Sanjay K Mohindroo
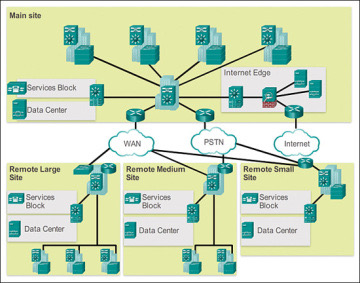
In today's technologically advanced world, networking plays a vital role in the success of any business or organization. Cisco, as one of the world's leading networking technology providers, offers a wide range of network protocols that are essential for managing and maintaining a network. This guide will provide an in-depth understanding of Cisco network protocols for IT leaders and networking professionals who want to gain a comprehensive knowledge of Cisco networking. In this article, we will list and explain the various Cisco network protocols that IT networking folks and IT leadership need to be aware of.
- Routing Protocols: Routing protocols are used to enable routers to communicate with each other and determine the best path for data transmission. Cisco offers three primary routing protocols:
- Routing Information Protocol (RIP): a distance-vector protocol that sends the entire routing table to its neighbors every 30 seconds.
- Open Shortest Path First (OSPF): a link-state protocol that exchanges link-state advertisements to construct a topology map of the network.
- Enhanced Interior Gateway Routing Protocol (EIGRP): a hybrid protocol that uses both distance-vector and link-state algorithms to determine the best path.
- Switching Protocols: Switching protocols are used to forward data packets between different network segments. Cisco offers two primary switching protocols:
- Spanning Tree Protocol (STP): a protocol that prevents network loops by shutting down redundant links.
- VLAN Trunking Protocol (VTP): a protocol that synchronizes VLAN configuration information between switches.
- Wide Area Network (WAN) Protocols: WAN protocols are used to connect remote networks over a wide geographic area. Cisco offers two primary WAN protocols:
- Point-to-Point Protocol (PPP): a protocol used to establish a direct connection between two devices over a serial link.
- High-Level Data Link Control (HDLC): a protocol used to encapsulate data over serial links.
- Security Protocols: Security protocols are used to secure the network and prevent unauthorized access. Cisco offers two primary security protocols:
- Internet Protocol Security (IPSec): a protocol used to secure IP packets by encrypting them.
- Secure Sockets Layer (SSL): a protocol used to establish a secure connection between a client and a server.
- Multi-Protocol Label Switching (MPLS): MPLS is a protocol used to optimize the speed and efficiency of data transmission. It uses labels to forward packets instead of IP addresses, which allows for faster routing and less congestion on the network.
- Border Gateway Protocol (BGP): BGP is a protocol used to route data between different autonomous systems (AS). It is commonly used by internet service providers to exchange routing information.
- Hot Standby Router Protocol (HSRP): HSRP is a protocol used to provide redundancy for IP networks. It allows for two or more routers to share a virtual IP address, so if one router fails, the other can take over seamlessly.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. It is commonly used in voice and video applications to prevent latency and ensure high-quality transmission.
In conclusion, Cisco network protocols are essential for maintaining and managing a network. Understanding these protocols is crucial for IT networking folks and IT leadership. By implementing Cisco network protocols, organizations can ensure that their network is secure, efficient, and reliable. Relevant examples and case studies can provide a better understanding of how these protocols work in real-life scenarios.
Examples of some of the Cisco network protocols mentioned in the article.
- Routing Protocols: Let's take a look at OSPF, which is a link-state protocol that exchanges link-state advertisements to construct a topology map of the network. This protocol is commonly used in enterprise networks to provide faster convergence and better scalability. For example, if there is a link failure in the network, OSPF routers can quickly recalculate the best path and update the routing table, ensuring that data is still transmitted efficiently.
- Switching Protocols: The Spanning Tree Protocol (STP) is a protocol that prevents network loops by shutting down redundant links. It works by selecting a single active path and blocking all other redundant paths, ensuring that there is no possibility of a loop forming. For example, if there are two switches connected via multiple links, STP will identify the shortest path and block the other links to prevent broadcast storms or other network issues.
