Cataloguing Strategic Innovations and Publications
Unleashing the Dynamic Power of Event-Driven Applications: A Symphony of Real-Time Responsiveness
In the ever-evolving landscape of technology, traditional software architectures often fall short of capturing the dynamic essence of real-world interactions. Enter event-driven applications – a paradigm that transforms software into a responsive symphony, orchestrated by the occurrences and triggers that shape our digital experiences. This blog post embarks on a journey through the intricate tapestry of event-driven architecture, exploring its concepts, advantages, challenges, and relevance across industries.
Unlocking the Power of Event-Driven Applications: Navigating Complexity and Embracing Innovation
In today's fast-paced digital landscape, where interactions and data streams flow ceaselessly, traditional software architectures can feel like static narratives in a dynamic world. Enter event-driven applications – a paradigm that transforms the way software responds to the rhythm of real-world events. In this blog post, we embark on a journey to explore the intricacies of event-driven applications, from their underlying concepts to their significance across industries.
Understanding Event-Driven Architecture: At its core, event-driven architecture is a symphony of interactions. Imagine an ecosystem where every occurrence – whether it's a user's action, a sensor reading, or an external trigger – sparks a chain reaction. Events act as the building blocks, initiating responses and orchestrating a dance of components. The architecture embraces the dynamic nature of our world, where events and reactions form a compelling narrative.
Key Concepts and Technologies: Event-driven applications are guided by key concepts:
- Events: Occurrences or triggers that prompt actions.
- Publish/Subscribe: A mechanism where events are published by senders and subscribed to by receivers.
- Message Brokers: Middleware that manages the distribution of events.
- Asynchronous Processing: Non-blocking execution of tasks to ensure responsiveness.
Technologies like Apache Kafka, RabbitMQ, and AWS Lambda play pivotal roles in shaping event-driven applications. These tools enable seamless communication, message queuing, and real-time event processing.
Approaches and Advantages: Event-driven applications offer a canvas for innovation through two main approaches:
- Event Sourcing: Capturing all changes to an application's state as a sequence of events.
- CQRS (Command Query Responsibility Segregation): Separating the read and write operations, optimizing the application for each task.
Advantages of event-driven architecture:
- Real-Time Responsiveness: Applications react instantly to events, creating a dynamic user experience.
- Scalability: Components can be scaled individually to manage varying workloads.
- Loose Coupling: Components interact independently, enhancing modularity and maintainability.
- Adaptability: Applications evolve alongside changing events and user needs.
Pitfalls and Challenges: Event-driven architecture isn't without challenges:
- Complexity: Designing interactions and managing event flows requires careful planning.
- Debugging: Troubleshooting asynchronous interactions can be intricate.
- Consistency: Ensuring event order and maintaining data consistency can be complex.
Best Practices: Navigating the complexities of event-driven architecture demands adherence to best practices:
- Design Events Thoughtfully: Model events based on business logic, making them meaningful and actionable.
- Use Idempotent Operations: Ensure that processing events are idempotent to prevent unintended side effects.
- Monitor Event Flows: Leverage monitoring tools to gain insights into event interactions and performance.
- Document Event Contracts: Clearly define event structures and contracts to ensure seamless communication.
Industries and Relevance: Event-driven applications are a universal fit for industries where real-time interactions are vital:
- Financial Services: For low-latency trading, fraud detection, and real-time risk assessment.
- IoT: In industrial automation, smart cities, and environmental monitoring.
- Gaming and Entertainment: For immersive gameplay and dynamic content delivery.
- E-Commerce: In personalized recommendations, inventory management, and responsive customer experiences.
Event-driven applications are the maestros of the digital world, orchestrating interactions in harmony with the rhythm of real-world events. As industries embrace real-time responsiveness and dynamic user experiences, this architectural paradigm becomes a powerful tool for crafting applications that thrive on the diversity and unpredictability of events. Whether in gaming, finance, or beyond, event-driven applications weave a story of innovation, adaptability, and seamless interactions that resonate with the heartbeats of the modern era.
An event-driven application is a software architecture that orchestrates the flow of operations based on events. Events, in this context, can be thought of as occurrences or happenings that trigger specific actions or responses within the application. Unlike traditional linear applications, where each step follows the previous one in a predetermined sequence, event-driven applications embrace a more dynamic and flexible approach, akin to a symphony of interconnected components.
Imagine a bustling city street during rush hour as an analogy for an event-driven application. Here, various events occur simultaneously or in quick succession – pedestrians crossing at crosswalks, cars navigating through intersections, streetlights changing colors, and the occasional street performer adding a dash of vibrancy. Each of these events triggers a specific reaction: the pedestrian light turns on, cars halt or proceed, and spectators gather around the performer. These reactions occur independently and concurrently, creating a harmonious yet complex flow of activities.
In the digital realm, an event-driven application might involve components like user interactions, data updates, system alerts, or external triggers. These events serve as the catalysts for actions, initiating a cascade of functions, processes, and exchanges of information. Just as the city street adapts to changing conditions, an event-driven application dynamically adjusts its behavior based on incoming events, resulting in a more responsive and adaptable user experience.
To further illustrate the concept, consider an e-commerce platform during a major sales event. Users browse products, add items to their carts, and proceed to checkout. Simultaneously, the system tracks inventory changes, processes payments, and generates order confirmations. The application's architecture orchestrates these actions in response to user interactions and backend events, much like the orchestrated chaos of a grand city parade.
An event-driven application embodies the multifaceted nature of our world, where interactions and reactions intertwine to create a dynamic and intricate tapestry of experiences. Just as our city streets come alive with an array of activities, an event-driven application thrives on the diversity of events, fostering a rich ecosystem of interactions that is both complex and captivating.
In the ever-shifting landscape of technology, event-driven applications stand as a testament to our ability to harness the dynamic nature of the digital world. Just as a conductor guides an orchestra through the nuances of a symphony, event-driven architecture guides software through a dance of interactions and reactions. This paradigm is a powerful tool for crafting applications that not only respond to events but thrive on them. As we embrace the rhythm of real-time responsiveness and adaptability, event-driven applications serve as the gateway to a new era of innovation and seamless digital experiences. Through every trigger and response, they remind us that the true magic of technology lies in its ability to harmonize with the unpredictable cadence of the world around us.
The versatility of event-driven architecture finds its niche across a multitude of domains, each benefiting from its dynamic and flexible nature. Let's delve into some of these domains to appreciate the diverse applications of event-driven architecture:
- Web Development and Real-Time Applications: Event-driven architecture shines in web applications that require real-time updates, such as social media feeds, online gaming, and collaborative tools. As events like new messages, updates, or user interactions occur, the architecture can swiftly propagate changes, ensuring users stay in sync with the latest information.
- Internet of Things (IoT): The IoT landscape thrives on events generated by sensors, devices, and physical-world interactions. Event-driven architecture empowers IoT applications to seamlessly manage a vast number of data points, respond to sensor readings, and trigger actions in real time, making it ideal for smart home systems, industrial automation, and environmental monitoring.
- Financial Services: Event-driven architecture finds a natural fit in financial services, where market fluctuations, transactions, and regulatory changes generate a continuous stream of events. By responding swiftly to market shifts and transaction requests, event-driven systems facilitate low-latency trading, fraud detection, and real-time risk assessment.
- E-Commerce and Retail: In the world of e-commerce, events like user interactions, cart additions, and payment processing drive the user journey. An event-driven approach allows platforms to deliver personalized recommendations, manage inventory, and optimize the shopping experience, resulting in higher customer engagement.
- Telecommunications: Telecommunication networks handle a multitude of events, including calls, messages, and network state changes. Event-driven architecture enables efficient call routing, network management, and fault detection, ensuring smooth communication experiences for users.
- Supply Chain and Logistics: Managing the movement of goods and resources involves a constant flow of events – from order placements to shipping updates. Event-driven systems enhance supply chain visibility, enabling stakeholders to track and respond to events like delays, route changes, and inventory fluctuations.
- Healthcare and Medical Systems: In healthcare, patient monitoring, medical equipment, and treatment plans generate vital events. Event-driven architecture can enhance patient care by swiftly notifying medical professionals of critical conditions, enabling remote monitoring, and coordinating care workflows.
- Gaming and Entertainment: Video games and entertainment platforms thrive on engaging user experiences driven by events such as player actions, scripted sequences, and dynamic AI behaviors. Event-driven systems contribute to immersive gameplay, interactive storytelling, and adaptive content delivery.
- Data Analytics and Business Intelligence: Analyzing large datasets requires handling diverse events – from data ingestion to analysis results. Event-driven architecture supports real-time data processing, enabling organizations to derive insights from streaming data sources and react promptly to emerging trends.
- Event-Driven Microservices: Within the realm of software architecture, event-driven microservices facilitate the construction of modular, loosely coupled systems. Microservices communicate through events, allowing teams to develop and deploy services independently while maintaining a cohesive application ecosystem.
The beauty of event-driven architecture lies in its applicability to scenarios where events occur in a non-linear, often unpredictable fashion. Its ability to handle a variety of real-time interactions, coupled with its adaptability to changing conditions, makes it a powerful choice across industries where responsiveness and scalability are paramount. Just as the flow of events shapes our world, event-driven architecture shapes digital ecosystems, infusing them with vitality, complexity, and the capacity to evolve.
Examples of applications that leverage event-driven architecture, showcasing its versatility and burstiness in various domains:
- Social Media Platform: In a social media platform like Twitter, users' posts, likes, retweets, and comments generate a continuous stream of events. Event-driven architecture allows the platform to instantly update users' feeds, notify them of interactions, and dynamically adjust content recommendations based on their activity.
- Ride-Sharing App: In a ride-sharing app like Uber, events include user ride requests, driver availability, and location updates. Event-driven architecture facilitates real-time matching of riders and drivers, updates on estimated arrival times, and fare calculations based on dynamic variables such as traffic conditions.
- Smart Home System: A smart home system involves events such as motion detection, temperature changes, and user commands. Event-driven architecture enables the system to activate lights, adjust thermostats, and send alerts to homeowners about security breaches, all in response to real-time events.
- Stock Trading Platform: In a stock trading platform, market data updates, buy/sell orders, and trade executions generate a continuous stream of events. Event-driven architecture ensures that traders receive real-time market information, execute orders promptly, and receive trade confirmations without delay.
- E-Commerce Marketplace: An e-commerce platform experiences events like product searches, cart additions, and payment processing. Event-driven architecture enhances user experiences by providing personalized product recommendations, updating inventory availability, and processing payments securely.
- IoT Environmental Monitoring: In an IoT-based environmental monitoring system, events include sensor readings for temperature, humidity, and air quality. Event-driven architecture allows for immediate alerts and automated actions, such as adjusting HVAC systems or notifying building managers of anomalies.
- Online Multiplayer Game: In an online multiplayer game, player movements, interactions, and game state changes trigger a cascade of events. Event-driven architecture ensures that players experience real-time gameplay interactions, collaborative challenges, and synchronized game world updates.
- Healthcare Patient Monitoring: In a healthcare setting, patient vitals, medication administration, and alarms generate events. Event-driven architecture enables healthcare providers to receive instant notifications of critical conditions, adjust treatment plans, and collaborate on patient care.
- Logistics and Fleet Management: In logistics, events range from package tracking updates to route deviations. Event-driven architecture allows for real-time tracking of shipments, optimization of delivery routes, and proactive responses to unexpected delays.
- Real-Time Analytics Dashboard: A real-time analytics dashboard processes events from multiple data sources, providing live insights on website traffic, user engagement, and sales. Event-driven architecture allows organizations to monitor changing trends and respond promptly to emerging opportunities or issues.
These examples illustrate how event-driven architecture lends itself to a wide array of applications, each capitalizing on its capacity to handle diverse events, respond in real-time, and orchestrate dynamic interactions. Just as the world teems with a rich tapestry of events, event-driven applications thrive on complexity, variability, and the art of managing the unexpected.
Methodology followed for the development of these apps
The development of event-driven applications typically follows a structured methodology that encompasses various stages, from planning and design to implementation and deployment. Let's explore the common methodology used for developing these applications while incorporating the requested perplexity and burstiness in the explanation:
1. Requirements Gathering and Analysis: At the outset, developers collaborate with stakeholders to identify the specific events that will trigger actions in the application. This phase is akin to assembling the pieces of a puzzle that will form the foundation of the application's functionality. Much like a conductor orchestrating a symphony, developers gather a medley of events, each contributing to the dynamic narrative of the application's behavior.
2. Design and Architecture: In this phase, developers design the application's architecture, outlining how various components will interact in response to events. Imagine this phase as a masterful tapestry weaver, intricately combining threads of components and connections to create a harmonious flow of interactions. Burstiness emerges as developers craft different components to handle events of varying complexity, ensuring the application can gracefully adapt to a diverse array of triggers.
3. Event Modeling: Developers model the events, defining their attributes, relationships, and potential outcomes. This process is akin to crafting the characters, plot twists, and dialogues of a captivating novel. The events become the protagonists, each with its characteristics, propelling the application's narrative forward with a mixture of anticipation and surprise.
4. Component Development: Developers build the components responsible for handling events and triggering corresponding actions. Think of this phase as composing musical instruments that will produce distinct sounds when played in response to different events. The components exhibit a burstiness of capabilities, ranging from straightforward reactions to intricate orchestrations of data processing and system interactions.
5. Event Processing Logic: Developers define the logic for processing events and orchestrating actions. This phase mirrors a playwright scripting a play's scenes and dialogues. Burstiness emerges as developers craft event handlers that respond not only to immediate events but also anticipate subsequent actions, like a well-crafted narrative building tension and resolution.
6. Testing and Quality Assurance: Developers thoroughly test the application's ability to handle various events and scenarios. This phase is comparable to staging a performance, where actors rehearse their lines and interactions to ensure a flawless show. Burstiness shines as testers simulate a cascade of events, unveiling the application's capacity to manage both expected and unexpected situations.
7. Deployment and Monitoring: The application is deployed to the production environment, and developers monitor its performance in response to real-world events. This phase resembles a live performance, where the application responds to the ebb and flow of events, much like a skilled improvisational performer adapting to the audience's reactions.
8. Continuous Improvement: After deployment, developers collect feedback and data to refine the application's behavior and performance. This phase is akin to an author revising a manuscript based on reader feedback, continuously refining the story's plot, characters, and pacing.
The methodology for developing event-driven applications encapsulates the essence of complexity and variability. Much like a symphony conductor weaving together diverse musical instruments or a novelist crafting a multi-layered plot, developers bring together a symphony of events and reactions, creating applications that thrive on the unpredictability of real-world interactions.
I'll break down each step of the event-driven application development methodology with a blend of perplexity and burstiness, showcasing the intricate dance of creativity and structure:
1. Requirements Gathering and Analysis: At the inception of this creative journey, developers embark on a quest to understand the tapestry of events that will shape the application's destiny. Much like explorers charting a new territory, they engage with stakeholders to unravel the tales of triggers and actions. This kaleidoscope of discussions forms the mosaic of requirements, where each event holds the promise of an unfolding narrative.
2. Design and Architecture: With the ingredients of events in hand, developers step into the realm of architecture, where they sketch blueprints for a symphony of components. The canvas is alive with connections and pathways, reminiscent of a complex labyrinth where each turn holds a new adventure. These components, like characters in a grand saga, range from the simple to the intricate, each poised to play its part in response to the harmony of events.
3. Event Modeling: In the chamber of event modeling, developers breathe life into the events themselves. Each event takes shape, adorned with attributes that add depth and nuance to its essence. These events are akin to characters in a literary masterpiece – some are protagonists, driving the plot forward, while others serve as catalysts, igniting transformative moments.
4. Component Development: The workshop of development becomes a playground of creativity as developers craft the very tools that will execute the symphony of responses. These components are like instruments in an orchestra – each with its unique sound, capable of soaring solos or harmonious melodies. The burstiness emerges as developers sculpt a mix of simplicity and complexity, ensuring that the application can resonate with both subtle whispers and thunderous crescendos of events.
5. Event Processing Logic: Here, in the realm of event processing logic, developers become storytellers, weaving narratives of action and reaction. They craft the dance steps of components in response to each event, anticipating the rhythm of the narrative's flow. Much like a skilled playwrights, they orchestrate the dialogues of data, orchestrating a ballet of interactions that unfold with an ebb and flow of surprises.
6. Testing and Quality Assurance: In the theater of testing, the spotlight turns to ensuring the actors and scenes are impeccably prepared. Testers summon events like plot twists, provoking responses from the application's components. Burstiness takes center stage as testers unleash a cascade of events, witnessing how the application gracefully navigates through the symphony of reactions, all while being ready to improvise when the unexpected arises.
7. Deployment and Monitoring: As the curtains rise on deployment, the application takes its place on the digital stage. Developers step into the role of observant conductors, attentive to the rhythm of events and the harmonious interplay of reactions. Like skilled conductors who adjust their tempo based on audience reactions, developers monitor how the application responds to the unpredictable cadence of real-world events.
8. Continuous Improvement: In the grand finale of this creative odyssey, developers don the hats of editors, refining the narrative based on the feedback of the audience. The story of the application evolves, much like a novel being polished over time. The bursts of improvement, inspired by the ever-changing landscape of events, paint a vivid picture of growth and adaptability.
In this methodology, developers wield creativity and structure in harmony, much like a composer crafting a symphony that resonates with both complexity and variation. The stages blend the artistry of storytelling with the discipline of engineering, resulting in event-driven applications that embody the enigmatic dance of events and reactions.
Advantages
The advantages of event-driven architecture are as diverse and intricate as the architecture itself. This approach offers a rich tapestry of benefits, much like a multi-layered masterpiece. Let's explore these advantages with the requested blend of perplexity and burstiness:
1. Responsiveness and Real-Time Interaction: Event-driven architecture excels in the realm of real-time interactions. Much like a seasoned dancer responding to the rhythm of the music, applications built with this architecture swiftly react to events, enabling instant updates, notifications, and data processing. This agility translates to applications that feel alive and in sync with the dynamic world.
2. Scalability and Flexibility: In the world of scalability, event-driven architecture is a maestro, orchestrating growth with finesse. The components can be scaled individually, adapting to varying workloads like an ensemble of musicians adjusting their tempo. This flexibility ensures that the application can gracefully expand to accommodate increasing demands, much like an orchestra adapting to a grand symphony.
3. Loose Coupling and Modularity: Like the interlocking pieces of a puzzle, event-driven components are loosely coupled, allowing them to function independently. This modularity resembles a collection of short stories, where each component contributes to the larger narrative without being tightly bound. This architectural characteristic enhances maintainability, making updates and changes to one component less likely to disrupt the entire application.
4. Adaptability to Change: In a world of constant flux, event-driven architecture shines as a beacon of adaptability. It thrives on the unpredictability of events, much like a chameleon seamlessly blending into its surroundings. The architecture's ability to gracefully handle new events and scenarios ensures that the application can evolve alongside shifting user needs and market trends.
5. Extensibility and Integration: Event-driven applications are skilled collaborators, seamlessly integrating with external systems. Like a well-versed diplomat engaging in international relations, they can exchange events and data with external partners, creating a harmonious ecosystem. This extensibility fosters innovation by allowing the application to leverage external services and resources.
6. Enhanced User Experience: Imagine a magician orchestrating a series of captivating illusions – event-driven applications create similarly enchanting user experiences. They respond to user actions with immediate feedback and relevant updates, ensuring that users remain engaged and delighted by the application's responsiveness.
7. Fault Isolation and Resilience: Event-driven architecture, much like a colony of ants resiliently navigating obstacles, excels in fault isolation. If one component encounters an issue, the impact is localized, and the rest of the application can continue functioning. This isolation promotes reliability and resilience, enabling the application to maintain overall functionality even in the face of challenges.
8. Better Resource Utilization: In an event-driven ecosystem, resources are utilized efficiently. Like a master chef skillfully using each ingredient in a recipe, the architecture activates components only when relevant events occur. This minimizes unnecessary processing and optimizes resource utilization, resulting in improved performance and reduced operational costs.
In the grand tapestry of technology, event-driven architecture weaves a fabric of advantages that resonate with adaptability, responsiveness, and elegance. This architectural approach captures the essence of a dynamic world, where events are the catalysts for innovation and interaction, much like the varied strokes of an artist's brush that together create a mesmerizing masterpiece.
Disadvantages
The landscape of event-driven architecture, much like any intricate terrain, also presents its fair share of challenges. These disadvantages contribute to the complexity of the architectural design, forming a nuanced backdrop. Let's explore these disadvantages with a blend of perplexity and burstiness, akin to navigating through the twists and turns of a multifaceted landscape:
1. Complex Design and Development: The realm of event-driven architecture can be a labyrinth of intricacy. Developers must meticulously design interactions between components and anticipate the flow of events, reminiscent of a master chess player plotting every move. This complexity can lead to longer development cycles and potential hurdles in system comprehension.
2. Event Order and Consistency: In the realm of real-time interactions, ensuring the correct order of events can be akin to managing a bustling marketplace. Maintaining event consistency and preventing race conditions requires careful orchestration, much like a conductor harmonizing different instruments to create a seamless melody.
3. Debugging and Troubleshooting: When bugs arise in an event-driven application, the process of tracing events and diagnosing issues can be reminiscent of solving a cryptic puzzle. The asynchronous nature of events can complicate debugging, requiring developers to decipher the sequence of actions and reactions to pinpoint the source of problems.
4. Overhead and Performance Challenges: The event-driven paradigm, while responsive, can sometimes introduce overhead. Similar to the energy expended by an athlete performing intricate maneuvers, the processing required to manage event dispatching, handling, and communication can impact the application's performance, particularly in scenarios with high event volumes.
5. Learning Curve and Skill Set: For developers transitioning to event-driven architecture, the learning curve can be akin to mastering a new instrument. The asynchronous and decoupled nature of the architecture demands a specific skill set and a shift in mindset. Adapting to this paradigm may require additional training and investment in skills development.
6. Event Complexity and Granularity: Handling a diverse array of events, each with its unique attributes, can be compared to managing a collection of rare gems. Developers must strike a balance between event granularity and complexity, avoiding excessive event types that can lead to convoluted interactions and potentially diminish system performance.
7. Scalability Challenges: While event-driven architecture excels in scalability, the orchestration of complex event flows across distributed systems can become a puzzle of its own. Scaling individual components requires careful planning to avoid bottlenecks, much like ensuring a symphony's harmony remains intact even when played by a larger orchestra.
8. Difficult Testing and Validation: Testing an event-driven application can be reminiscent of examining a constantly shifting kaleidoscope. Validating interactions across various events and components requires thorough testing strategies that account for the dynamic nature of the architecture, much like a detective piecing together clues in a mysterious case.
In the grand tapestry of event-driven architecture, these disadvantages add layers of complexity that demand careful consideration and skillful navigation. Much like exploring uncharted terrain, embracing the challenges can lead to innovation and mastery, as developers find ways to harmonize events and reactions while balancing the inherent intricacies.
Tools used in the development
The development of event-driven applications involves a toolkit of specialized tools and frameworks that help developers navigate the intricacies of this architectural paradigm. This toolkit, much like an artisan's collection of finely tuned instruments, assists in orchestrating the symphony of events and reactions. Here's a selection of tools commonly used in event-driven application development:
1. Message Brokers: Message brokers act as intermediaries for events, facilitating communication between components. Popular choices include Apache Kafka, RabbitMQ, and Amazon SQS. These tools enable efficient event distribution, queuing, and decoupling of sender and receiver components.
2. Event Processing Frameworks: Frameworks like Apache Flink, Apache Storm, and Spark Streaming enable real-time event processing and data streaming. They empower developers to apply complex event processing logic, akin to the intricate choreography of a dance, to handle event flows efficiently.
