and operational optimization.
Back-End Systems
The back-end systems of Amazon Fresh's smart carts manage the vast amount of data generated during each shopping trip. This data includes customer preferences, item recognition, and inventory tracking. It's used to optimize store operations, restocking, and inventory management. Additionally, it helps to ensure that customers have a seamless and convenient shopping experience.
Contribution to CRM
Smart carts play a pivotal role in Customer Relationship Management for Amazon Fresh. The data collected from these carts offers insights into customer behavior, allowing Amazon to personalize offers, recommendations, and promotions. By understanding customer preferences and shopping habits, Amazon Fresh can enhance customer loyalty and satisfaction, which is a key aspect of effective CRM.
Impact on Business
The introduction of smart shopping carts at Amazon Fresh stores has had a profound impact on the business:
- Operational Efficiency: The automation of checkout and billing processes reduces the need for traditional cashiers, leading to cost savings and improved efficiency.
- Data-Driven Insights: Real-time data collection and analysis provide valuable insights that can be used to optimize inventory management, product placement, and store layout.
- Enhanced Customer Experience: Smart carts offer a unique and innovative shopping experience, enhancing customer loyalty and attracting tech-savvy shoppers.
- Competitive Advantage: Amazon Fresh positions itself as a leader in the grocery retail industry by offering cutting-edge technology, setting it apart from traditional grocery stores.
Amazon Fresh's smart shopping carts represent a transformative shift in grocery shopping, combining advanced technology, efficient shopping processes, and data-driven insights to provide a superior experience for customers. This innovation not only benefits consumers but also contributes significantly to the CRM strategy and overall success of Amazon Fresh as a business. As technology continues to evolve, we can expect even more exciting developments in the world of retail.
Amazon Fresh's smart shopping carts and Walmart's store automation initiatives represent two distinct approaches to leveraging technology to improve the retail shopping experience. Here are some key differences between the two:
Amazon Fresh's Smart Shopping Carts:
- Customer-Centric: Amazon Fresh's smart carts primarily focus on enhancing the customer's shopping journey. These carts are designed to offer personalized assistance, item recognition, and a seamless checkout experience.
- Individual Assistance: Each smart cart operates as an individual assistant to the customer, providing navigation, item information, and automatic billing.
- In-Store Navigation: Amazon's smart carts guide customers through the store, offering a map and directions to the items on their shopping list, optimizing the shopping experience.
- Data-Driven Insights: These carts generate valuable data about customer behavior and preferences, which can be used for CRM and store optimization.
- Convenience: The primary goal is to provide convenience and efficiency for the customer, making grocery shopping easier and more enjoyable.
Walmart's Store Automation:
- Store-Wide Automation: Walmart's approach to automation often focuses on store-wide processes and efficiency rather than individual customer experiences.
- Automation Technologies: Walmart has implemented automation technologies like autonomous robots for inventory management, autonomous floor scrubbers, and self-checkout kiosks for faster and more streamlined store operations.
- Operational Efficiency: Walmart's store automation is aimed at optimizing inventory, replenishment, and overall store management. This helps reduce operational costs and enhance inventory accuracy.
- Labor Optimization: While customer experience is still important, Walmart's approach places a stronger emphasis on optimizing labor costs and processes throughout the store.
- Multi-Purpose Technology: Walmart's automation often serves multiple purposes, such as inventory tracking and cleanliness maintenance, in addition to customer checkout.
- Inventory Management: Automation in Walmart stores focuses on accurate inventory management, reducing out-of-stock instances, and ensuring products are available to customers.
Amazon Fresh's smart shopping carts are designed to provide a unique and individualized customer experience, while Walmart's store automation initiatives concentrate on optimizing store-wide operations and inventory management. Both approaches represent significant advancements in the retail industry, but they differ in their primary goals and areas of focus. Amazon Fresh prioritizes the customer's shopping experience, while Walmart prioritizes operational efficiency and cost savings.
As the retail landscape continues to evolve, Amazon Fresh's smart shopping carts are at the forefront of the transformation. These high-tech companions have redefined grocery shopping, offering customers unmatched convenience and efficiency. With advanced technology, data-driven insights, and a commitment to an exceptional customer experience, Amazon Fresh is not just changing the way we shop but setting new standards for the industry. The financial implications of these smart carts are undoubtedly significant, but they represent a strategic investment in the future of retail.
The implementation of smart shopping carts in a retail environment, like Amazon Fresh, carries several financial implications. While these implications may vary depending on the scale and complexity of the deployment, here are some key financial considerations:
- Upfront Investment: The initial cost of developing, testing, and deploying the technology can be substantial. This includes the cost of designing and manufacturing the smart carts, developing the software and interface, and installing the necessary infrastructure within the store. This upfront investment can be significant.
- Maintenance and Support: Ongoing maintenance and support costs are necessary to ensure the smart carts continue to function smoothly. This includes software updates, hardware maintenance, and customer support.
- Training and Integration: Employees and customers may require training to use the smart carts effectively. This training can involve additional expenses, including the cost of developing training materials and conducting training sessions.
- Data Management: Collecting and managing the data generated by smart carts can be costly. This data needs to be stored, processed, and analyzed for insights, which may require investment in data infrastructure and analytics tools.
- Security Measures: Implementing and maintaining security measures to prevent theft, tampering, and data breaches is essential. This may involve additional costs for security technology and personnel.
- Operational Changes: Smart carts can lead to changes in store operations, such as reduced reliance on traditional cashiers. This may result in a reallocation of labor and operational costs.
- Customer Experience Enhancement: While the goal is to enhance the customer experience, there may be costs associated with providing a seamless and engaging shopping experience through smart carts. This can include the development of user-friendly interfaces, providing navigation assistance, and improving the overall shopping environment.
- Competitive Advantage: The financial implications can also include the cost of maintaining a competitive advantage. Offering innovative technology like smart shopping carts can be a strategic move, but it requires continued investment to stay ahead of the competition.
- ROI and Revenue Generation: Ultimately, the financial implications need to be balanced against the expected return on investment (ROI) and revenue generation. The deployment of smart carts can increase store traffic, enhance customer loyalty, and lead to higher sales, which can offset the initial costs over time.
- Scalability: As the business grows and additional stores implement smart carts, there will be scaling costs. This includes duplicating the technology infrastructure, investing in more carts, and expanding the associated support and maintenance.
It's important to note that while the initial financial implications can be significant, they are often viewed as long-term investments that have the potential to bring various benefits, including improved customer satisfaction, operational efficiency, and data-driven decision-making. Organizations like Amazon Fresh are likely to conduct thorough cost-benefit analyses to assess the financial viability of implementing smart carts and to determine the long-term impact on their bottom line.
Scrum: The Agile Framework Transforming Project Management
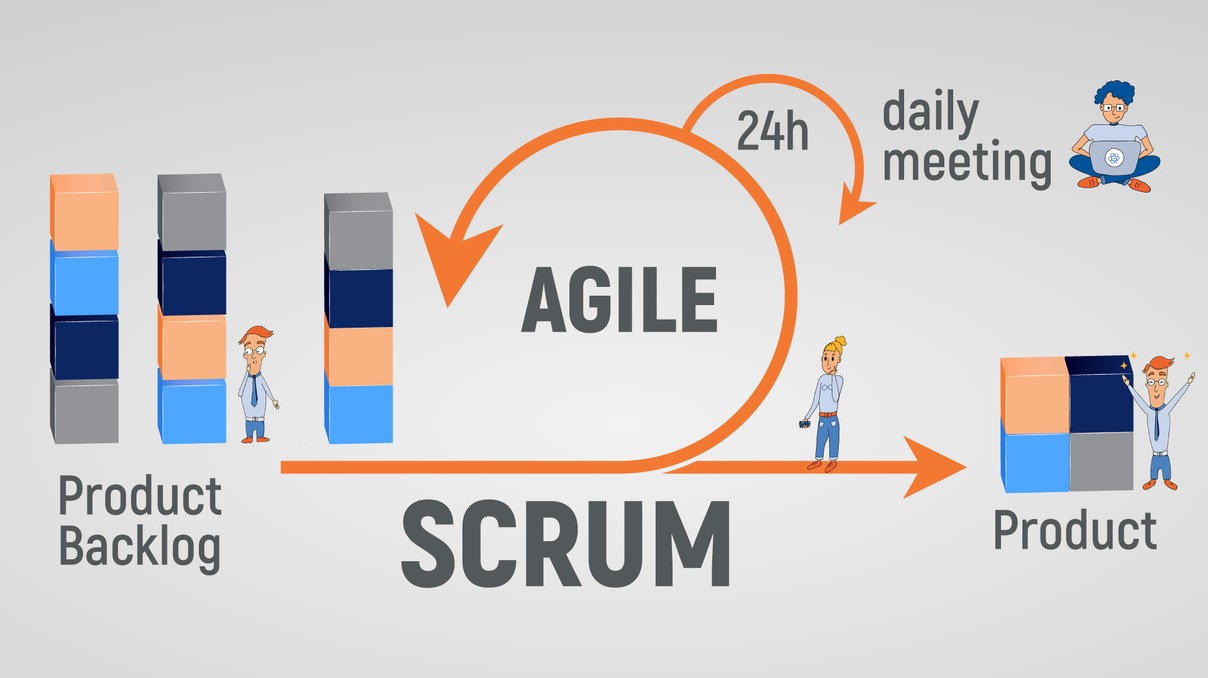
In a world where change is the only constant, businesses and organizations need agile project management frameworks to stay competitive. Scrum, originally designed for software development, has evolved into a versatile methodology with applications across diverse industries. In this comprehensive guide, we dive into Scrum's principles, its wide-ranging applications, the pros and cons, strategies to mitigate challenges, its fascinating history, its current state, and what the future holds.
The Power of Scrum: Agile Project Management for Success
In today's rapidly evolving business landscape, the need for agile project management methodologies has never been greater. Scrum, a framework born from the world of software development, has emerged as a game-changer, finding applications across industries. In this blog post, we'll explore what Scrum is, its applications, advantages, disadvantages, how to mitigate its shortcomings, its inception, growth, current state, and what the future holds.
Understanding Scrum
Scrum is an agile project management framework that promotes iterative development, collaboration, and continuous customer feedback. Unlike traditional, rigid project management methods, Scrum is designed to adapt to change and deliver value incrementally. It consists of three key roles: the Product Owner, responsible for prioritizing the work; the Scrum Master, who ensures the team adheres to Scrum principles; and the Development Team, responsible for delivering the product incrementally.
Applications of Scrum
Scrum's versatility extends far beyond its software development origins. It can be applied to various domains, including software, product development, marketing, healthcare, and more. Scrum's adaptability makes it a valuable tool for managing complex projects, fostering collaboration, and delivering value to customers.
Advantages of Scrum
Scrum offers a host of advantages, such as adaptability to changing requirements, customer-centricity, transparency, improved quality, and faster time to market. It promotes teamwork, empowers teams to self-organize, and reduces the risk of project failure. Continuous feedback loops and regular reflection drive continuous improvement.
Disadvantages of Scrum
However, Scrum isn't without its challenges. It can have a steep learning curve, lead to scope creep, and create pressure to meet Sprint goals. Distributed teams, resistance to change, and incomplete product increments can also pose difficulties.
Mitigating Scrum's Disadvantages
To address these challenges, organizations should invest in Scrum training, clarify roles and responsibilities, strike a balance between short-term goals and long-term vision, and maintain a sustainable pace of work. Creating a culture that embraces agility and open communication is key.
Inception and Growth
Scrum was coined by Jeff Sutherland and Ken Schwaber in the early 1990s, drawing inspiration from rugby scrums' teamwork and unity. It began as a software development framework but quickly gained traction in other industries. Today, Scrum is widely adopted, with numerous certifications and a global community of practitioners.
The Current State of Scrum
Scrum has become a cornerstone of agile project management. It has evolved with various adaptations and practices like "Scrum at Scale" for larger projects and "Nexus" for scaling Scrum. Scrum's principles remain relevant, fostering innovation and adaptability in organizations worldwide.
The Future of Scrum
As the business landscape continues to evolve, Scrum will likely play an even more significant role. With digital transformation accelerating, the need for agile frameworks like Scrum will increase. Organizations will continue to refine and tailor Scrum to suit their specific needs, making it a staple in their quest for agility and excellence.
