In this post, we will discuss the concept of zero-trust security, its advantages and disadvantages, best practices, approaches to implement, and the organizations that should use this methodology. We will explore how zero-trust security can help protect sensitive data and prevent unauthorized access in today's world, where cyber threats are on the rise.
In recent years, there has been a significant increase in the number of cyber attacks on organizations worldwide. In response, many businesses have implemented various security measures to protect their sensitive data and prevent unauthorized access. One such approach is zero-trust security, which has become increasingly popular among organizations of all sizes. In this blog post, we will discuss what zero-trust security is, its advantages and disadvantages, best practices, and approaches to implement, as well as which organizations should use this methodology.
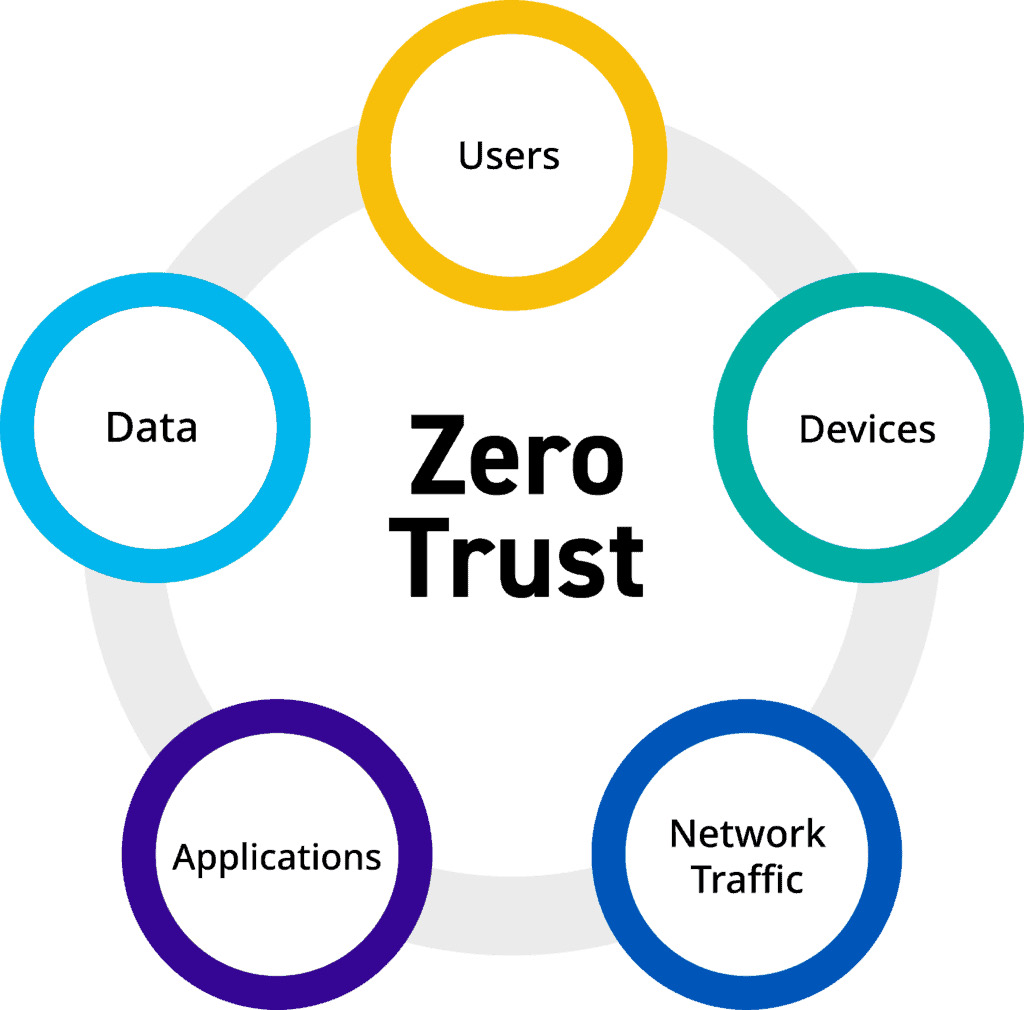
What is Zero-Trust Security?
Zero-trust security is a security model that assumes that all devices, users, applications, and data are untrusted until proven otherwise. This approach requires organizations to verify and authenticate every user and device attempting to access their network, even if they are already inside the network perimeter. Zero-trust security focuses on limiting access to sensitive data and systems, reducing the attack surface, and increasing security.
Advantages and Disadvantages of Zero-Trust Security
One of the main advantages of zero-trust security is that it significantly reduces the risk of data breaches and cyber-attacks. By assuming that all devices and users are untrusted, organizations can implement stronger security measures, such as multi-factor authentication, access controls, and encryption. Zero-trust security also provides better visibility into network activity, making it easier to detect and respond to threats.
However, zero-trust security can also have some disadvantages. It can be expensive and complex to implement, requiring significant changes to the organization's network infrastructure and security policies. Zero-trust security can also increase the risk of user frustration and reduce productivity, as users may need to authenticate multiple times to access different resources.
Best Practices for Implementing Zero-Trust Security
Here are some best practices for implementing zero-trust security in your organization:
1. Develop a comprehensive security policy that includes zero-trust principles, such as access controls, authentication, and encryption.
2. Implement multi-factor authentication for all users, devices, and applications.
3. Limit access to sensitive data and systems to only those who need it, and monitor all access attempts.
4. Use encryption to protect data in transit and at rest.
5. Implement network segmentation to reduce the attack surface and limit lateral movement.
6. Use behavioral analytics and machine learning to detect and respond to threats in real-time.
Approaches to Implementing Zero-Trust Security
There are several approaches to implementing zero-trust security, including:
1. Network Segmentation: This approach involves dividing the network into smaller, more manageable segments, and applying access controls and authentication measures to each segment.
2. Identity and Access Management: This approach focuses on managing user identities and access to resources, enforcing policies such as multi-factor authentication and role-based access control.
3. Micro-segmentation: This approach involves dividing the network into even smaller segments, allowing for more granular access controls and security policies.
Organizations That Should Use Zero-Trust Security
Zero-trust security is suitable for organizations of all sizes and industries, but it is especially important for those that handle sensitive data, such as financial institutions, healthcare providers, and government agencies. Any organization that wants to reduce the risk of cyber-attacks and data breaches should consider implementing zero-trust security.
Conclusion
Zero-trust security is a security model that assumes that all devices, users, applications, and data are untrusted until proven otherwise. It focuses on limiting access to sensitive data and systems, reducing the attack surface, and increasing security. While zero-trust security can be complex and expensive to implement, it provides significant advantages in terms of reducing the risk of cyber-attacks and data breaches. By following best practices and choosing the right approach for your organization, you can implement zero-trust security and protect your sensitive data from unauthorized access.