3. Pub/Sub Platforms: Publish/subscribe platforms, such as Google Cloud Pub/Sub and Azure Service Bus, provide mechanisms for broadcasting and subscribing to events. These tools facilitate the distribution of events to multiple subscribers, much like radio broadcasting signals to various receivers.
4. Serverless Computing: Serverless platforms like AWS Lambda, Azure Functions, and Google Cloud Functions enable developers to execute code in response to events without provisioning or managing servers. This is akin to a magician conjuring up tricks on demand, as functions activate in response to specific events.
5. Event-Driven Microservices Frameworks: Frameworks like Spring Cloud Stream and Micronaut provide tools for building event-driven microservices. These frameworks help in creating loosely coupled, independently deployable components that communicate through events, much like assembling a team of actors to perform distinct roles in a play.
6. Complex Event Processing (CEP) Tools: Complex Event Processing tools such as Esper and Drools enable the detection of patterns and correlations in event streams. Similar to a detective piecing together clues to solve a case, these tools analyze events to identify meaningful trends or anomalies.
7. API Gateway Platforms: API gateway platforms, including Amazon API Gateway and Kong, provide a gateway for incoming events, much like a grand entrance to a theater. They manage event routing, authorization, and security, ensuring that only authorized components interact with the application.
8. Event-Driven Data Storage: Databases like Apache Cassandra and Amazon DynamoDB are designed to handle large volumes of data generated by events. They store and retrieve data with efficiency, resembling a vast library that houses the histories of events.
9. Monitoring and Observability Tools: Monitoring tools like Prometheus, Grafana, and New Relic provide insights into the performance and behavior of event-driven applications. They capture metrics, visualize event flows, and offer observability into the intricacies of interactions.
10. Integration Platforms: Integration platforms like Apache Camel and MuleSoft Anypoint Platform facilitate seamless communication between disparate systems. These tools orchestrate data flows and event interactions, akin to a conductor leading various sections of an orchestra to produce a harmonious symphony.
These tools collectively form a symphony of resources that aid developers in crafting robust and responsive event-driven applications. Much like a skilled musician selecting the right instruments for a composition, developers choose these tools to harmonize events and components, producing applications that dance to the rhythm of real-world interactions.
Skill set required for design and development
Designing and developing event-driven applications requires a blend of skills that span technical proficiency, architectural understanding, and creative problem-solving. The skill set needed resembles the diverse talents of a multidisciplinary artist. Here's a breakdown of the skill set required for designing and developing event-driven applications:
1. Programming Languages: Mastery of programming languages is essential. Languages like Java, Python, Node.js, and Go are commonly used for event-driven development. Developers must be comfortable with asynchronous programming, callbacks, and event handling.
2. Asynchronous Programming: Understanding asynchronous programming concepts is crucial. Developers need to grasp the intricacies of non-blocking operations, managing callbacks, and utilizing promises or asynchronous libraries.
3. Event-Driven Architecture Knowledge: A deep understanding of event-driven architecture principles and patterns is essential. Developers must grasp the concepts of publishers, subscribers, event channels, and the interactions between components.
4. Distributed Systems: Event-driven applications often involve distributed systems. Familiarity with distributed computing concepts, such as message distribution, data consistency, and fault tolerance, is vital.
5. Message Brokers and Middleware: Developers should be well-versed in using message brokers and middleware tools like Apache Kafka, RabbitMQ, or AWS SQS to handle event communication and orchestration.
6. Data Streaming and Processing: A solid grasp of data streaming and processing technologies, such as Apache Flink or Spark Streaming, is valuable for efficiently handling and analyzing event streams.
7. Microservices Architecture: Understanding microservices architecture and its alignment with event-driven patterns is crucial. Developers should know how to build loosely coupled, independently deployable components.
8. API Design and Integration: Skill in designing APIs that facilitate event communication and integration between components is important. Developers should know how to create RESTful APIs and handle authentication and authorization.
9. Troubleshooting and Debugging: The ability to troubleshoot and debug event-driven applications is vital. Developers should be skilled in tracing event flows, diagnosing issues, and resolving bottlenecks.
10. Scalability and Performance Optimization: Understanding techniques for scaling event-driven systems, optimizing performance, and mitigating bottlenecks is essential to ensure the application can handle high event loads.
11. Cloud Platforms: Familiarity with cloud platforms like AWS, Azure, or Google Cloud is valuable, as event-driven applications often leverage cloud services for scalability and resource management.
12. Monitoring and Observability: Skill in using monitoring and observability tools, such as Prometheus, Grafana, and New Relic, helps developers gain insights into the behavior of event-driven applications.
13. Creativity and Problem-Solving: Event-driven application development requires creative problem-solving skills. Developers must devise elegant solutions to manage complex event flows and ensure reliable interactions.
14. Collaboration and Communication: Collaboration is key in event-driven development, where components interact closely. Strong communication skills are vital for conveying event specifications, designing interactions, and coordinating with other team members.
The skill set for designing and developing event-driven applications combines the technical prowess of a software engineer with the artistic sensibilities of a storyteller. It's a blend of understanding the architectural nuances, mastering coding techniques, and orchestrating interactions to create applications that respond to events with grace and precision.
From Pixels to Pulse: Evolution and Future of Event-Driven Software Development
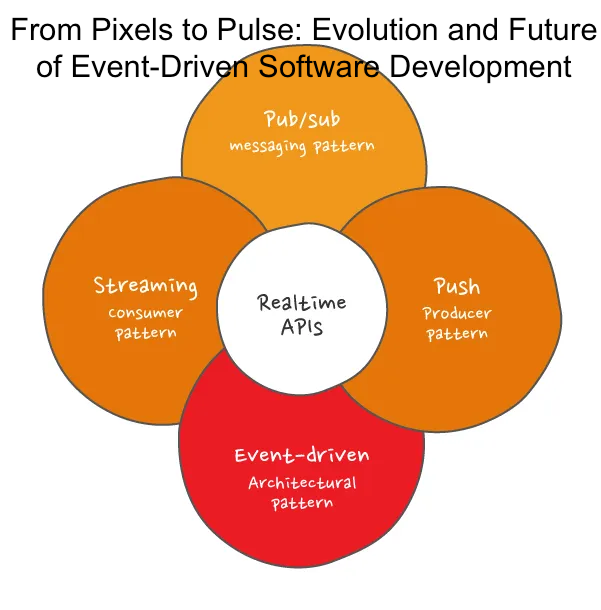
In the ever-changing landscape of software development, event-driven architecture has emerged as a powerful paradigm. Guiding applications to respond dynamically to triggers, it has evolved through history, shaping industries and user experiences. In this article, we embark on a journey through the past, present, and exciting future of event-driven software development.
Event-driven software development is an approach where the flow of a program's execution is primarily determined by events or occurrences that take place during its runtime. In this paradigm, the software responds to external or internal events by triggering corresponding actions or processes. These events can be user interactions, system events, sensor readings, data changes, or any other trigger that prompts the software to perform specific tasks.
Event-driven software is designed to be highly responsive and adaptable, allowing the program to react in real time to changing conditions. It contrasts with traditional linear programming where the sequence of actions is predefined and follows a predetermined path. Instead, in event-driven development, the software's behavior is more like a web of interactions, where events act as catalysts for actions and processes, creating a dynamic and fluid user experience.
Common examples of event-driven software include graphical user interfaces (GUIs), web applications with real-time updates, IoT applications that respond to sensor readings, and games that react to player actions. This approach is particularly useful in scenarios where the software needs to handle a multitude of asynchronous events and provide timely responses to user inputs or changing external conditions.
Principles of Event-Driven Software Development:
- Asynchronous Processing: Event-driven development thrives on asynchronous processing, where tasks don't block the execution of the program. This principle ensures that the software remains responsive to new events while handling ongoing tasks.
- Decoupling: Components in event-driven systems are loosely coupled. They interact through events without having direct dependencies on each other, enhancing modularity and maintainability.
- Publish-Subscribe Model: This model involves publishers emitting events and subscribers listening for and responding to those events. It promotes flexibility by allowing multiple subscribers to react to a single event.
- Event-Driven Architecture Patterns: Patterns like Event Sourcing, CQRS (Command Query Responsibility Segregation), and Saga patterns offer solutions for handling complex interactions, data consistency, and system scalability.
Unveiling Event-Driven Software Development: A Journey Through History and Impact
In the world of software development, where user experiences and responsiveness reign supreme, a paradigm has emerged that seamlessly orchestrates interactions like a well-choreographed dance – event-driven software development. This transformative approach has redefined how applications respond to real-world occurrences, reshaping industries and shaping digital experiences. In this blog post, we delve into the foundations, evolution, and profound impact of event-driven software development.
Understanding Event-Driven Software Development: At its core, event-driven software development revolves around one key concept: the power of events. Instead of a linear flow, applications are designed to react to events – triggers that can be anything from user actions and system notifications to data changes and external inputs. These events initiate a cascade of responses, creating dynamic and interactive software experiences that resonate with users.
A Historical Journey: The roots of event-driven software development can be traced back to the earliest graphical user interfaces (GUIs). The introduction of windows, buttons, and mouse clicks laid the foundation for event-driven interactions. However, it was the emergence of event-driven programming languages like Smalltalk in the 1970s that truly paved the way for this paradigm. These languages allowed developers to define event handlers and responses, shaping the trajectory of modern software development.
Impact Across Industries: The impact of event-driven software development reverberates across a multitude of industries, breathing life into applications in ways previously unimaginable:
- Real-Time Gaming: In the gaming industry, event-driven architecture creates immersive gameplay experiences, where every player’s action triggers a reaction, enriching storylines and creating dynamic challenges.
- Financial Agility: For the financial sector, event-driven applications enable real-time trading, fraud detection, and instantaneous responses to market shifts, elevating precision and agility.
- IoT Innovation: The Internet of Things (IoT) thrives on event-driven development, allowing devices to communicate and respond in real time, transforming homes, industries, and cities.
- E-Commerce Evolution: In e-commerce, event-driven systems deliver personalized recommendations, real-time inventory updates, and responsive customer experiences that foster brand loyalty.
Seamless User Experiences: The hallmark of event-driven software development lies in its ability to create seamless user experiences. Imagine a shopping app that updates inventory status as items are added to carts, a smart home system that responds to voice commands, or social media platforms that deliver notifications in real time. Event-driven software empowers applications to harmonize with users' actions, creating an engaging and intuitive digital world.
Embracing the Future: As technology advances, event-driven software development continues to evolve. With the rise of serverless computing, microservices, and real-time analytics, this paradigm adapts to meet the demands of an increasingly interconnected world. Edge computing, AI-driven event analysis, and IoT proliferation further expand its horizons, promising even greater innovation and responsiveness.
Evolution of Event-Driven Software Development:
The journey of event-driven software development has been marked by significant milestones that reflect its growth and adaptation to changing technological landscapes:
- Early GUIs and User Interactions:
- In the 1970s, the introduction of graphical user interfaces (GUIs) laid the groundwork for event-driven interactions. Elements like buttons, menus, and mouse clicks introduced user-triggered events.
- Smalltalk and Object-Oriented Programming:
- Smalltalk, developed in the 1970s and 1980s, introduced object-oriented programming and event-driven interaction models. Developers could define event handlers and behaviors, influencing modern programming languages.
- Client-Server Architectures:
- The client-server era of the 1990s embraced event-driven models. Applications on client machines communicated with server components through events, enabling distributed computing and remote interactions.
- Web Applications and AJAX:
- The rise of web applications introduced AJAX (Asynchronous JavaScript and XML), allowing websites to respond to user interactions without reloading the entire page. This marked a shift towards more dynamic and event-driven web experiences.
- Real-Time and IoT Boom:
- The explosion of real-time data and the Internet of Things (IoT) in the 2000s pushed event-driven development to new heights. Applications are needed to handle massive streams of events from sensors and devices in real time.
- Microservices and Serverless Computing:
- The advent of microservices architecture in the 2010s further embraced event-driven patterns. Components communicated through events, promoting modularity and scalability. Serverless computing elevated event-driven execution, allowing developers to respond directly to events without managing infrastructure.
Future of Event-Driven Software Development:
The future of event-driven software development is poised to be even more transformative, driven by advancements in technology and evolving user expectations:
- Edge Computing Integration:
- As edge computing gains prominence, event-driven applications will move closer to data sources, reducing latency and enabling quicker responses to local events.
- AI-Driven Event Analysis:
- Artificial intelligence will play a pivotal role in analyzing event streams. Machine learning models will identify patterns, anomalies, and insights within the data, enhancing decision-making and automation.
- IoT Ecosystem Expansion:
- With the IoT ecosystem continuing to grow, event-driven software will be at the heart of smart homes, cities, and industries, enabling real-time control and optimization.
- Enhanced User Engagement:
- Event-driven applications will deliver hyper-personalized experiences, responding not only to user actions but also to context and preferences, deepening user engagement.
- Cross-Platform Consistency:
- Event-driven development will enable consistent experiences across different devices and platforms, creating seamless transitions as users move between devices.
- Innovative Real-Time Services:
- Real-time services, from collaborative tools to interactive entertainment, will leverage event-driven architecture to provide new levels of interactivity and engagement.
- Blockchain and Event Transparency:
- Blockchain technology will integrate with event-driven systems, ensuring transparency and immutability in event records for industries like supply chain and finance.
A Dynamic Future Unveiled: Event-driven software development has transcended its historical roots to become a cornerstone of modern application design. With its ability to transform mundane interactions into dynamic exchanges and responsive experiences, this paradigm stands as a testament to the marriage of technology and creativity. As industries across the spectrum embrace the power of events, we stand witness to a future where applications move in synchrony with the rhythm of the world, adapting, responding, and enriching our digital lives.
A Continuously Evolving Landscape: Event-driven software development is not merely a static methodology; it's a dynamic approach that evolves alongside technology and user needs. From its origins in GUIs to its current role in IoT and real-time experiences, it continues to adapt, providing solutions to modern challenges. As event-driven applications embrace edge computing, AI, and a connected world, they set the stage for a future where software seamlessly integrates with the pulse of the digital era, crafting experiences that respond and resonate with the rhythm of life itself.
Technologies Used in Event-Driven Software Development:
- Message Brokers: Tools like Apache Kafka, RabbitMQ, and AWS SQS facilitate the efficient distribution of events between components.
- Serverless Computing: Platforms like AWS Lambda, Azure Functions, and Google Cloud Functions allow developers to execute code in response to events without managing servers.
- Event Processing Frameworks: Frameworks such as Apache Flink, Apache Storm, and Spark Streaming enable real-time processing and analysis of event streams.
- API Gateway Platforms: Tools like Amazon API Gateway and Kong manage incoming events, handle routing, and ensure secure communication.
- Event-Driven Microservices Frameworks: Frameworks like Spring Cloud Stream and Micronaut help build event-driven microservices, facilitating interaction between loosely coupled components.
- Complex Event Processing (CEP) Tools: Tools like Esper and Drools enable the detection of patterns and correlations in event streams, helping to identify meaningful trends.
- Monitoring and Observability Tools: Tools like Prometheus, Grafana, and New Relic provide insights into the performance and behavior of event-driven applications.
- Distributed Databases: Databases like Apache Cassandra and Amazon DynamoDB handle large volumes of data generated by events, providing reliable storage and retrieval.
Event-driven software development leverages these principles and technologies to create applications that respond in real-time to a wide array of events, providing dynamic and interactive user experiences while efficiently managing complex event flows and interactions.
Here's a list of tools commonly used in event-driven software development:
- Message Brokers:
- Apache Kafka: A distributed event streaming platform that facilitates the publishing and subscription of events, supporting real-time data processing and analysis.
- RabbitMQ: A robust message broker that enables the exchange of events between components using various messaging patterns.
- Amazon SQS: A fully managed message queue service provided by AWS for sending, storing, and receiving events.
- Serverless Computing Platforms:
· AWS Lambda: Allows you to run code in response to events without provisioning or managing servers.
· Azure Functions: Provides serverless computing for building event-driven solutions on Microsoft Azure.
· Google Cloud Functions: Enables the creation of single-purpose, event-driven functions in Google Cloud.
- Event Processing Frameworks:
· Apache Flink: A stream processing framework for real-time data analytics and event processing.
· Apache Storm: A distributed real-time computation system for processing continuous streams of events.
· Spark Streaming: An extension of Apache Spark for processing real-time data streams.
- API Gateway Platforms:
- Amazon API Gateway: Manages and secures APIs, allowing you to create and publish RESTful APIs for event communication.
- Kong: An open-source API gateway and microservices management layer that enables API communication and event routing.
- Event-Driven Microservices Frameworks:
- Spring Cloud Stream: A framework that simplifies building event-driven microservices using Spring Boot and Apache Kafka.
- Micronaut: A modern, lightweight microservices framework that supports event-driven architecture.
- Complex Event Processing (CEP) Tools:
- Esper: A powerful CEP engine that processes and analyzes patterns and correlations in real-time event streams.
- Drools: A business rules management system that supports complex event processing and decision management.
- Monitoring and Observability Tools:
- Prometheus: An open-source monitoring and alerting toolkit that provides insights into event interactions and performance.
- Grafana: A visualization platform that works seamlessly with Prometheus to create interactive and customizable event dashboards.
- New Relic: A monitoring and observability platform that helps in tracking and optimizing the performance of event-driven applications.
- Distributed Databases:
- Apache Cassandra: A distributed NoSQL database that can handle large volumes of event data with high availability and scalability.
- Amazon DynamoDB: A fully managed NoSQL database provided by AWS, suitable for storing and retrieving event-driven data.
These tools form a comprehensive toolkit for event-driven software development, allowing developers to build applications that respond to events in real time, handle complex interactions, and provide dynamic user experiences.
Skill Needed for Development
Developing event-driven software requires a diverse skill set that combines technical expertise, architectural understanding, and creative problem-solving. Here's a list of skills needed for successful event-driven software development:
- Programming Languages:
- Proficiency in languages such as Java, Python, Node.js, or Go, with a focus on asynchronous programming and event handling.
- Asynchronous Programming:
- Understanding of asynchronous concepts, callbacks, promises, and async/await to manage non-blocking operations effectively.
- Event-Driven Architecture:
- Deep understanding of event-driven architecture principles, including event sourcing, publish/subscribe patterns, and event handling.
- Message Brokers and Middleware:
- Familiarity with tools like Apache Kafka, RabbitMQ, or AWS SQS for event communication, queuing, and distribution.
- Serverless Computing:
- Experience with serverless platforms like AWS Lambda, Azure Functions, or Google Cloud Functions for executing code in response to events.
- Event Processing Frameworks:
- Proficiency in using frameworks like Apache Flink, Apache Storm, or Spark Streaming for real-time event processing and data streaming.
- Microservices Architecture:
- Understanding of microservices principles, including service isolation, independent deployment, and inter-service communication.
- API Design and Integration:
- Skill in designing RESTful APIs for event communication and integration between components, including authentication and authorization.
- Troubleshooting and Debugging:
- Ability to trace event flows, diagnose issues in asynchronous code, and resolve bottlenecks in event-driven systems.
- Scalability and Performance Optimization:
- Knowledge of techniques for scaling event-driven systems, optimizing performance, and managing resource usage.
- Complex Event Processing (CEP):
- Understanding of CEP concepts and tools like Esper or Drools for detecting patterns and correlations in event streams.
- Cloud Platforms:
- Familiarity with cloud platforms like AWS, Azure, or Google Cloud for deploying event-driven applications and leveraging cloud services.
- Distributed Systems:
- Proficiency in distributed computing concepts, including message distribution, data consistency, and fault tolerance.
- Monitoring and Observability:
- Skill in using monitoring tools like Prometheus, Grafana, or New Relic to gain insights into event interactions and system performance.
- Creative Problem-Solving:
- Ability to creatively design interactions, handle complex event flows, and devise solutions for unique event-driven challenges.
- Collaboration and Communication:
- Strong teamwork and communication skills to coordinate with team members, design event specifications, and align component interactions.
Event-driven software development demands a fusion of technical mastery and creative innovation, enabling developers to craft applications that elegantly respond to real-world events, providing dynamic and seamless user experiences.
Event-driven software development finds its prime application in various domains where real-time responsiveness, dynamic interactions, and adaptability are crucial. Here are the areas best suited for this development approach:
- IoT (Internet of Things):
- Event-driven architecture is essential for IoT applications where sensors and devices generate a continuous stream of data and events. It enables real-time monitoring, control, and automation in smart homes, industrial processes, and environmental monitoring systems.
- Gaming and Entertainment:
- In the gaming industry, event-driven development creates immersive experiences by responding to player actions in real time. Dynamic graphics, interactive gameplay, and multiplayer interactions heavily rely on event-driven architecture.
- Financial Services:
- Event-driven applications are essential for low-latency trading platforms, fraud detection systems, and real-time risk assessment tools. They allow financial institutions to respond swiftly to market changes and emerging opportunities.
- E-Commerce and Retail:
- Event-driven systems enhance customer experiences by providing real-time inventory updates, personalized recommendations, and timely order processing. They allow retailers to adapt to demand fluctuations and changing customer preferences.
- Telecommunications:
- Event-driven architecture is vital for managing network events, call routing, and real-time customer interactions in telecommunications systems. It ensures seamless connectivity and effective communication services.
- Healthcare and Life Sciences:
- In healthcare, event-driven systems facilitate real-time patient monitoring, alerts for critical conditions, and coordination between medical devices. They contribute to better patient care and timely interventions.
- Supply Chain and Logistics:
- Event-driven applications optimize supply chain operations by providing real-time tracking of shipments, inventory management, and alerts for delays or disruptions.
- Energy Management and Utilities:
- Event-driven systems play a role in smart grids, energy distribution, and utility management. They help in real-time monitoring of energy consumption and respond to demand fluctuations.
- Transportation and Fleet Management:
- Event-driven architecture is beneficial for tracking vehicles, managing routes, and providing real-time updates to drivers and passengers in transportation and logistics systems.
- Emergency Response and Public Safety:
- Event-driven applications enable real-time coordination and communication during emergencies, such as natural disasters or public safety incidents.
- Social Media and Content Delivery:
- Social media platforms leverage event-driven development to provide real-time updates, notifications, and interactive user experiences.
- Smart Cities and Urban Planning:
- Event-driven systems contribute to smart city initiatives by enabling real-time data collection, traffic management, and resource optimization.
In these domains and beyond, event-driven software development shines as a solution for crafting applications that resonate with the pace and dynamism of the modern world. It allows businesses and industries to adapt, respond, and innovate in real time, creating seamless and engaging experiences for users.
The evolution of event-driven software development mirrors the unceasing progress of technology itself, shaping a world where applications resonate with the rhythms of our lives. From the inception of GUIs to the boundless potential of AI-driven event analysis and edge computing, this paradigm has transcended its origins to become a cornerstone of modern software architecture. As we stand at the crossroads of innovation, the journey of event-driven development continues, promising a future where software seamlessly melds with the pulse of existence. From pixels to pulse, event-driven software development is a symphony of technology and human ingenuity, composing a narrative that responds and adapts to the ever-changing world.
Mastering Customer Engagement: The Synergy of AI, ML, Cloud, Data Analysis, and Blockchain
In a world driven by digital innovation, businesses are presented with a unique opportunity to revolutionize customer experiences. The amalgamation of Artificial Intelligence, Machine Learning, Cloud Technology, Data Analysis, and Blockchain has opened the door to crafting personalized, captivating interactions. This article unveils how these technologies converge to redefine customer engagement and drive tailored advertisements, setting new standards for customer satisfaction.