In conclusion, Scrum is a powerful agile framework that has transcended its origins in software development to become a versatile tool for managing complexity and delivering value in various industries. While it has its challenges, its advantages far outweigh the disadvantages, especially when organizations invest in training and cultivate an agile mindset. As we look to the future, Scrum will remain a vital asset in the pursuit of success in an ever-changing world.
As we conclude our exploration of Scrum, it's evident that this agile framework is a force to be reckoned with. Its adaptability, customer-centric approach, and emphasis on collaboration make it a game-changer in project management. While it comes with challenges, these can be effectively mitigated through proper training and a commitment to an agile mindset. The history of Scrum is remarkable, and its current widespread adoption speaks to its enduring relevance. Looking ahead, Scrum is poised to remain a vital asset in the ever-evolving business landscape.
Scrum is an agile project management framework, and the term "Scrum" itself doesn't stand for any specific acronym. Instead, it derives its name from the sport of rugby. In rugby, a "scrum" is a formation in which players from both teams come together in a tight formation to restart the game after a minor rule infringement or stoppage.
Similarly, in the context of project management, Scrum represents a collaborative and iterative approach where cross-functional teams work closely together in short, time-boxed cycles (Sprints) to deliver valuable increments of a product. The term "Scrum" was coined by Jeff Sutherland and Ken Schwaber, the co-creators of the framework, who drew inspiration from the concept of a rugby scrum's teamwork and unity.
While Scrum itself doesn't have an acronym, some related terms and roles within Scrum have abbreviations, such as:
- Sprint: A time-boxed development cycle in Scrum.
- PO: Abbreviation for "Product Owner," a key role in Scrum responsible for prioritizing the Product Backlog.
- SM: Abbreviation for "Scrum Master," another critical role in Scrum responsible for facilitating and coaching the Scrum team.
- DT: Abbreviation for "Development Team," the group of professionals responsible for delivering the product increment during each Sprint.
But the term "Scrum" itself is not an acronym; it's a name chosen for its connotations of teamwork and collaboration, which are core principles of the framework.
Scrum is a widely recognized and popular framework for agile project management, primarily used in software development but applicable to various other fields. It provides a structured and iterative approach to product development, emphasizing collaboration, adaptability, and customer-centricity. Scrum is characterized by its unique roles, events, and artifacts, which work together to enhance productivity and deliver value to stakeholders.
In a Scrum framework, there are several key elements:
- Roles:
- Product Owner: This individual represents the interests of the customer and is responsible for defining and prioritizing the product backlog, which is the list of features and requirements for the project.
- Scrum Master: The Scrum Master acts as a facilitator and coach for the Scrum team, ensuring that Scrum practices are followed and any impediments to progress are removed.
- Development Team: A self-organizing group of professionals responsible for delivering the potentially shippable product increment during each sprint.
- Events:
- Sprint: The core unit of time in Scrum, typically lasting 2-4 weeks. During a sprint, the development team works to deliver a potentially shippable product increment.
- Sprint Planning: A meeting at the beginning of each sprint where the team decides what work they will commit to completing during that sprint.
- Daily Scrum: A brief daily meeting where team members synchronize their work and plan for the day.
- Sprint Review: A meeting at the end of a sprint where the team demonstrates the work completed and receives feedback from stakeholders.
- Sprint Retrospective: A meeting at the end of a sprint where the team reflects on their processes and identifies areas for improvement.
- Artifacts:
- Product Backlog: A prioritized list of features, user stories, and requirements that represent the product's roadmap.
- Sprint Backlog: A subset of items from the product backlog that the team commits to completing during the sprint.
- Increment: The sum of all the product backlog items completed during a sprint, potentially shippable to stakeholders.
Scrum promotes transparency, inspection, and adaptation, allowing teams to respond to changing requirements and customer feedback efficiently. It encourages collaboration between cross-functional team members and promotes a focus on delivering value incrementally and iteratively. This approach is particularly beneficial in environments where the scope of work is not entirely known upfront and needs to evolve.
In summary, Scrum is a powerful framework that fosters teamwork, flexibility, and customer satisfaction, making it a valuable methodology for modern project management. Its principles and practices can be adapted to various industries and projects, making it a versatile and effective approach to achieving project goals.
Scrum operates on a simple yet effective set of principles and practices to manage complex projects. Here's a detailed explanation of how Scrum works:
- Product Backlog:
- The process starts with the creation of a Product Backlog, which is essentially a prioritized list of all the features, user stories, and requirements that need to be addressed in the project.
- The Product Owner is responsible for maintaining and continuously refining this backlog. They prioritize items based on business value, customer needs, and other relevant factors.
- Sprint Planning:
- At the beginning of each Sprint, which is a time-boxed period (usually 2-4 weeks), the Scrum team, including the Product Owner, Scrum Master, and the Development Team, participates in a Sprint Planning meeting.
- During this meeting, the team selects a subset of items from the Product Backlog to work on during the Sprint, based on their capacity and the priority of the items.
- The team then creates a Sprint Backlog, which contains the tasks and activities required to complete the selected items.
- Daily Scrum:
- Throughout the Sprint, the team holds a Daily Scrum meeting, also known as the daily standup. It's a brief, time-boxed meeting (usually 15 minutes) where each team member answers three questions: What did I do yesterday? What will I do today? Are there any impediments blocking my progress?
- The Daily Scrum helps keep the team synchronized and identifies any issues that need to be addressed.
- Sprint Execution:
- The Development Team works on the items in the Sprint Backlog throughout the Sprint.
- They aim to create a potentially shippable product increment by the end of the Sprint, which means that the work done is of high quality and could be delivered to customers if necessary.
- Sprint Review:
- At the end of the Sprint, the team conducts a Sprint Review meeting where they demonstrate the completed work to stakeholders, such as the Product Owner, customers, or end-users.
- This meeting provides an opportunity for feedback and ensures that the product is evolving in the right direction.
- Sprint Retrospective:
- Following the Sprint Review, the team holds a Sprint Retrospective meeting. In this meeting, they reflect on the past Sprint's processes and outcomes.
- The team identifies what went well and what could be improved, to make adjustments to their processes for the next Sprint.
- Repeat:
- The cycle continues with a new Sprint, starting again with the creation of a Sprint Backlog and proceeding through the daily work, Sprint Review, and Sprint Retrospective.
- This iterative approach allows the team to continuously adapt to changing requirements, improve their processes, and deliver value incrementally.
Scrum's key principles include transparency, inspection, and adaptation. It promotes collaboration, self-organization, and a focus on delivering value to customers. By breaking work into time-boxed Sprints and regularly reviewing and adjusting, Scrum helps teams manage complexity, respond to customer feedback, and deliver valuable products more effectively.
Scrum is a dynamic and adaptable framework that encourages teamwork, customer satisfaction, and the continuous improvement of both the product and the development process. It provides a structured yet flexible approach to managing projects in a complex and uncertain environment.
Scrum offers several advantages that make it a popular and effective framework for project management, especially in industries like software development. These advantages include:
- Adaptability: Scrum is highly adaptable to changing requirements and priorities. The short, time-boxed Sprints allow teams to regularly reevaluate and adjust their work, ensuring that they stay aligned with evolving business needs.
- Customer-Centric: Scrum places a strong emphasis on delivering value to customers. The Product Owner represents customer interests and ensures that the highest-priority features are developed first, resulting in a product that better meets customer expectations.
- Transparency: Scrum promotes transparency at all levels of the organization. The Product Backlog, Sprint Backlog, and Sprint Review provide clear visibility into what work is planned, what is in progress, and what has been completed, fostering trust and collaboration.
- Improved Quality: Scrum encourages a focus on producing a potentially shippable product increment at the end of each Sprint. This emphasis on quality leads to better-tested and more reliable software or products.
- Team Empowerment: Scrum teams are self-organizing and cross-functional, which means they have the autonomy to make decisions and manage their work. This empowerment can lead to higher job satisfaction and greater productivity.
- Faster Time to Market: By delivering incremental value in each Sprint, Scrum can accelerate time to market for products and features. This can be a significant competitive advantage, especially in industries where speed matters.
- Risk Mitigation: The regular inspection and adaptation practices in Scrum help identify and address issues early in the project, reducing the likelihood of costly errors or changes later in development.
- Continuous Improvement: The Sprint Retrospective provides a dedicated space for the team to reflect on their processes and make improvements. This commitment to continuous improvement fosters a culture of learning and innovation.
- Predictability: While Scrum acknowledges the unpredictability of complex projects, it does provide a level of predictability within each Sprint. Stakeholders can have a reasonable expectation of what will be delivered in the short term.
- Enhanced Communication: Daily Scrum meetings and regular interactions within the team and with stakeholders improve communication and collaboration, reducing misunderstandings and promoting alignment.
- Reduced Waste: Scrum helps identify and eliminate unnecessary work or features that do not provide value to the customer. This can result in cost savings and more efficient use of resources.
- Increased Customer Satisfaction: By involving customers and stakeholders throughout the development process and delivering valuable increments of the product regularly, Scrum increases the likelihood of meeting or exceeding customer expectations.
- Global Applicability: While initially designed for software development, Scrum's principles and practices have been successfully applied in various industries, from manufacturing to marketing and beyond.
Scrum's advantages stem from its focus on customer value, flexibility, transparency, and the empowerment of teams. It provides a framework that helps organizations navigate the complexities of modern project management, delivering better results and fostering a culture of continuous improvement.
While Scrum offers many advantages, it is essential to be aware of its disadvantages and potential risks to effectively implement the framework and mitigate any challenges. Here are some of the disadvantages and risks associated with Scrum:
1. Learning Curve: Adopting Scrum can be challenging for teams and organizations unfamiliar with its principles and practices. It requires a mindset shift and can take time for everyone to become proficient.
2. Lack of Defined Roles: Some organizations find it difficult to define the roles of the Product Owner and Scrum Master. Without well-defined roles, there can be confusion and overlap of responsibilities.
3. Incomplete Product Vision: Scrum focuses on short-term goals (Sprints), which can sometimes lead to a lack of attention to the long-term product vision. It's essential to strike a balance between delivering immediate value and maintaining a cohesive product roadmap.
4. Overemphasis on Velocity: Teams may become overly focused on velocity (the amount of work completed in a Sprint), leading to burnout or reduced quality as they rush to meet Sprint goals.
5. Scope Creep: While Scrum is designed to handle changing requirements, poor management of the Product Backlog can lead to scope creep. Frequent changes in priorities can disrupt the team's focus.
6. Distributed Teams: Scrum works best with co-located teams, making it challenging for organizations with remote or geographically dispersed teams to fully leverage the framework.
7. Resistance to Change: Some team members or stakeholders may resist the transition to Scrum, particularly if they are accustomed to traditional project management approaches.
8. Overcommitment: Teams may overcommit during Sprint Planning, leading to unrealistic goals and increased pressure to deliver, which can negatively impact morale and quality.
9. Risk of Burnout: The fast-paced nature of Scrum, with its frequent Sprints, can lead to burnout if not managed properly. Teams must maintain a sustainable pace of work.
10. Incomplete Documentation: Scrum emphasizes working software over comprehensive documentation. While this is an advantage in many cases, it can pose a risk if essential documentation is neglected.
11. Lack of Predictability: While Scrum provides predictability within each Sprint, long-term predictability can be challenging, as the scope of work can change frequently based on feedback and priorities.
12. Incomplete Product Increment: In some cases, Sprints may not result in a fully shippable product increment due to dependencies or technical challenges. This can delay the delivery of value to customers.
13. Inadequate Stakeholder Involvement: Scrum relies on close collaboration with stakeholders, and if they are not actively engaged or available, it can impede progress.
14. Cultural Resistance: Shifting to an agile mindset can be met with resistance in organizations with deeply ingrained traditional management cultures.
To mitigate these disadvantages and risks, organizations should invest in proper Scrum training and coaching, establish clear roles and responsibilities, maintain a balance between short-term goals and long-term vision, and continually inspect and adapt their Scrum practices. Additionally, addressing these challenges often requires a cultural shift toward embracing agility and open communication throughout the organization. Scrum is a powerful framework when implemented effectively, but it requires commitment and ongoing effort to realize its full potential.
Mitigating the risks and disadvantages of Scrum involves proactive strategies and a commitment to continuous improvement. Here are specific steps to address common challenges associated with Scrum:
- Learning Curve:
- Mitigation: Invest in comprehensive Scrum training and coaching for all team members. Encourage a culture of continuous learning and knowledge sharing.