- Wide Area Network (WAN) Protocols: The Point-to-Point Protocol (PPP) is a protocol used to establish a direct connection between two devices over a serial link. PPP provides authentication, compression, and error detection features, making it an ideal protocol for connecting remote sites. For example, if a company has a branch office in a remote location, it can use PPP to connect the remote site to the main office via a leased line.
- Security Protocols: Internet Protocol Security (IPSec) is a protocol used to secure IP packets by encrypting them. This protocol provides confidentiality, integrity, and authentication features, making it an ideal choice for securing data transmissions over the Internet. For example, if an organization needs to send sensitive data over the internet, it can use IPSec to encrypt the data, ensuring that it cannot be intercepted or modified by unauthorized parties.
- Quality of Service (QoS): QoS is a protocol used to prioritize network traffic to ensure that important data receives the necessary bandwidth. For example, if an organization is running voice and video applications on their network, they can use QoS to prioritize that traffic over other less critical traffic, ensuring that no latency or jitter could impact the quality of the transmission.
These are just a few examples of how Cisco network protocols work in real-life scenarios. By understanding how these protocols work and implementing them correctly, organizations can ensure that their network is secure, efficient, and reliable.
Here are some examples of how organizations can implement Cisco network protocols in their network infrastructure:
- Routing Protocols: An organization can implement the OSPF protocol by configuring OSPF on their routers and setting up areas to control network traffic. They can also use OSPF to optimize the path selection between routers by configuring the cost of the links based on bandwidth and delay.
- Switching Protocols: To implement the Spanning Tree Protocol (STP), an organization can configure STP on their switches to prevent network loops. They can also use Rapid Spanning Tree Protocol (RSTP) or Multiple Spanning Tree Protocol (MSTP) to reduce the convergence time and improve network performance.
- Wide Area Network (WAN) Protocols: An organization can implement the Point-to-Point Protocol (PPP) by configuring PPP on their routers to establish a direct connection between two devices over a serial link. They can also use PPP with authentication, compression, and error detection features to improve the security and efficiency of their network.
- Security Protocols: To implement the Internet Protocol Security (IPSec) protocol, an organization can configure IPSec on their routers and firewalls to encrypt data transmissions and provide secure communication over the Internet. They can also use IPSec with digital certificates to authenticate users and devices.
- Quality of Service (QoS): An organization can implement Quality of Service (QoS) by configuring QoS on their switches and routers to prioritize network traffic. They can also use QoS with Differentiated Services Code Point (DSCP) to classify and prioritize traffic based on its type and importance.
These are just a few examples of how organizations can implement Cisco network protocols in their network infrastructure. By implementing these protocols correctly, organizations can ensure that their network is secure, efficient, and reliable, providing the necessary tools to support business-critical applications and services.
Here's a tutorial on how to configure some of the Cisco network protocols on routers and switches.
- Routing Protocols:
Step 1: Enable the routing protocol on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the router ID and set up the interfaces by using the "router ospf" command.
Step 3: Set up the areas to control network traffic by using the "area" command.
Step 4: Configure the cost of the links based on bandwidth and delay by using the "ip ospf cost" command.
Step 5: Verify the OSPF configuration by using the "show ip ospf" command.
- Switching Protocols:
Step 1: Enable the Spanning Tree Protocol (STP) on the switch by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the bridge priority by using the "spanning-tree vlan [vlan-id] root" command.
Step 3: Set up the port priority and cost by using the "spanning-tree vlan [vlan-id] [port-id] priority [priority]" and "spanning-tree vlan [vlan-id] [port-id] cost [cost]" commands.
Step 4: Verify the STP configuration by using the "show spanning tree" command.