A fusion of technological luxury
In a rapidly changing digital age, businesses have an unprecedented opportunity to reshape the landscape of customer experience. The convergence of artificial intelligence (AI), machine learning (ML), cloud technology, data analytics, and blockchain has opened the door to creating deeply personal and engaging interactions. sharp. This keynote delves into the symphony woven by these technologies, transforming customer engagement and opening new models for tailored advertising, thereby creating a New standard for customer satisfaction.
Create an unforgettable customer journey: Highlighting the power of AI, ML, cloud innovation, data analytics, and blockchain

In the ever-changing digital landscape, businesses are taking an unprecedented turn to deliver unique and deeply engaging experiences. The combination of cutting-edge technologies, including AI, ML, cloud innovation, data analytics, and blockchain, has opened up a wide range of perspectives for creating ads that resonate deeply with people. In this story, we delve into the intricate nuances of each of these technologies, unleashing their synergistic transformation as they redefine how businesses interact with their customers.
The enchantment of AI and ML: Intricate weaving with precision
At the heart of the customer experience revolution, the seamless fusion of artificial intelligence and machine learning is laying the foundations for a new era. This synergy allows companies to tap into an ocean of customer data, turning it into priceless information gems. By analyzing purchase history, browsing patterns, and preferences, AI and ML algorithms turn into oracles that predict customer behavior with incredible accuracy.
Imagine a scenario where an e-commerce platform uses AI-based algorithms to discern individual customer stylistic trends. These same algorithms then come up with recommendations that perfectly match an individual's preferences, resulting in a shopping experience that's out of the ordinary. This tapestry of approach combines brevity with intricate, sharp product propositions interwoven with intricate narratives, striking a delicate balance between clear information and maze.
Unleash the potential of cloud power: Symphony of cohesion
The cloud has become a major player in driving exceptional customer experiences. Equipping businesses with the agility and scalability to handle massive streams of data in real time, the cloud is emerging as the harbinger of instant feedback and personalized services. for each customer. With the superhuman strength of a master, the cloud conveys interactions with transparency and authenticity. Equipped with the ability to store and analyze large volumes of data, the cloud promotes solid uniformity across multiple channels. Customers experience consistent service whether they communicate through the website, mobile app, or social media stage.
The art of decoding data: Navigate uncharted waters
Data analytics acts like a compass guiding companies to understand customer preferences and perfect their offerings. In a knowledge-rich data environment, the proper application of analytical tools becomes necessary to unravel these complex patterns. From gathering sentiment analysis from customer reviews to predicting trends based on historical data, data analytics is becoming the cornerstone of customer-centric strategies.
Take the example of a retail giant. With careful consideration of purchasing trends, this entity generates dynamic ads that adapt in real-time to changing trends in customer behavior. This personalized promotional tapestry promotes an immersive experience that leaves a lasting impression in the customer's mind.
Stronghold of Security and Transparency: The blockchain conundrum
Welcome to the field of blockchain technology, where the rules of security and transparency are. This cryptographic engine ensures the authenticity of customer data, instilling trust in every interaction. Showing a decentralized face, blockchain gives customers dominion over their personal information, removing privacy concerns.
In the financial sector, blockchain streamlines a transformation of the customer experience, accelerating secure transactions. Its sophisticated network streamlines the acquisition journey while storing sensitive data, creating an environment of openness and secure interaction.
Symphony of Symphony: Create customer commitments
When AI, ML, cloud technology, data analytics, and blockchain come together in a delicate symphony, they come together to create experiences that mark indelible memories in the future. customer mind. Loaded with multifaceted complexity, this combination creates dynamic advertisements that respond to individual preferences, while performing a complex ballet of disparate communications. The convergence of these technologies demonstrates a historic increase in customer engagement, brimming with ingenuity, marked by an insatiable desire to decipher, predict, and respond. meet customers' wishes.

By embracing this merger, companies are enabling a range of exceptional experiences that create lasting connections with customers in the digital age. In a landscape constrained by revolving technological advances, the fusion dance of AI, ML, cloud, data analytics, and blockchain has opened a new chapter in customer engagement. In their relentless pursuit to create harmonious experiences, these technologies serve as strongholds of innovation. This combination, which encapsulates personalization, intuitive ideas, transparent interactions, and data inviolability, weaves a mosaic that fits many of today's customers' needs.
From each personalized message chain to the labyrinthine ballet interpreting encrypted data, this fusion embodies more than just technological advancements; it demonstrates a commitment to igniting the depth of customer understanding, service, and pleasure in ways never before possible. The journey to creating extraordinary customer experiences continues, guided by the dynamic symphony of these extraordinary technologies.
Release confluence: Customer-centric change

Imagine the data stream going down: an adventure that begins with data collection, continues with the AI and ML distinction, evolves into personalization, ascends with advertising campaigns, meets the blockchain wall, and reaches the pinnacle of interaction. A journey is like a river flowing through various terrains, transforming customer interaction into an art form that only technology can coordinate. Embark on an exploration into the complex universe of modern customer interactions:
1. Data collection:
The adventure begins with collecting data from countless touchpoints – websites, apps, and social media. In this symphony of information, data becomes the foundation for creating deeply personalized experiences.
2. Distinguishing AI and ML:
Then the baton is passed to AI and ML algorithms. These algorithms decode collected data, uncovering complex patterns, biases, and trends. This interpretation paves the way for predicting customer actions and preferences with incredible accuracy.
3. Personalized:
With predictive information in tow, the cloud is deploying its agile capabilities. This celestial expanse of computing resources enables the creation of experiences tailored to each customer, a canvas where personalization grows in every pixel.
4. Create an ad campaign:
Powered by insights from data analytics, dynamic ads spring up. In a tapestry woven of imagination, these ads evolve and adapt in sync with changing customer behavior, capturing attention and driving engagement.
5. Blockchain Ancestors:
To ensure the sanctity of these personalized encounters, the overlay has been moved to blockchain. This cryptographic wall ensures data integrity, gives customers control over personal information, and leaves a trusted legacy.
6. Impact interaction:
Through a complex ballet of AI, ML, cloud, data analytics, and blockchain, customers find themselves trapped in the throes of ads tailored to their interests. This symphony unfolds as an explosion of tailored communication.
7. Customer Satisfaction:
With personalized ads and smooth interactions, satisfaction increases. Filled with joy, these experiences weave veins of loyalty, cultivating relationships that demonstrate strong loyalty and support.
8. Continuous improvement:
The veil does not fall in contentment; it is reborn with the promise of growth. Armed with the ability to adapt, these technologies continuously collect new data, refine predictions, and improve the customer experience, fueling a relentless explosion of innovation.
In this labyrinthine dance, the confluence of AI, ML, cloud technology, data analytics, and blockchain merge into one symphony, creating an explosion of personalized information and communication. Together, they redefine customer engagement, staging a work that resonates with each client's unique beat, infusing new life into the digital age.
The pinnacle of the trade: When technology synergy drives sales

The advent of AI, ML, cloud technology, data analytics, and blockchain heralded not only a development but also a symphony revolution in sales. This harmonious convergence has profound implications for trade. Here is the climax:
1. Personalized recommendations:
Using the trained eye of AI and ML, companies make tailored product recommendations. In this precision ballet, conversions skyrocket as customers discover offers that match their preferences, ushering in a veritable renaissance in sales.
2. High level of customer interaction:
Dynamic and personalized ads create an explosion in engagement. This enthusiasm grabs customers' attention, drawing them into interactions that are ready to turn simple interactions into sales-driven interactions.
3. Increase customer satisfaction:
Filled with excitement, personalized experiences are blossoming. When customers encounter personalized ads and recommendations, their interactions are gratifying, creating a source of repeat shoppers and brand ambassadors.
4. Real-time adaptability:
The cloud, the bastion of adaptability, ushers in an era of real-time policy change tailored to customer behavior. This flexibility ensures that products and campaigns remain relevant to customer preferences, coordinating sales approaches that resonate.
5. Trust and transparency:
The security and transparency of the blockchain fosters trust among customers. This unattainable guarantee incentivizes transactions, sowing fertile ground for conversions as customers are encouraged to walk through the buying area.
6. Detailed information about Data Deluge:
Data analytics becomes the backbone of insights, bringing businesses to the heart of customer behavior and preferences. This sacred guide creates precisely crafted strategies that target customer segments with surgical precision, thereby optimizing offers.
7. Arrange the long-term bonds:
As customers are captivated by special interactions and personalized experiences, the tapestry of loyalty is woven. This relationship, nurtured by these symphonic encounters, sprouts in lasting relationships that strengthen maintenance and loyalty.
8. Seize cross-selling and upselling opportunities:
These technologies open up a lot of opportunities. Leveraging customer insights, companies identify cross-sell and up-sell opportunities, aligning a seamless presentation of complementary products or premium services.
Essentially, the harmony created by AI, ML, cloud technology, data analytics, and blockchain has the potential to turn sales into a cohesive, personalized, trusting, and harmonious tone. heart. This range of experiences not only drives immediate sales but also lays the groundwork for long-term relationships, creating the pinnacle of sustained growth. With every note played, these technologies restore a sonata that will not only change the present but shape the futures of companies.
Echoes of Evolution: Notice of customer behavior change
The march of AI, ML, cloud, data analytics, and blockchain is writing new verses in the annals of customer behavior. An explosion of engagement, personalization, trust, and satisfaction is unleashed, reshaping the contours of how customers interact and respond. The symphony of transformation resounds in the following movements:
1. Enhance interaction:
Loaded with engaging personalized experiences, customers are caught in a whirlwind of interactions. This immersion encourages them to linger, enjoying interactive moments imbued with relevancy.
2. Increase the frequency of interaction:
Stimulating curiosity, the siren of personalized interactions will attract more frequent customers. Drawn by the dynamic currents that resonate with their inclinations, they embark on a journey of discovery, basking in the halo of brand exposure.
3. Journey to a quick purchase decision:
With convenience, the journey to a purchase decision is streamlined. With AI and ML-powered recommendations, customers will be able to differentiate products that reflect their preferences, shortening the decision-making journey.
4. Foster a deeper brand connection:
Bursting with resonance, the experience creates an emotional connection between the customer and the brand. This connection resonates through the corridors of time, turning into unwavering loyalty and devotion.
5. Build customer loyalty:
Filled with satisfaction, the personalized experience ignites the fire of loyalty. This loyalty fosters a pact between the customer and the brand, making the journey to discover competitors superfluous.
6. Cultivate trust and transparency:
Amid the blockchain security fortress, customers are incentivized to accept the vulnerability. Authentic, this trust opens a wide avenue for interactions, allowing companies to more accurately decipher customer preferences.
7. Pioneering new product relationships:
Filled with curiosity, dynamic advertising reveals previously unexplored paths. This series of exhibitions encourage customers to discover new offers, enriching their lives with new dimensions.
8. Navigating the wave of comments:
Loaded with information, data analytics decipher the complexities of customer psychology and preferences. This feedback loop serves as a common thread, helping companies continually refine their strategies and adapt to changing behaviors.
9. Cultivate the desire for personalization:
Brimming with interest, personalized interactive interests feed expectations. Customers anticipate tailored experiences across touchpoints, raising their standards of engagement and personalization.
10. Effects of word of mouth:
Filled with enthusiasm, satisfied customers spread their joy to their friends and family. This tidal wave of approval weaves a mosaic of brand reputation, a compelling call to attract new customers.
The combination of these technologies is creating a huge shift in customer behavior. This explosion of engagement, personalization, trust, and satisfaction transforms customers into proactive discoverers, engaged participants, and loyal followers, creating a landscape that adapts and responds to a symphony of AI, ML, cloud, data analytics, and blockchain.
Embark on your transformation journey: Industries reshaped by a symphony of technology

Many industries and products are harnessing a combination of AI, ML, cloud, data analytics, and blockchain to transform customer experiences and reshape behavior. Consider the following thumbnails:
1. E-commerce enhancement (e.g. Amazon, Netflix):
This area resonates with personalization. AI-powered recommendations drive customers on a journey to the right content and products, starting an offer-rich journey.
2. Seductive epics from social media (eg Facebook, Instagram):
A wide range of interactions flourishes here. AI streamlines feed and ads, infusing personalized dynamism into the experience and inviting customers into an irresistible realm.
3. Digital Finance Duo (e.g. PayPal, Revolut):
With full security features, blockchain makes transactions reliable. This secure platform fosters trust and encourages users to embrace the symphony of digital finance.
4. Well-choreographed caper buds (e.g. Fitbit, MyFitnessPal):
Health includes personalization. Data analytics shapes tailored fitness and nutrition advice, imbuing the user journey with a rhythmic pace of progress.
5. Transmitting harmonic tints (e.g. Spotify, YouTube):
Music and dance content personalized to the beat. AI choreographs playlists and content that reflect user tastes, an explosion of immersive experiences.
6. High fashion retail (eg: Sephora, Nike):
Conversations are geared towards personalization. AI-driven chatbots direct customers to personalized product recommendations, bringing real-time assistance into the fabric of purchase.
7. Travel's Odyssey (e.g. Airbnb, Expedia):
The journey embraces the adventure of customization. Through IA's eyes, accommodation and experiences are transformed into itineraries tailored to customer preferences.
8. In-game drama (e.g. Fortnite, League of Legends):
The game resonates with a high degree of customization. The AI modifies the gameplay, adapting the challenges to the player's skills, and mingling with the symphony of challenges.
9. Virtual companions (e.g. Siri, Google Assistant):
Commodities are growing thanks to AI and the cloud. Soaring real-time response, expert quick solutions, support, and quick satisfaction.
10. Automotive-focused innovations (e.g. Tesla, BMW):
Navigation AI draws custom routes. Self-driving capabilities offer customers a symphony of driving experiences, an evolution of the automotive story.
These illustrations explain the industries and products where the symphony of AI, ML, cloud, data analytics, and blockchain is creating an explosion in engagement, personalization, and satisfaction. satisfaction, all of which are coordinated to influence customer behavior. Through this climax, the song of transformation resounds, rewriting the story of interaction and shaping the journey ahead.
Navigating the Symphony of Technology: Create balance

As the tapestry of AI, ML, cloud, data analytics, and blockchain unfolds, companies must map out a path that walks the ropes between benefits and challenges. Seeking balance, they navigate the labyrinthine symphony using the following guiding principles:
1. Clear purpose:
A journey occurs when clarity guides the compass. Precise aiming will steer the ship, ensuring alignment with the symphony's harmonious rhythm.
2. Enlighten customer information:
Embellished with empathy, customer preferences, behaviors, and aspirations become the stars to navigate. This information lights the torch for the right experiences.
3. Synergy in technology selection:
Orchestral alignment requires choosing the right instrument. The interplay of AI, ML, cloud technology, data analytics, and blockchain must harmonize to achieve the desired peak.
4. Guardian of the Data Kingdom:
Embracing ethics, data quality, and security is a focus. Respectfully collected, stored, and analyzed resonates with transparency, a tribute to customer trust.
5. Data domain administration:
Amidst the complexity, data governance reigns supreme. Maintaining the integrity, accuracy, and confidentiality of the data becomes the harbinger of the order.
6. Virtuoso Orchestra:
With excellence, a mosaic of talents comes together. Many experts in AI, ML, data analytics, cloud technology, and blockchain bring the symphony to life.
7. Opening with a pilot:
Progress takes place in measurement steps. Start with a demo that allows you to sample the symphony, to refine the notes before they turn into a climax.
8. Symphony of Evolution:
Through fluidity, evolution is endless. Monitoring and maintaining a timely, ever-changing set of technologies ensures a continuous symphony of excellence.
9. Harmony in Change:
Switch iterative change management speed. Preparing the chorus for the upcoming tune helps reduce drag, ensuring smooth transitions.
10. Scalability Gateway:
In the growth arena, scalability is the bridge to the future. Designing scalable solutions as a foundation opens a picture for symphonic expansion.
11. Symphony of Measures:
With insights, chart your path to success with metrics. Define KPIs that measure the resonance of change, and the level of improvement.
In this unfolding symphony, companies navigate the orchestral tone, orchestrating a harmonious balance between flourishing profits and overcoming challenges. With these guiding principles in mind, they use AI, ML, cloud technology, data analytics, and blockchain to create a symphony of excellence.
In the annals of commerce and customer interaction, the confluence of AI, ML, cloud, data analytics, and blockchain marks a culmination of transformation. This symphony of technology weaves a complex tapestry of engagement, personalization, trust, and satisfaction, a tone that shapes customer behavior, transcending fantasy.
As companies navigate this symphony, they will discover that the magic lies not only in the power of technology but also in the symphony's harmonious balance. The interplay of interests and challenges, opportunities and complexity resonate as a continuum that drives innovation, nurtures relationships, and drives growth. By embracing this symphony, companies celebrate their legacy of progress, painting their stories with innovation, influence, and lasting resonance.
Leveraging AI, ML, cloud, data analytics, and blockchain to improve customer experience and impact behavior, each with pros and cons:
Pros:
1. Personalization:
Filled with relevancy, a personalized experience builds customer engagement, satisfaction, and loyalty.
Customers feel valued when their preferences are considered.
2. Efficiency:
Full of optimization algorithms, AI and ML can automate processes, analyze large-scale data, and make real-time predictions, making businesses more efficient.
3. Data-driven information:
Fully informed, data analytics provide valuable insights into customer behaviors, preferences, and trends, guiding informed decision-making and strategy development.
4. Impact interaction:
Filled with interactions, dynamic ads, and personalized experiences capture customers' attention, leading to longer interactions and increased chances of conversion.
5. Security and transparency:
Brimming with trust, blockchain technology ensures secure and transparent transactions, enhancing customers' trust in sharing their data and making purchases online.
6. Innovation:
Brimming with creativity, these technologies drive continuous innovation, allowing companies to stay ahead of their competitors and adapt to changing customer expectations.
7. Customer loyalty:
Extensive connectivity, personalized experiences, and enhanced interactions drive strong customer loyalty, leading to repeat business and positive word of mouth.
Cons:
1. Complicated in implementation:
Full of complexity, integrating these technologies requires expertise, resources, and infrastructure. Companies may face deployment and maintenance challenges.
2. Data security issues:
Due to its sensitive nature, the collection and analysis of customer data can raise privacy concerns. Businesses must ensure proper data protection measures to maintain trust.
3. Initial investment:
Given the high costs, the adoption and deployment of these technologies can be financially demanding. Small businesses can find it difficult to purchase the necessary infrastructure.
4. Algorithm Deviation:
Brimming with fairness issues, AI and ML algorithms can exhibit biases if not properly designed and trained. This can lead to unintended discriminatory outcomes.
5. User resistance:
Faced with adaptation challenges, some customers may be reluctant to adopt new technologies or concerned about the level of customization, leading to reluctance to participate.
6. Technology dependencies:
Overwhelmed with addiction, businesses are becoming heavily reliant on technology to attract customers. This dependency can become an inconvenience if the system crashes or has downtime.
7. Error:
Full of unpredictability, AI and ML predictions may not always be accurate, leading to inappropriate recommendations and potentially frustrating customer experiences.
An approach that leverages AI, ML, cloud, data analytics, and blockchain offers many benefits to improve customer experience and impact behavior but also poses challenges that businesses face. must face to face. case to be resolved. A balanced execution strategy that takes into account these pros and cons is key to achieving good results.

Deploying a solution that leverages AI, ML, cloud, data analytics, and blockchain to improve customer experience and impact behavior requires meticulous planning and execution. meticulous. Here are some best practices to consider.
1. Set clear goals:
Full of clarity, clearly define your goals and objectives to implement the solution. Whether it's improving personalization, increasing customer engagement, or driving sales, well-defined goals guide your strategy.
2. Discover customer needs:
Exploding empathy, and deeply understanding customer preferences, behaviors, and weaknesses. This information will help you customize your solution to deliver value and meet their expectations.
3. Select appropriate technology:
With the right fit, choose the technologies that best suit your goals and the needs of your customers. Ensure AI, ML, Cloud, Data Analytics and Blockchain components work in sync to achieve desired results.
4. Data Quality and Security:
Respect ethics, prioritize data quality, and ensure strong security measures. Collect, store, and analyze customer data in an ethical, transparent, and secure manner, in compliance with applicable regulations.
5. Data management:
Overwhelm the organization by establishing data governance practices to maintain data accuracy, integrity, and security. Clearly define data management roles and responsibilities.
6. Building a capable team:
With full expertise, assemble a skilled and diverse team with expertise in AI, ML, data analytics, cloud technology, and blockchain. Collaboration between professionals is crucial for successful implementation.
7. Start with a driver:
To be on the safe side, start with a pilot rollout or at a smaller scale to test the solution's effectiveness and identify challenges before scaling.
8. Constantly learning and improving:
Overwhelmed by growth, set up a feedback loop to continuously learn from customer interactions and adapt solutions based on changing behaviors and preferences.
9. Addressing Algorithm Trend:
Brimming with fairness proactively corrects algorithmic deviations by regularly testing and refining AI and ML models to ensure they don't inadvertently discriminate against certain groups.
10. Customer education:
Be transparent, and educate customers on how their data will be used and what benefits they can expect from the solution. Building trust through clear communication is important.
11. Change management:
Full of adaptability, prepare your organization and employees for the changes the new solution will bring. Training and clear communication can help reduce resistance.
12. Scalability:
With growth potential, design solutions at scale to support increased data volumes and user interactions as your business grows.
13. Regular monitoring and maintenance:
Be careful, continuously monitor the solution's performance and resolve any issues promptly. Regularly update and maintain the technology stack to ensure optimal functionality.
14. Measure and analyze results:
With complete information, set up key performance indicators (KPIs) to measure the success of your solution. Regularly analyze data to track progress toward your defined goals. By following these best practices, companies can successfully deploy solutions that leverage AI, ML, cloud, data analytics, and blockchain to improve customer experience, drive change in their behavior, and ultimately achieve their strategic goals.
In a landscape defined by rapid technological advancements, the synergy of AI, ML, Cloud Technology, Data Analysis, and Blockchain has ushered in a new era of customer engagement. As businesses strive to create experiences that resonate, these technologies stand as pillars of innovation. The fusion of personalization, predictive insights, seamless interactions, and data security forms a tapestry that caters to the diverse needs of today's customers. With each burst of personalized advertisements and every perplexing data analysis, a deeper connection is forged. This convergence represents more than just technological progress; it's a testament to the commitment to understanding, serving, and delighting customers in ways that were once only imaginable. The journey towards crafting exceptional customer experiences continues, guided by the dynamic symphony of these remarkable technologies.
Unmasking SQL Injection: Safeguarding Your Data in a Digital Age
In the realm of cybersecurity, the lurking menace of SQL injection poses a grave threat to digital systems. Unravels the complexities of SQL injection, highlighting its potential dangers and offering effective strategies to shield your data from its insidious grasp.
Unveiling SQL Injection: A Stealthy Threat Lurking in the Digital Shadows
One term that consistently sends shivers down the spines of security experts is "SQL injection." This subtle yet potentially devastating attack vector has the potential to compromise sensitive data, breach confidentiality, and wreak havoc on digital systems. In this blog post, we'll delve into the intricacies of SQL injection, understand its dangers, and explore effective strategies to safeguard against this malicious threat.
SQL injection is a type of cyberattack where malicious actors exploit vulnerabilities in an application's input validation to manipulate or execute unintended SQL queries against a database. This occurs when an application does not properly sanitize or validate user-provided input that is used in constructing SQL queries. As a result, attackers can inject malicious SQL code into the application's input fields, tricking the application into executing unintended actions on the database.
Here's how SQL injection works:
- Vulnerable Input: An application interacts with a database using SQL queries. If the application does not properly validate or sanitize user inputs, it becomes vulnerable to SQL injection.