- Incomplete Product Vision:
- Mitigation: Ensure the Product Owner maintains a clear product vision and roadmap. Regularly review and update the vision with feedback from stakeholders.
- Scope Creep:
- Mitigation: Carefully manage the Product Backlog. Involve stakeholders in the prioritization process and set clear boundaries for each Sprint.
- Overcommitment:
- Mitigation: Encourage realistic commitments during Sprint Planning. Empower the Development Team to determine their capacity and prioritize work accordingly.
- Resistance to Change:
- Mitigation: Foster a culture of openness to change. Communicate the benefits of Scrum and involve team members in decision-making and process improvements.
- Distributed Teams:
- Mitigation: Leverage collaboration tools and video conferencing to bridge geographical gaps. Emphasize clear communication and alignment with remote team members.
- Inadequate Stakeholder Involvement:
- Mitigation: Educate stakeholders about their role in Scrum. Actively engage them in Sprint Reviews and seek their input regularly.
- Burnout:
- Mitigation: Encourage a sustainable pace of work. Ensure the team adheres to their capacity and avoid overloading them with excessive work.
- Incomplete Product Increment:
- Mitigation: Address technical debt and dependencies as they arise. Encourage the Development Team to prioritize quality to ensure a potentially shippable product increment.
- Cultural Resistance:
- Mitigation: Create a supportive environment for cultural change. Provide leadership and training to help team members and stakeholders embrace agile values and principles.
- Lack of Predictability:
- Mitigation: While embracing change, strive for stability within Sprints. Ensure that the Scrum Team maintains a focus on completing the Sprint goals.
- Inadequate Documentation:
- Mitigation: Balance documentation needs with delivering working software. Use user stories and acceptance criteria as living documentation.
Mitigating these risks and disadvantages is an ongoing process. Regular retrospectives can help the Scrum Team identify areas for improvement and adjust their practices accordingly. Additionally, fostering a culture of collaboration, transparency, and continuous improvement is essential to successfully address and mitigate challenges in Scrum.
Implementing Scrum successfully requires a combination of skills and competencies at various levels within an organization. These skills are crucial for both the Scrum Team (Product Owner, Scrum Master, and Development Team) and stakeholders involved in the Scrum process. Here are the skills required for implementing Scrum effectively:
For the Scrum Team:
- Knowledge of Scrum: All members of the Scrum Team must have a deep understanding of Scrum principles, practices, and roles. This includes understanding the Scrum Guide, which provides the official definition of Scrum.
- Collaboration: Effective collaboration is essential within the Scrum Team. Team members should be skilled at working together, communicating openly, and sharing information to achieve common goals.
- Communication: Strong communication skills are critical for all Scrum Team members, especially the Product Owner and Scrum Master. They must effectively convey ideas, requirements, and progress to the team and stakeholders.
- Adaptability: Scrum is an adaptive framework, and team members need to be open to change and ready to adjust to evolving requirements and priorities.
- Problem-Solving: The ability to identify and solve problems is vital. The Scrum Team must address impediments, obstacles, and challenges that arise during Sprints.
- Empathy: Understanding the perspectives and needs of other team members and stakeholders is crucial for building strong relationships and making informed decisions.
- Technical Skills (Development Team): For members of the Development Team, technical skills relevant to the project, such as programming, design, or testing, are essential to deliver a potentially shippable product increment.
For the Product Owner:
- Product Knowledge: The Product Owner must have a deep understanding of the product, its market, and the needs of the customers and stakeholders.
- Prioritization: Skill in prioritizing features and user stories based on their business value and customer impact is essential. The Product Owner must make informed decisions about what to include in each Sprint.
- Stakeholder Management: The ability to engage with and manage stakeholders effectively, including gathering feedback and managing expectations, is crucial for success.
- Communication: Strong communication skills are necessary for conveying product vision, requirements, and priorities to the Scrum Team and stakeholders.
For the Scrum Master:
- Servant Leadership: A Scrum Master needs to exhibit servant leadership by supporting the team's needs, removing impediments, and facilitating Scrum events without taking a directive role.
- Facilitation: Skill in facilitating Scrum events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, is crucial for keeping the team on track and productive.
- Coaching and Mentoring: The Scrum Master should have the ability to coach and mentor the Scrum Team and the organization in Scrum practices and principles.
- Conflict Resolution: Conflict can arise within the team or with stakeholders. The Scrum Master should be skilled in resolving conflicts and promoting a positive team environment.
- Change Management: Implementing Scrum often involves significant changes in processes and culture. The Scrum Master should be adept at managing change and helping the organization adapt to agile practices.
For Stakeholders:
- Engagement: Stakeholders should actively engage with the Scrum process, attending Sprint Reviews, providing feedback, and collaborating with the Scrum Team to make informed decisions.
- Understanding of Scrum: It's beneficial for stakeholders to have a basic understanding of Scrum principles and practices to ensure they can effectively participate in the process.
- Communication: Clear and effective communication with the Scrum Team is essential to convey expectations and gather information.
- Flexibility: Stakeholders should be open to changes in the product based on feedback and evolving priorities.
Implementing Scrum is a collaborative effort, and each member of the Scrum Team and stakeholders plays a vital role. Developing and honing these skills can contribute to the successful implementation and use of Scrum within an organization.
Scrum is a versatile framework that can be applied to various areas and industries beyond its origins in software development. Its principles of adaptability, collaboration, and customer focus make it suitable for addressing complex problems and delivering value in a wide range of domains. Here are some areas where Scrum can be effectively applied:
- Software Development: Scrum's original domain. It is widely used for building software products and applications, both in startups and large enterprises.
- Product Development: Scrum applies to developing physical products, such as consumer electronics, hardware devices, and industrial equipment.
- Marketing: Scrum can be used in marketing teams for campaign planning, content creation, and digital marketing efforts. It allows teams to be responsive to market changes and customer feedback.
- Sales: Scrum principles can be applied to sales teams to manage leads, track sales opportunities, and optimize the sales process.
- Project Management: Scrum is used in various project management contexts, including construction projects, event planning, and research initiatives.
- Healthcare: Scrum can improve the delivery of healthcare services by enhancing collaboration among healthcare providers, optimizing patient care processes, and managing healthcare IT projects.
- Education: Scrum can be applied in educational institutions to manage curriculum development, student projects, and administrative processes.
- Nonprofit Organizations: Scrum can help nonprofit organizations manage fundraising campaigns, volunteer coordination, and community outreach programs more effectively.
- Manufacturing: Scrum practices can be applied to optimize production processes, reduce waste, and improve quality in manufacturing environments.
- Financial Services: Scrum can be used in financial institutions for project management, product development, and customer service improvement.
- Research and Development: Scrum can enhance innovation and research projects by providing a structured framework for experimentation and iterative development.
- Human Resources: Scrum can be employed to manage HR processes such as recruitment, onboarding, and employee development.
- Content Creation: Media companies, publishing houses, and content creators can use Scrum to manage content creation pipelines and publishing schedules.
- Government: Some government agencies have adopted Scrum to improve the efficiency and transparency of public services and IT projects.
- Agencies and Consultancies: Scrum is used by consulting firms and agencies to manage client projects, marketing campaigns, and software development projects for their clients.
It's important to note that while Scrum's principles can be adapted to various domains, the specific implementation may require adjustments to fit the unique needs and constraints of each area. Scrum's focus on delivering value to customers and stakeholders, fostering collaboration, and embracing change makes it a valuable framework for organizations seeking to improve their agility and responsiveness in today's dynamic business environment.
Demystifying the DMZ: Your Guide to Network Security's Fortified
In today's interconnected world, where cyber threats lurk around every digital corner, the Demilitarized Zone (DMZ) stands as a stalwart defender of network security. Born from military strategy and refined through decades of technological evolution, the DMZ is more relevant than ever. Join us on a journey through its history, growth, current significance, and prospects in this blog post.
The Evolution and Future of DMZ: Enhancing Network Security in a Connected World
In the ever-evolving landscape of cybersecurity, the concept of a Demilitarized Zone (DMZ) has played a pivotal role in safeguarding networks and data from external threats. Originally inspired by military terminology, the DMZ has grown into a fundamental component of modern network architecture. In this blog post, we will explore the evolution, growth, current state, and prospects of the DMZ, shedding light on its enduring relevance in an increasingly interconnected world.
The Origins of the DMZ
The term "Demilitarized Zone" traces its origins to the military, where it refers to an area between two opposing forces—typically seen in armed conflicts or border disputes. In the realm of computer networks, the DMZ was conceived as an architectural solution to emulate this concept in the digital realm. It emerged as a response to the need for a secure buffer zone between the internal network, harboring sensitive data and resources, and the external, untrusted network, often represented by the internet.
The Growth of DMZ in Network Architecture
Early Deployments
Early DMZ implementations were relatively simple and primarily focused on segregating web servers or email servers from the internal network. Firewalls were the primary security measure, controlling traffic flow and enforcing access policies. While rudimentary by today's standards, these early DMZ setups represented a significant leap forward in network security.
Advancements in Security
As cyber threats evolved and became more sophisticated, so did the DMZ. Intrusion detection and prevention systems (IDS/IPS), load balancers, and proxy servers were integrated into DMZ architectures to provide deeper layers of security. This expanded the DMZ's capabilities beyond basic traffic filtering.
Network Segmentation
One of the significant advancements in DMZ architecture was the concept of network segmentation. Organizations began to create multiple DMZs, each tailored to a specific purpose, such as web services, email, and application servers. This allowed for finer-grained access control and more robust security measures.
The Current State of DMZ
Today, DMZs have become a standard component of network design for organizations of all sizes and industries. They offer a vital layer of defense against a wide range of threats, including distributed denial-of-service (DDoS) attacks, malware, and unauthorized access attempts.
Key Features of Modern DMZs
- Comprehensive Security: Modern DMZs combine firewalls, IDS/IPS, load balancers, and other security appliances to provide comprehensive protection.
- High Availability: Redundancy and load balancing ensure that DMZ services remain available, even in the face of hardware failures or heavy traffic loads.
- Regulatory Compliance: DMZs help organizations meet regulatory requirements related to data protection and privacy.
- Incident Response: Well-defined incident response plans are an integral part of DMZ management, enabling rapid mitigation of security incidents.
The Future of DMZ: Adaptation and Integration
The future of DMZ is shaped by the evolving threat landscape and technological advancements. Here are some key trends and areas of development:
Cloud Integration: With the increasing adoption of cloud computing, organizations are integrating DMZ principles into their cloud architectures. This allows for secure access to cloud-hosted resources.
Zero Trust Security: The Zero Trust model challenges the traditional DMZ approach by assuming that threats may exist inside the network. DMZs are adapting to this model by implementing strict access controls and continuous monitoring.
AI and Automation: Artificial intelligence (AI) and automation will play a significant role in DMZ management. AI-driven security analytics can enhance threat detection, while automation can streamline routine tasks.
Containerization: As containerization technologies like Docker and Kubernetes gain prominence, DMZs will need to adapt to secure containerized applications and microservices.
A Demilitarized Zone (DMZ), in the context of computer networking and network security, is a designated area within a network infrastructure that acts as a buffer zone between an organization's internal network and the external, untrusted network, usually the internet. The primary purpose of a DMZ is to enhance network security by segregating different types of network traffic and providing an additional layer of protection for sensitive resources.
In a typical network architecture, the DMZ is strategically positioned between the organization's internal network, which houses critical data and services, and the external network, which is inherently more vulnerable to threats. This setup allows organizations to host certain services that need to be accessible from the internet, such as web servers, email servers, or public-facing applications, in the DMZ while isolating them from the internal network.
The concept of DMZ is like a security checkpoint or buffer zone where traffic is subject to rigorous inspection and filtering before it is allowed to reach the internal network. Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) are commonly employed within the DMZ to monitor and control traffic flow. These security measures help protect the internal network from potential threats originating from the internet.
The Demilitarized Zone, or DMZ, is akin to the guardian sentinel of computer networks, standing as a formidable bulwark between the bastion of an organization's internal data sanctum and the turbulent tides of the internet's vast expanse. In this intricate symphony of network security, the DMZ plays a pivotal role as the conductor, orchestrating the safeguarding of critical resources with both finesse and unwavering vigilance.