- Wide Area Network (WAN) Protocols:
Step 1: Enable the Point-to-Point Protocol (PPP) on the router by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the PPP authentication by using the "ppp authentication [chap/pap]" command.
Step 3: Set up the PPP options by using the "ppp multilink" and "ppp multilink fragment delay [delay]" commands.
Step 4: Verify the PPP configuration by using the "show ppp multilink" command.
- Security Protocols:
Step 1: Enable the Internet Protocol Security (IPSec) protocol on the router or firewall by entering the configuration mode using the "configure terminal" command.
Step 2: Configure the crypto map and set up the IP address and the pre-shared key by using the "crypto map [map-name] [seq-num] ipsec-isakmp" and "set peer [peer-address] key [pre-shared-key]" commands.
Step 3: Configure the access list to specify the traffic to be encrypted by using the "access-list [acl-number] permit [source-address] [destination-address]" command.
Step 4: Verify the IPSec configuration by using the "show crypto map" command.
- Quality of Service (QoS):
Step 1: Enable the Quality of Service (QoS) on the switch or router by entering the configuration mode using the "configure terminal" command.
Step 2: Set up the class map and the match criteria by using the "class-map [class-name]" and "match [criteria]" commands.
Step 3: Configure the policy map and the traffic shaping by using the "policy-map [policy-name]" and "shape average [bandwidth]" commands.
Step 4: Apply the QoS policy to the interface by using the "service-policy output [policy-name]" command.
Step 5: Verify the QoS configuration by using the "show policy-map interface [interface-name]" command.
These are just some basic steps for configuring some of the Cisco network protocols on routers and switches. Depending on your specific network requirements, you may need to configure additional settings or features. Always make sure to test and verify your configuration to ensure that it is working as expected.
Cisco's networking devices, such as routers and switches, run on an operating system (OS) called Cisco IOS (Internetwork Operating System). IOS is a proprietary OS that is specifically designed to run on Cisco's networking hardware.
IOS provides the networking infrastructure with a wide range of features, including routing, switching, and security protocols. It also includes a command-line interface (CLI) that allows administrators to configure and manage the device's settings.
One of the key advantages of IOS is its modular design, which allows administrators to customize the OS by adding or removing specific features as needed. This modularity provides flexibility in managing the network devices and helps to keep the OS streamlined and efficient.
In addition to the traditional IOS, Cisco also offers a range of specialized operating systems for specific devices or environments, such as IOS XR for service provider networks or IOS XE for enterprise networks.
Overall, IOS is a reliable and flexible operating system that has been proven to be effective in managing and securing Cisco's networking devices. Its CLI is widely used by network administrators around the world, making it a valuable tool for managing networks of all sizes and complexities.
I can provide an extensive list of all the commands used in Cisco IOS, but it would not be feasible to explain every command in detail as it would require a significant amount of time and space. Instead, I can provide an overview of some of the essential commands used in Cisco IOS and their functions:
- enable: This command enables privileged mode, which provides access to configuration commands and advanced system settings.
- show: This command displays information about the system configuration, interface status, and device performance.
- configure terminal: This command enters global configuration mode, which allows users to configure the device settings and protocols.
- interface: This command configures individual interfaces on the device, such as Ethernet or serial ports.
- ip address: This command assigns IP addresses to network interfaces.
- hostname: This command sets the device hostname, which is used for identification purposes.
- ping: This command sends ICMP packets to test network connectivity.
- traceroute: This command traces the path that packets take from the source to the destination.
- Access list: This command configures access control lists to control traffic flow and filter packets.
- shutdown: This command disables an interface or a protocol.
- reload: This command reloads the device, which is useful for resetting configurations or troubleshooting issues.
These commands are just a few examples of the many commands available in Cisco IOS. Each command has specific syntax and options, and it's essential to use them correctly to avoid configuration errors and network issues. Cisco provides extensive documentation and training resources for users to learn about the commands and their functions. Network administrators must understand the basics of IOS commands to effectively manage and maintain their networks.