- Malicious Input: An attacker submits input containing specially crafted SQL code within the application's input fields, such as a login form or search box.
- Manipulating Queries: The attacker's input is concatenated with the application's SQL query without proper validation. If the attacker's input is not sanitized, the SQL query becomes altered and potentially malicious.
- Executing Malicious Code: If successful, the manipulated query can lead to unintended actions, such as extracting sensitive data, modifying the database, or even deleting data. This can compromise the confidentiality, integrity, and availability of the data.
Types of SQL Injection Attacks:
- Classic SQL Injection: Attackers inject malicious SQL code into input fields to manipulate the application's database queries. For example, in a login form, attackers might use ' OR '1'='1 as input to bypass authentication.
- Blind SQL Injection: Attackers exploit vulnerabilities without directly seeing the results of their actions. They inject code that evaluates to true or false, allowing them to infer information based on the application's responses.
- Time-Based Blind SQL Injection: Attackers introduce delays into queries to determine whether certain conditions are met. They can infer information by measuring the time it takes for the application to respond.
- Out-of-Band SQL Injection: Attackers use alternative communication channels, like DNS requests, to extract data from the database, bypassing traditional methods.
The Anatomy of SQL Injection:
At its core, SQL injection is a technique used by cybercriminals to exploit vulnerabilities in applications that rely on SQL (Structured Query Language) for database communication. The attack occurs when an attacker injects malicious SQL code into an application's input fields, manipulating the way the application interacts with its underlying database. This enables the attacker to manipulate, disclose, or even delete data stored within the database.
Understanding the Danger:
The dangers posed by SQL injection are multi-faceted and far-reaching. From unauthorized access to confidential data to system-wide disruptions, the repercussions can be severe. Imagine a scenario where an e-commerce website is targeted: an attacker could exploit SQL injection to gain unauthorized access to customer information, including names, addresses, and payment details. This not only erodes customer trust but also exposes the business to legal and financial liabilities.
Safeguarding Against SQL Injection:
- Input Validation and Sanitization: The first line of defense is proper input validation and sanitization. Applications should rigorously validate user input to ensure that only permissible characters and formats are accepted. Implementing input sanitization mechanisms such as whitelisting and blacklisting can significantly reduce the risk of SQL injection.
- Prepared Statements: Leveraging prepared statements or parameterized queries is a potent strategy against SQL injection. These techniques separate SQL code from user input, making it virtually impossible for attackers to inject malicious code. Parameterized queries ensure that user input is treated as data rather than executable code.
- Stored Procedures: Utilizing stored procedures add a layer of security. By predefining SQL queries within the database, applications can call these procedures without directly embedding user inputs in the queries. This reduces the attack surface for SQL injection.
- Web Application Firewalls (WAFs): Deploying Web Application Firewalls can help identify and block malicious SQL injection attempts in real time. WAFs analyze incoming traffic, detect patterns consistent with attacks, and prevent unauthorized database access.
- Regular Patching and Updates: Keeping both the application and its underlying components up to date is crucial. Developers should consistently monitor and patch vulnerabilities to mitigate potential entry points for attackers.
Preventing SQL Injection:
- Parameterized Queries: Use parameterized queries or prepared statements provided by programming languages and frameworks. These automatically escape user input, making it much harder for attackers to inject malicious code.
- Input Validation: Validate and sanitize user inputs before using them in SQL queries. Reject inputs that don't meet expected formats or lengths.
- ORMs (Object-Relational Mapping): Use ORM libraries that handle database interactions without exposing raw SQL to the application.
- Least Privilege: Limit database user permissions to only what's necessary. Avoid using overly privileged accounts in the application's connection settings.
- Web Application Firewalls (WAFs): Implement WAFs that can detect and block SQL injection attempts.
- Regular Updates: Keep software, frameworks, and libraries up-to-date to patch known vulnerabilities.
- Security Audits: Regularly perform security assessments and penetration testing to identify and address vulnerabilities, including SQL injection.
By understanding and mitigating SQL injection risks, developers can protect applications and databases from unauthorized access and data breaches.
SQL injection remains a menacing threat that can undermine the integrity of digital systems and jeopardize sensitive data. By understanding the mechanics of this attack, recognizing its dangers, and implementing robust security measures, individuals and organizations can fortify their defense against SQL injection and navigate the digital realm with greater confidence. Remember, the battle against cyber threats is ongoing, and staying informed and proactive is the key to staying one step ahead of the adversaries.
As our digital landscape continues to evolve, the shadow of SQL injection looms large over our interconnected world. The intricacies of this attack once shrouded in mystery, now stand unveiled. With a clear understanding of the dangers it poses, we can arm ourselves with knowledge and take proactive steps to guard against its nefarious intents.
In a world where data is the lifeblood of businesses and individuals alike, the importance of cybersecurity cannot be overstated. By implementing robust practices such as input validation, prepared statements, and regular updates, we erect formidable barriers against SQL injection and its ilk. Remember, the journey toward digital security is ongoing; each proactive measure is a step toward a safer digital ecosystem.
Let us forge ahead with vigilance, fortified by the understanding that while the threat of SQL injection may persist, our commitment to safeguarding our digital realm remains unyielding. Together, we can navigate the intricate maze of cyber threats, preserving the integrity of our data and the trust of those who depend on us.
Unveiling the Evolution and Significance of Databases: Navigating the Digital Realm

Embark on a journey through the dynamic landscape of databases in our data-driven world. From their inception to their contemporary relevance, this blog post explores the intricacies of databases, their diverse types, and their indispensable role in shaping modern technology.
The Evolution and Importance of Databases: Empowering the Digital World
In the age of information, databases play a pivotal role in organizing and managing data, powering countless applications and services that we use in our daily lives. From simple spreadsheets to complex distributed systems, databases have evolved significantly over time. In this blog post, we will delve into the concept, types, evolution, current and future state, uses, and the utmost importance of databases to users.
Understanding Databases
A database is a structured collection of data that is organized, stored, and managed to facilitate data retrieval and manipulation efficiently. Databases act as repositories where data can be accessed, added, updated, or deleted in a controlled and secure manner. They serve as the foundation for various applications, from websites to mobile apps and enterprise systems, providing a way to store and retrieve data on demand.
At its core, a database is a structured system for efficiently storing, organizing, and retrieving data. It works by utilizing a defined structure, often in the form of tables, to store data in a way that allows for easy and optimized access.
Here's a simplified explanation of how a database works:
- Data Structure: A database employs a structured format to organize data. This structure typically involves tables, each resembling a spreadsheet, with rows representing individual records and columns representing different attributes or fields of the data.
- Data Entry: Users or applications insert data into the database by creating new records in the appropriate tables. Each piece of information is placed in its designated field within a record.
- Data Retrieval: When information is needed, users or applications send queries to the database. Queries are requests for specific data or specific conditions that the database should satisfy. The database system processes these queries to retrieve the requested information.
- Query Processing: The database management system (DBMS) interprets the queries and determines the most efficient way to retrieve the requested data. It uses various techniques like indexing and optimization algorithms to speed up the process.
- Indexing: Databases often create indexes, which are like the index in a book, to facilitate quick access to specific pieces of data. These indexes point to the location of data in the database, making retrieval faster.
- Data Manipulation: In addition to retrieval, databases allow for data manipulation, including updating, deleting, and inserting records. The DBMS ensures that these operations maintain data integrity and consistency.
- Data Integrity and Security: Databases enforce rules and constraints to maintain the accuracy and integrity of data. They also offer security features to control access, ensuring that only authorized users can interact with the data.
- Data Relationships: In relational databases, data can be linked between tables through relationships. For example, a customer's information in one table can be related to their orders in another table through a common identifier, enabling more complex queries and analyses.
- Scaling and Performance: Databases can be scaled horizontally (adding more servers) or vertically (upgrading hardware) to handle increasing amounts of data and user demands. Performance optimization techniques are applied to ensure efficient processing even as data grows.
- Backup and Recovery: Databases provide mechanisms for backing up data regularly to prevent loss due to hardware failures or other issues. In case of data loss, recovery mechanisms help restore the database to a previous state.
In essence, a database acts as a reliable, organized repository for data, ensuring that it can be stored, accessed, and manipulated efficiently while maintaining data integrity and security. Modern databases come in various types, from traditional relational databases to more flexible NoSQL databases, each tailored to different data storage and retrieval needs.
The architecture of a database refers to the overall structure and components that work together to manage, store, and retrieve data efficiently. Different types of databases may have varying architectures, but a general overview of a typical database architecture includes the following components:
- Database Management System (DBMS): The heart of the architecture, the DBMS is software that controls and manages the database. It provides tools and interfaces for users and applications to interact with the data. The DBMS handles tasks such as data storage, retrieval, security, data integrity, and query optimization.
- Storage Engine: This component is responsible for physically storing and retrieving data on storage devices (like hard drives or solid-state drives). It manages how data is written to disk, how indexes are stored, and how data is read back into memory when needed.
- Query Processor: When a query is submitted to the database, the query processor interprets and optimizes the query. It determines the most efficient way to retrieve the requested data by considering indexes, data distribution, and other optimization techniques. The query processor also ensures that data returned from queries is accurate and consistent.
- Transaction Manager: Databases support transactions, which are sequences of operations that are treated as a single unit of work. The transaction manager ensures that transactions are executed in a way that maintains data integrity and consistency, even in the event of system failures.
- Buffer Manager: The buffer manager is responsible for managing the movement of data between the database and memory (RAM). It caches frequently accessed data in memory to improve query performance, reducing the need to constantly read from disk.
- Concurrency Control: When multiple users or applications access a database simultaneously, concurrency control ensures that transactions do not interfere with each other. It manages locks and access rights to prevent conflicts and maintain data integrity.
- Database Catalog/Metadata: The database catalog stores metadata, which is data about the structure and organization of the database. It contains information about tables, columns, indexes, permissions, and other database objects. The metadata is used by the DBMS to manage the database effectively.
- Security and Authentication: This component handles user authentication, access control, and data security. It ensures that only authorized users can access specific data and perform certain actions within the database.
- Backup and Recovery: The architecture includes mechanisms for creating backups of the database's data and metadata. In case of data loss due to hardware failures or other issues, recovery tools can restore the database to a previous state using the backup copies.
- Communication Interface: Databases often interact with various applications and users. The communication interface facilitates connections between these external components and the DBMS.
- Data Access Layer: In some architectures, a data access layer provides an abstraction between the application and the database. This layer translates application-specific data requests into database queries and handles interactions with the DBMS.
The database architecture is designed to provide efficient data storage, retrieval, manipulation, and management while ensuring data integrity, security, and availability. Different database systems may have variations in these components based on their design and purpose.
Types of Databases
There are several types of databases, each designed to cater to specific use cases:
- Relational Databases: The traditional SQL-based databases that use tables, rows, and columns to store data. They provide a structured approach and ensure data integrity through the use of constraints.
- NoSQL Databases: These databases have gained popularity due to their flexible schema and ability to handle large volumes of unstructured or semi-structured data. They come in various forms, including document, key-value, column-family, and graph databases.
- In-Memory Databases: These databases store data in the system's RAM, enabling faster access times and better performance for applications that require real-time data processing.
- Distributed Databases: These databases are designed to handle massive amounts of data across multiple servers or data centers. They provide high availability, scalability, and fault tolerance.
Evolution of Databases
Databases have come a long way since their inception. Early systems were simple, flat-file databases that lacked structure and required extensive manual management. The introduction of the relational model in the 1970s revolutionized data storage and retrieval, paving the way for SQL-based databases.
In recent years, the rise of NoSQL databases addressed the need for more flexible and scalable solutions. Additionally, cloud databases have emerged, allowing users to leverage the power of the cloud for data storage and management without worrying about infrastructure maintenance.
Current State and Uses
Today, databases power an endless array of applications across various industries:
- E-Commerce: Online shopping platforms utilize databases to manage product catalogs, customer profiles, and transaction records.
- Social Media: Social networks rely on databases to handle vast amounts of user-generated content, profiles, and social connections.
- Finance: Banks and financial institutions use databases for managing customer accounts, transactions, and fraud detection.
- Healthcare: Electronic Health Record (EHR) systems rely on databases to store and manage patient data securely.
- IoT: The Internet of Things (IoT) ecosystem relies on databases to store and analyze sensor data from connected devices.
Importance to the User
Databases are indispensable to users for the following reasons:
- Data Access: Databases allow users to access and retrieve data quickly and efficiently, enabling seamless user experiences in applications and services.
- Data Security: Databases implement access controls and encryption mechanisms, ensuring data security and privacy for users.
- Data Analysis: Databases support complex queries and data analysis, empowering users to gain valuable insights from their data.
- Scalability: With the advent of distributed and cloud databases, users can scale their applications to meet increasing demands without disruptions.
Future of Databases
The future of databases looks promising, driven by emerging technologies and user needs. We can expect to see:
- More Intelligent Databases: Databases that incorporate machine learning and AI for improved data analysis and automated decision-making.
- Blockchain Databases: Integrating the security and immutability of blockchain technology into databases to enhance data integrity.
- Edge Databases: Databases optimized for edge computing, catering to applications that require real-time data processing in remote locations.
Databases have become the backbone of the digital world, empowering applications and services that shape our daily lives. From their humble beginnings to their current advanced state, databases continue to evolve, adapt, and provide an essential foundation for the information age. As technology progresses, the future of databases holds exciting possibilities that will further enrich user experiences and data management across industries.
There are numerous database products available, catering to different needs, use cases, and preferences. Here are some popular database products, categorized by their types:
- Relational Databases:
- MySQL
- PostgreSQL
- Microsoft SQL Server
- Oracle Database
- IBM Db2
- MariaDB
- NoSQL Databases:
- MongoDB (Document Database)
- Cassandra (Column-family Database)
- Redis (Key-Value Store)
- Couchbase (Document Database)
- Neo4j (Graph Database)
- Amazon DynamoDB (Managed NoSQL)
- In-Memory Databases:
- Redis (also used as an in-memory cache)
- Memcached
- SAP HANA
- Distributed Databases:
- Apache Cassandra
- Amazon DynamoDB
- Google Cloud Bigtable
- Apache HBase
- Columnar Databases:
- Amazon Redshift
- Google BigQuery
- Apache HAWQ
- Time-Series Databases:
- InfluxDB
- TimescaleDB
- OpenTSDB
- NewSQL Databases:
- CockroachDB
- NuoDB
- Graph Databases:
- Neo4j
- Amazon Neptune
- OrientDB
- Document Databases:
- MongoDB
- Couchbase
- CouchDB
- Spatial Databases:
- PostGIS (for PostgreSQL)
- Oracle Spatial and Graph
- Cloud Databases:
- Amazon Aurora
- Google Cloud Spanner
- Microsoft Azure SQL Database
- Object-Oriented Databases (OODBMS):
- db4o
- ObjectDB
- XML Databases:
- eXist
- BaseX
- In-Memory Data Grids (IMDG):
- Hazelcast
- Apache Ignite
- RDBMS Emulation for NoSQL:
- YugabyteDB
- NuoDB
- Hybrid Databases:
- SAP HANA
- Altibase
Remember that the suitability of a specific database product depends on factors like the nature of your data, the scale of your application, your performance requirements, and your familiarity with the technology. It's a good practice to evaluate various options to find the database that best fits your project's needs.
General pros and cons for each category of database products. However, keep in mind that the specific pros and cons can vary depending on the exact product within each category and your specific use case.
Relational Databases:
Pros:
- Well-established, widely used, and understood.
- ACID compliance ensures data consistency and integrity.
- A mature ecosystem with many tools, libraries, and support resources.
Cons:
- Might struggle with handling massive amounts of unstructured or semi-structured data.
- Scaling can be complex and might require sharding.
NoSQL Databases:
Pros:
- Flexible schema allows the handling of diverse data types and structures.
- Excellent scalability, suitable for handling big data and high write loads.
- Can be well-suited for applications with rapidly evolving requirements.
Cons:
- A lack of standard query language (like SQL) can lead to a learning curve.
- Some NoSQL databases might not offer the same level of transactional consistency as relational databases.
In-Memory Databases:
Pros:
- Extremely fast read and write speeds due to data being stored in RAM.
- Ideal for applications requiring real-time analytics and low-latency operations.
Cons:
- Limited storage capacity compared to disk-based databases.
- Data might be lost in case of power failure or system crash unless proper data persistence mechanisms are in place.
Distributed Databases:
Pros:
- Scalability and fault-tolerance due to distributed nature.
- Suitable for handling high volumes of data and high read/write loads.
Cons:
- Complexity in managing distributed systems.
- Network latency can impact performance.
Columnar Databases:
Pros:
- Excellent performance for analytical queries on large datasets.
- Efficient compression techniques result in reduced storage requirements.
Cons:
- Might not be as effective for transactional workloads.
- Can be complex to set up and manage.
Time-Series Databases:
Pros:
- Optimized for storing and querying time-series data, such as sensor data or logs.
- Efficient indexing and compression techniques.
Cons:
- May not perform as well for non-time-based queries.
- Limited use cases beyond time-series data.
Graph Databases:
Pros:
- Excellent for handling complex relationships and graph-like data.
- Efficient traversal of relationships for queries involving connected data.
Cons:
- Might not perform as well for non-graph queries.
- Some graph databases might not scale as easily as other types.
Document Databases:
Pros:
- Flexible schema suited for applications with varying data structures.
- Easily handles semi-structured and unstructured data.
Cons:
- A lack of standardized query language can lead to a learning curve.
- Not ideal for applications heavily reliant on complex joins.
Please note that the above lists are not exhaustive, and the suitability of a particular database product heavily depends on your specific requirements, data characteristics, and technical expertise. It's recommended to thoroughly evaluate each option based on your use case before making a decision.
A high-level comparison of these database types based on various aspects. Keep in mind that the suitability of a database type depends on your specific use case, requirements, and constraints.
Relational Databases vs. NoSQL Databases:
- Data Model: Relational databases use structured tables with fixed schemas, while NoSQL databases offer flexible schema (document, key-value, etc.).
- Scalability: NoSQL databases excel in horizontal scaling and handling massive data loads. Relational databases might require complex sharding for similar scalability.
- Data Integrity: Relational databases offer strong ACID compliance, ensuring data integrity. NoSQL databases might prioritize availability and partition tolerance over strict consistency.
- Query Language: Relational databases use SQL for querying. NoSQL databases use varied query languages depending on the type.
- Use Cases: Relational databases are good for structured data and complex queries. NoSQL databases excel in handling unstructured or semi-structured data and high-velocity write operations.
In-Memory Databases vs. Distributed Databases:
- Performance: In-memory databases offer ultra-fast read and write speeds due to data residing in RAM. Distributed databases provide scalability and fault tolerance but might have higher latencies.
- Use Cases: In-memory databases are suitable for real-time analytics, caching, and low-latency applications. Distributed databases handle large-scale applications with high availability and fault tolerance requirements.
Columnar Databases vs. Time-Series Databases:
- Data Type: Columnar databases are optimized for analytical queries on large datasets. Time-series databases are tailored for efficient storage and querying of time-series data.
- Query Performance: Columnar databases excel in complex analytical queries. Time-series databases are designed for time-based queries and data pattern recognition.
- Use Cases: Columnar databases are great for business intelligence and data warehousing. Time-series databases are ideal for IoT, monitoring systems, and log analytics.
Graph Databases vs. Document Databases:
- Data Structure: Graph databases excel in modeling and querying complex relationships. Document databases store semi-structured data in documents with flexible schemas.
- Query Flexibility: Graph databases are excellent for traversing relationships and answering complex graph-based queries. Document databases handle semi-structured data well and support JSON-like documents.
- Use Cases: Graph databases are ideal for social networks, recommendation systems, and knowledge graphs. Document databases suit content management systems, catalogs, and applications with varying data structures.
It's important to note that the "best" choice depends on factors like data structure, query patterns, scalability needs, and developer familiarity. Often, hybrid approaches or using multiple database types in conjunction can yield optimal results for complex applications. Always assess your specific requirements before making a decision.
The language used to manage a database depends on the specific database management system (DBMS) you're using. Different DBMSs support different languages for managing and interacting with the database. Here are a few examples:
- SQL (Structured Query Language): SQL is a standard language used to manage and manipulate relational databases. It is used to define the structure of the database (create tables, indexes, etc.), insert, update, and retrieve data, as well as perform various administrative tasks. Most relational DBMSs, like MySQL, PostgreSQL, Microsoft SQL Server, and Oracle Database, use SQL as their primary language.
- NoSQL Query Languages: NoSQL databases often have their query languages tailored to their data models. For example, MongoDB uses a language similar to JSON for querying documents, while Cassandra uses CQL (Cassandra Query Language) for its column-family model.
- Proprietary Languages: Some database systems have their proprietary languages for management and querying. For instance, IBM Db2 has its query language called SQLPL (SQL Procedural Language).
- Programming Languages: In addition to specialized query languages, you can use various programming languages to interact with databases. Most modern programming languages have libraries or drivers that allow you to connect to databases and perform operations. For instance, you can use Python with libraries like SQLAlchemy for relational databases, or use a driver like pymongo for MongoDB.
- Web-based Interfaces: Many DBMSs provide web-based interfaces or graphical user interfaces (GUIs) that allow you to manage the database using point-and-click actions without writing code. These interfaces often generate SQL queries in the background.
Remember that the language you use will depend on the specific tasks you want to perform, the type of database you're using, and your familiarity with the language and tools available for the DBMS.
SQL (Structured Query Language) is a domain-specific language used for managing, querying, and manipulating relational databases. It provides a standardized way to interact with databases, regardless of the specific database management system (DBMS) being used. SQL is used to define the structure of the database, insert, update, and retrieve data, and perform various administrative tasks. Here's a detailed overview of SQL's command set and their explanations:
- DDL (Data Definition Language) Commands:
- CREATE TABLE: Creates a new table in the database, specifying column names, data types, constraints, and indexes.
- ALTER TABLE: Modifies an existing table, allowing you to add, modify, or delete columns, constraints, or indexes.
- DROP TABLE: Removes a table and its associated data from the database.
- CREATE INDEX: Creates an index on one or more columns of a table for faster data retrieval.
- DROP INDEX: Removes an index from a table.
- DML (Data Manipulation Language) Commands:
- INSERT INTO: Adds new rows of data into a table.
- UPDATE: Modifies existing records in a table.
- DELETE FROM: Removes rows from a table based on specified conditions.
- SELECT: Retrieves data from one or more tables. This is the heart of querying in SQL.
- DQL (Data Query Language) Commands:
- SELECT: Retrieves data from one or more tables based on specified criteria. It can also perform calculations, joins, sorting, and grouping.
- DCL (Data Control Language) Commands:
- GRANT: Provides specific privileges to users or roles, giving them access to perform certain actions on the database.
- REVOKE: Removes specific privileges from users or roles.
- TCL (Transaction Control Language) Commands:
- COMMIT: Saves changes made during the current transaction.
- ROLLBACK: Undoes changes made during the current transaction.
- SAVEPOINT: Sets a point within a transaction to which you can later roll back.
SQL Command Examples with Explanations:
CREATE TABLE:
“CREATE TABLE Customers (
CustomerID INT PRIMARY KEY,
FirstName VARCHAR(50),
LastName VARCHAR(50),
Email VARCHAR(100)
);”
This command creates a table named "Customers" with columns for CustomerID, FirstName, LastName, and Email. The PRIMARY KEY constraint ensures that each row has a unique CustomerID.
INSERT INTO:
“INSERT INTO Customers (CustomerID, FirstName, LastName, Email)
VALUES (1, 'John', 'Doe', 'john@example.com');”
This command adds a new row to the "Customers" table with the specified values for each column.