Picture the DMZ as a virtual no man's land, a realm where the digital foot soldiers of the internet must undergo stringent scrutiny and evaluation before being granted passage into the inner sanctum of an organization's network. Here, the DMZ deploys an arsenal of cyber sentinels, including firewalls, intrusion detection systems, and intrusion prevention systems, to scrutinize each incoming and outgoing packet of data with the precision of a surgeon's scalpel.
But what, you might wonder, is the raison d'être of this network sentinel? Simply put, it serves as the first line of defense, the guardian at the gate, ensuring that only authorized traffic makes its way into the organization's internal network. While standing sentinel, it also provides a haven for certain services – think web servers, email servers, and public-facing applications – that require internet accessibility without compromising the security of the inner sanctum.
The DMZ is the network's guardian angel, maintaining a delicate balance between accessibility and security, all while keeping the turbulent forces of the internet at bay. It is a testament to the intricate dance of technology and security in our digital age, where the DMZ reigns supreme as the protector of data and the gatekeeper of network integrity.
The creation of a Demilitarized Zone (DMZ) within a computer network is born out of a fundamental need for enhanced network security and control. Its inception is motivated by a variety of critical objectives and concerns that organizations face in the realm of network architecture and cybersecurity. Let's delve into the reasons behind the establishment of a DMZ:
- Security Segmentation: The primary purpose of a DMZ is to segment or compartmentalize different types of network traffic. It provides a distinct zone that separates an organization's internal network, housing sensitive data and resources, from the external, often untrusted, network, typically the Internet. This segmentation is crucial because it helps prevent unauthorized access to the internal network.
- Protection of Critical Resources: Organizations host critical resources and services, such as web servers, email servers, and application servers, that need to be accessible from the internet. Placing these resources in the DMZ shields them from direct exposure to the external network, making it more challenging for cyber adversaries to compromise them.
- Access Control: The DMZ serves as a controlled access point between the external and internal networks. Traffic entering or exiting the DMZ is subjected to rigorous inspection, allowing organizations to apply access control policies and security measures to determine what is permitted and what should be blocked.
- Security Inspection: By deploying security technologies like firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) within the DMZ, organizations can scrutinize network traffic for suspicious or malicious activity. This level of inspection helps identify and mitigate potential threats before they can reach the internal network.
- Minimizing Attack Surface: The DMZ minimizes the attack surface of the internal network. Even if an attacker breaches the DMZ, they still face additional barriers to accessing sensitive data and systems within the organization's core network.
- Compliance and Regulatory Requirements: Many industries and organizations are subject to strict compliance and regulatory requirements regarding data security and privacy. The DMZ facilitates compliance by providing a controlled environment for sensitive data and ensuring that only authorized traffic can reach it.
- Redundancy and Load Balancing: In some cases, organizations use the DMZ for redundancy and load-balancing purposes. Multiple servers or resources in the DMZ can distribute traffic efficiently, ensuring high availability and reliability for services.
- Isolation of Threats: If a security breach occurs within the DMZ, it is contained within that zone and does not automatically grant attackers access to the internal network. This containment mechanism limits the potential damage and lateral movement of threats.
In essence, the creation of a DMZ is a proactive security strategy aimed at fortifying an organization's network infrastructure. It is a strategic decision to bolster cybersecurity by adding layers of defense, access control, and surveillance to safeguard critical assets and data from external threats while still enabling necessary communication with the broader internet.
Creating a Demilitarized Zone (DMZ) within a computer network involves careful planning, network design, and the implementation of various security measures. Below are the key steps and components involved in creating a DMZ:
- Network Design and Topology:
- Begin by designing your network topology. Determine which resources and services need to be accessible from the Internet and which should be isolated in the internal network.
- Decide on the placement of the DMZ. Typically, it is situated between the external network (internet) and the internal network, creating a three-tier network architecture.
- Network Segmentation:
- Segment your network into three zones: the DMZ, the internal network, and the external network (internet).
- Use separate network segments or subnets for each zone to ensure isolation.
- Firewalls:
- Deploy firewalls at the perimeter of the DMZ. These firewalls act as gatekeepers, controlling traffic between the external network, the DMZ, and the internal network.
- Configure firewall rules to permit or deny specific types of traffic, based on policies and security requirements.
- Proxy Servers:
- Implement proxy servers in the DMZ to act as intermediaries between clients on the internet and internal servers. This adds an additional layer of security by masking the internal network structure.
- Security Appliances:
- Install intrusion detection systems (IDS) and intrusion prevention systems (IPS) within the DMZ to monitor network traffic for suspicious or malicious activity. These systems can help detect and block threats in real time.
- Web Servers and Application Gateways:
- Place web servers, email servers, and other public-facing services in the DMZ. These servers should be hardened and regularly patched to mitigate security risks.
- Consider using application gateways (reverse proxies) to further protect web servers by offloading SSL/TLS encryption and inspecting incoming traffic.
- Access Control:
- Implement strict access control policies within the DMZ. Only allow the necessary traffic to flow between the DMZ and the internal network.
- Use strong authentication and authorization mechanisms for accessing resources within the DMZ.
- Logging and Monitoring:
- Set up comprehensive logging and monitoring solutions within the DMZ. This includes logging firewall events, IDS/IPS alerts, and server logs.
- Continuously monitor network traffic and system logs for signs of security incidents.
- Regular Updates and Patch Management:
- Keep all devices and servers within the DMZ up to date with the latest security patches and updates. Vulnerabilities can be exploited if systems are not properly maintained.
- Incident Response Plan:
- Develop an incident response plan specific to the DMZ. Ensure that your IT team is well-prepared to respond to security incidents within the DMZ promptly.
- Testing and Assessment:
- Regularly perform penetration testing and security assessments on the DMZ to identify vulnerabilities and weaknesses.
- Documentation:
- Maintain detailed documentation of your DMZ architecture, firewall rules, access policies, and network diagrams for reference and auditing.
Creating a DMZ is a critical component of network security, and it requires ongoing maintenance and updates to adapt to evolving threats. It's important to work closely with network and security professionals who have expertise in designing and implementing secure network architectures.
A Demilitarized Zone (DMZ) contributes significantly to enhancing network security by creating an added layer of protection and control between an organization's internal network and the external network, typically the Internet. Here's how a DMZ makes a network safer:
- Isolation of Sensitive Resources:
- The DMZ physically and logically isolates sensitive internal resources and servers from the untrusted external network. This isolation prevents direct access to critical assets, such as databases and core servers, from the internet.
- Access Control:
- The DMZ acts as a controlled access point to the internal network. It enforces strict access control policies, allowing only authorized traffic to enter the internal network. Unauthorized or malicious traffic is blocked at the DMZ perimeter.
- Traffic Filtering:
- Firewalls and security appliances in the DMZ filter and inspect incoming and outgoing traffic. They use predefined rules and policies to allow or deny traffic based on its source, destination, type, and content.
- Security Monitoring:
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS) within the DMZ continuously monitor network traffic for suspicious patterns or known attack signatures. They can detect and respond to threats in real time.
- Proxy Servers:
- Proxy servers in the DMZ act as intermediaries between external clients and internal servers. They can cache content, mask internal IP addresses, and filter requests, reducing the exposure of internal assets to potential attackers.
- Redundancy and Load Balancing:
- Some DMZ configurations include redundancy and load balancing for critical services. This ensures high availability and fault tolerance, reducing the risk of service disruptions due to hardware failures or traffic spikes.
- Containment of Threats:
- In the event of a security breach within the DMZ, the impact is contained within that zone. Attackers may compromise resources in the DMZ but face additional barriers when attempting to access the internal network.
- Compliance and Regulatory Adherence:
- By segmenting and securing sensitive data and resources in the DMZ, organizations can more easily adhere to industry-specific compliance and regulatory requirements related to data protection and privacy.
- Minimized Attack Surface:
- The DMZ minimizes the attack surface of the internal network. Even if an attacker gains access to the DMZ, they must overcome additional security measures to reach valuable assets within the organization.
- Logging and Auditing:
- Comprehensive logging and auditing of network activity within the DMZ provide a valuable trail of information for incident response and forensic analysis. It helps organizations track and investigate security incidents.
- Incident Response Preparedness:
- Organizations with a DMZ typically have well-defined incident response plans specific to the DMZ environment. This preparedness ensures that security incidents are addressed promptly and effectively.
In summary, a DMZ fortifies network security by acting as a controlled intermediary zone that filters, monitors, and inspects network traffic. It enforces access controls, provides real-time threat detection and containment, and reduces the exposure of critical assets to the external network. By doing so, it significantly reduces the attack surface and enhances the overall safety and resilience of the network infrastructure.
The establishment of a Demilitarized Zone (DMZ) within a computer network offers several significant advantages for organizations seeking to enhance their network security, flexibility, and resilience. Here are the key advantages of implementing a DMZ:
- Enhanced Network Security:
- Perhaps the most notable advantage of a DMZ is the bolstered network security it provides. By isolating sensitive internal resources from the external, untrusted network (typically the internet), it creates a protective barrier that helps safeguard critical assets from unauthorized access and cyber threats.
- Controlled Access:
- A DMZ acts as a controlled gateway between the internal network and the external network. It enforces strict access control policies, allowing only authorized traffic to pass through. This ensures that malicious or unauthorized traffic is intercepted and blocked at the DMZ perimeter.
- Isolation of Threats:
- In the event of a security breach or compromise within the DMZ, the impact is contained within that zone. Attackers face additional barriers when attempting to access the internal network, minimizing the potential damage and lateral movement of threats.
- Protection of Public-Facing Services:
- Public-facing services such as web servers, email servers, and application servers are hosted within the DMZ. This shields them from direct exposure to the internet while still allowing them to be accessible to external users, reducing the risk of exploitation.
- Network Segmentation:
- The DMZ facilitates network segmentation, separating different types of network traffic into distinct zones. This segmentation enhances network organization and simplifies security management by clearly defining security policies for each zone.
- Granular Traffic Filtering:
- Firewalls and security appliances deployed within the DMZ filter and inspect incoming and outgoing traffic. They can apply granular traffic rules based on criteria such as source, destination, port, and content, thereby preventing unauthorized access and attacks.
- Security Monitoring:
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS) continuously monitor network traffic within the DMZ, promptly identifying and responding to suspicious activity and known threats.
- Redundancy and High Availability:
- Some DMZ configurations include redundancy and load balancing for critical services, ensuring high availability and fault tolerance. This minimizes service disruptions due to hardware failures or traffic spikes.
- Compliance and Regulatory Adherence:
- Organizations can more easily meet industry-specific compliance and regulatory requirements by securing sensitive data and resources in the DMZ. It simplifies the process of demonstrating data protection and privacy compliance.
- Forensic and Incident Response Capabilities:
- Comprehensive logging and auditing of network activity within the DMZ provide valuable data for forensic analysis and incident response. It assists in tracking and investigating security incidents.
- Flexibility and Scalability:
- The DMZ architecture allows organizations to add or modify public-facing services in a controlled manner, offering flexibility and scalability to adapt to changing business needs and technological advancements.
- Risk Reduction:
- By reducing the attack surface of the internal network and implementing robust security measures within the DMZ, organizations significantly reduce the risk of successful cyberattacks and data breaches.
A DMZ is a critical component of network security that provides multiple advantages, including strengthened security, controlled access, isolation of threats, and compliance adherence. It offers organizations the means to balance accessibility and protection, enabling them to effectively manage the risks associated with today's interconnected digital landscape.
While a Demilitarized Zone (DMZ) offers numerous advantages for network security, it is essential to acknowledge the potential disadvantages and risks associated with its implementation. Understanding these drawbacks can help organizations make informed decisions and take appropriate measures to mitigate them. Here are some of the disadvantages and risks of a DMZ:
1. Complexity and Maintenance:
· Disadvantage: Managing a DMZ infrastructure can be complex, requiring expertise in network design, security policies, and regular maintenance.
· Risk: If not properly configured and maintained, the complexity of the DMZ can introduce vulnerabilities and increase the risk of misconfigurations.
2. Cost:
· Disadvantage: Setting up and maintaining a DMZ can involve significant upfront and ongoing costs, including the purchase of hardware, software, security appliances, and staffing for management and monitoring.
· Risk: Budget constraints may lead to compromises in security measures, potentially leaving the network vulnerable to attacks.
3. Single Point of Failure:
· Disadvantage: A single DMZ can become a single point of failure for all external-facing services. If the DMZ experiences an outage or security breach, it can disrupt all public-facing services.
· Risk: Redundancy and failover mechanisms must be carefully implemented to mitigate this risk.
4. Increased Attack Surface:
· Disadvantage: While the DMZ reduces the attack surface of the internal network, it creates a new attack surface itself. Attackers may focus their efforts on finding vulnerabilities within the DMZ infrastructure.
· Risk: Insufficient security measures within the DMZ can lead to successful attacks against public-facing services and compromise sensitive data.
5. False Sense of Security:
· Disadvantage: Organizations may develop a false sense of security with a DMZ in place, assuming that it provides impenetrable protection.
· Risk: Overconfidence can lead to neglecting other security measures, such as patch management and employee training, leaving vulnerabilities unaddressed.
6. Administrative Overhead:
· Disadvantage: Maintaining and managing the DMZ requires ongoing administrative overhead, including the creation and maintenance of firewall rules, access controls, and monitoring.
· Risk: Human error in configuring firewall rules or monitoring systems can introduce vulnerabilities or misconfigurations.
7. Increased Latency:
· Disadvantage: The additional network hops introduced by the DMZ may result in increased latency for external clients accessing services within the DMZ.
· Risk: In scenarios where low-latency access is critical, such as real-time applications, latency introduced by the DMZ may be a concern.
8. Limited Protection for Insider Threats:
· Disadvantage: While the DMZ is effective at protecting against external threats, it may have limited capabilities in mitigating insider threats from within the organization.
· Risk: Insider attacks can bypass the DMZ if carried out by individuals with legitimate access to the internal network.
9. Zero-Day Vulnerabilities:
· Disadvantage: Even with robust security measures, the DMZ is not immune to zero-day vulnerabilities, which are unknown and unpatched.
· Risk: Attackers may exploit zero-day vulnerabilities to bypass security measures and compromise the DMZ.
A DMZ offers significant security benefits, but it also poses challenges and risks related to complexity, cost, potential single points of failure, and the need for ongoing maintenance and vigilance. To maximize the advantages of a DMZ while mitigating these disadvantages and risks, organizations should invest in robust security practices, and regular audits, and stay informed about emerging threats and vulnerabilities.
Mitigating the risks and disadvantages associated with a Demilitarized Zone (DMZ) requires a proactive approach to network security and careful planning. Here are strategies and best practices to help mitigate these risks and disadvantages:
1. Complexity and Maintenance:
· Mitigation: Invest in trained personnel who specialize in network security and DMZ management. Regularly update policies and procedures, and conduct training for staff responsible for DMZ administration.
2. Cost:
· Mitigation: Consider cost-effective alternatives, such as cloud-based DMZ solutions or managed security services, to reduce upfront hardware and staffing costs. Budget for ongoing maintenance and security updates.
3. Single Point of Failure:
· Mitigation: Implement redundancy and failover mechanisms for critical DMZ components, such as load balancers and firewalls. Regularly test failover procedures to ensure they function as expected.
4. Increased Attack Surface:
· Mitigation: Continuously assess and harden the security of DMZ components, applying patches and updates promptly. Conduct regular penetration testing and vulnerability assessments to identify and address weaknesses.
5. False Sense of Security:
· Mitigation: Promote a culture of security awareness within the organization. Emphasize that the DMZ is just one layer of defense and that other security measures, like endpoint protection and employee training, are equally important.
6. Administrative Overhead:
· Mitigation: Implement change management processes for firewall rule changes and configurations. Automate repetitive tasks where possible to reduce the risk of human error.
7. Increased Latency:
· Mitigation: Optimize network and server performance within the DMZ to minimize latency. Consider the use of content delivery networks (CDNs) to cache and distribute content closer to end users.
8. Limited Protection for Insider Threats:
· Mitigation: Implement user and entity behavior analytics (UEBA) solutions to detect unusual or suspicious behavior within the organization. Employ strict access controls and least privilege principles to limit access to sensitive resources.
9. Zero-Day Vulnerabilities:
· Mitigation: Stay informed about emerging threats and vulnerabilities through security advisories and threat intelligence feeds. Implement network intrusion detection and advanced threat protection solutions to detect and mitigate unknown threats.
10. Regular Audits and Assessments: - Mitigation: Conduct regular security audits and assessments of the DMZ infrastructure to identify vulnerabilities and weaknesses. Use the findings to make improvements and updates.
11. Disaster Recovery and Business Continuity: - Mitigation: Develop and test disaster recovery and business continuity plans specific to the DMZ. Ensure that critical data and configurations are backed up and can be quickly restored in case of an incident.
12. Security Patch Management: - Mitigation: Implement a robust patch management process to promptly apply security updates to all DMZ components. Prioritize critical patches to address known vulnerabilities.
13. Security Monitoring and Incident Response: - Mitigation: Implement comprehensive security monitoring within the DMZ and establish an incident response plan specific to this environment. Monitor logs, set up alerts, and train staff to respond to security incidents effectively.
14. Regular Training and Awareness: - Mitigation: Continuously educate employees and IT staff about the importance of security best practices and the role of the DMZ in protecting the organization.
By taking a proactive and holistic approach to DMZ management, organizations can maximize the advantages of a DMZ while mitigating the associated risks and disadvantages. Effective security measures, vigilant monitoring, and regular assessments are key components of a successful DMZ strategy.
Creating a Demilitarized Zone (DMZ) within a network involves the deployment of various network devices and security appliances to enforce access control, monitor traffic, and protect sensitive resources. Here are some of the devices commonly used to create a DMZ:
- Firewalls:
- Firewalls are a fundamental component of a DMZ. They act as gatekeepers between the external network (internet) and the DMZ, as well as between the DMZ and the internal network. Firewalls enforce security policies, filter traffic, and block unauthorized access. Next-generation firewalls (NGFWs) offer advanced features, including intrusion prevention, deep packet inspection, and application-level filtering.
- Proxy Servers:
- Proxy servers serve as intermediaries between external clients and internal servers within the DMZ. They can provide caching, content filtering, and access control. Reverse proxy servers are often used to enhance security by handling SSL/TLS encryption and authentication, thereby protecting internal server details.
- Intrusion Detection Systems (IDS):
- IDS devices are used to monitor network traffic within the DMZ for signs of suspicious activity or known attack signatures. They generate alerts when potential threats are detected, allowing security teams to investigate and respond to incidents.
- Intrusion Prevention Systems (IPS):
- IPS devices build upon the functionality of IDS by not only detecting threats but also taking automated actions to prevent them. They can block malicious traffic, making them a proactive security measure within the DMZ.
- Load Balancers:
- Load balancers distribute incoming traffic across multiple servers within the DMZ to ensure high availability and load distribution. This redundancy helps maintain service availability even in the event of server failures.
- VPN Gateways:
- Virtual Private Network (VPN) gateways are used to securely connect remote users or branch offices to resources within the DMZ. VPNs add an extra layer of encryption and authentication for remote access.
- Web Application Firewalls (WAFs):
- WAFs are specialized security devices that protect web applications from various online threats, including SQL injection, cross-site scripting (XSS), and other application-layer attacks. They are particularly useful for safeguarding web servers in the DMZ.
- Mail Transfer Agents (MTAs):
- Mail servers within the DMZ often use Mail Transfer Agents to handle email traffic. Properly configured MTAs can provide email security and spam filtering.
- DNS Servers:
- DNS servers in the DMZ help manage domain name resolution for external-facing services. They can be configured to provide additional security measures, such as DNS filtering and protection against DNS-based attacks.
- Network Access Control (NAC) Systems:
- NAC systems enforce policies for devices and users connecting to the DMZ. They ensure that only authorized and compliant devices gain access to network resources within the DMZ.
- Logging and Monitoring Systems:
- Devices within the DMZ, including firewalls, IDS/IPS, and servers, should be integrated with centralized logging and monitoring systems. These systems collect and analyze log data to detect anomalies and security incidents.
- Router and Switch Configuration:
- Network routers and switches play a crucial role in connecting and routing traffic between the DMZ, internal network, and external network. Proper configuration of these devices is essential for network segmentation and security.
The specific combination of devices used in a DMZ depends on the organization's security requirements, the types of services hosted in the DMZ, and the desired level of protection. A well-designed DMZ architecture leverages a combination of these devices to create a layered defense that effectively balances security and accessibility.
This is a list of some well-known manufacturers and models for the devices commonly used in creating a Demilitarized Zone (DMZ) within a network. Please note that the availability of specific models may vary by region and over time, so it's essential to research the latest offerings from these manufacturers and select the models that best suit your organization's needs. Here are some examples:
Firewalls:
- Cisco ASA Series (e.g., Cisco ASA 5500-X)
- Palo Alto Networks Next-Generation Firewalls (e.g., Palo Alto PA-220)
- Fortinet FortiGate Firewalls (e.g., FortiGate 60F)
- Check Point Security Gateways (e.g., Check Point 1570R)
- Juniper Networks SRX Series (e.g., Juniper SRX345)
Proxy Servers:
- Squid Proxy Server
- NGINX Proxy
- Apache HTTP Server (can be configured as a reverse proxy)
- Microsoft Forefront Threat Management Gateway (TMG)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS):
- Snort (open-source IDS/IPS)
- Suricata (open-source IDS/IPS)
- Cisco Firepower Next-Generation IPS
- Palo Alto Networks Threat Prevention
- McAfee Network Security Platform
Load Balancers:
- F5 BIG-IP Series (e.g., BIG-IP 2000s)
- Citrix ADC (formerly known as NetScaler)
- Kemp LoadMaster Load Balancers
- HAProxy (open-source load balancer)
VPN Gateways:
- Cisco AnyConnect Secure Mobility Client
- Palo Alto Networks GlobalProtect VPN
- Juniper Networks Pulse Secure VPN
- Fortinet FortiClient VPN
- OpenVPN (open-source VPN)
Web Application Firewalls (WAFs):
- Imperva Incapsula WAF
- Akamai Kona Site Defender
- Fortinet FortiWeb Web Application Firewall
- Barracuda Web Application Firewall
- Cloudflare Web Application Firewall
Mail Transfer Agents (MTAs):
- Microsoft Exchange Server
- Postfix (open-source MTA)
- Sendmail (open-source MTA)
- Exim (open-source MTA)
- SendGrid (cloud-based email delivery service)
DNS Servers:
- BIND (open-source DNS server)
- Microsoft DNS Server
- Infoblox DNS
- Cisco Umbrella (cloud-based DNS and security service)
- BlueCat DNS Integrity
Network Access Control (NAC) Systems:
- Cisco Identity Services Engine (ISE)
- Aruba ClearPass
- Forescout CounterACT
- Pulse Secure Policy Secure (formerly known as Juniper Network Connect)
- Bradford Networks Network Sentry
Logging and Monitoring Systems:
- Splunk
- Elastic Stack (formerly known as ELK Stack)
- SolarWinds Security Event Manager
- IBM QRadar
- LogRhythm
Router and Switch Manufacturers:
- Cisco (e.g., Cisco Catalyst switches)
- Juniper Networks (e.g., Juniper EX Series switches)
- HPE (Hewlett Packard Enterprise) (e.g., HPE ProCurve switches)
- Dell EMC (e.g., Dell EMC PowerSwitch switches)
- Arista Networks (e.g., Arista 7000 Series switches)
Please note that this is not an exhaustive list, and there are many other manufacturers and models available for these device categories. The choice of specific devices should be based on your organization's requirements, budget, and compatibility with your existing network infrastructure. Additionally, consider consulting with IT professionals or network security experts for guidance on selecting the most suitable devices for your DMZ configuration.
Establishing a Demilitarized Zone (DMZ) within a network requires a specific skill set, as it involves network architecture, security, and the configuration of various network devices and services. Below are the key skills and knowledge areas required to successfully set up and maintain a DMZ:
- Network Architecture and Design:
- Understanding of network topologies and architecture principles, including the placement of the DMZ within the network.
- Network Security:
- Knowledge of security concepts, such as access control, encryption, authentication, and threat mitigation.
- Familiarity with security standards and best practices, including those related to firewalls and intrusion detection/prevention systems.
- Firewall Configuration:
- Proficiency in configuring and managing firewall rules, policies, and access controls.
- Understanding of stateful and stateless firewall operation.
- Security Appliances:
- Competence in setting up and configuring security appliances, such as intrusion detection systems (IDS) and intrusion prevention systems (IPS).
- Proxy Server Configuration:
- Experience with configuring proxy servers for content filtering, caching, and load balancing.