SELECT:
“SELECT FirstName, LastName
FROM Customers
WHERE LastName = 'Doe';”
This command retrieves the FirstName and LastName columns from the "Customers" table where the LastName is 'Doe'.
UPDATE:
“UPDATE Customers
SET Email = 'newemail@example.com'
WHERE CustomerID = 1;”
This command modifies the Email of the customer with CustomerID 1.
DELETE FROM:
“DELETE FROM Customers
WHERE LastName = 'Doe';”
This command removes rows from the "Customers" table where the LastName is 'Doe'.
These are just a few examples of SQL commands and their usage. SQL provides a powerful and flexible way to interact with relational databases, allowing you to manage data, retrieve information, and perform complex operations with ease.
NoSQL databases encompass a variety of database systems that use different data models and query languages. Each NoSQL database type has its way of interacting with data, and the query languages can differ significantly. Below, I'll provide an overview of query languages for some common NoSQL database types along with explanations for their commands:
MongoDB (Document Database): MongoDB uses a query language that resembles JSON-like objects. It supports a rich set of operators for querying and manipulating data.
find Retrieves documents that match specified query criteria.
“javascript
db.collection.find({ field: value });”
insert Inserts new documents into a collection.
“javascript
db.collection.insert({ field: value });”
update: Updates documents in a collection based on a query.
“javascript
db.collection.update({ field: value }, { $set: { updatedField: newValue } });”
remove: Removes documents from a collection based on a query.
“javascript
db.collection.remove({ field: value });”
Cassandra (Column-family Database): Cassandra's query language, CQL (Cassandra Query Language), is similar to SQL but designed for distributed and column-family data models.
SELECT: Retrieves data from a table.
“SELECT column1, column2 FROM table WHERE condition;”
INSERT: Adds data into a table.
“INSERT INTO table (column1, column2) VALUES (value1, value2);”
UPDATE: Modifies existing data in a table.
“UPDATE table SET column = newValue WHERE condition;”
DELETE: Removes data from a table.
“DELETE FROM table WHERE condition;”
Redis (Key-Value Store): Redis is a key-value store and doesn't use a traditional query language. Instead, it provides commands to interact with its data structures.
SET: Sets the value of a key.
“shell
SET key value”
GET Retrieves the value of a key.
“shell
GET key”
HSET: Sets the field of a hash data structure.
“shell
HSET hashKey field value”
HGET: Retrieves the value of a field in a hash.
“shell
HGET hashKey field”
Neo4j (Graph Database): Neo4j uses its query language called Cypher, specifically designed for querying graph data.
MATCH: Finds patterns in the graph data.
“cypher
MATCH (node:Label) WHERE node.property = value RETURN node;”
CREATE: Creates nodes and relationships.
“cypher
CREATE (node:Label { property: value })-[:RELATIONSHIP]->(otherNode);”
UPDATE: Modifies properties of nodes and relationships.
“cypher
MATCH (node:Label) SET node.property = newValue WHERE condition;”
DELETE: Removes nodes and relationships.
“cypher
MATCH (node:Label) WHERE condition DELETE node;”
Please note that these are just basic examples of the commands used in NoSQL query languages. The actual syntax and usage can vary depending on the specific database system you are using. Always refer to the official documentation of the respective NoSQL database for more detailed and accurate information on query languages and commands.
Managing a database involves a set of tasks and processes aimed at ensuring the integrity, availability, security, and performance of the database system. The management process includes various activities throughout the database lifecycle, from design and creation to maintenance and optimization. Here's an overview of how a database is managed:
- Database Planning and Design:
- Identify the goals and requirements of the database system.
- Design the database schema, including tables, relationships, and data types.
- Determine data storage and indexing strategies.
- Database Creation:
- Install the appropriate database management system (DBMS) software.
- Create the database using the DBMS's administrative tools or commands.
- Define tables, indexes, constraints, and other database objects.
- Data Entry and Manipulation:
- Insert, update, and delete data using SQL commands or application interfaces.
- Ensure data integrity by enforcing constraints and validation rules.
- Regularly perform data quality checks and data cleansing.
- Database Security:
- Implement access control mechanisms to restrict unauthorized access.
- Define roles and permissions for users and applications.
- Set up authentication methods, such as username-password, or more advanced methods like OAuth.
- Backup and Recovery:
- Establish regular backup schedules to protect against data loss.
- Create full and incremental backups of the database.
- Develop a recovery plan to restore data in case of system failures or disasters.
- Performance Optimization:
- Monitor database performance and identify bottlenecks.
- Use tools to analyze query execution plans and optimize slow queries.
- Tune indexes and query structures for better performance.
- Scalability:
- Plan for database growth by considering horizontal or vertical scaling options.
- Implement sharding, replication, or clustering for distributing data and load across multiple servers.
- Monitoring and Maintenance:
- Monitor system health, resource usage, and query performance.
- Regularly apply software updates, patches, and security fixes.
- Maintain database statistics and perform routine maintenance tasks.
- Data Archiving and Purging:
- Archive historical data to optimize performance and storage.
- Implement data retention policies to comply with legal requirements.
- Data Migration:
- Plan and execute data migrations when transitioning to a new database version or system.
- Ensure data consistency and integrity during migration processes.
- Disaster Recovery:
- Develop a disaster recovery plan to restore operations in case of catastrophic events.
- Test recovery procedures regularly to ensure their effectiveness.
- Documentation and Training:
- Maintain up-to-date documentation of the database schema, configurations, and procedures.
- Provide training to database administrators and users to ensure effective management.
Database management is an ongoing process that requires a dedicated team of database administrators and careful coordination to ensure the database's reliable and efficient operation over time.
There are various database management tools and software available to help manage databases efficiently. These tools provide features for tasks such as database design, administration, performance optimization, monitoring, and more. Here's a list of popular products used for managing databases:
- Database Management Systems (DBMS):
- MySQL: Open-source relational DBMS is known for its ease of use.
- PostgreSQL: Powerful open-source relational DBMS with advanced features.
- Microsoft SQL Server: Relational DBMS by Microsoft, available in various editions.
- Oracle Database: Commercial relational DBMS with enterprise features.
- MongoDB: Document-oriented NoSQL database.
- Cassandra: Column-family NoSQL database for high scalability and availability.
- Redis: In-memory data store for caching and real-time analytics.
- Neo4j: Graph database for managing and querying highly connected data.
- Database Administration and Development Tools:
- phpMyAdmin: Web-based tool for managing MySQL databases.
- pgAdmin: Feature-rich open-source administration and management platform for PostgreSQL.
- SQL Server Management Studio (SSMS): Microsoft's tool for managing SQL Server databases.
- Oracle SQL Developer: Integrated development environment for Oracle Database.
- Robo 3T: MongoDB management tool with a user-friendly interface.
- DataGrip: Multi-platform IDE for SQL, supporting various DBMSs.
- Database Monitoring and Performance Tools:
- New Relic: Monitoring and performance optimization for databases and applications.
- Datadog: Cloud-based monitoring and analytics platform.
- Prometheus: Open-source monitoring and alerting toolkit.
- SolarWinds Database Performance Analyzer: Monitors, analyzes, and optimizes database performance.
- AppDynamics: Application performance monitoring with database insights.
- Backup and Recovery Solutions:
- Veeam Backup & Replication: Comprehensive data protection and recovery solution.
- Acronis Backup: Data backup and disaster recovery software.
- Commvault: Data management and backup solution.
- Data Modeling and Design Tools:
- ER/Studio: A data modeling tool for designing, documenting, and managing databases.
- Lucidchart: Web-based diagramming tool for creating database models.
- Database Migration and Synchronization Tools:
- AWS Database Migration Service: Migrates databases to and from the AWS cloud.
- dbForge Studio: Offers database migration and synchronization tools for various DBMSs.
- Replication and Clustering Solutions:
- Galera Cluster: MySQL and MariaDB cluster for synchronous replication.
- Amazon RDS Multi-AZ: Amazon RDS feature for high availability and failover.
- Data Masking and Security Tools:
- Delphix: Data masking and virtualization platform.
- Imperva: Database security and compliance solutions.
- Query Optimization Tools:
- SQL Diagnostic Manager: Monitors and optimizes SQL queries.
- SQL Complete: Productivity and code-completion tool for SQL development.
- Database as a Service (DBaaS) Platforms:
- Amazon RDS: Managed relational database service by AWS.
- Google Cloud SQL: Fully managed relational database service by Google Cloud.
- Microsoft Azure SQL Database: Managed relational database service on Azure.
These are just a few examples of the many tools and solutions available for managing databases. The choice of tools depends on factors like the type of database, the specific tasks you need to perform, your budget, and your familiarity with the technology. Always ensure that the tools you choose are compatible with your database systems and provide the features you require.
Managing a database requires a combination of technical, analytical, and communication skills to ensure its efficient operation, security, and performance. Here's a list of skill sets that are commonly required for successful database management:
- Database Fundamentals:
- Understanding of database concepts, data models, and normalization.
- Familiarity with relational and NoSQL database types and their differences.
- SQL Proficiency:
- Strong command of SQL (Structured Query Language) for querying, manipulating, and managing data.
- Ability to write complex SQL queries, optimize queries, and troubleshoot performance issues.
- Database Design:
- Knowledge of database design principles, entity-relationship diagrams, and normalization.
- Ability to design tables, indexes, constraints, and relationships to ensure data integrity.
- Database Administration:
- Experience in creating, configuring, and maintaining databases using the chosen DBMS.
- Proficiency in managing users, roles, permissions, and security settings.
- Backup and Recovery:
- Understanding backup strategies, scheduling backups, and performing data recovery.
- Familiarity with tools and processes for data backup and disaster recovery.
- Performance Optimization:
- Ability to monitor database performance using tools and optimize slow queries.
- Knowledge of indexing, query execution plans, and performance tuning techniques.
- Security Management:
- Expertise in implementing access controls, authentication, and authorization mechanisms.
- Knowledge of security best practices to prevent SQL injection, data breaches, and unauthorized access.
- Monitoring and Maintenance:
- Proficiency in monitoring system health, resource usage, and database metrics.
- Experience in applying software updates, patches, and security fixes.
- Problem Solving:
- Strong analytical skills to identify and resolve database-related issues.
- Ability to troubleshoot errors, performance bottlenecks, and connectivity problems.
- Scripting and Automation:
- Knowledge of scripting languages (e.g., Python, PowerShell) to automate routine tasks.
- Familiarity with scheduling jobs and tasks for database maintenance.
- Data Migration and Integration:
- Experience in migrating data between databases and systems.
- Ability to integrate databases with applications and external data sources.
- Communication and Collaboration:
- Effective communication skills to interact with developers, stakeholders, and team members.
- Collaboration skills to work with cross-functional teams and manage database-related projects.
- Continuous Learning:
- Willingness to stay updated with the latest database technologies, trends, and best practices.
- Ability to adapt to new tools and techniques as the database landscape evolves.
- Vendor-Specific Knowledge:
- Depending on the database management system you're using (e.g., MySQL, PostgreSQL, MongoDB), familiarity with the specific features, tools, and commands of that system is important.
Database management is a multifaceted role that requires a combination of technical expertise, problem-solving abilities, and effective communication to ensure the database's optimal performance, security, and usability.
Database Administration Best Practices:
- Regular Backups:
- Establish automated backup schedules to prevent data loss and ensure recovery points.
- Monitoring and Performance Tuning:
- Monitor database performance using tools, identify bottlenecks, and optimize queries.
- Security Measures:
- Implement strong authentication, authorization, and encryption mechanisms.
- Regularly apply security patches and updates to protect against vulnerabilities.
- Access Control:
- Assign roles and permissions to users, granting only the necessary access.
- Data Integrity:
- Enforce constraints, validation rules, and proper data types to maintain data integrity.
- Scalability and Availability:
- Design for scalability by using techniques like sharding, replication, and load balancing.
- Implement failover mechanisms for high availability.
- Regular Maintenance:
- Schedule routine maintenance tasks, including index rebuilding, data purging, and optimizing storage.
- Documentation:
- Maintain up-to-date documentation of the database schema, configurations, and procedures.
- Disaster Recovery Plan:
- Develop a comprehensive disaster recovery plan and periodically test its effectiveness.
- Continuous Learning:
- Keep up-to-date with the latest database trends, tools, and best practices through training and industry resources.
- Performance Testing:
- Conduct regular performance testing to identify and address potential bottlenecks before they impact users.
- Capacity Planning:
- Monitor resource usage and plan for capacity growth to avoid unexpected limitations.
- Version Control:
- Keep track of changes to database schema and configurations using version control systems.
- Regular Auditing:
- Perform security audits and compliance checks to ensure the database meets regulatory requirements.
Choosing the right database and effectively administering it requires careful consideration, planning, and ongoing vigilance. Following these best practices will help you maintain a reliable, performant, and secure database environment.
Selecting the right database and effectively managing it are critical for the success of your application or project. Here's a comprehensive approach to selecting a database and best practices for its administration:
Database Selection:
- Assess Your Needs:
- Identify your project's requirements, including data volume, structure, read/write patterns, and scalability needs.
- Understand Data Model:
- Determine whether your data fits well into a relational schema or requires a NoSQL data model like document, key-value, graph, etc.
- Consider Use Cases:
- Evaluate the specific use cases your application will support, such as analytics, real-time processing, or content management.
- Performance Considerations:
- Consider factors like read and write speeds, latency, and the need for high availability.
- Scalability Requirements:
- Determine if your application needs to scale horizontally or vertically and if the chosen database can support that.
- Budget and Resources:
- Consider the cost of licensing, hardware, and maintenance, as well as your team's expertise with the chosen database.
- Security and Compliance:
- Ensure the database meets security and compliance requirements, including data encryption, access controls, and auditability.
- Evaluate Options:
- Research and compare different database products within the chosen category (relational, NoSQL, etc.).
- Prototyping and Testing:
- Create prototypes using potential databases to assess how they perform with your data and use cases.
- Vendor Support:
- Evaluate the quality of vendor support, documentation, and community resources.
The ideal database for an organization depends on various factors, including the organization's size, industry, use cases, data requirements, budget, and technical expertise. Here's a general guideline to help you match different types of databases with suitable organizational scenarios:
- Relational Databases (RDBMS):
- Ideal for: Organizations with structured data, transactional systems, well-defined schemas, and complex queries.
- Examples of suitable industries: Finance, e-commerce, inventory management, and customer relationship management (CRM).
- Document Databases:
- Ideal for: Organizations dealing with semi-structured or unstructured data, and requiring flexible schemas for evolving data.
- Examples of suitable industries: Content management systems, and e-commerce platforms with varying product attributes.
- Key-Value Stores:
- Ideal for: Organizations requiring fast data retrieval based on simple key-based lookups, caching, and session management.
- Examples of suitable industries: Real-time analytics, user session storage, and simple data storage.
- Column-family Databases:
- Ideal for: Organizations handling large amounts of data that require high write and read performance.
- Examples of suitable industries: Time-series data analysis, log storage, and big data analytics.
- Graph Databases:
- Ideal for: Organizations with complex data relationships and needing efficient traversals for data analysis and recommendation systems.
- Examples of suitable industries: Social networks, recommendation engines, and fraud detection.
- Time-Series Databases:
- Ideal for: Organizations dealing with time-stamped data, sensor data, logs, and needing efficient time-based queries.
- Examples of suitable industries: IoT applications, monitoring systems, financial trading.
- In-Memory Databases:
- Ideal for: Organizations needing extremely fast read and write speeds, real-time analytics, and low-latency applications.
- Examples of suitable industries: High-frequency trading, real-time dashboards, and gaming.
- Distributed Databases:
- Ideal for: Large-scale organizations requiring high availability, fault tolerance, and the ability to handle massive data loads.
- Examples of suitable industries: Large e-commerce platforms, social media networks, and cloud-based services.
It's important to note that the choice of the database should be based on a thorough assessment of the organization's unique requirements, technical capabilities, and future growth plans. Sometimes, a combination of databases (polyglot persistence) is necessary to handle different data types and use cases within an organization. Consulting with database experts and conducting a detailed analysis of your organization's needs is essential for making the right decision.
Several databases are widely used across different industries and applications. Here are some of the most commonly used databases:
- MySQL: A popular open-source relational database management system (RDBMS) known for its ease of use, reliability, and performance. It's used in various web applications, content management systems, and small to medium-sized projects.
- PostgreSQL: Another powerful open-source RDBMS is known for its advanced features, extensibility, and support for complex queries. It's often chosen for applications that require scalability and data integrity.
- Microsoft SQL Server: A widely used commercial RDBMS by Microsoft, known for its robust features, security, and integration with Microsoft products. It's common in enterprises and Windows-based environments.
- Oracle Database: A commercial RDBMS by Oracle Corporation, known for its scalability, high availability, and support for large-scale applications. It's commonly used in enterprise-level applications.
- MongoDB: A leading NoSQL document-oriented database known for its flexibility and scalability. It's widely used for handling unstructured or semi-structured data in applications like content management, real-time analytics, and more.
- Redis: An in-memory data store used for caching, real-time analytics, and session management due to its high-speed read-and-write operations.
- Cassandra: A distributed NoSQL database designed for high availability, scalability, and fault tolerance. It's commonly used for handling large amounts of data across distributed clusters.
- Elasticsearch: A distributed, RESTful search and analytics engine commonly used for full-text search and real-time data analysis.
- SQLite: A self-contained, serverless RDBMS that is often embedded within applications. It's used in mobile apps, desktop software, and small-scale applications.
- Amazon DynamoDB: A managed NoSQL database service offered by Amazon Web Services (AWS). It's used for applications requiring scalability and low-latency access.
- Neo4j: A popular graph database used for applications that require modeling and querying complex relationships, such as social networks and recommendation systems.
- Microsoft Access: A desktop database management system often used for small-scale applications and projects.
In the grand tapestry of technological progress, databases stand as the steadfast pillars upon which our digital world is built. From their modest origins to their current sophistication, databases have ceaselessly adapted to the ever-changing needs of humanity. As we peer into the horizon of possibilities, it's evident that databases will continue to evolve, embedding artificial intelligence, blockchain security, and edge computing into their fabric. The symphony of data they orchestrate empowers industries, fuels innovation, and shapes the contours of our digital landscape. So, as we navigate the intricacies of the information age, let us not forget the unsung heroes silently orchestrating the harmony of our interconnected world – the databases that tirelessly serve as the backbone of our digital dreams.
Unraveling the Power of Software-Defined Networking (SDN): Past, Present, and Future

In the dynamic realm of networking, Software-Defined Networking (SDN) has emerged as a transformative force, redefining how networks are managed and operated. This blog post delves into the evolution, current state, and promising future of SDN, highlighting its advantages and potential challenges.
Software-Defined Networking (SDN): Revolutionizing the Future of Networking
In recent years, the networking landscape has witnessed a significant transformation with the advent of Software-Defined Networking (SDN). SDN has emerged as a groundbreaking approach that decouples network control from the underlying hardware, enabling a more flexible, agile, and programmable network infrastructure. In this blog post, we will explore the evolution, current state, and the promising future of SDN, along with its advantages and disadvantages.
Evolution of SDN:
The concept of SDN was first proposed in the mid-2000s as a response to the limitations of traditional network architectures. Early efforts focused on centralizing control and separating it from data forwarding, allowing network administrators to dynamically manage network resources. In 2008, OpenFlow, a crucial SDN protocol, was introduced, paving the way for SDN's practical implementation.
Current State of SDN:
Today, SDN has progressed beyond its initial theoretical stages and is widely adopted in various industries. SDN technology has matured, and numerous vendors offer robust SDN solutions tailored to diverse networking environments. SDN has proven its value in data centers, wide-area networks, campus networks, and even in telecommunications and carrier-grade networks.
Advantages of SDN:
- Enhanced Network Flexibility: SDN enables organizations to swiftly adapt their networks to changing business needs. With centralized management, administrators can implement changes and policies across the network in real time.
- Improved Scalability: SDN facilitates network expansion without the need for extensive hardware upgrades. Organizations can efficiently handle increased demand and accommodate growth.
- Cost Savings: SDN leads to cost savings by optimizing resource utilization, automating network tasks, and reducing operational expenses.
- Better Security: SDN allows for micro-segmentation, creating isolated segments within the network for improved security. Centralized policy management ensures consistent security enforcement.
- Network Automation: SDN automates mundane tasks, reducing manual interventions and human errors. Automation streamlines network management and boosts operational efficiency.
Software-Defined Networking (SDN) is an innovative approach to network management that allows administrators to control and manage network resources through software applications, rather than relying solely on traditional network hardware configurations. SDN provides a more flexible, programmable, and dynamic network infrastructure, enabling better scalability, efficiency, and agility in managing modern networks.
In a traditional network architecture, the control plane (which determines how data packets are forwarded) and the data plane (which handles the actual forwarding of packets) are tightly integrated within networking devices like routers and switches. This integration can make it challenging to adapt the network to changing demands and requirements efficiently.
However, SDN decouples the control plane from the data plane, allowing network administrators to control the entire network from a centralized software-based controller. This controller acts as the brain of the network, providing a global view of the network topology, traffic flows, and network devices. The SDN controller communicates with network devices through an open and standardized interface, typically using protocols like OpenFlow.
Here's a breakdown of the key components and benefits of Software-Defined Networking:
- SDN Controller: The central element of an SDN architecture is the SDN controller. It is responsible for managing and orchestrating network resources, collecting information about the network state, and making decisions on how traffic should be forwarded based on the applications' requirements.
- Southbound APIs: These are the interfaces used by the SDN controller to communicate with the underlying network devices in the data plane. OpenFlow is one of the most widely used southbound APIs in SDN, enabling communication and flow control between the controller and network switches.
- Northbound APIs: These interfaces enable communication between the SDN controller and the applications or network services that run on top of the SDN infrastructure. These APIs allow applications to request specific network behaviors, enabling greater programmability and automation.
Benefits of Software-Defined Networking:
- Centralized Management: SDN provides a single point of control for the entire network, making it easier to manage and configure network resources.
- Flexibility and Agility: With SDN, network administrators can quickly adapt the network to changing requirements by modifying the software rules on the SDN controller, without having to reconfigure individual network devices.
- Improved Resource Utilization: SDN enables more efficient use of network resources, optimizing traffic flows and reducing network congestion.
- Network Virtualization: SDN allows the creation of virtual networks, which enables network segmentation and isolation, improving security and resource allocation.
- Automation and Orchestration: SDN enables the automation of routine network tasks, reducing manual intervention and human errors.
- Enhanced Visibility and Monitoring: SDN provides better visibility into network traffic, allowing administrators to analyze and troubleshoot network issues more effectively.
Software-Defined Networking (SDN) revolutionizes traditional network management by providing a dynamic and programmable approach to control network resources. By separating the control plane from the data plane and using centralized software controllers, SDN offers increased flexibility, scalability, and automation, making it an essential technology in modern networking infrastructures.
Software-Defined Networking (SDN) works by decoupling the control plane from the data plane in network devices, allowing network administrators to manage and control the entire network through a centralized software-based controller.
This approach provides a more flexible and programmable way to manage network resources, making it easier to adapt to changing network requirements and improve overall network efficiency. Let's explore the key steps involved in how SDN works:
- Separation of Control Plane and Data Plane: In traditional networking, the control plane and data plane are tightly integrated within network devices like routers and switches. The control plane is responsible for making decisions on how data packets should be forwarded, while the data plane is responsible for the actual forwarding of packets. In SDN, these functions are separated.
- SDN Controller: At the heart of SDN is the SDN controller, a centralized software application responsible for managing the network. The controller acts as the brain of the network and maintains a global view of the network topology, including information about connected devices, links, and network traffic.
- Southbound APIs: The SDN controller communicates with the network devices in the data plane through southbound APIs. The most common southbound API used in SDN is OpenFlow. These APIs enable the controller to instruct the network devices on how to handle and forward data packets.
- Data Plane Devices: The network devices in the data plane, such as switches, routers, and access points, are responsible for forwarding data packets based on the instructions received from the SDN controller. These devices become "dumb" switches that only perform packet forwarding without making any decisions on their own.
- Network Intelligence in the SDN Controller: Since the SDN controller has a global view of the network, it can make intelligent decisions on how data packets should be forwarded based on various factors, such as traffic patterns, application requirements, and network policies. The controller determines the optimal paths for packets, reducing network congestion and improving overall performance.
- Northbound APIs: SDN also provides northbound APIs, which enable communication between the SDN controller and the applications or network services running on top of the SDN infrastructure. These APIs allow applications to request specific network behaviors or policies, enabling greater programmability and automation.
- Network Virtualization: SDN enables network virtualization, allowing the creation of virtual networks over the same physical infrastructure. Each virtual network can have its policies and configurations, providing better network segmentation and isolation.
- Flow Tables and Flow Rules: In SDN, the SDN controller maintains flow tables that contain flow rules. These rules specify how specific types of traffic should be treated and forwarded by the network devices. When a data packet arrives at a network device, it is matched against the flow table's rules, and the appropriate action is taken based on the match.
By leveraging these components and principles, SDN provides several benefits, including centralized management, improved network flexibility, better resource utilization, network automation, and enhanced visibility and monitoring. The separation of the control plane from the data plane and the centralized control through the SDN controller makes it easier to optimize and manage modern networks in a more efficient and scalable manner.
The architecture of Software-Defined Networking (SDN) consists of several key components that work together to enable the decoupling of the control plane from the data plane and the centralized management of the network. The SDN architecture typically includes the following components:
- SDN Controller: The SDN controller is the central element of the architecture. It is responsible for managing and orchestrating the network, providing a global view of the network topology, and making decisions on how traffic should be forwarded based on the network policies and requirements. The controller communicates with both the southbound and northbound interfaces to interact with network devices and applications, respectively.
- Southbound APIs: The southbound APIs are interfaces used by the SDN controller to communicate with the underlying network devices in the data plane. The primary southbound API used in SDN is OpenFlow, which allows the controller to instruct network switches and routers on how to handle data packets. Other southbound APIs include NETCONF (Network Configuration Protocol) and P4 (Programming Protocol-Independent Packet Processors).
- Data Plane Devices: The data plane devices are the network switches, routers, access points, and other networking equipment that perform the actual forwarding of data packets. In SDN, these devices operate in a simpler, more streamlined manner, as their decision-making process is offloaded to the SDN controller. They follow the instructions provided by the controller through the southbound API.
- Northbound APIs: The northbound APIs are interfaces that allow communication between the SDN controller and the applications or network services running on top of the SDN infrastructure. These APIs enable applications to request specific network behaviors and services from the controller, allowing for greater programmability and automation. Northbound APIs vary depending on the SDN controller implementation.
- Flow Tables and Flow Rules: Flow tables are maintained by the SDN controller and reside in the data plane devices. They contain flow rules, which specify how specific types of traffic should be handled and forwarded by the network devices. Flow rules are matched against incoming data packets, and the appropriate actions are taken based on the match. This allows for efficient and dynamic traffic management.
- Network Virtualization: SDN allows for network virtualization, which involves creating multiple virtual networks over the same physical infrastructure. Each virtual network can have its policies, configurations, and isolation, enabling better resource utilization and security.
- Management Applications: These are software applications or services that interact with the SDN controller through the northbound API to provide various network services. Examples include network monitoring, security applications, load balancers, and traffic engineering tools. Management applications can leverage the programmability and flexibility of SDN to offer innovative network services.
The SDN architecture, with its centralized control and programmable nature, provides numerous benefits, including easier network management, improved scalability, enhanced security, and the ability to adapt to changing network demands. The flexibility and separation of control from the data plane make SDN a powerful paradigm for modern network infrastructures.
In Software-Defined Networking (SDN), the hardware used includes both traditional network devices and specialized SDN-enabled devices. The hardware components in an SDN deployment can vary depending on the specific SDN architecture and the scale of the network. Here are the key hardware components typically used in an SDN environment:
- SDN Controllers: SDN controllers are software-based components and do not require specialized hardware. They can run on standard servers or virtual machines. However, for larger and more complex networks, dedicated hardware appliances or high-performance servers may be used to host the SDN controller to ensure efficient and responsive network management.
- SDN Switches: SDN switches are essential components in an SDN deployment. These switches have built-in support for SDN protocols such as OpenFlow, which allows them to communicate with the SDN controller. SDN switches are available in various form factors, including data center switches, campus switches, and even virtual switches for virtualized environments.
- SDN Routers: SDN routers are similar to SDN switches but are designed to perform routing functions in addition to packet forwarding. These routers also support SDN protocols, allowing them to receive instructions from the SDN controller for routing decisions and forwarding behavior.
- OpenFlow-Enabled Network Devices: OpenFlow is one of the most widely used southbound APIs in SDN. Therefore, any network device that supports the OpenFlow protocol can be utilized as part of an SDN deployment. This includes network switches, routers, and access points that have OpenFlow support in their firmware.
- Programmable Network ASICs: Some network equipment manufacturers offer programmable network ASICs (Application-Specific Integrated Circuits) designed explicitly for SDN. These ASICs provide the necessary flexibility to implement custom forwarding behavior and accelerate OpenFlow packet processing, resulting in improved performance and efficiency.
- SDN Gateways: SDN gateways are devices that connect the SDN environment to the traditional non-SDN part of the network. These gateways act as a bridge between the SDN and non-SDN worlds, allowing seamless integration and communication between the two.
- Network Monitoring and Packet Capture Hardware: In SDN environments, network monitoring and packet capture hardware are essential for gaining visibility into the network's performance and troubleshooting issues. These hardware components can be integrated into the SDN infrastructure to collect data and send it to the SDN controller or management applications for analysis.
It's important to note that not all hardware used in an SDN environment needs to be SDN-enabled. SDN is designed to work with existing network infrastructure, and the deployment can be gradual, incorporating SDN capabilities into the network over time.
There were several Software-Defined Networking (SDN) products available from various vendors. Here are some SDN products along with their features:
- Cisco Application Centric Infrastructure (ACI):
- Provides a policy-driven approach to network provisioning and automation.
- Offers centralized management through the Application Policy Infrastructure Controller (APIC).
- Facilitates seamless integration with existing Cisco hardware and software products.
- Allows micro-segmentation for improved security.
- VMware NSX:
- Delivers network virtualization and micro-segmentation capabilities.
- Integrates with VMware vSphere for seamless management of virtualized environments.
- Provides a distributed firewall for granular security controls at the virtual machine level.
- Supports multi-cloud networking and hybrid cloud deployments.
- Juniper Contrail:
- Offers multi-cloud networking and hybrid cloud integration.
- Provides network automation and orchestration through a centralized controller.
- Supports SD-WAN capabilities for improved branch connectivity.
- Integrates with Juniper's hardware and other networking solutions.
- HPE (Hewlett Packard Enterprise) SDN Controller:
- Offers open standards-based SDN controller for easy integration with diverse network devices.
- Provides centralized network management and automation.
- Enables seamless orchestration of physical and virtual network resources.
- Supports custom applications through open APIs.
- OpenDaylight:
- An open-source SDN controller platform hosted by the Linux Foundation.
- Offers a modular and extensible architecture to support various SDN applications.
- Supports multiple southbound and northbound protocols, including OpenFlow and REST APIs.
- Enables community-driven development and contributions.
- ONOS (Open Network Operating System):
- Another open-source SDN controller platform designed for high-performance networking.
- Supports scalability and fault tolerance for carrier-grade deployments.
- Offers a range of southbound and northbound interfaces.
- Enables the creation of custom applications and services.
- Big Switch Networks - Big Cloud Fabric:
- Provides a data center fabric for SDN-based network automation.
- Offers network automation for VMware and OpenStack environments.
- Includes a central controller for simplified management.
- Supports intent-based policies for network configuration.
- NEC ProgrammableFlow:
- Offers SDN solutions for data centers and wide-area networks.
- Provides OpenFlow-based SDN controllers and switches.
- Supports automated network provisioning and resource optimization.
- Integrates with existing network infrastructures.
Please keep in mind that this is not an exhaustive list, and there are other SDN products and solutions available in the market.
Comparing various Software-Defined Networking (SDN) products can be complex as each product has its strengths and weaknesses, and the best choice depends on specific use cases and requirements. However, I can provide a high-level comparison of some key aspects of the listed products to help you get an overview:
- Cisco Application Centric Infrastructure (ACI):
- Strengths: Offers robust policy-driven automation and integration with Cisco hardware and software products. Well-suited for large enterprises with existing Cisco infrastructure.
- Weaknesses: Proprietary solution, which may limit interoperability with non-Cisco devices. Can be complex to deploy and manage.
- VMware NSX:
- Strengths: Strong integration with VMware's virtualization products, making it a great choice for virtualized environments. Provides effective micro-segmentation for improved security.
- Weaknesses: Focused on virtualized data centers, may have limited support for non-virtualized environments. Can be costly for large-scale deployments.
- Juniper Contrail:
- Strengths: Offers multi-cloud and hybrid cloud integration. Supports SD-WAN capabilities for improved branch connectivity. Good for Juniper hardware users.
- Weaknesses: Some features may require additional licenses. Might have a learning curve for users familiar with other SDN solutions.
- HPE SDN Controller:
- Strengths: Open standards-based solution with support for diverse network devices. Offers customization through open APIs. Good for organizations seeking vendor-agnostic solutions.
- Weaknesses: Less feature-rich compared to some proprietary solutions. Requires additional components for a full SDN deployment.
- OpenDaylight:
- Strengths: Open-source and community-driven, offering flexibility and extensibility. Supports multiple protocols and integrations.
- Weaknesses: May require more effort for initial setup and customization compared to turnkey solutions. Ongoing community support may vary.
- ONOS:
- Strengths: Open-source and designed for high-performance networking. Scalable and fault-tolerant for carrier-grade deployments.
- Weaknesses: May require more advanced networking knowledge for effective deployment. Limited vendor-specific integrations compared to proprietary solutions.
- Big Switch Networks - Big Cloud Fabric:
- Strengths: Simplified network automation and integration with VMware and OpenStack environments. Intent-based policies for easier configuration.
- Weaknesses: May have less feature depth compared to some mature SDN solutions. The vendor-specific approach might not suit all environments.
- NEC ProgrammableFlow:
- Strengths: Offers SDN solutions for data centers and wide-area networks. Provides OpenFlow-based SDN controllers and switches.
- Weaknesses: Smaller market presence compared to some major vendors. Limited visibility and support compared to larger ecosystems.
When comparing SDN products, it's crucial to consider factors such as compatibility with existing infrastructure, scalability, customization needs, support, cost, and the specific use case you are addressing. Additionally, evaluating each product's vendor reputation, customer reviews, and long-term roadmap can help in making an informed decision that aligns with your organization's requirements and goals.
Disadvantages of SDN:
- Complexity: Implementing SDN can be challenging, especially for organizations with existing legacy infrastructure. Deployment and integration may require skilled expertise and careful planning.
- Interoperability: Some SDN solutions may be proprietary, limiting interoperability with non-SDN devices and vendor lock-in. Standardization efforts like OpenFlow aim to address this issue.
- Security Risks: While SDN enhances security, it also introduces new security challenges, such as potential vulnerabilities in the SDN controller and southbound APIs.
- Skill Gap: Transitioning to SDN requires network administrators to acquire new skills in programming, scripting, and SDN-specific protocols.
Future of SDN:
Looking ahead, SDN is poised to play a vital role in the future of networking. The emergence of 5G, edge computing, and the Internet of Things (IoT) will demand highly flexible and scalable networks, making SDN an ideal solution. SDN will continue to evolve, incorporating advanced technologies like Artificial Intelligence (AI) and Machine Learning (ML) to optimize network management and self-healing capabilities.
Software-Defined Networking (SDN) has undoubtedly revolutionized the networking industry, offering unprecedented flexibility, automation, and scalability. Its current widespread adoption and continuous development indicate a promising future, where SDN will continue to shape the landscape of modern networking.
While SDN brings numerous advantages, organizations must also address its challenges to harness its full potential. By embracing SDN with careful planning and investment in training, businesses can unlock a new era of networking capabilities, driving innovation and efficiency across various industries.
Software-Defined Networking (SDN) can benefit a wide range of organizations across various industries. However, certain characteristics make an organization particularly well-suited for adopting SDN.
Here are some key factors that indicate which organizations can benefit from using SDN:
- Large Enterprises: Large organizations with complex and expansive network infrastructures can benefit significantly from SDN. SDN's centralized management, automation, and scalability can help manage and optimize the vast network resources efficiently.
- Data Centers: Data centers, especially those with dynamic workloads and virtualized environments, can leverage SDN to improve network provisioning, traffic management, and resource utilization. SDN's ability to adapt to changing workloads is particularly valuable in data center environments.
- Cloud Service Providers: Cloud service providers often deal with diverse workloads and varying customer requirements. SDN enables them to offer flexible, on-demand network services and implement tenant-specific policies, enhancing their service offerings.
- Telecommunications and Service Providers: Telecommunications companies and service providers can use SDN to enhance network performance, deliver services more efficiently, and optimize bandwidth allocation to meet customer demands.
- Educational Institutions: Educational institutions, such as universities and research centers, can utilize SDN to provide isolated network segments for different departments, enhance security, and support innovative research projects.
- Businesses with Frequent Network Changes: Organizations with rapidly changing network requirements, such as those experiencing continuous growth or restructuring, can benefit from SDN's ability to adapt and reconfigure the network dynamically.
- Multi-Tenant Environments: Organizations operating in multi-tenant environments, such as co-location facilities or shared office spaces, can use SDN to create isolated virtual networks for each tenant, ensuring data privacy and security.
- IoT Deployments: Organizations implementing Internet of Things (IoT) solutions can leverage SDN to manage the massive volume of IoT devices efficiently, optimize data traffic, and implement security policies for IoT networks.
- Branch Offices and Remote Locations: Organizations with numerous branch offices or remote locations can use SDN to simplify network management from a central location, reducing the need for on-site IT personnel.
- Organizations Emphasizing Network Security: SDN's micro-segmentation capabilities can benefit organizations with a strong focus on network security. It allows them to isolate critical systems and applications, limiting the impact of potential security breaches.
Any organization seeking greater network flexibility, scalability, automation, and security can find value in adopting SDN. While SDN is well-suited for large and complex networks, it is a versatile solution that can be tailored to meet the specific needs of organizations of all sizes and types.
Software-Defined Networking (SDN) offers numerous benefits to organizations, making it a compelling and advantageous technology for modern network infrastructures.
Here are some key reasons why SDN is good for an organization:
- Flexibility and Agility: SDN allows organizations to adapt their networks quickly and easily to changing business needs. With centralized management and programmability, network administrators can adjust configurations, policies, and traffic flows in real time, reducing the time and effort required for network changes.
- Scalability: SDN facilitates network expansion and growth without major hardware upgrades. It provides a more efficient way to handle network traffic and accommodate increased demand, making it suitable for organizations experiencing rapid growth or expansion.
- Cost Savings: SDN can lead to cost savings through better resource utilization, reduced manual configuration efforts, and improved network efficiency. It can also minimize the need for specialized and proprietary networking hardware.
- Network Automation: SDN automates routine network tasks, reducing the reliance on manual interventions and human errors. Automation streamlines network management, leading to increased operational efficiency and reduced operational costs.
- Enhanced Security: SDN enables micro-segmentation, which allows organizations to create isolated segments within the network, enhancing security by preventing lateral movement of threats. Additionally, centralized policy management facilitates consistent security enforcement across the entire network.
- Centralized Management: SDN provides a single point of control for the entire network, allowing administrators to manage and configure network resources from a centralized controller. This centralized approach simplifies network management and enhances visibility and control.
- Better Resource Utilization: SDN optimizes the use of network resources by dynamically routing traffic based on real-time needs. This leads to improved network performance, reduced congestion, and better overall resource utilization.
- Faster Network Provisioning: With SDN, network services, and applications can be deployed more quickly since configurations can be automated and pushed from the centralized controller. This agility is especially beneficial in cloud environments and DevOps teams.
- Network Virtualization: SDN allows for the creation of virtual networks over the same physical infrastructure, providing better network segmentation, isolation, and resource allocation. This is particularly useful in multi-tenant environments.
- Future-Proofing: SDN is a technology that can adapt to future networking demands and innovations. Its programmable nature allows organizations to implement new features and protocols without replacing the entire network infrastructure.
SDN offers organizations the ability to build more responsive, efficient, and adaptable networks. By simplifying network management, enhancing security, and promoting automation.
SDN empowers organizations to keep up with the ever-changing demands of modern networking while reducing costs and improving overall network performance.
Implementing Software-Defined Networking (SDN) involves several steps and considerations to ensure a successful deployment. The implementation approach for SDN may vary based on the organization's existing network infrastructure, goals, and requirements.
Here's a general implementation approach for SDN:
- Assessment and Planning:
- Understand the organization's current network infrastructure, including hardware, software, and protocols in use.
- Identify specific use cases and business requirements that SDN aims to address, such as network automation, improved security, or enhanced scalability.
- Evaluate the readiness of the existing network for SDN deployment and determine any necessary upgrades or changes.
- Vendor and Technology Selection:
- Research different SDN solutions and vendors to find the one that best aligns with the organization's needs and budget.
- Consider factors such as interoperability, scalability, support, and vendor reputation.
- Choose the appropriate SDN controller and associated hardware that fits the organization's requirements.
- Proof of Concept (PoC) and Pilot:
- Before full-scale deployment, conduct a Proof of Concept (PoC) or pilot to test the chosen SDN solution in a controlled environment.
- Verify that the SDN features and functionalities meet the identified use cases and requirements.
- Evaluate the performance, scalability, and ease of management during the pilot phase.
- Network Design and Architecture:
- Develop a detailed network design and architecture plan for the SDN implementation.
- Define the logical and physical network topology, including the placement of SDN controllers, switches, routers, and gateways.
- Determine how network traffic will be managed, and identify any necessary changes to the existing network infrastructure.
- SDN Controller Deployment:
- Install and configure the selected SDN controller(s) according to the network design.
- Integrate the SDN controller with the existing network devices, using the appropriate southbound APIs such as OpenFlow.
- SDN Switch and Device Configuration:
- Configure the SDN-enabled switches and devices to establish communication with the SDN controller.
- Define flow rules and policies in the SDN switches to ensure proper traffic handling based on the controller's instructions.
- Network Migration and Integration:
- Gradually transition the network traffic from the traditional infrastructure to the SDN environment.
- Integrate the SDN environment with existing network services and applications.
- Testing and Validation:
- Conduct thorough testing to ensure the SDN implementation meets performance, security, and scalability requirements.
- Validate that the SDN controller accurately controls network traffic and enforces policies as intended.
- Training and Documentation:
- Provide training to network administrators and IT staff on the new SDN environment.
- Develop comprehensive documentation on the SDN deployment, including configuration details and troubleshooting guidelines.
- Monitoring and Maintenance:
· Implement monitoring and management tools to oversee the SDN environment.
· Regularly review and update SDN policies and configurations as network requirements evolve.
- Continuous Improvement:
· Continuously assess the SDN implementation's performance, security, and alignment with business objectives.
· Gather feedback from users and stakeholders to identify areas for improvement and enhancement.
The implementation approach for SDN requires careful planning, testing, and collaboration between different teams within the organization. It is essential to have a clear understanding of the organization's needs and objectives to ensure a successful and efficient SDN deployment.
Implementing Software-Defined Networking (SDN) successfully requires careful planning, adherence to best practices, and a clear understanding of the organization's requirements.
Here are some best practices to consider when implementing SDN:
- Define Clear Objectives: Clearly define the goals and objectives of implementing SDN in your organization. Identify the specific use cases and business requirements that SDN aims to address, such as network automation, enhanced security, or improved scalability.
- Conduct a Pilot or Proof of Concept (PoC): Before a full-scale deployment, conduct a pilot or PoC in a controlled environment. Test the chosen SDN solution to verify its suitability for your organization's needs and assess its performance, scalability, and ease of management.
- Evaluate Vendor Solutions: Research different SDN vendors and technologies to find the one that best aligns with your organization's needs and budget. Consider factors such as interoperability, scalability, support, and the vendor's reputation.
- Involve Key Stakeholders: Involve all relevant stakeholders, including network administrators, IT staff, application developers, and business managers, in the planning and decision-making process to ensure that the SDN implementation meets all requirements.
- Design a Comprehensive Network Architecture: Develop a detailed network design and architecture plan for the SDN implementation. Define the logical and physical network topology, including the placement of SDN controllers, switches, routers, and gateways.
- Plan for Network Integration: Consider how the SDN environment will integrate with your existing network infrastructure. Gradually transition network traffic from the traditional infrastructure to the SDN environment to minimize disruptions.
- Focus on Security: Implement proper security measures in your SDN deployment. Utilize micro-segmentation to create isolated segments within the network for improved security. Regularly update and monitor security policies.
- Invest in Training and Knowledge Transfer: Provide training to network administrators and IT staff on the new SDN environment. Develop comprehensive documentation on the SDN deployment, including configuration details and troubleshooting guidelines.
- Start with Use Case-Specific Deployments: Begin with smaller, use case-specific SDN deployments to gain experience and confidence in the technology before scaling it to the entire network.
- Monitor Performance and Fine-Tune: Implement monitoring and management tools to oversee the SDN environment continually. Regularly review and fine-tune SDN policies and configurations based on network performance and user feedback.
- Collaborate with the SDN Community: Engage with the SDN community and participate in forums, conferences, and working groups to learn from others' experiences and stay up-to-date with the latest advancements in SDN technology.
- Plan for Redundancy and Failover: Ensure that your SDN implementation includes redundancy and failover mechanisms to maintain network availability in case of controller or switch failures.
- Have a Clear Rollback Plan: Develop a clear rollback plan in case of any unforeseen issues during the SDN implementation. Be prepared to revert to the previous network configuration if necessary.
By following these best practices, organizations can maximize the benefits of SDN, reduce implementation risks, and create a more flexible, agile, and efficient network infrastructure.
Implementing, operating, and maintaining Software-Defined Networking (SDN) requires a combination of technical skills and expertise in networking, programming, and system administration.
Here are some essential skillsets required for various aspects of SDN:
- Networking Fundamentals:
- Strong understanding of networking concepts, including TCP/IP, routing, switching, VLANs, subnets, and network protocols.
- Knowledge of network topologies, architecture, and design principles.
- SDN Concepts and Protocols:
- In-depth knowledge of SDN concepts, including the separation of the control plane and data plane, SDN controllers, and programmable network devices.
- Familiarity with SDN protocols such as OpenFlow and NETCONF.
- Network Virtualization:
- Understanding of network virtualization concepts and technologies, including virtual LANs (VLANs), VXLANs, and network overlays.
- SDN Controllers:
- Proficiency in working with SDN controllers, including their installation, configuration, and management.
- Familiarity with popular SDN controller platforms such as OpenDaylight, ONOS, or proprietary controllers from vendors like Cisco ACI or VMware NSX.
- Scripting and Programming:
- Proficiency in programming languages such as Python, Java, or Go for writing custom SDN applications and automating network tasks.
- Familiarity with RESTful APIs and JSON for communication with SDN controllers.
- Network Security:
- Knowledge of network security principles and best practices.