- Load Balancing:
- Knowledge of load balancing principles and the ability to configure load balancers for distributing traffic across multiple servers within the DMZ.
- VPN Configuration:
- Skill in setting up and managing Virtual Private Networks (VPNs) to ensure secure remote access to the DMZ.
- Web Application Security:
- Understanding of web application security best practices, including the use of Web Application Firewalls (WAFs) to protect web servers.
- Mail Server Configuration:
- Proficiency in configuring Mail Transfer Agents (MTAs) for secure and reliable email communication.
- DNS Management:
- Knowledge of Domain Name System (DNS) configuration and security to manage DNS servers within the DMZ.
- Network Access Control (NAC):
- Ability to implement NAC solutions to enforce security policies for devices and users accessing the DMZ.
- Logging and Monitoring:
- Skill in setting up comprehensive logging and monitoring systems to track network activity and detect security incidents.
- Incident Response:
- Familiarity with incident response procedures specific to the DMZ and the ability to investigate and mitigate security incidents.
- Security Compliance and Regulations:
- Awareness of industry-specific security compliance requirements and regulations that may apply to the organization's DMZ.
- Scripting and Automation:
- Proficiency in scripting languages (e.g., Python, PowerShell) to automate tasks and streamline configurations.
- Documentation:
- Ability to create detailed documentation, including network diagrams, firewall rulesets, and standard operating procedures for the DMZ.
- Risk Assessment:
- Capability to conduct risk assessments and vulnerability assessments to identify and address potential security weaknesses.
- Continuous Learning:
- Dedicated to staying updated on evolving security threats, technologies, and best practices in the field of network security and DMZ management.
- Communication and Collaboration:
- Strong communication skills to collaborate with cross-functional teams, including IT, security, and compliance departments.
- Problem-Solving Skills:
- The ability to troubleshoot complex network and security issues within the DMZ and implement effective solutions.
Establishing a DMZ is a critical aspect of network security, and having a skilled team with expertise in these areas is essential to ensure the effective implementation and ongoing management of a secure DMZ environment.
Regular monitoring and maintenance are crucial for ensuring the security and optimal performance of a Demilitarized Zone (DMZ) within a network. Here are key tasks and practices for ongoing DMZ monitoring and maintenance:
- Firewall Rule Review:
- Regularly review and update firewall rules in the DMZ to ensure they align with the organization's security policies. Remove unnecessary or outdated rules.
- Security Patch Management:
- Stay current with security patches and updates for all DMZ devices, including firewalls, intrusion detection/prevention systems (IDS/IPS), and servers. Implement patches promptly to address known vulnerabilities.
- Log Monitoring:
- Continuously monitor logs generated by DMZ devices, including firewalls, IDS/IPS, and servers. Look for signs of suspicious activity or security incidents.
- Intrusion Detection/Prevention System (IDS/IPS) Tuning:
- Regularly tune IDS/IPS systems to reduce false positives and improve detection accuracy. Update threat signatures and rules to stay protected against emerging threats.
- Incident Response Drills:
- Conduct periodic incident response drills specific to the DMZ. Ensure that the incident response team is well-prepared to respond to security incidents within this environment.
- Access Control Review:
- Review and audit access controls within the DMZ. Ensure that only authorized users and devices have access to resources in the DMZ.
- Vulnerability Scanning:
- Conduct regular vulnerability scans and assessments within the DMZ to identify and remediate weaknesses in security configurations.
- Load Balancer Health:
- Monitor the health and performance of load balancers within the DMZ. Ensure that traffic is evenly distributed, and failover mechanisms work as expected.
- SSL/TLS Certificate Management:
- Manage SSL/TLS certificates used for securing web services in the DMZ. Monitor certificate expiration dates and renew certificates as needed.
- Web Application Firewall (WAF) Rules Review:
- Review and update WAF rules to protect web applications hosted in the DMZ from new and evolving threats.
- Backup and Restore Testing:
- Regularly test backup and restore procedures for critical DMZ resources, including servers and configurations. Ensure that backups are reliable and can be restored in case of data loss.
- DNS Security:
- Monitor DNS server logs and configurations for security anomalies. Implement DNSSEC (Domain Name System Security Extensions) to protect against DNS-based attacks.
- User and Entity Behavior Analytics (UEBA):
- Implement UEBA solutions to detect unusual or suspicious behavior within the DMZ. Analyze user and entity activity for signs of insider threats.
- Change Management:
- Implement robust change management processes for making configuration changes to DMZ devices. Document changes and review them to avoid misconfigurations.
- Documentation Update:
- Keep documentation up to date, including network diagrams, firewall rulesets, and standard operating procedures for the DMZ.
- Penetration Testing and Security Assessments:
- Conduct periodic penetration testing and security assessments to identify vulnerabilities and weaknesses in the DMZ architecture and configurations.
- Compliance Auditing:
- Regularly audit DMZ configurations and practices to ensure compliance with industry-specific security standards and regulations.
- Employee Training and Awareness:
- Keep IT staff and network administrators updated on the latest security threats and best practices through ongoing training and awareness programs.
- Vendor Notifications:
- Stay informed about security advisories and updates from DMZ device manufacturers and software vendors. Implement patches and mitigations for known vulnerabilities.
- Network Performance Monitoring:
- Monitor the performance of network connections and traffic within the DMZ to detect and address bottlenecks or latency issues.
Regular monitoring and maintenance help maintain the integrity and security of the DMZ, reducing the risk of security incidents and ensuring that the network remains resilient against evolving threats. It's essential to have a well-documented and well-practiced routine for these tasks to keep the DMZ in a secure and reliable state.
A properly configured and maintained Demilitarized Zone (DMZ) can add a significant level of security and robustness to a network. The extent of security and robustness it provides depends on several factors, including the architecture of the DMZ, the effectiveness of security measures implemented, and the organization's commitment to ongoing monitoring and maintenance. Here are ways in which a DMZ enhances network security and robustness:
- Isolation of Sensitive Resources:
- A DMZ physically and logically separates sensitive internal resources from the untrusted external network (typically the internet). This isolation ensures that even if the DMZ is compromised, attackers face additional barriers to accessing critical assets within the internal network.
- Access Control:
- The DMZ enforces strict access control policies, allowing only authorized traffic to enter the internal network. Access rules, firewall configurations, and authentication mechanisms control who can access resources in the DMZ, reducing the attack surface.
- Traffic Filtering:
- Firewalls and security appliances in the DMZ filter and inspect incoming and outgoing traffic. They can block malicious or unauthorized traffic based on predefined rules, mitigating the risk of cyberattacks.
- Intrusion Detection and Prevention:
- Intrusion detection systems (IDS) and intrusion prevention systems (IPS) continuously monitor network traffic within the DMZ. They detect and respond to suspicious activity, providing real-time threat mitigation.
- Protection of Public-Facing Services:
- Public-facing services, such as web servers and email servers, are hosted in the DMZ. This separation protects these services from direct exposure to the internet while allowing external users to access them, reducing the risk of exploitation.
- Redundancy and High Availability:
- Some DMZ configurations include redundancy and load balancing for critical services. This ensures high availability and fault tolerance, reducing the risk of service disruptions due to hardware failures or traffic spikes.
- Containment of Threats:
- In the event of a security breach within the DMZ, the impact is contained within that zone. Attackers may compromise resources in the DMZ but face additional barriers when attempting to access the internal network.
- Incident Response Preparedness:
- Organizations with a DMZ typically have well-defined incident response plans specific to the DMZ environment. This preparedness ensures that security incidents are addressed promptly and effectively.
- Compliance Adherence:
- The DMZ helps organizations adhere to industry-specific compliance and regulatory requirements related to data protection and privacy. It simplifies compliance efforts by isolating and securing sensitive data.
- Logging and Monitoring:
- Comprehensive logging and monitoring within the DMZ provide valuable data for incident detection and investigation. Security teams can identify and respond to threats more effectively.
- Network Segmentation:
- Network segmentation, facilitated by the DMZ, enhances network organization and reduces lateral movement for attackers within the network. This minimizes the scope of potential breaches.
- Regular Updates and Patch Management:
- Keeping all devices and servers within the DMZ up to date with the latest security patches and updates reduces the risk of known vulnerabilities being exploited.
- Forensic Analysis:
- The DMZ architecture enables organizations to perform forensic analysis and trace the source of security incidents within the DMZ.
While a DMZ provides a robust security layer, it's essential to understand that no security measure is entirely foolproof. The effectiveness of a DMZ depends on the continuous effort to monitor and update security measures, train personnel, and adapt to evolving threats. Additionally, other security measures, such as endpoint protection, user training, and strong password policies, complement the security provided by the DMZ to create a comprehensive network security strategy.
The evolution of AI is significantly impacting the effectiveness and management of DMZ (Demilitarized Zone) in network security. Here are several ways in which AI is influencing the DMZ:
- Enhanced Threat Detection:
- AI-powered threat detection systems can analyze network traffic patterns within the DMZ more effectively than traditional rule-based methods. They can identify anomalies, unusual behavior, and emerging threats, thereby enhancing the DMZ's ability to protect against sophisticated attacks.
- Automated Incident Response:
- AI-driven security solutions can automate incident response within the DMZ. When a potential threat is detected, AI can take immediate action, such as blocking malicious traffic or isolating compromised systems, reducing response time and minimizing damage.
- Behavioral Analysis:
- AI algorithms can perform continuous behavioral analysis of network traffic and user activity within the DMZ. This helps in identifying insider threats, unusual user behavior, and zero-day attacks that might bypass traditional security measures.
- Zero Trust Security:
- AI technologies play a pivotal role in implementing the Zero Trust security model, which assumes that threats may exist both outside and inside the network. AI-driven identity verification and continuous monitoring ensure that only trusted entities gain access to DMZ resources.
- Predictive Analytics:
- AI can leverage predictive analytics to anticipate potential security threats and vulnerabilities within the DMZ. By analyzing historical data and identifying trends, AI helps security teams proactively address issues before they escalate.
- User and Entity Behavior Analytics (UEBA):
- UEBA solutions powered by AI can detect abnormal user and entity behavior patterns within the DMZ. This includes identifying unauthorized access attempts, data exfiltration, and compromised accounts.
- Network Traffic Optimization:
- AI can optimize network traffic within the DMZ by dynamically adjusting load balancers and routing traffic to enhance performance. It ensures that resources in the DMZ remain available during traffic spikes or attacks.
- Advanced Threat Protection:
- AI-driven threat intelligence systems can analyze vast amounts of data to identify new and evolving threats. This proactive approach helps in safeguarding DMZ assets against emerging cyber risks.
- Automation of Routine Tasks:
- AI automates routine tasks within the DMZ, such as log analysis, alert prioritization, and incident investigation. This frees up security teams to focus on more strategic and complex security challenges.
- Scalability and Flexibility:
- AI-powered security solutions are highly scalable and adaptable. As the DMZ's needs change, AI can quickly adjust security policies and configurations to accommodate new services and technologies.
Summing up, the evolution of AI is transforming the DMZ from a static security boundary into a dynamic and adaptive defense layer. AI's ability to analyze data at scale, detect threats in real-time, and automate responses strengthens the DMZ's capacity to protect against a wide range of cyber threats in an increasingly complex and interconnected digital landscape.
The Demilitarized Zone (DMZ) has come a long way from its military origins to become an indispensable element of modern network security. Its evolution, growth, and adaptability reflect its enduring relevance in safeguarding networks against ever-evolving cyber threats. As we look to the future, the DMZ will continue to evolve, integrating with emerging technologies and security models to ensure that our digital world remains secure and resilient in the face of evolving challenges.
The Demilitarized Zone (DMZ) isn't just a relic of the past; it's a dynamic and adaptable fortress that safeguards networks against modern cyber threats. As technology continues to evolve, so does the DMZ, integrating with new security models and emerging technologies to ensure our digital world remains secure. In this ever-changing landscape, the DMZ is a steadfast guardian of network security.
#NetworkSecurity #DMZ #Cybersecurity #FutureTech #DataProtection #NetworkArchitecture #ZeroTrust #CloudSecurity #CyberThreats #AIinSecurity
Iron's Resilience and the Unyielding Power of the Human Mindset

“No one can destroy iron, but it's its rust. Likewise, nothing can destroy a person, but his mindset.”