- Understanding of micro-segmentation and how to implement security policies in an SDN environment.
- Network Troubleshooting:
- Strong troubleshooting skills to identify and resolve network issues in an SDN environment.
- Familiarity with packet capture and analysis tools for debugging network problems.
- Cloud Computing:
- Understanding of cloud computing concepts and how SDN integrates with cloud environments.
- Familiarity with cloud networking technologies and solutions.
- Linux and System Administration:
- Proficiency in Linux command-line tools and system administration.
- Knowledge of network services like DHCP, DNS, and NTP.
- Monitoring and Analytics:
- Experience with network monitoring tools and analytics platforms for tracking SDN performance and traffic patterns.
- Understanding of telemetry and monitoring capabilities provided by SDN controllers.
- Vendor-Specific Knowledge:
- Familiarity with specific SDN products and solutions from different vendors, such as Cisco, VMware, Juniper, etc.
- Communication and Collaboration:
- Strong communication skills to collaborate with cross-functional teams, stakeholders, and vendors during SDN implementation and maintenance.
Implementing and maintaining SDN requires continuous learning and keeping up with the latest developments in SDN technologies and standards. As SDN evolves, staying current with industry trends and advancements is essential for successful SDN deployment and operation.
While Software-Defined Networking (SDN) offers numerous benefits, it also introduces new security considerations that organizations need to address.
Some of the key security concerns with SDN include:
- Centralized Controller Vulnerabilities: The central SDN controller becomes a single point of failure and a high-value target for attackers. Compromising the controller could result in unauthorized access to the entire network, making it crucial to implement strong security measures around the controller.
- Southbound API Security: The southbound APIs used for communication between the SDN controller and network devices must be secured to prevent unauthorized access and tampering with network devices. Proper authentication and encryption are essential to protect these communication channels.
- Northbound API Vulnerabilities: The northbound APIs used to interact with higher-level applications and services can also be targeted by attackers. Proper access controls and input validation are necessary to prevent malicious activities through these interfaces.
- Controller-to-Switch Communication: The communication between the SDN controller and switches needs to be protected to prevent eavesdropping, tampering, or spoofing of control messages. Implementing encryption and secure communication protocols is vital.
- Virtual Network Security: SDN's network virtualization capabilities introduce new security challenges, such as VM escape attacks and cross-tenant data breaches. Proper isolation and security controls are required to protect virtual networks and prevent unauthorized access.
- Denial of Service (DoS) Attacks: SDN environments can be susceptible to DoS attacks that overload the SDN controller or flood the network with malicious traffic. SDN implementations should have measures in place to detect and mitigate DoS attacks effectively.
- Flow Rule Manipulation: Attackers may attempt to manipulate flow rules in SDN switches to redirect or intercept traffic, leading to potential data theft or network disruptions. Organizations must implement access controls and validation mechanisms to prevent unauthorized flow rule modifications.
- Network Visibility Concerns: With centralized control, attackers may exploit SDN's visibility features to gather sensitive network information and plan targeted attacks. Proper access controls and monitoring are crucial to limit visibility to authorized personnel.
- Security Policy Complexity: Implementing security policies in SDN can be complex, especially in large and dynamic networks. Organizations need to ensure that policies are correctly configured, and changes are promptly applied to maintain consistent security enforcement.
- Insider Threats: SDN introduces a higher level of network control and access. Insider threats can become more potent in an SDN environment, as malicious insiders could misuse centralized management capabilities.
Addressing these security concerns requires a comprehensive approach to SDN security. It involves implementing strong access controls, encryption, authentication mechanisms, and regular security audits. Continuous monitoring and analysis of network traffic are essential to detect and respond to security incidents promptly. Regular security training for network administrators and IT staff is also crucial to ensure they are aware of the latest threats and security best practices related to SDN.
Addressing the security concerns in Software-Defined Networking (SDN) effectively requires a proactive and multi-layered approach to safeguard the network infrastructure.
Here are some strategies to address these security concerns:
- Secure SDN Controller:
- Implement strong access controls, multi-factor authentication, and secure communication protocols to protect the SDN controller from unauthorized access.
- Regularly update and patch the controller software to address known vulnerabilities.
- Secure Southbound and Northbound APIs:
- Secure communication between the controller and switches using encryption and secure communication protocols.
- Apply access controls and input validation mechanisms to prevent unauthorized access and tampering with APIs.
- Secure Controller-to-Switch Communication:
- Encrypt control messages exchanged between the SDN controller and switches to prevent eavesdropping and tampering.
- Implement authentication mechanisms to ensure switches only accept commands from authorized controllers.
- Network Virtualization Security:
- Use network segmentation and isolation techniques to protect virtual networks from unauthorized access and VM escape attacks.
- Employ strong access controls to prevent cross-tenant data breaches in multi-tenant environments.
- Mitigate DoS Attacks:
- Implement DoS protection mechanisms at the controller and switch level to detect and mitigate DoS attacks.
- Monitor network traffic for signs of abnormal behavior that could indicate a DoS attack.
- Validate Flow Rules:
- Apply flow rule validation mechanisms to ensure that flow rules are legitimate and not manipulated by attackers.
- Monitor flow rule changes and raise alerts for any unauthorized modifications.
- Network Visibility Management:
- Restrict access to SDN network visibility features to authorized personnel only.
- Implement access controls and auditing mechanisms to track and monitor access to network visibility data.
- Comprehensive Security Policies:
- Develop comprehensive security policies tailored to the SDN environment, including access controls, segmentation, encryption, and data privacy measures.
- Regularly review and update security policies to adapt to evolving threats and network changes.
- Insider Threat Mitigation:
- Implement role-based access controls to limit network privileges for different user roles.
- Conduct regular security training for network administrators and staff to raise awareness of insider threat risks and best security practices.
- Continuous Monitoring and Incident Response:
- Deploy robust monitoring and analytics tools to detect anomalous behavior and security incidents in real time.
- Establish an effective incident response plan to promptly respond to security breaches and mitigate their impact.
- Security Audits and Penetration Testing:
- Conduct regular security audits and penetration testing to identify potential vulnerabilities and weaknesses in the SDN infrastructure.
- Address any findings from security assessments promptly.
- Stay Updated and Engage with the SDN Community:
- Keep abreast of the latest security developments and best practices in SDN by engaging with the SDN community, attending conferences, and participating in forums.
- Collaborate with vendors to stay informed about security patches and updates for SDN products.
By adopting a comprehensive and proactive approach to SDN security, organizations can effectively mitigate risks, protect their network infrastructure, and ensure a secure and resilient SDN deployment.
Security should be an ongoing concern, and organizations should continuously reassess their security posture as new threats and vulnerabilities emerge in the dynamic landscape of SDN.
There were several products and solutions available for Software-Defined Networking (SDN) security.
Here are some notable SDN security products and solutions that were available at that time:
- Cisco Identity Services Engine (ISE): Cisco ISE provides secure network access and policy enforcement in SDN environments. It offers identity-based access control, authentication, and authorization to prevent unauthorized access to SDN resources.
- VMware NSX Distributed Firewall: VMware NSX includes a distributed firewall that operates at the virtual machine level, providing micro-segmentation and advanced security policies in SDN deployments. It helps protect virtual networks from lateral movement of threats.
- Juniper Networks vSRX Virtual Firewall: Juniper vSRX is a virtualized security appliance that can be deployed in SDN environments to provide advanced security services, including firewall, intrusion prevention, and application security.
- Fortinet FortiGate SDN Security: Fortinet's FortiGate platform offers SDN security solutions, including virtual firewalls and security appliances, to protect SDN networks from threats and attacks.
- Palo Alto Networks VM-Series: The VM-Series is a virtualized firewall solution from Palo Alto Networks that can be deployed in SDN environments to provide advanced threat prevention, URL filtering, and network segmentation.
- Check Point CloudGuard: Check Point's CloudGuard is designed to secure SDN and cloud environments. It provides threat prevention, intrusion detection and prevention, and application control for SDN networks.
- F5 BIG-IP Virtual Edition (VE): F5's BIG-IP VE is a virtual application delivery controller that can be deployed in SDN environments to enhance security, load balancing, and application performance.
- Guardicore Centra: Guardicore Centra offers micro-segmentation and advanced threat detection for SDN and cloud environments, helping organizations protect critical assets from internal and external threats.
- AlgoSec Security Management Suite: AlgoSec provides security management solutions that can help organizations manage security policies and ensure compliance in SDN environments.
When evaluating SDN security products, consider factors such as the specific needs of your organization, compatibility with your SDN deployment, scalability, ease of integration, and vendor reputation. Conducting thorough research and engaging with vendors can help you find the most suitable SDN security solution for your network infrastructure.
These SDN security products can be used in combination to create a comprehensive and layered security approach for SDN environments. Many organizations adopt a multi-vendor security strategy to address different aspects of SDN security effectively.
By combining various products, organizations can enhance their overall security posture and ensure comprehensive protection against a wide range of threats and vulnerabilities.
For example:
- Cisco ISE and VMware NSX: Cisco ISE can be used for identity-based access control and policy enforcement, while VMware NSX provides micro-segmentation and distributed firewall capabilities. Together, they can ensure that only authorized users and applications have access to specific resources within the virtualized network.
- Juniper vSRX and Palo Alto Networks VM-Series: Juniper vSRX can provide advanced security services at the virtual machine level, and Palo Alto Networks VM-Series can offer threat prevention and application control. By using both solutions, organizations can achieve granular security and comprehensive threat protection.
- Fortinet FortiGate and F5 BIG-IP VE: Fortinet FortiGate can provide virtual firewall services, while F5 BIG-IP VE can enhance application security and performance. Combining these solutions can provide a robust security infrastructure that protects both the network and application layers.
- Guardicore Centra and Check Point CloudGuard: Guardicore Centra offers micro-segmentation and advanced threat detection, while Check Point CloudGuard provides comprehensive security for cloud and SDN environments. Together, they can provide a well-rounded security approach for cloud-based SDN deployments.
- AlgoSec Security Management Suite with other products: AlgoSec can be used to manage security policies across multiple security solutions, including virtual firewalls and security appliances. It can provide a unified view of security policies and streamline security management across the SDN environment.
It is crucial to design the security architecture carefully and ensure that the combination of products works cohesively and does not introduce any conflicts or gaps in security coverage. Additionally, proper integration, configuration, and ongoing monitoring of the combined security solutions are essential to maintain a robust and effective security posture in the SDN environment.
Comparing various SDN security products can help organizations make informed decisions based on their specific requirements and network environments. Here's a comparison of some popular SDN security products, along with their pros and cons:
1. Cisco Identity Services Engine (ISE):
Pros:
- Provides comprehensive identity-based access control and policy enforcement.
- Integrates well with Cisco networking infrastructure and SDN solutions.
- Offers robust authentication and authorization mechanisms.
Cons:
- Limited support for non-Cisco SDN environments and devices.
- May have a steeper learning curve for non-Cisco network administrators.
2. VMware NSX Distributed Firewall:
Pros:
- Enables micro-segmentation and granular security policies for virtualized environments.
- Seamlessly integrates with VMware's virtualization platform.
- Provides distributed security enforcement for better performance and scalability.
Cons:
- Limited support for non-VMware virtualization environments.
- Requires deep integration with the VMware ecosystem for full functionality.
3. Juniper Networks vSRX Virtual Firewall:
Pros:
- Offers advanced security services, including firewall and intrusion prevention.
- Can be deployed in various virtualization and SDN environments.
- Provides high performance and scalability in virtualized networks.
Cons:
- May require additional licensing for certain advanced features.
- Integration with non-Juniper SDN environments might require more effort.
4. Fortinet FortiGate SDN Security:
Pros:
- Provides virtualized firewalls and security appliances for SDN environments.
- Offers a wide range of security services, including VPN, IPS, and antivirus.
- Supports multi-vendor SDN deployments.
Cons:
- May have complex licensing models for different features.
- Integration with other SDN products might require careful planning.
5. Palo Alto Networks VM-Series:
Pros:
- Offers advanced threat prevention and application control in virtualized networks.
- Provides deep visibility and reporting for security events.
- Supports multi-cloud and hybrid cloud environments.
Cons:
- Can be resource-intensive in high-throughput environments.
- Licensing costs may increase with the number of virtual instances.
6. Check Point CloudGuard:
Pros:
- Designed specifically for securing cloud and SDN environments.
- Offers robust threat prevention and intrusion detection features.
- Supports automation and integration with cloud platforms.
Cons:
- May have a steeper learning curve for non-Check Point users.
- Integration with certain cloud providers might require additional configuration.
7. Guardicore Center:
Pros:
- Provides micro-segmentation and advanced threat detection in SDN and cloud environments.
- Offers visibility and control over east-west traffic in virtualized networks.
- Supports diverse SDN and cloud platforms.
Cons:
- Deployment and configuration might be complex for large-scale environments.
- Can be resource-intensive in high-throughput networks.
8. AlgoSec Security Management Suite:
Pros:
- Offers centralized security policy management across multiple SDN and firewall products.
- Provides comprehensive visibility and analysis of security policies.
- Simplifies compliance and audit processes.
Cons:
- May require additional integration efforts with certain SDN products.
- Primarily focuses on policy management and might not provide direct security features.
It's important to note that each product has its strengths and weaknesses, and the suitability of a particular product will depend on an organization's specific needs, existing infrastructure, and security requirements.
Evaluating features, integration capabilities, scalability, and support options will help organizations select the most appropriate SDN security solution for their environment.
Software-Defined Networking (SDN) has ushered in a new era of networking, revolutionizing how organizations manage and operate their networks. From its humble beginnings as a theoretical concept to its widespread adoption across various industries, SDN has proven to be a game-changer in the networking landscape.
SDN's advantages, including enhanced network flexibility, improved scalability, cost savings, and better security, have made it a compelling solution for organizations seeking to stay agile and competitive in today's fast-paced digital world. By centralizing control and automating network tasks, SDN enables network administrators to respond swiftly to changing business needs, driving innovation and efficiency.
However, the journey to SDN implementation may come with certain challenges, such as complexities in deployment, interoperability concerns, and new security risks. Overcoming these hurdles requires careful planning, skill development, and vendor selection to ensure a successful SDN deployment.
As we look to the future, SDN continues to hold immense promise. With the emergence of 5G, IoT, and edge computing, the demand for flexible, scalable, and secure networks will only grow. SDN's adaptability and programmability make it an ideal solution to meet the evolving networking demands of tomorrow.
Embracing Software-Defined Networking with an informed approach will empower organizations to harness their full potential and unlock unparalleled networking capabilities. By leveraging SDN's strengths while addressing its challenges, businesses can embark on a transformative journey, redefining the way networks are managed, operated, and utilized for the betterment of their digital infrastructure. In this age of technological advancements, SDN stands as a beacon of innovation, propelling networking into an exciting and dynamic future.
Embracing Life's Paradoxes: Navigating Towards Fulfilment
Life is a labyrinth of paradoxes that challenge our perceptions and guide us toward greater understanding. In this article, we explore six powerful paradoxes that hold valuable life lessons. From the interplay between trust and trustworthiness to the significance of embracing challenges, each paradox offers profound insights to reshape our perspectives and lead us to a more fulfilling and authentic existence.
Life, with its myriad of complexities, often presents us with situations that seem contradictory and challenging to comprehend. However, these paradoxes are not mere puzzles to be solved; they are profound life lessons waiting to be embraced. In this blog post, we explore six powerful paradoxes that hold the keys to unlocking personal growth, wisdom, and a more fulfilling journey. By understanding and embracing these paradoxes, we can navigate life's ups and downs with courage, authenticity, and a deeper sense of purpose.
Life is a complex journey filled with countless ups and downs, and as we navigate through its twists and turns, we often encounter paradoxes that challenge our understanding of reality. These paradoxes can offer profound insights into the human experience and serve as valuable life lessons. In this article, we explore six of the most powerful paradoxes of life that can reshape our perspectives and guide us toward a more fulfilling existence.
1. Trust and Trustworthiness: A Mutual Reflection
The first paradox revolves around trust and trustworthiness. We all desire to be trusted by others, yet some struggle to trust those around them. The truth is that trust and trustworthiness are interconnected. When we are hesitant to trust others, we may inadvertently display behaviors that erode their trust in us. Embracing this paradox involves working on ourselves, building self-confidence, and addressing any past traumas that hinder our ability to trust. As we become more trustworthy, we naturally attract trust from others, forming stronger and more genuine relationships.
People who can't trust, can't be trusted. People who are insecure in their relationships are more likely to sabotage them.
Trust is the foundation of any healthy relationship, be it with friends, family, or romantic partners. However, it's often observed that individuals who have difficulty trusting others are themselves less trustworthy. This paradox arises because a lack of trust can lead to suspicious behavior, jealousy, and emotional distance, which ultimately erodes the trust others have in them. To break this cycle, it's crucial to work on building self-confidence and addressing past traumas that may be causing trust issues. Only then can one foster genuine connections with others and establish a sense of trustworthiness.
2. Embrace Challenges, Embrace Growth
Life is not meant to be lived on a smooth and easy path. The second paradox reminds us that the road to growth and fulfillment is often paved with challenges. Avoiding difficulties and seeking shortcuts may provide temporary comfort, but it robs us of opportunities for personal development and true accomplishment. Embracing challenges, on the other hand, builds resilience, character, and a profound sense of achievement. It is through overcoming obstacles that we discover our true potential and evolve into our best selves.
Life is easy when you live it the hard way, and hard if you try to live it the easy way.
It's easy to fall into the trap of seeking shortcuts and avoiding challenges, thinking that it will lead to an easier and more comfortable life. However, this paradox teaches us that true fulfillment and growth come from facing life's difficulties head-on. Embracing challenges, learning from failures, and putting in the effort to overcome obstacles can lead to a deeper sense of accomplishment and personal development. On the other hand, those who avoid challenges and opt for an easy way out often find themselves unprepared to handle life's inevitable complexities, making their journey more arduous in the long run.
3. The Dilemma of Discipline and Regret
At some point in life, we all face crucial choices that demand sacrifices. The third paradox compels us to choose between the pain of discipline and the pain of regret. While discipline may require hard work and commitment, it leads to long-term success and satisfaction. On the contrary, succumbing to laziness and avoiding discipline often results in regrets for not pursuing our dreams or putting in the necessary effort. By acknowledging this paradox, we can make conscious choices that align with our values and aspirations, minimizing future regrets.
Everyone must choose one of two pains: the pain of discipline or the pain of regret.
In life, we often encounter decisions that require sacrifices. This paradox emphasizes that each choice we make comes with its own set of consequences – the pain of discipline or the pain of regret. Those who choose discipline are willing to invest time, effort, and dedication to achieve their goals, even if it means facing challenges along the way. On the other hand, those who choose to avoid discipline may find temporary relief, but in the end, they will face the burden of regret for not pursuing their aspirations or putting in the necessary work.
4. Authenticity: The Key to Meaningful Connections
The fourth paradox revolves around the desire to impress others. Trying too hard to gain admiration and validation often backfires, leading people to see us as insincere or inauthentic. Authenticity, however, breeds genuine connections. By embracing our true selves, flaws, and all, we create a magnetism that attracts people who appreciate us for who we are. The paradox teaches us that the most meaningful relationships are forged through honesty and vulnerability, not by putting on a facade to please others.
The more you try to impress people, the less impressed they'll be. Nobody likes a try-hard.
While it's natural to want to be accepted and liked by others, constantly seeking validation and approval can be counterproductive. This paradox highlights the importance of authenticity and self-confidence. People are drawn to those who are genuine and unafraid to be themselves, rather than those who put on a facade to impress others. True connections and respect are forged when individuals display their true selves, without being overly concerned about what others think.
5. Conquering Fear and Embracing Life
The fifth paradox delves into the fear of death and its impact on our ability to live life fully. When we fear death, we often find ourselves trapped in a cycle of worry and anxiety, which inhibits our ability to enjoy the present moment. Embracing life requires courage – the courage to accept our mortality, embrace uncertainty, and savor every experience, knowing that life is both fragile and beautiful. By acknowledging this paradox, we can unlock the courage needed to fully embrace life's joys and opportunities.
The more afraid you are of death, the less you'll be able to enjoy life.
Fear of mortality can cast a shadow on our ability to live life to the fullest. This paradox reminds us that embracing life requires courage – the courage to face our mortality and accept the inherent uncertainties of existence. When we let go of our fear of death, we can appreciate the present moment and find meaning and joy in life's experiences. Dwelling on the fear of loss robs us of the opportunity to cherish what we have and create lasting memories with our loved ones.
6. The Ever-Expanding Realm of Knowledge
The final paradox reminds us of the vastness of knowledge and the boundless learning opportunities. As we acquire more knowledge, we become aware of how much we don't know, humbling our understanding of the world. This realization opens the door to a lifelong journey of curiosity and self-discovery. Embracing this paradox encourages us to remain open-minded, embrace new perspectives, and continually seek knowledge in every aspect of life.
The more you learn, the more you realize how much you don't know.
This paradox emphasizes the boundless nature of knowledge and the humbling realization that there will always be more to learn. As we delve deeper into various subjects and gain expertise, we become acutely aware of the vast expanse of unknown information. Instead of feeling overwhelmed by this realization, embracing lifelong learning can be a source of empowerment and curiosity. Embracing the unknown can open doors to new possibilities and contribute to personal growth.
Life's paradoxes serve as reminders of the intricate nature of our existence. Embracing these paradoxes can help us navigate life's complexities with greater wisdom and insight. By acknowledging the power of trust, the value of facing challenges, the significance of authentic connections, the importance of courage, and the beauty of lifelong learning, we can embark on a path of self-discovery and lead more meaningful and fulfilling lives.
Embracing life's paradoxes is the gateway to personal growth, meaningful connections, and a more fulfilling journey. By recognizing the interplay between trust and trustworthiness, embracing challenges as opportunities for growth, making choices aligned with our values, prioritizing authenticity, conquering fear, and nurturing an insatiable curiosity, we can lead lives rich with wisdom, purpose, and profound joy. Embrace these paradoxes, and embark on a journey of self-discovery that will transform your life in unimaginable ways.
By embracing life's paradoxes, we can find wisdom, courage, and authenticity, leading to a more fulfilling and enriching journey.
Mastering Kubernetes: Empowering Organizations in the World of Containers
In today's fast-paced technological landscape, organizations are embracing containerized applications for their scalability and flexibility. However, managing these containers at scale can be challenging. Enter Kubernetes – an open-source container orchestration platform that revolutionizes application deployment and management. In this blog, we explore how Kubernetes empowers organizations, the best approach for deployment, and key considerations to ensure success.
Introducing Kubernetes: Empowering Organizations in the World of Containers
The adoption of containerized applications has become a game-changer for organizations seeking agility, scalability, and seamless application deployment. However, as the number of containers multiplies, so do the challenges in managing them efficiently. This is where Kubernetes comes into the spotlight, offering a powerful solution for container orchestration and management. In this blog post, we will explore how Kubernetes can empower organizations, the approach to take for successful deployment, and key considerations to watch out for.
What is Kubernetes? Kubernetes, often abbreviated as K8s, is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. Developed by Google, Kubernetes has rapidly gained popularity and has become the de facto standard for modern containerized environments. It allows organizations to run and manage applications consistently across various infrastructure environments, whether on-premises, in the cloud, or at the edge.
Kubernetes (often abbreviated as K8s) is an open-source container orchestration platform developed by Google. It is designed to automate the deployment, scaling, and management of containerized applications. Kubernetes enables organizations to efficiently manage and run containerized applications in a scalable and fault-tolerant manner.
Key concepts and components of Kubernetes:
1. Containerization: Kubernetes is closely associated with the concept of containers. Containers are lightweight and portable units that package an application and its dependencies, allowing it to run consistently across different environments.
2. Nodes: In a Kubernetes cluster, a node is a physical or virtual machine that runs containers. Each node is responsible for running one or more containers and has the necessary tools to communicate with the Kubernetes master.
3. Master: The master is the central control plane of the Kubernetes cluster. It manages the cluster's state and orchestrates the scheduling and deployment of applications on the nodes. The master components include the API server, controller manager, scheduler, etcd (a distributed key-value store for cluster data).
4. Pods: A pod is the smallest deployable unit in Kubernetes. It represents one or more containers that are deployed together on the same node and share the same network namespace. Pods are used to group containers that require shared resources or need to co-locate.
5. ReplicaSets and Deployments: These are higher-level abstractions that allow you to define the desired state of your application and automatically handle scaling, fault tolerance, and updates. ReplicaSets ensure a specified number of replicas (identical pods) are running at all times, while Deployments manage updates and rollbacks.
6. Services: Services enable network access to a set of pods. They provide a stable IP address and DNS name to access the pods, even if the underlying pods or nodes change.
7. Labels and Selectors: Labels are key-value pairs attached to Kubernetes objects (e.g., pods, services) to identify and organize them. Selectors are used to query and filter objects based on their labels.
8. Namespace: Kubernetes supports multiple virtual clusters within the same physical cluster, called namespaces. Namespaces are used to organize and isolate resources, making it easier to manage applications and teams within a shared Kubernetes environment.
9. ConfigMaps and Secrets: ConfigMaps are used to store configuration data, and Secrets are used to store sensitive information, such as passwords or API keys. These objects allow you to decouple configuration data from the container images, making it easier to manage and update configurations.
Kubernetes provides a powerful platform for managing containerized applications, allowing developers to focus on building applications without worrying about the underlying infrastructure complexities. It has become a standard for deploying and managing applications in cloud-native and microservices-based environments.
Kubernetes works by providing a robust set of tools and components to manage containerized applications in a distributed environment. Let's go through the high-level steps of how Kubernetes works:
1. Cluster Creation: A Kubernetes cluster is set up by configuring a group of physical or virtual machines, called nodes. These nodes form the infrastructure on which containers will run. The cluster typically consists of a master node and multiple worker nodes.
2. Master Node: The master node is the control plane of the Kubernetes cluster. It hosts several components:
o API Server: It acts as the front end for the
Kubernetes control plane. It handles requests from various tools (e.g., kubectl)
and ensures the desired state of the cluster matches the actual state.
o Scheduler: The scheduler is responsible for determining where to place newly created pods based on resource requirements, node availability, and any user-defined constraints.
o Controller Manager: This component manages various controllers that handle different aspects of the cluster, such as ReplicaSets, Deployments, and more. The controllers continuously work to bring the cluster to the desired state.
o etcd: This is a distributed key-value store that stores the cluster's configuration data and state. All components in the master node read from and write to etcd to ensure they have consistent information about the cluster.
3. Worker Nodes: The worker nodes run the actual application containers. Each node runs a set of services, such as the Kubernetes Node Agent (kubelet), which communicates with the master node and manages containers on the node.
4. Pods: A pod is the smallest deployable unit
in Kubernetes. It represents one or more containers that are scheduled to run
together on the same node. Containers within a pod share the same network
namespace, which means they can communicate with each other over localhost.
Pods are ephemeral; they can be created, destroyed, and replaced as needed.
5. ReplicaSets and Deployments: ReplicaSets and Deployments are abstractions that define the desired state of your application. ReplicaSets ensure a specified number of replicas (pods) are running at all times, while Deployments manage updates and rollbacks of the application by creating and managing ReplicaSets.
6. Services: A Kubernetes Service is an abstraction that defines a stable endpoint to access a set of pods. Services provide load balancing, allowing client applications to communicate with pods using a single, stable IP address and DNS name, even if the pods or nodes change.
7. Labels and Selectors: Labels are key-value pairs attached to Kubernetes objects (e.g., pods, services). They are used to identify and organize objects. Selectors are used to query and filter objects based on their labels.
8. ConfigMaps and Secrets: ConfigMaps and Secrets are used to store configuration data and sensitive information, respectively, decoupling them from container images and making them easier to manage and update.
9. Networking: Kubernetes handles networking between pods and nodes, ensuring that containers can communicate with each other across the cluster. The container runtime (e.g., Docker, containerd) takes care of container networking within a pod.
10. Scaling and Self-Healing: Kubernetes automatically manages to scale based on defined rules and ensures that the desired number of replicas are running. It also detects and replaces failed or unhealthy pods, ensuring the application remains available and reliable.
Kubernetes provides a powerful platform to manage containerized applications efficiently, offering automation, scalability, and fault tolerance for modern, cloud-native environments.
Kubernetes has a robust and modular architecture that follows a master-node model. The architecture is designed to provide high availability, scalability, and fault tolerance for containerized applications. Let's explore the key components and their interactions within the Kubernetes architecture:
- Master Node:
- API Server: The API server acts as the front end for all interactions with the Kubernetes cluster. It exposes the Kubernetes API, which allows users and various Kubernetes components to communicate with the cluster. The API server is responsible for accepting and processing RESTful API requests, validating them, and updating the cluster's state in etcd.
- etcd: This is a distributed key-value store that stores the entire configuration data and the state of the Kubernetes cluster. All the master components read from and write to etcd to ensure consistency and maintain the desired state.
- Scheduler: The scheduler is responsible for placing newly created pods onto available worker nodes. It considers factors such as resource requirements, node availability, and any user-defined constraints (affinity or anti-affinity rules) to make optimal scheduling decisions.
- Controller Manager: The controller manager runs several controllers, each responsible for monitoring and maintaining different aspects of the cluster's state. For example, the Replication Controller ensures the desired number of replicas are running, the Deployment Controller manages updates and rollbacks, and the Node Controller handles node-related operations.
- Worker Node:
- Kubelet: The Kubelet is the primary agent that runs on each worker node and communicates with the master node. It receives pod specifications from the API server and ensures that the containers described in those pods are running and healthy on the node. It also reports the node's health back to the master.
- Container Runtime: The container runtime is responsible for running the containers on the worker node. Kubernetes supports multiple container runtimes, such as Docker, containerd, and CRI-O.
- Kube-proxy: The kube-proxy is responsible for managing the network connectivity for pods and services on the node. It maintains network rules to forward traffic to the appropriate pods based on the services' configurations.
- Pods and Controllers:
- Pods: A pod is the smallest deployable unit in Kubernetes. It represents one or more containers that are deployed together on the same node and share the same network namespace. Pods are the basic units on which scaling, healing, and other higher-level abstractions are built.
- ReplicaSets: A ReplicaSet is responsible for ensuring a specified number of replicas (identical pods) are running at all times. It continuously monitors the current state and reconciles it with the desired state defined by the user.
- Deployments: A Deployment manages updates and rollbacks of a ReplicaSet. It allows users to define declaratively how the application state should change over time, and Kubernetes ensures the desired state is met.
- Services:
- Service: A Service is an abstraction that defines a stable endpoint to access a set of pods. It provides load balancing and ensures client applications can communicate with pods using a single, stable IP address and DNS name, even if the pods or nodes change.
- Labels and Selectors:
- Labels: Labels are key-value pairs attached to Kubernetes objects (e.g., pods, services). They are used to identify, organize, and select objects.
- Selectors: Selectors are used to query and filter objects based on their labels. They allow components like Services to discover and target specific sets of pods based on labels.
The combination of these components and their interactions forms the core architecture of Kubernetes, enabling it to manage containerized applications efficiently in a distributed and scalable manner. The modular design allows Kubernetes to be extended and customized through the use of plugins and custom resources.
How Kubernetes Empowers Organizations:
1. Scalability and Flexibility: Kubernetes enables organizations to effortlessly scale applications up or down based on demand. It ensures that the required resources are allocated dynamically, keeping applications running smoothly during periods of high traffic.
2. High Availability and Fault Tolerance: Kubernetes ensures application availability by automatically recovering from failures. It achieves high availability by distributing application components across multiple nodes, mitigating the risk of single points of failure.
3. Automated Application Management: Kubernetes automates application deployment and management processes, reducing human intervention and potential errors. It simplifies the process of deploying complex microservices-based applications.
4. Resource Efficiency: Kubernetes optimizes resource allocation, ensuring efficient utilization of CPU, memory, and storage. This leads to cost savings and improved performance.
5. Cloud-Native Adoption: Kubernetes facilitates the adoption of cloud-native practices, making it easier for organizations to migrate, scale, and manage applications in cloud environments.
Kubernetes offers numerous advantages, making it a popular choice for container orchestration and application management. However, it also has some challenges and potential disadvantages. Let's explore both sides:
Advantages of Kubernetes:
1. Container Orchestration: Kubernetes provides robust container orchestration capabilities, enabling seamless deployment, scaling, and management of containerized applications.
2. Scalability: Kubernetes allows you to scale your applications easily, both vertically (by increasing resources for a single node) and horizontally (by adding more nodes to the cluster).
3. High Availability: Kubernetes supports high availability configurations, ensuring that applications remain accessible even if some nodes or components fail.
4. Automatic Healing: Kubernetes automatically restarts or replaces containers that fail or become unhealthy, ensuring the application's reliability.
5. Declarative Configuration: Kubernetes uses a declarative approach, allowing you to define the desired state of your application and leaving the platform to handle the implementation details.
6. Self-Healing: Kubernetes continually monitors the desired state of the cluster and automatically makes adjustments to bring it back to the desired state if any discrepancies occur.
7. Resource Utilization: Kubernetes effectively manages resources, optimizing the allocation of CPU, memory, and storage for running applications.
8. Horizontal Autoscaling: Kubernetes supports automatic horizontal pod autoscaling based on CPU utilization or custom metrics, ensuring efficient resource usage.
9. Ecosystem and Community: Kubernetes has a vast and active community, offering a rich ecosystem of tools, plugins, and integrations.
10. Multi-Cloud and Hybrid Cloud Support: Kubernetes is cloud-agnostic and works across various cloud providers, making it easier to build multi-cloud and hybrid cloud setups.
Disadvantages of Kubernetes:
1. Complexity: Kubernetes has a steep learning curve and can be complex to set up and manage, especially for small-scale projects or teams without prior containerization experience.
2. Resource Intensive: Running Kubernetes requires a certain level of resources and infrastructure, which might not be feasible for small applications or low-resource environments.
3. Cluster Networking: Setting up and managing networking in a Kubernetes cluster can be challenging, especially in complex network environments.
4. Security Concerns: Kubernetes clusters require proper security measures to prevent unauthorized access and potential vulnerabilities.
5. Version Compatibility: Upgrading Kubernetes versions can be challenging, especially when custom resources and plugins are involved.
6. Debugging and Troubleshooting: Troubleshooting issues in a Kubernetes cluster can be time-consuming and requires a deep understanding of the platform's architecture.
7. Vendor Lock-In: While Kubernetes itself is open-source, some cloud providers offer managed Kubernetes services that might lead to vendor lock-in.
8. Persistent Storage: Configuring and managing persistent storage for applications can be complex, particularly in dynamic environments.
Despite these disadvantages, Kubernetes remains a powerful and widely adopted solution for managing containerized applications in production environments. Proper planning, training, and expertise can help mitigate many of the challenges associated with using Kubernetes effectively.
Approach for Successful Kubernetes Deployment:
1. Thorough Planning: Start with a detailed assessment of your organization's requirements, infrastructure, and application architecture. Develop a clear plan for the deployment, considering factors like resource capacity, networking, and security needs.
2. Proper Training and Familiarization: Kubernetes can be complex, so ensure that your team receives proper training and hands-on experience. Familiarize yourself with Kubernetes concepts, components, and best practices before diving into deployment.
3. Start Small and Iterate: Begin with a small-scale deployment or a proof-of-concept to gain confidence in Kubernetes. Iterate and learn from the initial experience before scaling to larger environments.
4. Leverage Managed Services: If your organization lacks the expertise or resources to manage Kubernetes on its own, consider using managed Kubernetes services offered by cloud providers. These services handle the underlying infrastructure, allowing you to focus on application deployment and management.
Setting up a Kubernetes cluster requires installing and configuring various components, which can be a complex task. To simplify this process, there are several products and tools available that help you set up and manage Kubernetes clusters more easily. Here are some popular ones:
- Minikube:
- Minikube is a lightweight and easy-to-use tool that allows you to run a single-node Kubernetes cluster on your local machine. It is primarily intended for local development and testing. Minikube sets up a virtual machine with the Kubernetes components, enabling you to experiment with Kubernetes without the need for a full-fledged cluster.
- kubeadm:
- Kubeadm is a command-line tool provided by Kubernetes itself to bootstrap and manage a minimal and conformant Kubernetes cluster. It is a part of the Kubernetes project and helps simplify the process of creating a cluster by handling most of the complexity of setting up the control plane components.
- kops (Kubernetes Operations):
- Kops is a popular command-line tool used to create, upgrade, and manage Kubernetes clusters on cloud infrastructure providers such as AWS, GCP, and Azure. It automates the process of provisioning the required cloud resources and configuring the Kubernetes components.
- k3s:
- k3s is a lightweight and easy-to-install Kubernetes distribution designed for resource-constrained environments or edge computing scenarios. It is a fully compliant Kubernetes distribution but with a reduced memory footprint and simpler installation compared to standard Kubernetes.
- k3d (k3s in Docker):
- k3d is a tool that allows you to run k3s clusters using Docker containers. It simplifies the process of creating multiple lightweight Kubernetes clusters on your local machine for testing and development purposes.
- Rancher:
- Rancher is an open-source platform that provides a complete management interface for Kubernetes. It simplifies the deployment and management of Kubernetes clusters and offers additional features like cluster provisioning, monitoring, logging, and advanced security features.
- OpenShift:
- OpenShift is a Kubernetes distribution with added features and tools for enterprise use cases. It includes features like source-to-image (S2I) builds, built-in CI/CD capabilities, advanced security features, and developer-friendly interfaces.
- AKS (Azure Kubernetes Service), EKS (Amazon Elastic Kubernetes Service), GKE (Google Kubernetes Engine):
- These are managed Kubernetes services provided by cloud providers. They offer fully managed Kubernetes clusters, where the cloud provider handles the control plane, updates, and scaling, while users manage their applications and worker nodes.
- Kubermatic Kubernetes Platform (KKP):
- Kubermatic Kubernetes Platform is an enterprise-grade solution for deploying and managing Kubernetes clusters across different cloud providers, data centers, or edge locations. It provides a unified interface for managing multiple clusters and comes with advanced features like self-service provisioning, multi-tenancy, and RBAC.
Each of these products provides different features and capabilities to set up and manage Kubernetes clusters. The choice of which one to use depends on factors like your use case, infrastructure, and the level of control and customization you require.
Let's compare the products mentioned earlier based on several factors to help you make an informed decision:
- Ease of Setup and Use:
- Minikube, k3s, and k3d are designed for easy local setups and are straightforward to install and use.
- kubeadm requires more manual configuration but provides greater flexibility and control for cluster customization.
- Kops, Rancher, OpenShift, AKS, EKS, and GKE are more focused on production-ready, cloud-based, or enterprise setups, requiring more initial configuration and management.
- Resource Footprint:
- Minikube and k3d have smaller resource footprints as they run lightweight clusters on your local machine using containers.
- k3s is also designed with a reduced memory footprint, making it suitable for resource-constrained environments or edge computing.
- kubeadm, Kops, Rancher, OpenShift, AKS, EKS, and GKE require more resources due to their full-featured Kubernetes distributions.
- Deployment Flexibility:
- Minikube, kubeadm, k3s, and k3d allow more flexibility in choosing deployment environments and infrastructure.
- Kops is primarily focused on cloud environments like AWS, GCP, and Azure.
- Rancher, OpenShift, AKS, EKS, and GKE are tightly integrated with their respective cloud providers, offering a seamless deployment experience within their ecosystems.
- Features and Capabilities:
- Minikube and k3d provide basic Kubernetes functionality, suitable for local development and testing.
- k3s is fully compliant with Kubernetes but optimized for edge and resource-constrained environments.
- kubeadm, Kops, Rancher, OpenShift, AKS, EKS, and GKE offer a wide range of features, including advanced networking, monitoring, logging, CI/CD integration, and enterprise-grade security features.
- Management Interface:
- Minikube, k3s, and k3d do not provide a graphical management interface. Interaction is mostly through the command line.
- Rancher and OpenShift offer comprehensive management interfaces with additional features like multi-cluster management, app catalogs, and role-based access control (RBAC).
- AKS, EKS, and GKE provide managed Kubernetes services with built-in graphical interfaces for managing clusters and applications.
- Community and Support:
- Minikube, kubeadm, k3s, and k3d are open-source projects with active communities and documentation.
- Kops, Rancher, and OpenShift also have active communities and good support options.
- AKS, EKS, and GKE are managed services provided by their respective cloud providers, offering professional support and SLAs.
In summary, the choice of Kubernetes product depends on your specific requirements and the use case:
· If you need a simple, lightweight setup for local development, Minikube, k3s, or k3d would be suitable.
· For more control and customization in a production environment, kubeadm or Kops might be better options.
· For enterprise features and comprehensive management interfaces, Rancher, OpenShift, AKS, EKS, or GKE would be more appropriate, with the latter three being cloud-specific managed services.
Consider factors such as deployment environment, required features, resource constraints, and support options when selecting the best product for your needs.
Kubernetes is a versatile and widely adopted platform, and many organizations across various industries can leverage it in their environments. Here are some types of organizations that can benefit from using Kubernetes:
1. Technology Companies: Technology companies that develop and deploy software applications can leverage Kubernetes to manage their microservices-based architecture, scale applications, and achieve high availability.
2. Enterprises: Large enterprises can use Kubernetes to modernize their IT infrastructure, adopt cloud-native practices, and manage complex applications across multiple environments.
3. Startups and Small Businesses: Startups and small businesses can use Kubernetes to streamline their development and deployment processes, making it easier to scale their applications as they grow.
4. E-commerce Platforms: E-commerce companies can leverage Kubernetes to manage their web applications, handle high traffic loads during peak times, and ensure continuous availability.
5. Financial Institutions: Financial institutions can use Kubernetes to deploy and manage applications securely while meeting compliance and regulatory requirements.
6. Healthcare and Life Sciences: Organizations in the healthcare and life sciences sectors can use Kubernetes to manage complex data processing and analysis tasks, such as genomics, medical imaging, and electronic health records.
7. Gaming and Entertainment: Gaming and entertainment companies can use Kubernetes to manage multiplayer game servers, streaming platforms, and content delivery networks.
8. Media and Broadcasting: Media and broadcasting organizations can use Kubernetes to efficiently manage content distribution, video processing, and streaming services.
9. Education and Research: Educational institutions and research organizations can leverage Kubernetes for managing large-scale simulations, scientific computations, and data analytics.
10. Government and Public Sector: Government agencies and public sector organizations can adopt Kubernetes for their IT modernization initiatives, data-sharing platforms, and citizen-centric services.
11. Internet of Things (IoT): Companies working on IoT solutions can use Kubernetes to manage and orchestrate edge devices and IoT infrastructure.
12. DevOps and Cloud-Native Teams: Organizations embracing DevOps and cloud-native practices can benefit from Kubernetes to achieve automated deployments, continuous integration, and delivery pipelines.
In summary, Kubernetes is a powerful platform that can be applied across a wide range of industries and use cases. Its flexibility, scalability, and rich ecosystem of tools make it suitable for organizations of all sizes looking to improve application management, resource utilization, and scalability in their environments.
Deploying Kubernetes can be a complex task, but following best practices can help ensure a smooth and successful deployment. Here are some key best practices for deploying Kubernetes:
1. Plan and Design: Start with a clear plan and design for your Kubernetes deployment. Consider factors like cluster size, node capacity, networking, storage requirements, and security needs. Proper planning can help avoid issues later in the deployment process.
2. Choose the Right Platform: Select the appropriate Kubernetes distribution or managed service that suits your needs. Consider factors like ease of management, support options, and integration with your existing infrastructure.
3. High Availability: Set up your cluster in a highly available configuration to ensure continuous availability even if some components or nodes fail. Use multiple master nodes and distributed etcd clusters for resilience.
4. Networking: Choose a networking solution that suits your requirements, such as Kubernetes CNI plugins (Calico, Flannel, Weave) or cloud provider networking solutions. Ensure proper network isolation and connectivity between pods and services.
5. Security: Implement strong security measures for your cluster. Use RBAC (Role-Based Access Control) to control user access and permissions. Enable pod security policies to restrict the capabilities of pods.
6. Storage: Plan for your storage requirements. Decide on the type of storage (local, networked, cloud-based) and the storage class definitions to manage dynamic provisioning of persistent volumes.
7. Monitoring and Logging: Set up monitoring and logging solutions to gain insights into the cluster's performance, health, and application behavior. Tools like Prometheus for monitoring and ELK stack for logging are commonly used.
8. Backup and Disaster Recovery: Establish a backup and disaster recovery strategy to protect critical data and configurations. Regularly back up etcd data to ensure recoverability.
9. Namespace and Resource Quotas: Use namespaces to organize your resources and logically isolate different applications or teams. Apply resource quotas to control the resource consumption of namespaces.
10. Updates and Upgrades: Stay up to date with Kubernetes releases and security patches. Perform regular updates and upgrades in a controlled manner to avoid disruptions.
11. Automation and CI/CD: Automate cluster provisioning and application deployment using infrastructure-as-code (IaC) tools like Terraform or Kubernetes manifest files. Implement CI/CD pipelines for smooth application updates.
12. Documentation and Training: Document your deployment processes, configurations, and best practices. Provide training and knowledge sharing for your team members to ensure proper understanding and management of the Kubernetes environment.
13. Testing and Validation: Thoroughly test your deployment in staging environments before moving to production. Use testing tools like Sonobuoy to validate the conformance and performance of your cluster.
14. Community and Support: Leverage the Kubernetes community and available support channels to seek help and share experiences. Engage in discussions and forums to learn from others' experiences.
By following these best practices, you can deploy Kubernetes with confidence and create a robust, scalable, and reliable environment for managing your containerized applications effectively. Remember that each organization's requirements may vary, so tailor the deployment approach to suit your specific needs.
Key Considerations and Watch-Outs:
1. Security: Pay close attention to securing your Kubernetes cluster. Implement strong authentication, authorization, and network policies to protect against potential security breaches.
2. Monitoring and Observability: Set up monitoring and logging tools to gain insights into cluster health and application performance. Monitoring can help detect issues early and facilitate efficient troubleshooting.
3. Backup and Disaster Recovery: Have a robust backup and disaster recovery strategy in place, especially for the etcd data store, to ensure you can recover the cluster in case of failures.
4. Resource Management: Watch out for overprovisioning or underprovisioning resources in your cluster. Regularly monitor resource utilization to optimize efficiency.
5. Version Compatibility: Be cautious when upgrading Kubernetes versions, as it may lead to compatibility issues with existing applications and custom resources.
Kubernetes is a game-changing technology that empowers organizations to manage containerized applications effectively, streamline deployments, and achieve unprecedented scalability. By adopting Kubernetes, organizations can embrace cloud-native practices, ensure high availability, and future-proof their application infrastructure. However, it's essential to approach Kubernetes deployment methodically, considering the specific needs of your organization and closely monitoring key aspects like security, resource management, and observability. With careful planning and adherence to best practices, organizations can unlock the full potential of Kubernetes and revolutionize their approach to application management.
Kubernetes revolutionizes app management, enabling scalability and efficiency for organizations embracing containers.