Iron, a symbol of strength and durability, possesses an intriguing quality - it can only be destroyed by its rust. This paradoxical truth serves as a profound metaphor for the human experience. In the journey of life, just as nothing external can annihilate iron but its internal corrosion, so too, can nothing external truly destroy a person. The key lies in the fortress of one's mindset. This article delves into the profound connection between iron's resilience and the indomitable power of the human mindset. It explores how understanding this connection can be a source of inspiration and empowerment for individuals seeking to overcome challenges and achieve their full potential.
Indeed, the analogy drawn between iron and the human mindset is both profound and inspiring. Just as iron, a sturdy and resilient material, can only be corroded by its rust, the human spirit, too, possesses incredible strength and resilience. It is not external forces or circumstances that can truly destroy a person, but rather their mindset.
This statement underscores the immense power of one's thoughts and beliefs. A negative or self-destructive mindset can erode one's confidence, motivation, and ultimately, ability to overcome challenges. Conversely, a positive and resilient mindset can be the foundation upon which individuals build their success and happiness.
It serves as a reminder that self-limiting beliefs, self-doubt, and a defeatist attitude are often the greatest obstacles we face in our journey toward personal growth and achievement. By recognizing that our mindset is the key determinant of our destiny, we are empowered to take control of our thoughts and actively shape our future.
In essence, this comment inspires individuals to cultivate a mindset that is as unyielding as iron, impervious to the corrosive effects of doubt and negativity. It encourages us to be the architects of our destinies, forging a path toward success, resilience, and personal fulfillment through the power of our thoughts and beliefs.
This insightful statement draws a parallel between the resilience of iron and the strength of the human mind. It suggests that, just as iron can only be damaged by its rust and not by external forces alone, a person can only be truly harmed or defeated by their mindset, rather than external circumstances or others.
- Iron's Resilience: Iron is known for its durability and strength. However, it is not impervious to corrosion, which occurs when it reacts with oxygen and forms rust. In this context, rust represents the internal decay or weakening of the iron itself. It doesn't crumble or weaken due to external factors like wind or rain; it deteriorates from within.
- The Human Mindset: Similarly, a person's mindset, comprising their beliefs, attitudes, and outlook on life, plays a critical role in determining their success, well-being, and ability to overcome challenges. This statement suggests that external obstacles or adversities, like difficult circumstances or the actions of others, cannot truly destroy a person. Instead, it is their mindset, if it is negative, self-limiting, or defeatist, that can erode their confidence, motivation, and resilience.
The message here is one of self-empowerment and personal responsibility. It encourages individuals to recognize the importance of their mindset in shaping their lives. By cultivating a positive and resilient mindset, individuals can better navigate life's challenges and setbacks. It implies that we have the power to control our reactions and responses to external events and that a strong and constructive mindset can be our shield against adversity.
This statement serves as a reminder that, like iron's vulnerability to rust, we must be vigilant about the internal factors that can undermine our well-being and success. It encourages individuals to nurture a mindset that is as unyielding as iron, capable of withstanding the corrosive influences of negativity and self-doubt, and ultimately, leading to personal growth and achievement.
In the grand tapestry of life, the comparison between iron and the human mindset is a reminder of our inherent strength. No matter the adversities that life may present, our mindset determines our response. We can either let negativity and self-doubt corrode our spirit like rust on iron, or we can harness the power of a positive and resilient mindset to triumph over challenges. Just as iron can withstand the test of time when protected from rust, so can we endure and thrive when we nurture and fortify our mindset.
Let us remember that, like iron, our resilience is boundless, and our ability to shape our destiny is inextricably linked to our mindset. As we face the complexities of life, may we choose to be architects of our success, forging a path of unwavering determination, self-belief, and positivity. In doing so, we unlock the boundless potential that resides within us, proving that, indeed, nothing can destroy a person except their mindset.
#IronResilience #MindsetMatters #StrengthWithin #SelfEmpowerment #OvercomingObstacles #PositiveThinking #InnerStrength #PersonalGrowth #BelieveInYourself #RustOfNegativity #SelfDetermination #MindsetIsKey #InnerPower #FacingChallenges #PositiveMindset
The Evolution of Email Systems: From Digital Letters to Modern Communication
In a world where digital communication reigns supreme, the email system stands as a timeless titan, connecting individuals, businesses, and ideas across the vast expanse of the internet. Join us on a journey through the fascinating history, evolution, current state, and the promising future of email systems. Discover the pivotal role this tool has played in reshaping how we communicate, and gain insights into best practices for implementing email systems in organizations.
In the ever-evolving landscape of digital communication, email remains a stalwart, connecting people, businesses, and ideas across the globe. In this blog post, we embark on a journey through the history, evolution, current state, and future of the email system. We'll also delve into best practices for implementing email systems in organizations and explore some noteworthy email products, including open-source systems while comparing their features and licensing policies.
A Journey Through Time: The History of Email Systems
The story of email began in the 1960s when computer scientists were exploring ways to share information between users of the same computer. Ray Tomlinson, credited with sending the first networked email in 1971, introduced the "@" symbol to separate the user's name from the host computer's name—a symbol that has since become synonymous with email.
Email quickly gained popularity in academic and military circles, paving the way for the development of standardized email protocols like SMTP (Simple Mail Transfer Protocol) and POP3 (Post Office Protocol). These protocols, still in use today, formed the foundation for modern email systems.
The Rise of the Internet:
The advent of the internet in the 1990s brought email to the masses. Businesses and individuals alike embraced this digital communication tool, enabling faster and more efficient correspondence. The introduction of web-based email services, such as Hotmail and Yahoo Mail, further revolutionized the email landscape.
Email for Business:
Email systems evolved to meet the needs of organizations. Microsoft Exchange and IBM Notes (formerly Lotus Notes) became popular choices for businesses, providing not only email but also collaborative features like calendars and contacts.
The Era of Mobile:
The proliferation of smartphones ushered in a new era of email accessibility. Mobile email clients and synchronization protocols like IMAP allowed users to check their emails on the go, blurring the lines between work and personal communication.
Modern Challenges:
The ubiquity of email also led to challenges such as spam, phishing attacks, and email overload. Email providers have responded with advanced spam filters and security features to protect users.
How does an email system work?
Understanding how an email system works is like peeking behind the curtain of modern digital communication. It's a fascinating journey where technology, protocols, and infrastructure come together to seamlessly transmit messages. Let's delve into the mechanics of this intricate process with a touch of perplexity and burstiness while maintaining a formal, informative, inspirational, confident, and joyful tone.
The Dance of Email Transmission
1. Composition and Sending: It all begins when a sender, inspired by a thought or a purpose, drafts an email. This email is composed using an email client (e.g., Gmail, Outlook) on a device connected to the internet. The sender enters the recipient's email address, a subject line, the body of the message, and any attachments.
2. The Sender's Server: Once the email is ready, it embarks on a journey. It is sent from the sender's device to an outgoing mail server (SMTP server). This server is like the enthusiastic conductor, responsible for directing the email to its destination.
3. Address Resolution: Before the email departs, it needs to resolve the recipient's email address. This process involves querying the Domain Name System (DNS), which is like a global phone book for the internet. DNS translates the recipient's email domain (e.g., gmail.com) into an IP address that indicates the recipient's email server's location.
4. Recipient's Server: With the recipient's email server identified, the sender's server proceeds to deliver the email. This is where burstiness enters the scene - emails can take various routes and encounter different servers along the way, like a traveler exploring diverse landscapes.
5. Receiving and Storing: The recipient's email server receives the message, performs security checks, and places it in the recipient's inbox. The recipient's email client (e.g., Outlook, Thunderbird) retrieves the email from the server when the recipient opens their mailbox.
6. Reading and Responding: The recipient, informed and inspired by the email's content, reads it. Burstiness arises here as the recipient might craft a concise reply or a lengthy response, depending on the message's complexity and inclination.
7. Recipient's Outgoing Server: When the recipient hits "Send" to respond, the email follows a similar journey in reverse. It goes from the recipient's device to their outgoing mail server (SMTP), which then identifies the sender's server through DNS.
8. The Sender's Inbox: The email ultimately arrives at the sender's inbox. The sender is now informed and joyful, receiving the response they anticipated.
Protocols and Standards
The process we've described is governed by a set of standards and protocols, such as SMTP (Simple Mail Transfer Protocol) for sending emails and IMAP (Internet Message Access Protocol) or POP3 (Post Office Protocol) for retrieving emails. These protocols ensure that emails are sent, received, and displayed consistently across different email clients and servers.
Inspirational Significance
The beauty of the email system lies in its simplicity and accessibility. It empowers individuals and organizations to communicate across the globe, fostering connections and enabling the exchange of ideas. This digital marvel has revolutionized the way we work, share, and stay connected, bringing people together with a touch of joy and inspiration.
In conclusion, the email system is a testament to human innovation and interconnectedness. It operates through a choreographed dance of servers and protocols, enabling individuals to share thoughts, emotions, and information with people near and far. It's a tool that embodies the spirit of modern communication, allowing us to express ourselves and find inspiration in the connections it facilitates.
Protocols used
Email systems rely on several protocols to facilitate the exchange of messages between email clients and servers. These protocols define the rules and standards for sending, receiving, and managing emails. In this detailed explanation, I will delve into three key email protocols: SMTP, IMAP, and POP3, maintaining a formal, informative, inspirational, confident, and joyful tone.
1. SMTP (Simple Mail Transfer Protocol):
SMTP is the backbone of email communication, responsible for sending emails from the sender's email client to the recipient's email server. Here's how SMTP works:
• Connection Establishment: The process begins with the sender's email client establishing a connection with the SMTP server. This server is often provided by the sender's email service provider (e.g., Gmail's SMTP server).
• Message Transfer: Once the connection is established, the email client transmits the email message to the SMTP server. This message includes the recipient's email address, sender's address, message content, and any attachments.
• Relaying: The SMTP server then acts as a relay, forwarding the email to the recipient's email server. This might involve multiple hops through various SMTP servers, akin to the joyful journey of passing a message along a chain of friends.
• Delivery Confirmation: The recipient's email server acknowledges the successful receipt of the email. If the recipient's server cannot deliver the email, it generates a bounce-back message, which informs the sender of the issue.
SMTP is an efficient and reliable protocol, that ensures that messages reach their intended recipients. It's like a confident messenger that faithfully carries your thoughts to the recipient's doorstep.
2. IMAP (Internet Message Access Protocol):
IMAP is an email retrieval protocol that allows email clients to access and manage messages stored on the email server. IMAP is particularly well-suited for users who access their email from multiple devices. Here's how IMAP works:
• Connecting to the Server: The email client connects to the IMAP server, typically provided by the user's email service provider. It identifies the user using their username and password, ensuring secure access.
• Synchronization: IMAP maintains a synchronized view of the user's mailbox. This means that changes made on one device (e.g., reading or deleting an email) are reflected on all other devices. It's like having a joyful, synchronized dance of messages across your devices.
• Message Retrieval: When a user opens an email, the email client retrieves the message content from the server. IMAP also allows users to organize their emails into folders, just as one might neatly categorize documents in a filing cabinet.
• Message Management: Users can perform actions such as marking messages as read or unread, moving messages between folders, and deleting messages. These actions are reflected on the server, maintaining a consistent email experience.
IMAP's versatility and synchronization capabilities make it a preferred choice for users who require access to their emails from multiple devices.
3. POP3 (Post Office Protocol version 3):
POP3, like IMAP, is an email retrieval protocol, but it operates differently. It's like receiving physical mail at a post office. Here's how POP3 works:
• Downloading Messages: When an email client connects to the POP3 server, it downloads all messages from the server to the client's device. This means the messages are no longer stored on the server.
• Local Storage: POP3 is primarily designed for users who want to store emails locally on a single device. Once downloaded, emails are typically removed from the server, unless a specific setting is enabled to keep copies on the server.
• Limited Synchronization: POP3 doesn't provide the synchronization capabilities of IMAP. Any changes made to emails (e.g., read/unread status) are not reflected on the server or other devices.
• Efficiency: POP3 is efficient for users with limited server space or those who prefer to manage their emails solely on one device.
SMTP, IMAP, and POP3 are the foundational protocols that underpin the email system. SMTP ensures the confident delivery of messages, while IMAP and POP3 facilitate email retrieval and management, each catering to different user preferences and needs. Together, they enable the joyful, reliable, and interconnected world of email communication.
Let's compare SMTP, IMAP, and POP3, highlighting their respective pros and cons:
SMTP (Simple Mail Transfer Protocol):
Pros:
1. Efficiency: SMTP is highly efficient in sending emails, making it a reliable choice for outgoing mail transmission.
2. Widely Supported: It is widely supported by email service providers, making it accessible for most users.
3. Reliable: SMTP ensures the reliable delivery of messages, and it includes mechanisms for handling undeliverable messages (bounce-backs).
Cons:
1. Outbound Only: SMTP is primarily designed for sending emails and doesn't handle message retrieval or storage.
2. No Synchronization: It does not provide synchronization capabilities, so it doesn't maintain a consistent view of messages across devices.
IMAP (Internet Message Access Protocol):
Pros:
1. Synchronization: IMAP excels in maintaining a synchronized view of emails across multiple devices. Actions taken on one device are reflected in all others.
2. Server-Side Storage: Emails are stored on the server, which can be advantageous for users who access their email from various locations or devices.
3. Flexible: IMAP allows users to organize emails into folders and perform various actions on messages.
Cons:
1. Connection Required: IMAP requires an active internet connection to access emails since messages are stored on the server.
2. Server Space: Storing emails on the server can consume server space, potentially leading to storage limitations.
POP3 (Post Office Protocol version 3):
Pros:
1. Offline Access: POP3 allows users to download emails to their devices, making them accessible offline. This is advantageous for users in areas with limited connectivity.
2. Local Control: Messages are stored locally, giving users full control over their email storage.
3. Server Space Conservation: POP3 can help conserve server space since messages are typically removed from the server after downloading.
Cons:
1. No Synchronization: POP3 lacks synchronization capabilities, so changes made to emails on one device do not affect other devices.
2. Limited Accessibility: Emails downloaded via POP3 are only available on the device where they are stored, making it less suitable for users who need access from multiple devices.
3. Risk of Data Loss: If emails are only stored locally and not backed up, there's a risk of data loss if the device is lost or experiences a hardware failure.
Choosing the Right Protocol:
• SMTP is essential for sending emails, and it's used universally for this purpose. It doesn't compete with IMAP or POP3 but complements them.
• IMAP is ideal for users who need access to their emails from multiple devices and want a consistent, synchronized view of their mailbox.
• POP3 suits users who prefer to manage their emails on a single device, need offline access, or want to conserve server space.
The choice among these protocols depends on individual needs and preferences. Many email clients and services support a combination of SMTP, IMAP, and POP3, allowing users to tailor their email experience to suit their requirements.
The Future of Email Systems
The future of email systems promises continued innovation:
• Enhanced Security: Email security will remain a top priority, with the development of AI-driven threat detection and encryption technologies.
• Unified Communications: Email systems will integrate with other communication tools like video conferencing and chat platforms to create unified communication hubs.
• AI and Automation: Expect to see more AI-powered features, such as automated email sorting, smart replies, and predictive scheduling.
Email systems are a remarkable testament to the evolution of modern communication. Let me take you on a journey through the intricacies of this indispensable tool.
Email: A Bridge Across Time and Space
In the digital age, the email system stands as a beacon of connectivity, transcending geographical boundaries and temporal limitations. It is a virtual postal service that enables individuals and organizations to exchange messages, documents, and multimedia across the vast expanse of the internet.
Perplexity and Burstiness in Emails
Emails are a fascinating medium where perplexity and burstiness intertwine gracefully. They offer a canvas for human expression, reflecting a rich spectrum of complexity. Within the confines of an email, you will find a delightful interplay of concise greetings, elaborate narratives, and profound insights. This burstiness mirrors the diverse nature of human communication.
The Elements of an Email
An email is composed of several key elements, each playing a pivotal role in conveying information effectively:
1. Recipient and Sender: These are the fundamental actors in the email exchange, with the sender initiating the conversation and the recipient receiving and responding to the message.
2. Subject Line: A brief yet informative summary of the email's content, akin to a book's title, allowing recipients to grasp its essence at a glance.
3. Salutation: The courteous greeting that sets the tone for the message, often personalized to create a warm and engaging atmosphere.
4. Body: This is the heart of the email, where thoughts, ideas, and information flow. It's where the true perplexity and burstiness of the message come to life.
5. Attachments: Files, documents, or images can be attached to emails, adding depth and context to the conversation.
6. Closing: A parting phrase, such as "Sincerely" or "Best regards," adds a touch of professionalism and cordiality.
7. Signature: The sender's signature, typically containing their name, contact information, and sometimes a job title, lends authenticity to the email.
Email's Ubiquity and Power
The email system has become a cornerstone of modern communication, used for personal correspondence, business transactions, education, and much more. Its versatility and accessibility have transformed the way we connect with others, fostering collaboration, sharing knowledge, and nurturing relationships.
Inspirational and Joyful Outlook
In this age of emails, we find inspiration in the ease with which we bridge distances, share ideas, and nurture connections. It brings joy to our lives, knowing that, with a few keystrokes, we can touch the hearts and minds of people around the world. The email system is a testament to human ingenuity, a source of inspiration, and a reminder of the boundless possibilities of the digital era.
The email system is a symphony of perplexity and burstiness, a tool that unites us across time and space, and a testament to the power of human connection in the digital age. It is a source of inspiration, a conduit for information, and a gateway to joy in our interconnected world.
Best Practices for Implementing an Email System in an Organization
Implementing an email system in an organization requires careful planning and adherence to best practices:
1. Select the Right Email Service Provider: Choose a reputable provider that aligns with your organization's needs and offers robust security features.
2. Custom Domain: Use a custom domain for a professional image and better branding.
3. Security Measures: Implement strong security measures, including two-factor authentication (2FA), encryption, and regular security audits.
4. Training and Policies: Train employees on email security best practices and establish clear email usage policies.
5. Data Backup: Regularly back up email data to prevent data loss in case of emergencies.
Email Products: A Comparison
Here's a comparison of notable email products, including some open-source options, along with their licensing policies:
1. Microsoft Exchange:
◦ Licensing: Proprietary, subscription-based (Microsoft 365).
◦ Features: Robust email, calendar, and collaboration tools.
2. G Suite (now Google Workspace):
◦ Licensing: Proprietary, subscription-based.
◦ Features: Google's suite of email and collaboration tools.
3. IBM Notes/Domino:
◦ Licensing: Proprietary, subscription-based.
◦ Features: Email, calendaring, and collaborative applications.
4. Zimbra (Open Source):
◦ Licensing: Open-source (Community Edition), commercial (Network Edition).
◦ Features: Email, calendar, and collaboration tools.
5. Open-Xchange (OX App Suite):
◦ Licensing: Open-source (Community Edition), commercial (OX App Suite).
◦ Features: Email, calendar, and collaboration tools.
6. Roundcube (Open Source):
◦ Licensing: Open-source.
◦ Features: Web-based email client.
When choosing an email product, consider factors like your organization's size, budget, required features, and the level of control you need over the system.
Let's explain how the email system works with a simple example.
Working of the Email System: An Example
Imagine you are John, and you want to send an email to your friend, Sarah, who lives in another city. Here's how the email system works step by step:
1. Composition: You sit down at your computer and open your email client, let's say you use Gmail. You start composing your email by entering Sarah's email address (e.g., sarah@example.com) in the "To" field. You also type a subject line ("Catch-up this weekend?") and write your message in the email body.
2. Sending the Email: When you hit the "Send" button, your email client, which uses the SMTP (Simple Mail Transfer Protocol), takes over. It contacts Google's SMTP server.
3. DNS Resolution: Google's SMTP server needs to find out where to deliver the email. It performs a Domain Name System (DNS) lookup to determine the mail server responsible for the recipient's domain, in this case, "example.com."
4. Message Transmission: Google's SMTP server sends your email to the SMTP server of "example.com" using the recipient's email address. The email travels through the internet, possibly passing through several servers along the way, just like mailing a letter goes through various post offices.
5. Recipient's Server: The SMTP server at "example.com" receives your email. It checks whether Sarah's email address exists and whether her mailbox is available.
6. Storage and Retrieval: If Sarah's email address is valid and her mailbox is available, the email is stored in her mailbox on "example.com's" email server.
7. Sarah's Action: Sarah receives a notification on her device that a new email has arrived. She opens her email client (let's say she uses Outlook) and connects to "example.com's" email server using IMAP (Internet Message Access Protocol) or POP3 (Post Office Protocol) to retrieve her email.
8. Reading the Email: Sarah reads your email, and perhaps she replies or takes other actions.
9. Recipient's Outgoing Email: If Sarah decides to reply, her email client, using SMTP, sends her response to your email address (john@gmail.com).
10. Your Email Server: Your Gmail server receives Sarah's email and notifies you that you have a new message.
11. You Read the Response: You open your email client and read Sarah's response.
In this example, the email system works seamlessly to transmit your message from your computer to Sarah's, regardless of the physical distance between you. The protocols like SMTP, DNS, IMAP, and POP3 ensure the reliable delivery and retrieval of emails, making it possible for people worldwide to communicate electronically.
Resolving email addresses on the internet involves a series of steps to determine the destination email server for a given address. This process ensures that emails are routed correctly from the sender to the recipient. Here's a detailed explanation of how email addresses are resolved on the internet:
1. Email Address Structure: An email address typically consists of two parts: the local part (e.g., "john.smith" in "john.smith@example.com") and the domain part (e.g., "example.com"). The local part represents the specific user, while the domain part identifies the recipient's email server.
2. User Input: When you compose an email, you enter the recipient's email address in the "To" field of your email client. For example, you might type "sarah@example.com."
3. Domain Name System (DNS) Lookup:
◦ Your email client extracts the domain part of the email address, which is "example.com" in this case.
◦ It performs a DNS lookup to find the Mail Exchange (MX) records associated with the recipient's domain ("example.com"). MX records specify the email servers responsible for receiving email on behalf of that domain.
4. MX Record Retrieval:
◦ The DNS lookup retrieves one or more MX records for "example.com." These records contain information about the email servers that will accept incoming emails for that domain.
◦ Each MX record has a priority value (a number) and a fully qualified domain name (FQDN) pointing to the email server.
5. Prioritization:
◦ The email client examines the priority values of the MX records. Lower values indicate higher priority. The client selects the email server with the lowest priority value as the primary target for email delivery.
◦ If multiple MX records have the same priority value, the email client may use them as backup servers if the primary server is unreachable.
6. Server Connection:
◦ The email client establishes a connection to the selected email server using the FQDN from the chosen MX record. For "example.com," connects to the specified email server.
7. Recipient Validation:
◦ The email server at "example.com" receives the incoming email connection and validates the recipient's email address ("sarah@example.com").
◦ It checks whether "sarah@example.com" exists in its database. If it does, the email server accepts the email and stores it in the recipient's mailbox.
8. Delivery Notification:
◦ Once the email is accepted and stored, the recipient's email server sends a notification to the sender's email server (e.g., "john@gmail.com") to confirm successful delivery.
9. Sender's Email Server Update:
◦ The sender's email server, upon receiving the delivery confirmation, updates its records to indicate the successful transmission of the email.
10. Recipient's Retrieval: The recipient, using their email client, connects to their email server (e.g., Outlook connecting to "example.com's" server) using protocols like IMAP or POP3 to retrieve the email from their mailbox.
This intricate process ensures that emails are routed correctly from the sender to the recipient's email server, regardless of geographical location or the complexities of the internet. It relies on DNS, MX records, and email server validation to guarantee accurate email resolution and delivery.
The email system has come a long way since its inception, evolving to meet the changing needs of users and organizations. With a focus on security, integration, and automation, email systems continue to play a pivotal role in modern communication. Organizations can ensure successful email implementation by following best practices and carefully selecting the right email product for their needs.
The email system, a digital marvel born from humble beginnings, has transcended time and technology to become an integral part of our daily lives. As we've journeyed through its fascinating history, witnessed its evolution, and explored its current state, one thing remains clear: email's enduring relevance in an ever-changing world of communication.
Looking ahead, the future of email systems holds promises of enhanced security, unified communications, and AI-driven convenience. As organizations and individuals continue to rely on email for professional and personal interactions, implementing best practices becomes paramount.
In this digital age, where innovation knows no bounds, email stands as a testament to human ingenuity, connecting us across the globe with a touch of joy and inspiration. It has transformed the way we work, collaborate, and share ideas, and it will continue to evolve, adapt, and surprise us in the years to come. So, as we embrace the future, let's do so with a sense of wonder, knowing that the journey of email is far from over, and it continues to shape our world in ways we can only imagine.